基于ProxyPool创建Proxifier代理
如题目所见,闲来无事在做测试时发现被某网站封了IP,为防止再被封掉,因此有了这篇文章和搭建过程
0x01 安装redis服务
ubuntu16.04
apt-get install redis-server
检查是否服务是否启动
ps aux |grep redis
netstat -lanp | grep 6379

配置redis.conf文件
配置密码及使用远程登
参考:https://www.cnblogs.com/wxjnew/p/9189191.html
重启redis服务后进入redis客户端测试redis-clil
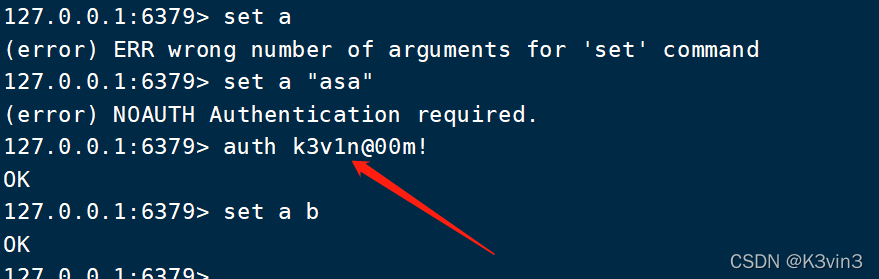
注意:Redis默认不是以守护进程的方式运行,可以通过该配置项修改,使用yes启用守护进程,设置为no

0x02 拉docker环境
为偷个懒,直接用docker搭建了
使用github开源ProxyPool项目进行免费的代理IP进行收集、进行可用性验证,将已经验证过代理链接信息保存在Redis数据库中,并且支持docker部署
github传送门:https://github.com/jhao104/proxy_pool
docker pull jhao104/proxy_pool
docker run --en vDB_CONN=redis://:redis数据库密码(不要设置密码,后续执行创建Proxifier配置文件python脚本,使用非认证操作)@ip:port/数据库序号(可以默认写0)-p 5010:5010 jhao104/proxy_pool:latest
docker run --env DB_CONN=redis://:@your-ip:6379/0 -p 5010:5010 jhao104/proxy_pool:lates
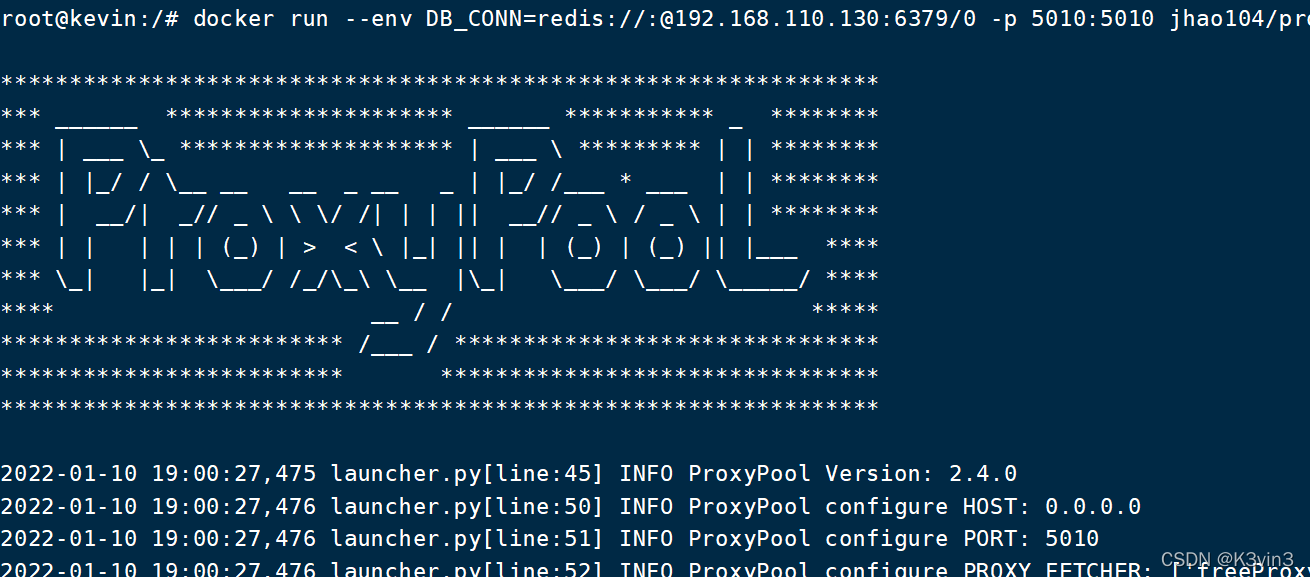
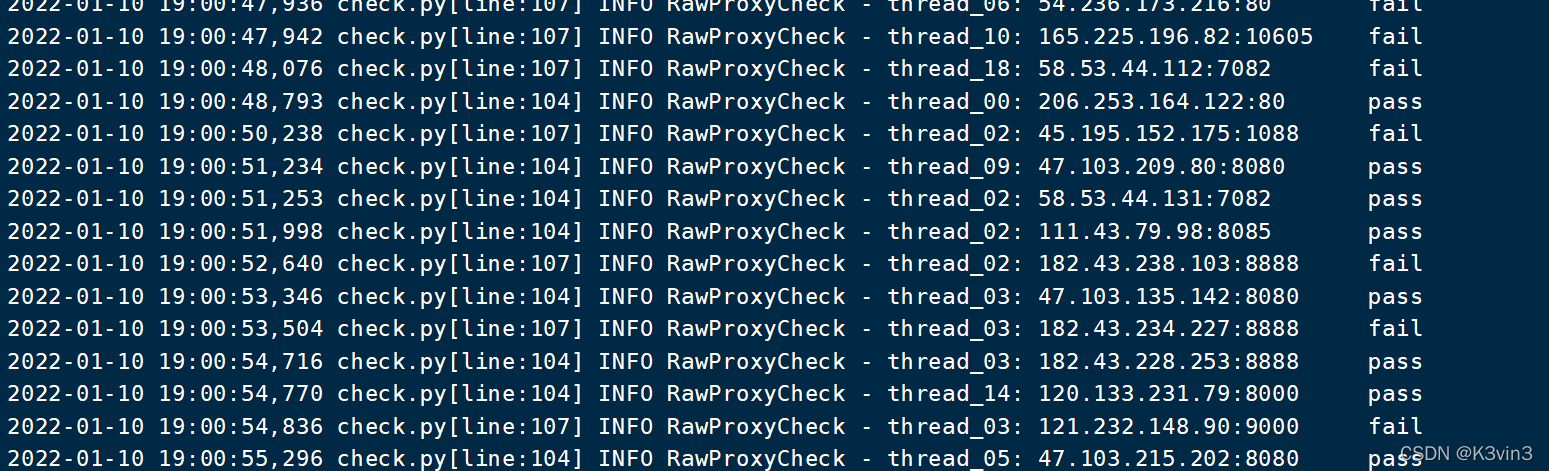
0x03 连接RedisDesktopManager
百度网盘传送门:https://pan.baidu.com/s/1NVPOWSjqDEvBFVA1nkk1uQ
提取码:z7qr
直接连接redis服务的地址
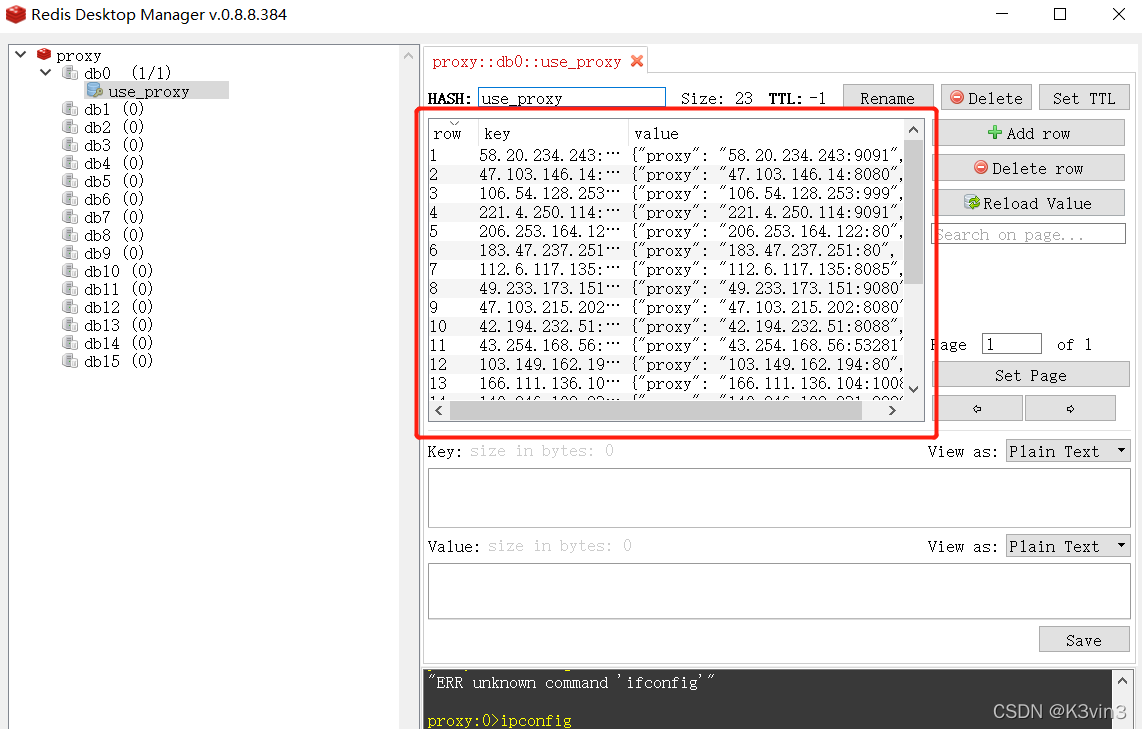
0x04 安装Proxifier
注意:这里Proxifier的版本不能太高,否则会报错,建议3.3.1
百度网盘传送门:https://pan.baidu.com/s/12U7cb4Mbd4pQzVLkaTJwtQ
提取码:hd2m
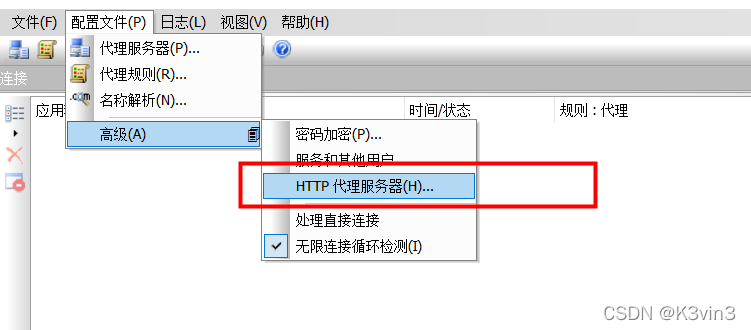
开启HTTP代理服务器设置,因为有一些代理ip是走HTTP协议的,而Proxifier默认只支持HTTPS协议
0x05 生成Proxifier配置文件
python3脚本如下
#!/usr/bin/python
# -*- coding:utf8 -*-
import redis
import json
from xml.etree import ElementTree
def RedisProxyGet():
ConnectString = []
pool = redis.ConnectionPool(host='你的redis服务地址', port=6379, db=0, decode_responses=True)
use_proxy = redis.Redis(connection_pool=pool)
key = use_proxy.hkeys('use_proxy')
for temp in key:
try:
ConnectString.append(json.loads(use_proxy.hget('use_proxy',temp)))
except json.JSONDecodeError: # JSON解析异常处理
pass
return ConnectString
def xmlOutputs(data):
i = 101
ProxyIDList = []
# ProxifierProfile根
ProxifierProfile = ElementTree.Element("ProxifierProfile")
ProxifierProfile.set("version", str(i))
ProxifierProfile.set("platform", "Windows")
ProxifierProfile.set("product_id", "0")
ProxifierProfile.set("product_minver", "310")
# Options 节点
Options = ElementTree.SubElement(ProxifierProfile, "Options")
# Options.Resolve
Resolve = ElementTree.SubElement(Options, "Resolve")
# Options.Resolve.AutoModeDetection
AutoModeDetection = ElementTree.SubElement(Resolve, "AutoModeDetection")
AutoModeDetection.set("enabled", "false")
# Options.Resolve.ViaProxy
ViaProxy = ElementTree.SubElement(Resolve, "ViaProxy")
ViaProxy.set("enabled", "false")
# Options.Resolve.ViaProxy.TryLocalDnsFirst
TryLocalDnsFirst = ElementTree.SubElement(ViaProxy, "TryLocalDnsFirst")
TryLocalDnsFirst.set("enabled", "false")
# Options.Resolve.ExclusionList
ExclusionList = ElementTree.SubElement(Resolve, "ExclusionList")
ExclusionList.text = "%ComputerName%; localhost; *.local"
# Options.*
Encryption = ElementTree.SubElement(Options, "Encryption")
Encryption.set("mode", 'basic')
Encryption = ElementTree.SubElement(Options, "HttpProxiesSupport")
Encryption.set("enabled", 'true')
Encryption = ElementTree.SubElement(Options, "HandleDirectConnections")
Encryption.set("enabled", 'false')
Encryption = ElementTree.SubElement(Options, "ConnectionLoopDetection")
Encryption.set("enabled", 'true')
Encryption = ElementTree.SubElement(Options, "ProcessServices")
Encryption.set("enabled", 'false')
Encryption = ElementTree.SubElement(Options, "ProcessOtherUsers")
Encryption.set("enabled", 'false')
# ProxyList
ProxyList = ElementTree.SubElement(ProxifierProfile, "ProxyList")
for temp in data:
i += 1 # 从101开始增加
# ProxyList.Proxy
Proxy = ElementTree.SubElement(ProxyList, "Proxy")
Proxy.set("id", str(i))
if not temp['https']:
Proxy.set("type", "HTTP")
else:
Proxy.set("type", "HTTPS")
Proxy.text = str(i)
ProxyIDList.append(i)
# ProxyList.Proxy.Address
Address = ElementTree.SubElement(Proxy, "Address")
Address.text = temp['proxy'].split(":", 1)[0]
# ProxyList.Proxy.Port
Port = ElementTree.SubElement(Proxy, "Port")
Port.text = temp['proxy'].split(":", 1)[1]
# ProxyList.Proxy.Options
Options = ElementTree.SubElement(Proxy, "Options")
Options.text = "48"
# RuleList
ChainList = ElementTree.SubElement(ProxifierProfile, "ChainList")
# RuleList.Chain
Chain = ElementTree.SubElement(ChainList, "Chain")
Chain.set("id", str(i))
Chain.set("type", "simple")
# RuleList.Chain.Name
Name = ElementTree.SubElement(Chain, "Name")
Name.text="AgentPool"
# RuleList.Chain.Proxy
for temp_id in ProxyIDList:
Proxy = ElementTree.SubElement(Chain, "Proxy")
Proxy.set("enabled", "true")
Proxy.text=str(temp_id)
# RuleList
RuleList = ElementTree.SubElement(ProxifierProfile, "RuleList")
# Rule
Rule = ElementTree.SubElement(RuleList, "Rule")
Rule.set("enabled", "true")
Name = ElementTree.SubElement(Rule,"Name")
Applications = ElementTree.SubElement(Rule,"Applications")
Action = ElementTree.SubElement(Rule,"Action")
Name.text="御剑后台扫描工具.exe [auto-created]"
Applications.text="御剑后台扫描工具.exe"
Action.set("type","Direct")
# Rule
Rule = ElementTree.SubElement(RuleList, "Rule")
Rule.set("enabled", "true")
Name = ElementTree.SubElement(Rule,"Name")
Targets = ElementTree.SubElement(Rule,"Targets")
Action = ElementTree.SubElement(Rule,"Action")
Name.text="Localhost"
Targets.text="localhost; 127.0.0.1; %ComputerName%"
Action.set("type", "Direct")
# Rule
Rule = ElementTree.SubElement(RuleList, "Rule")
Rule.set("enabled", "true")
Name = ElementTree.SubElement(Rule, "Name")
Action = ElementTree.SubElement(Rule, "Action")
Name.text = "Default"
Action.text = "102"
Action.set("type", "Proxy")
tree = ElementTree.ElementTree(ProxifierProfile)
tree.write("ProxifierConf.ppx", encoding="UTF-8", xml_declaration=True)
if __name__ == '__main__':
proxy_data = RedisProxyGet()
xmlOutputs(proxy_data)
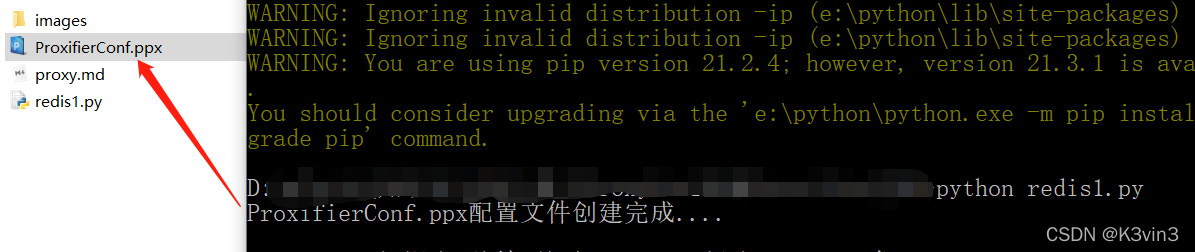
print("ProxifierConf.ppx配置文件创建完成....")
运行该脚本,生成ProxifierConf.ppx文件
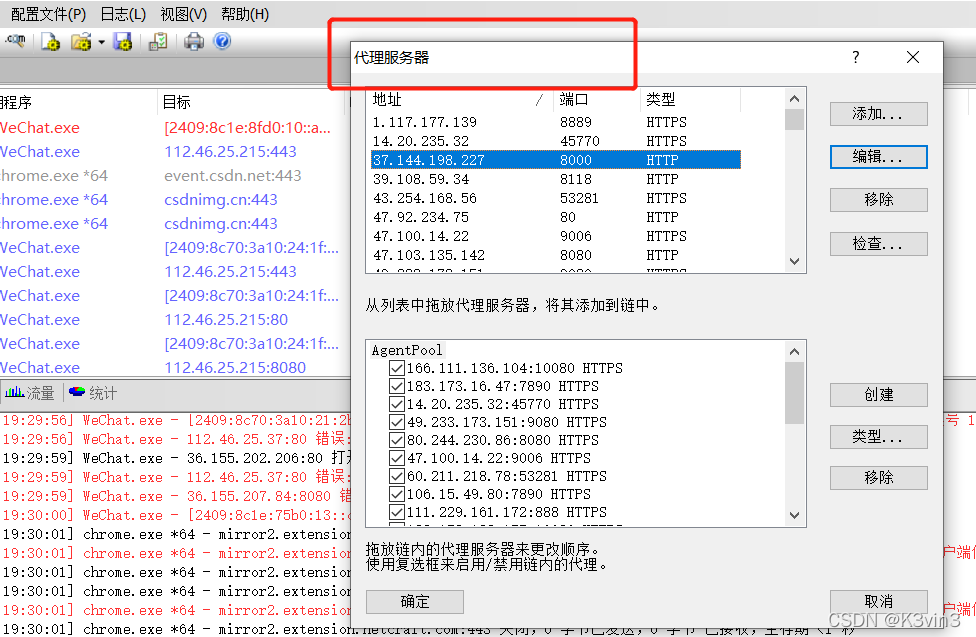
Proxifier配置文件导入(双击ProxifierConf.ppx导入)
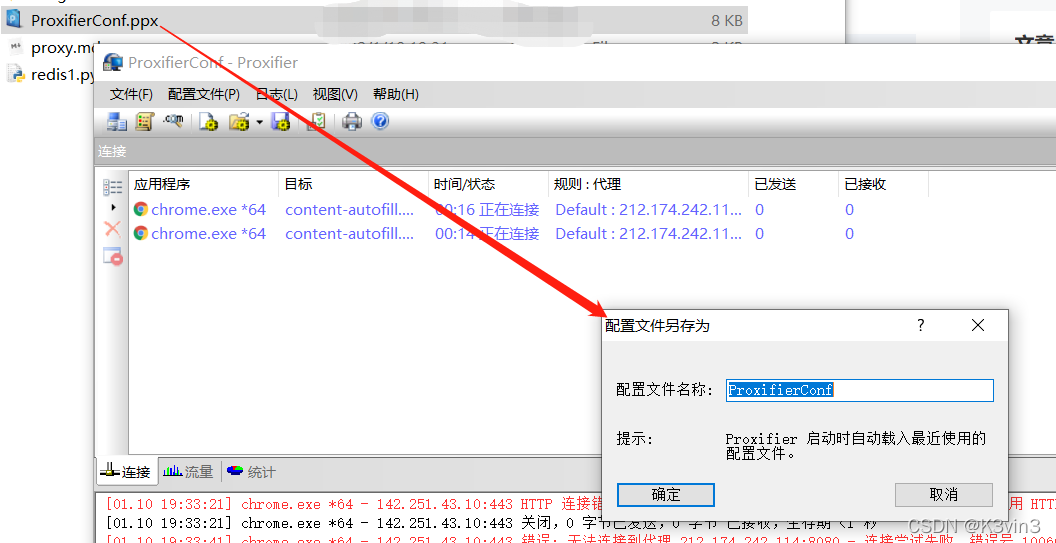
导入配置文件后可以看到代理服务器(代理池)中出现了很多代理地址
0x06
妈妈再也不用担心我被封IP啦