Software Security Issues (Especially Java)
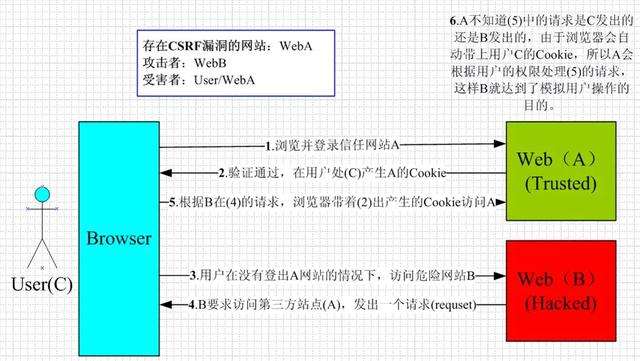
CSRF (Cross—Site Request Forgery) 跨站点请求伪造
(Cross Site Request Forgery, 跨站域请求伪造)是一种网络的攻击方式,它在 2007 年曾被列为互联网 20 大安全隐患之一,也被称为“One Click Attack”或者Session Riding,通常缩写为CSRF或者XSRF,是一种对网站的恶意利用。
https://www.jianshu.com/p/7f33f9c7997b
XSS (Cross Site Scripting) 跨站点脚本
跨站脚本(XSS)是一种攻击技术,包括将攻击者提供的代码回传到用户的浏览器实例中。浏览器实例可以是一个标准的网络浏览器客户端,也可以是一个嵌入软件产品的浏览器对象,如WinAmp中的浏览器、RSS阅读器或电子邮件客户端。代码本身通常是用HTML/JavaScript编写的,但也可能扩展到VBScript、ActiveX、Java、Flash或任何其他浏览器支持的技术。
当攻击者让用户的浏览器执行他/她的代码时,该代码将在托管网站的安全上下文(或区域)内运行。有了这个级别的权限,代码就有能力读取、修改和传输浏览器所能访问的任何敏感数据。一个跨站脚本用户可能会被劫持他/她的账户(cookie被盗),他们的浏览器被重定向到另一个地方,或者可能显示他们正在访问的网站提供的欺诈性内容。跨站脚本攻击从本质上破坏了用户和网站之间的信任关系。利用从文件系统加载内容的浏览器对象实例的应用程序可能会在本地机器区执行代码,从而使系统受到损害。
Cross-site Scripting (XSS) is an attack technique that involves echoing attacker-supplied code into a user’s browser instance. A browser instance can be a standard web browser client, or a browser object embedded in a software product such as the browser within WinAmp, an RSS reader, or an email client. The code itself is usually written in HTML/JavaScript, but may also extend to VBScript, ActiveX, Java, Flash, or any other browser-supported technology.
When an attacker gets a user’s browser to execute his/her code, the code will run within the security context (or zone) of the hosting web site. With this level of privilege, the code has the ability to read, modify and transmit any sensitive data accessible by the browser. A Cross-site Scripted user could have his/her account hijacked (cookie theft), their browser redirected to another location, or possibly shown fraudulent content delivered by the web site they are visiting. Cross-site Scripting attacks essentially compromise the trust relationship between a user and the web site. Applications utilizing browser object instances which load content from the file system may execute code under the local machine zone allowing for system compromise.
[The Web Application Security Consortium / Cross Site Scripting (webappsec.org)](http://projects.webappsec.org/w/page/13246920/Cross Site Scripting)
reflected XSS
stored XSS
DOM XSS
XML RPC (Remote Procedure call) XML远程过程调用
是一个远程过程调用(远程程序呼叫)的分布式计算协议,通过XML将调用函数封装,并使用HTTP协议作为调用传送机制。
一个XML-RPC消息就是一个请求体为XML的http-post请求,被调用的方法在服务器端执行并将执行结果以xml格式编码后返回。
Anti-Exploitation Capabilities
Address Space Layout Randomization (ASLR)地址空间布局随机化
一种反利用特性,它将内存映射加载到不可预测的位置。ASLR使得攻击者更难将控制重定向到他们引入到应用程序进程地址空间中的代码。
An anti-exploitation feature which loads memory mappings into unpredictable locations. ASLR makes it more difficult for an attacker to redirect control to code that they have introduced into the address space of an application process.
Data Execution Prevention (DEP) 数据执行预防
在现代计算机硬件上执行的现代操作系统的一种反利用特性,它强制对内存页执行非执行权限。DEP阻止内存页同时包含数据和指令,这使得攻击者更难引入和执行代码。
An anti-exploitation feature of modern operating systems executing on modern computer hardware, which
enforces a non-execute permission on pages of memory. DEP prevents pages of memory from containing
both data and instructions, which makes it more difficult for an attacker to introduce and execute code.
Stack Cookie
一种反利用特性,它在函数调用开始时将一个值放在堆栈上,并在函数调用结束时检查该值是否相同。这也被称为"Stack Guard",或者“ Stack Canaries”。
An anti-exploitation feature that places a value on the stack at the start of a function call, and checks that the value is the same at the end of the function call. This is also referred to as Stack Guard, or Stack Canaries.
0-Day Vulnerability & 1-Day Vulnerability & N-Day Vulnerability
Galois/Counter Mode (GCM)
在密码学中,伽罗瓦/计数器模式(GCM)是对称密钥加密块密码的一种操作模式,因其性能而被广泛采用。GCM对最先进的高速通信通道的吞吐率可以用廉价的硬件资源来实现。[1]该操作是一种认证的加密算法,旨在提供数据的真实性(完整性)和保密性。GCM是为块大小为128位的块密码器而定义的。伽罗瓦消息认证码(GMAC)是GCM的一个只认证的变体,可以形成一个增量的消息认证码。GCM和GMAC都可以接受任意长度的初始化向量。
In cryptography, Galois/Counter Mode (GCM) is a mode of operation for symmetric-key cryptographic block ciphers which is widely adopted for its performance. GCM throughput rates for state-of-the-art, high-speed communication channels can be achieved with inexpensive hardware resources.[1] The operation is an authenticated encryption algorithm designed to provide both data authenticity (integrity) and confidentiality. GCM is defined for block ciphers with a block size of 128 bits. Galois Message Authentication Code (GMAC) is an authentication-only variant of the GCM which can form an incremental message authentication code. Both GCM and GMAC can accept initialization vectors of arbitrary length.
from Wikipedia-GCM Mode:Galois/Counter Mode - Wikipedia
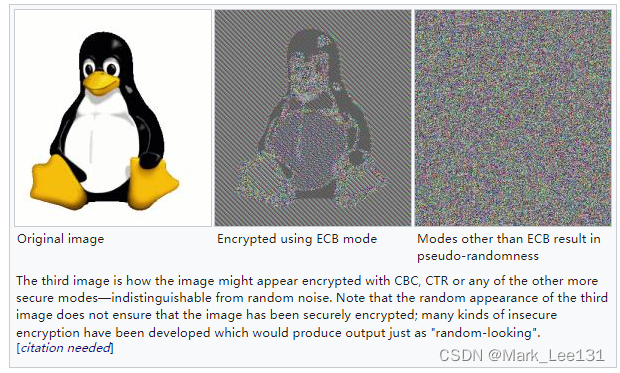
Electronic Code Book (ECB) Mode
加密模式中最简单的(也不再使用)是电子密码本(ECB)模式(以传统的物理密码本命名)。信息被分成若干块,每个块都被单独加密。
The simplest (and not to be used anymore) of the encryption modes is the electronic codebook (ECB) mode (named after conventional physical codebooks. The message is divided into blocks, and each block is encrypted separately.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-3ymb8Vxg-1651734774307)(D:\VSCode_Workspace\Software Security Issues (Especially Java)].assets\1920px-ECB_encryption.svg.png)
这种方法的缺点是缺乏扩散性。由于ECB将相同的明文块加密成相同的密文块,它不能很好地隐藏数据模式。不建议在加密协议中使用ECB。
当ECB模式被用来加密一个使用大面积均匀颜色的位图图像时,可以看到ECB在多大程度上可以在密码文本中留下明文数据模式的一个突出的例子。虽然每个单独的像素的颜色被加密了,但整个图像仍然可以被辨别出来,因为原始图像中相同颜色的像素的模式在加密版本中仍然存在。
The disadvantage of this method is a lack of diffusion. Because ECB encrypts identical plaintext blocks into identical ciphertext blocks, it does not hide data patterns well. ECB is not recommended for use in cryptographic protocols.
A striking example of the degree to which ECB can leave plaintext data patterns in the ciphertext can be seen when ECB mode is used to encrypt a bitmap image which uses large areas of uniform color. While the color of each individual pixel is encrypted, the overall image may still be discerned, as the pattern of identically colored pixels in the original remains in the encrypted version.
Wikipedia: Block cipher mode of operation - Wikipedia
Object deserialization in Java
如果在classpath中存在一个允许触发恶意操作的类,那么不受信任的数据的 Object deserialization 会导致远程代码执行。库的开发者倾向于修复提供潜在恶意触发的类。仍然有一些类被认为可以触发DoS攻击。deserialization是一个敏感的操作,它有大量的漏洞历史。只要在Java虚拟机中发现一个新的漏洞,网络应用就可能变得脆弱。
Object deserialization of untrusted data can lead to remote code execution, if there is a class in classpath that allows the trigger of malicious operation. Libraries developers tend to fix class that provided potential malicious trigger. There are still classes that are known to trigger Denial of Service. Deserialization is a sensible operation that has a great history of vulnerabilities. The web application might become vulnerable as soon as a new vulnerability is found in the Java Virtual Machine.
Serialization in Java
在java中,serialization 是用来将一个对象转换为字节流的方式,它可以通过网络传输到任何其他运行中的JVM,也可以被持久化到磁盘中,该对象可以再次被重建。Java为此提供了serialization 的API。
In java serialization is way used to convert an object into a byte stream which can be transported to any other running JVM through a network or can be persisted into disk and that object can be rebuilt again. Java provides serialization API for this.
可序列化接口是一个标记性接口。标记接口是没有任何方法的,因此,Serializable接口没有任何方法,它给编译器的指示是使用Java Serialization机制来serialize这个对象。
Serializable interface is a marker interface. A marker interface doesn’t have any method i.e. Serializable interface doesn’t have any method, it gives indication to compiler that use Java Serialization mechanism to serialize this object.
Deserialization in Java
Deserialization 是serialization的反向过程。它是一个从 serialized 状态重建对象的过程。
Deserialization is the reverse process of serialization. It is the process of rebuilding object from serialized state.
