1 概述:
1.1 环境
版本信息如下:
a、操作系统:centos 7.6
b、openssl: openssl-1.0.2
2 创建自签CA:
以下将生成一个名称为ca.key的key文件和一个名称为ca.crt的证书文件,CA的common name叫EXAMPLE Cert Authority。
openssl req -x509 -sha256 -newkey rsa:4096 -keyout ca.key -out ca.crt -days 3560 -nodes -subj '/CN=EXAMPLE Cert Authority'
3 签发自定义证书:
3.1 生成key文件和csr文件
key文件名称为server.key,csr文件名称为server.csr,common name为www.example.com。
openssl req -new -newkey rsa:4096 -keyout server.key -out server.csr -nodes -subj '/CN=www.example.com'
3.2 编写csr扩展文件extfile
SAN就在subjectAltName字段中指定,可以写多个域名和IP,例如域名为dinner,IP为192.168.35.72。
cat > extfile.cnf << EOF
[ v3_req ]
# Extensions to add to a certificate request
extendedKeyUsage = serverAuth,clientAuth
subjectAltName = DNS:dinner,DNS:localhost,IP:192.168.35.72,IP:127.0.0.1
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
EOF
3.3 生成证书文件
依据key文件、csr文件和csr扩展文件,生成证书文件(名称为server.crt)
openssl x509 -req -sha256 -days 3650 \
-extfile extfile.cnf \
-extensions v3_req \
-in server.csr -CA ca.crt -CAkey ca.key -out server.crt -CAcreateserial
3.4 检验证书文件是否由指定CA签署
openssl verify -CAfile ca.crt -verbose server.crt
3.5 查看证书文件详细
openssl x509 -in server.crt -noout -text
4 openssl案例应用
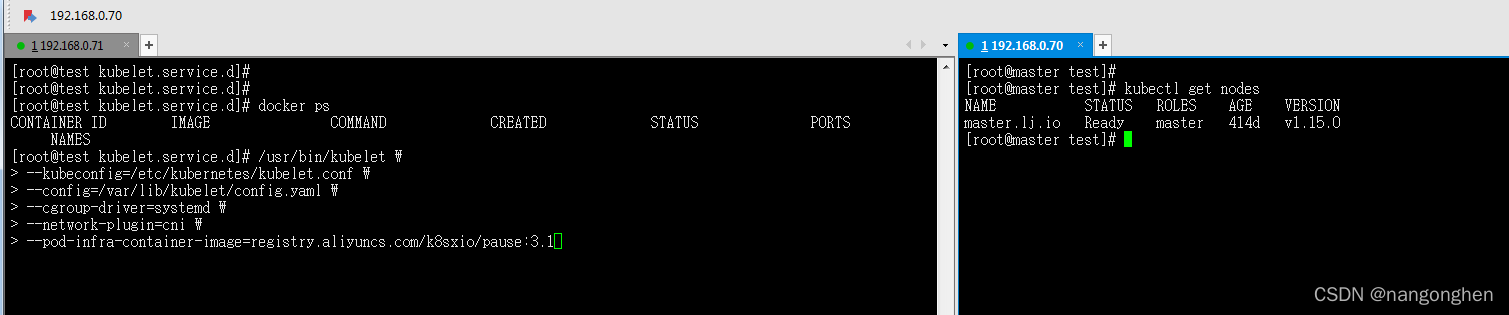
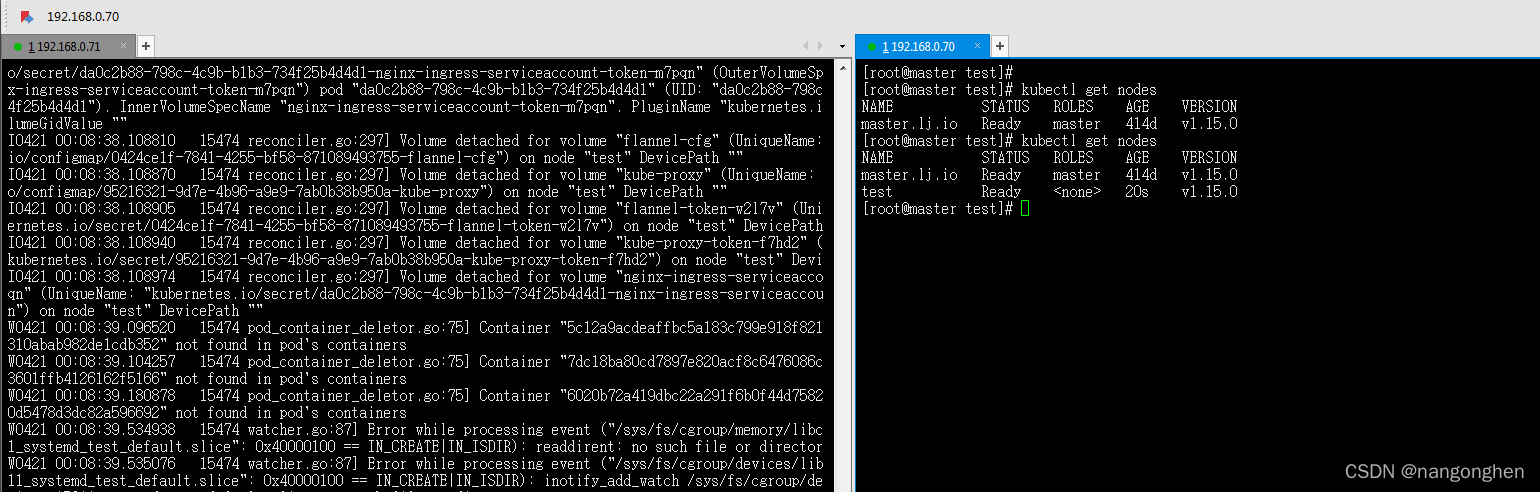
为k8s集群新增一个node节点,node节点名称为test,通过openssl命令生成kubelet的证书和key文件。
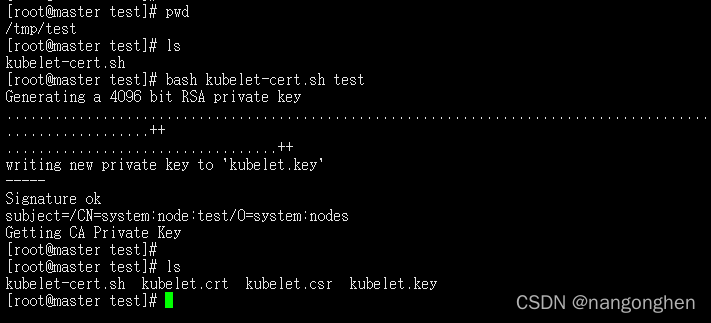
4.1 制作生成kubelet证书和key文件的脚本(kubelet-cert.sh)
假设k8s集群控制面板组件的CA证书和key分别是:/etc/kubernetes/pki/ca.crt和/etc/kubernetes/pki/ca.key。
#/bin/bash
nodeName=$1
subj="/CN=system:node:$nodeName/O=system:nodes"
openssl req -new -newkey rsa:4096 -keyout kubelet.key -out kubelet.csr -nodes -subj "$subj"
openssl x509 -req -in kubelet.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -out kubelet.crt -CAcreateserial
4.2 生成kubelet证书和key文件
在master节点上,使用脚本生成kubelet的key文件(kubelet.key)和证书文件(kubelet.crt),并通过scp指令将它们复制到node节点的/var/lib/kubelet/pki/目录中。
4.3 创建kubelet的kubeconfig文件
node节点已经具备证书文件 /var/lib/kubelet/pki/kubelet.crt 和key文件 /var/lib/kubelet/pki/kubelet.key,
现在创建kubeconfig文件 /etc/kubernetes/kubelet.conf,内容如下:
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1ETXdNVEUzTURJMU1sb1hEVE14TURJeU56RTNNREkxTWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTlB1Ckc4VHFuL0RuSjNNWkxFaGNUMTA3SFlnMVZsL0JtTkhMdm1RY1I3S0JGWlVxdHFsQllYcnNqa3dhRzlDV3BOVG8KL0QyN1Q2Y0g2enJqYmFhVjMxTXZPY1B3cVlkMTJXZTdPUEd6MEZLemMxcThWak9ndjIrUG40dy95NXk3dG5MVQp3MjR2eXpRT255b3ltVk9LWG5YWENHM2FTRVNCbDBUTWphVE5JN2t5RjFIeWxZNCtkOHRDWHc4YVNhNTdXWTNOCjVwcWIzNVNJNkUvUG9KL0ZtNFRhekFrdWZPVmZDUENjcTdhZlF3Vk0ycC92dm5IaWRXbEZicitWL3ZhWndlVGkKVG9JL1NYNVl0eFhHMWlSdFJROGlyTFpVUVdYbGJwampkeEsvQVVzVmFkNHFDdkd1UGRSQy9xQjJwWG96SllncAo5OTB1dWxwWG9pQWo3RGJYMUdjQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFDVlhGTThuQk94TXlwMnBoRm5jdjVXMHJOUW8Kc1puaTNjK3huWGJVZDcwM2lTUmdJbDgvL1RzSm1adjVWSzJ2OCtxTzU2bnNma0FTQ2dOOWZWdlRGZi9PYklJQgozMkxvMXZ1RjBld1VwdmpaYXVBNlBGdDVvNEVVeVcxTXYxYkNDdUN2NzZvR0RNeE1uczJ0TU9neWxRMmxxRzRECjd5ZHh6c0pKUnZMNXJJa3E4dlF2U1lydjRyNGlSbVZCNXZIZjBPTmRsQTFNdzZScFROZTBkL0R6VUhnRmVVYjIKVisvQ1pMdS96aThON3U2ays0UTFsWFJ3S2dQVjRjSGZUZVJLVUppTmVTeC92NnJoUlpvQ0c5bWcvbXU1SWFweQo2TGtJQXZ0YmZVdktVM3grUU5zL1BuWkxScndsbGVmT1ZVZGYrTDZtMFRtcVo3UUpjYnh2VjdtcUZDYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
server: https://192.168.0.70:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: system:node:test
name: system:node:test@kubernetes
current-context: system:node:test@kubernetes
kind: Config
preferences: {}
users:
- name: system:node:test
user:
client-certificate: /var/lib/kubelet/pki/kubelet.crt
client-key: /var/lib/kubelet/pki/kubelet.key
4.4 创建kubelet自身的配置文件
在node节点,创建配置文件/var/lib/kubelet/config.yaml,内容如下:
address: 0.0.0.0
apiVersion: kubelet.config.k8s.io/v1beta1
cgroupDriver: cgroupfs
cgroupsPerQOS: true
clusterDNS:
- 10.96.0.10
configMapAndSecretChangeDetectionStrategy: Watch
containerLogMaxFiles: 5
containerLogMaxSize: 100Mi
contentType: application/vnd.kubernetes.protobuf
cpuCFSQuota: true
cpuCFSQuotaPeriod: 100ms
cpuManagerPolicy: none
cpuManagerReconcilePeriod: 10s
enableControllerAttachDetach: true
enableDebuggingHandlers: true
enforceNodeAllocatable:
- pods
eventBurst: 10
eventRecordQPS: 5
evictionHard:
imagefs.available: 5%
memory.available: 500Mi
nodefs.available: 5%
nodefs.inodesFree: 5%
evictionPressureTransitionPeriod: 5m0s
failSwapOn: true
fileCheckFrequency: 20s
hairpinMode: promiscuous-bridge
healthzBindAddress: 127.0.0.1
healthzPort: 10248
httpCheckFrequency: 20s
imageGCHighThresholdPercent: 85
imageGCLowThresholdPercent: 80
imageMinimumGCAge: 2m0s
iptablesDropBit: 15
iptablesMasqueradeBit: 14
kind: KubeletConfiguration
kubeAPIBurst: 10
kubeAPIQPS: 5
makeIPTablesUtilChains: true
maxOpenFiles: 1000000
maxPods: 110
nodeLeaseDurationSeconds: 40
nodeStatusReportFrequency: 1m0s
nodeStatusUpdateFrequency: 10s
port: 10250
registryBurst: 10
registryPullQPS: 5
rotateCertificates: true
runtimeRequestTimeout: 2m0s
serializeImagePulls: true
staticPodPath: /etc/kubernetes/manifests
4.5 启动kubelet程序
不需要启动参数bootstrap-kubeconfig,命令如下:
/usr/bin/kubelet \
--kubeconfig=/etc/kubernetes/kubelet.conf \
--config=/var/lib/kubelet/config.yaml \
--cgroup-driver=systemd \
--network-plugin=cni \
--pod-infra-container-image=registry.aliyuncs.com/k8sxio/pause:3.1