基于DNS服务实现分离解析,基于ssh实现两台虚拟机免密登陆
题目
1.通过dns分离技术解析www.qq.com主机ip地址,实现通过内网主机解析为内网服务主机,外网主机解析到外网主机。
2.配置A和B主机实现免密登录
一、注意实现dns分离技术解析最好需要三台虚拟,一台客户端,一台内网,一台外网
1.编辑配置文件
[root@A .ssh]# vim /etc/named.conf
代码如下:
options {
listen-on port 53 { 192.168.159.130; };
directory "/var/named";//正反向解析的区域文件路径
allow-query { any; };
};
#zone "qq.com" IN {
# type master; //缓存服务器 hint
# file "named.qq.com";
#};
# zone "159.168.192.in-addr.arpa" IN {
# type master;
# file "named.192.168.159";
#};
acl"intranet"{ 192.168.159.133; };
acl"internet"{ 192.168.159.135; };
view"intranet"{
match-clients{"intranet";};
zone"qq.com" IN{
type master;
file"named.qq.com";
notify yes;
};
};
view"internet"{
match-clients{"internet";};
zone"qq.com" IN{
type master;
file"named.qq1.com";
};
};
1.修改文件
[root@A .ssh]# vim /var/named/named.qq.com
代码如下:
;主机名 TTL Class type(SOA) 数据
$TTL 1D
@ IN SOA @ admin.admin.com. (
2021071501 ;版本号
1M ;检查时间
1M ;重试时间
1M ;过期时间
1M ) ;否定答案的缓存时长
IN NS dns.qq.com.
IN NS dns1.qq.com.
dns1 IN A 192.168.159.133
dns IN A 192.168.159.130
www IN A 192.168.159.222
aaa IN A 192.168.159.100
bbb IN A 192.168.159.250
ccc IN A 192.168.159.200
~
[root@A .ssh]# vim /var/named/named.qq1.com
代码如下:
;主机名 TTL Class type(SOA) 数据
$TTL 1D
@ IN SOA @ admin.admin.com. (
2021071501 ;版本号
1M ;检查时间
1M ;重试时间
1M ;过期时间
1M ) ;否定答案的缓存时长
IN NS dns.qq.com.
IN NS dns1.qq.com.
dns1 IN A 192.168.159.133
dns IN A 192.168.159.130
www IN A 192.168.159.111
aaa IN A 192.168.159.100
bbb IN A 192.168.159.200
ccc IN A 192.168.159.101
2.到内网主机测试
代码如下(示例):
[root@B .ssh]# nslookup
> server 192.168.159.130
Default server: 192.168.159.130
Address: 192.168.159.130#53
> www.qq.com
Server: 192.168.159.130
Address: 192.168.159.130#53
Name: www.qq.com
Address: 192.168.159.222 -----注意看IP地址 222
>
3.到外网主机测试
代码如下(示例):
[root@localhost ~]# nslookup
> server 192.168.159.130
Default server: 192.168.159.130
Address: 192.168.159.130#53
> www.qq.com
Server: 192.168.159.130
Address: 192.168.159.130#53
Name: www.qq.com
Address: 192.168.159.111 -----IP地址111
>
通过内外网主机访问同一个域名,解析地址一个为192.168.159.222 一个为192.168.111 如果相同则不成功,注意看前面博主的配置文件,看是否有误
二、配置A和B主机实现免密登录
1.A主机配置
代码如下(示例):
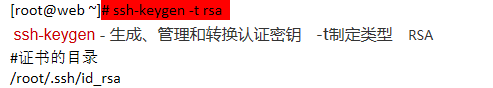
[root@localhost ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:IW1jdPT2JXskNMxqXnFPHgNTUNKXn09lLlUG//auEA0 root@localhost.localdomain
The key's randomart image is:
+---[RSA 3072]----+
| ..o BX+=|
| o . . .*OB|
| . * E.oO%|
| + o .o+oBB|
| S o..+o=|
| .. oo|
| . .|
| . . |
| ...|
+----[SHA256]-----+
[root@localhost ~]# cd /root/.ssh
[root@localhost .ssh]# ll
total 12
-rw-r--r--. 1 root root 477 Jul 15 05:29 authorized_keys
-rw-------. 1 root root 2610 Jul 15 07:41 id_rsa
-rw-r--r--. 1 root root 580 Jul 15 07:41 id_rsa.pub
[root@localhost .ssh]# ssh-copy-id -i /root/.ssh/id_rsa.pub root@192.168.159.133
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.159.133 (192.168.159.133)' can't be established.
ECDSA key fingerprint is SHA256:pSSlhWFEMJ/IZeb0fJ4omw++WD2ASZmR3espg5uLDOw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.159.133's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.159.133'"
and check to make sure that only the key(s) you wanted were added.
[root@localhost .ssh]# ssh 192.168.159.133 -----无需输入密码,即可登陆B主机
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last login: Thu Jul 15 07:08:33 2021 from 192.168.159.1
[root@B ~]# exit
2.B主机配置与A大致一样
代码如下(示例):
[root@B .ssh]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:uHuVsEM7PX+6mkLWkxcNfmuXlo07oOTHCGZzgILHGrc root@B
The key's randomart image is:
+---[RSA 3072]----+
| |
| . |
| o . . o |
| o = ..+ o o |
| = o..SB o o o+|
| . E .% @ o ++o|
| .= X O o.o |
| .o +.+ + |
| .. .ooo+ . |
+----[SHA256]-----+
[root@B .ssh]#
[root@B .ssh]# ll
total 16
-rw-------. 1 root root 1160 Jul 15 07:44 authorized_keys
-rw-------. 1 root root 2590 Jul 15 07:47 id_rsa
-rw-r--r--. 1 root root 560 Jul 15 07:47 id_rsa.pub
-rw-r--r--. 1 root root 177 Jul 15 05:12 known_hosts
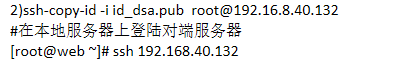
[root@B .ssh]# ssh-copy-id -i id_rsa.pub root@192.168.159.130
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.159.130's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.159.130'"
and check to make sure that only the key(s) you wanted were added.
[root@B .ssh]# ssh 192.168.159.130 ---无需输入密码登陆A主机
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last login: Thu Jul 15 07:46:36 2021 from 192.168.159.133
[root@A ~]# exit
总结
提示:这里对文章进行总结:
通过dns技术实现不同主机解析出统一域名不一样。注意有条件可以用用三台虚拟机,两台也行。
实现免密登陆主要通过