1.通过dns分离技术解析www.qq.com主机ip地址,实现通过内网主机解析为内网服务主机,外网主机解析到外网主机。
服务端:
【1】挂载、关闭防火墙和selinux以及下载和开启DNS服务
[root@localhost ~]# mount /dev/sr0 /mnt
[root@localhost ~]# systemctl stop firewalld
[root@localhost ~]# setenforce 0
[root@localhost ~]# yum install bind -y
[root@localhost ~]# systemctl start named
【2】更改配置自定义解析域
[root@localhost ~]# vim /etc/named.conf
options {
listen-on port 53 { 192.168.43.128; };
directory "/var/named";
allow-query { any; };
};
acl"内网"{192.168.43.129; };
acl"外网"{192.168.43.130; };
view"内网"{
match-clients{"内网"; };
zone "qq.com" IN {
type master;
file "named.qq.com";
notify yes;
};
};
view"外网"{
match-clients{"外网"; };
zone "qq.com" IN {
type master;
file "named.qq1.com";
};
};
【3】正向解析文件(区域数据文件)资源记录包含的元素
[root@localhost ~]# vim /var/named/named.qq.com
$TTL 1D
@ IN SOA @ rname.invalid. (
2021071401 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.qq.com.
dns IN A 192.168.43.128
www IN A 192.168.43.100
aaa IN A 192.168.43.88
bbb IN A 192.168.43.66
[root@localhost ~]# vim /var/named/named.qq1.com
$TTL 1D
@ IN SOA @ rname.invalid. (
2021071401 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.qq.com.
dns IN A 192.168.43.128
www IN A 192.168.43.200
aaa IN A 192.168.43.188
bbb IN A 192.168.43.166
【4】重启DNS服务
[root@localhost ~]# systemctl restart named
客户端:
【1】挂载、关闭防火墙和selinux以及下载和开启DNS服务
[root@localhost ~]# mount /dev/sr0 /mnt
[root@localhost ~]# systemctl stop firewalld
[root@localhost ~]# setenforce 0
[root@localhost ~]# yum install bind -y
[root@localhost ~]# systemctl start named
【2】绑定DNS服务器
[root@localhost ~]# nmcli connection modify ens160 ipv4.dns 192.168.43.128
[root@localhost ~]# vim /etc/resolv.conf
; generated by /usr/sbin/dhclient-script
search localdomain
nameserver 192.168.43.128
【3】测试
192.168.43.129:
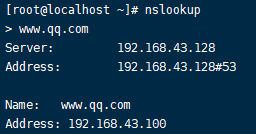
192.168.43.130:
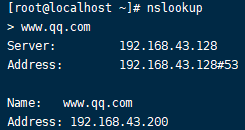
可以看到测试结果两台不同IP地址的客户端解析的IP地址结果不一致,实验成功
2.配置A和B主机实现免密登录
【1】在A主机创建秘钥:
[root@localhost ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:Y8wufjXZnjZ4+f7vGYyPibEBHwXTBSM/dF42Cs4MYOE root@localhost.localdomain
The key's randomart image is:
+---[RSA 3072]----+
| +o. =.+o+o|
| o = B.=.o|
| E + = . |
| o . . |
| S. + |
| o .* o o |
| . .. B + o |
| . .. . % + o|
| .. = *o==|
+----[SHA256]-----+
【2】检查秘钥创建情况
[root@localhost ~]# cd /root/.ssh
[root@localhost .ssh]# ll
总用量 12
-rw-------. 1 root root 2610 7月 17 06:37 id_rsa
-rw-r--r--. 1 root root 580 7月 17 06:37 id_rsa.pub
-rw-r--r--. 1 root root 176 7月 15 23:58 known_hosts
可看出已经创建成功
【3】在B主机上创建.ssh隐藏目录存放对方秘钥
[root@localhost ~]# mkdir .ssh.
[root@localhost ~]# cd .ssh
[root@localhost .ssh]# ll
总用量 0 #通过检查,该隐藏目录一开始为空
【4】传递公钥给B主机并进行改名操作
[root@localhost ~]# scp .ssh/id_rsa.pub root@192.168.43.129:/root/.ssh/authorized_keys #改名为对方公钥默认名字authorized_keys
root@192.168.43.129's password: #此处输入redhat(B主机root用户的密码)
id_rsa.pub 100% 580 459.9KB/s 00:00 #传输成功
【5】查看B主机.ssh隐藏目录接收秘钥后的情况
[root@localhost ~]# cd .ssh
[root@localhost .ssh]# ll
总用量 4
-rw-r--r-- 1 root root 580 7月 17 06:46 authorized_keys
可看出秘钥已经接收成功
【6】在A主机上测试
[root@localhost ~]# ssh 192.168.43.129
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last login: Sat Jul 17 06:42:18 2021 from 192.168.43.128
[root@localhost ~]# exit
注销
Connection to 192.168.43.129 closed.
[root@localhost ~]#
可看出已实现免密登录
【7】B主机反过来相应步骤一致,不作演示