1 前提
已通过kubeadm搭建集群环境,具体可参考——使用kubeadm部署k8s 1.15集群——基于CentOS 7
2 创建dashboard应用
直接使用官网提供的yaml文件,
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.2.0/aio/deploy/recommended.yaml
执行成功后,查看创建的pod资源,
[root@master ~]# kubectl get pod -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-856586f554-zfczc 1/1 Running 1 2d12h
kubernetes-dashboard-78c79f97b4-wthqj 1/1 Running 1 2d12h
如果创建失败,用describe命令看下是不是镜像拉取问题。
3 访问
总的来说有以下几种方式,
- kubectl proxy
- kubectl port-forward
- NodePort
- API Server
- Ingress
3.1 kubectl proxy
直接在master节点执行kubectl proxy即可,会有如下输出,
[root@master ~]# kubectl proxy
Starting to serve on 127.0.0.1:8001
这时就能通过以下链接访问,
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/
但对于我在vmware的情况,直接在物理机浏览器访问是不行的,因为这个localhost指向的是物理机,不是我的虚拟机,因次我们可以这样做,
[root@master ~]# kubectl proxy --address='192.168.0.110' -p 8888 --disable-filter=true
W0725 06:55:04.485719 78503 proxy.go:162] Request filter disabled, your proxy is vulnerable to XSRF attacks, please be cautious
Starting to serve on 192.168.0.110:8888
其中,
–address指定192.168.0.110是master节点ip,
-p指定端口号,
disable-filter=true表示禁用请求过滤功能,否则我们的请求会被拒绝
这时再通过以下链接访问,
http://192.168.0.110:8888/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/
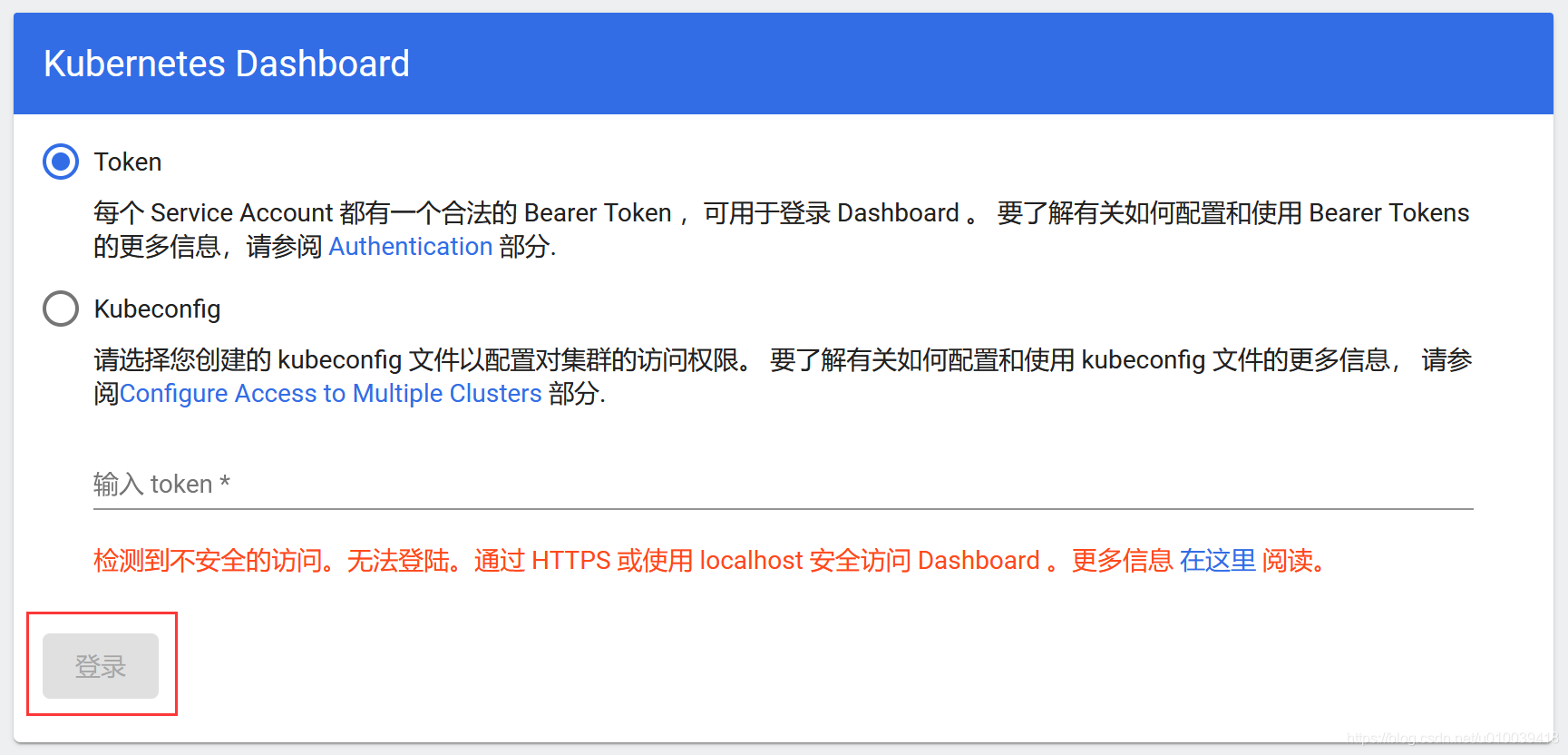 但还是有问题,你会发现这个时候登录按钮是灰色的,因为由于安全考虑,我们只能通过以下三种方式访问k8s的服务,
但还是有问题,你会发现这个时候登录按钮是灰色的,因为由于安全考虑,我们只能通过以下三种方式访问k8s的服务,
- http://localhost/…
- http://127.0.0.1/…
- https://<domain_name>/…
真要使用这种方式访问,可以在虚拟机开启图形界面登录,然后用虚拟机自带的浏览器访问,这里我们就不测试。
3.2 kubectl port-forward
这个和kubectl proxy很相似,但是可以大大简化url,它的复杂度都在执行命令的时候,
[root@master ~]# kubectl port-forward --address='192.168.0.110' -n kubernetes-dashboard service/kubernetes-dashboard 8080:443
Forwarding from 192.168.0.110:8080 -> 8443
Handling connection for 8080
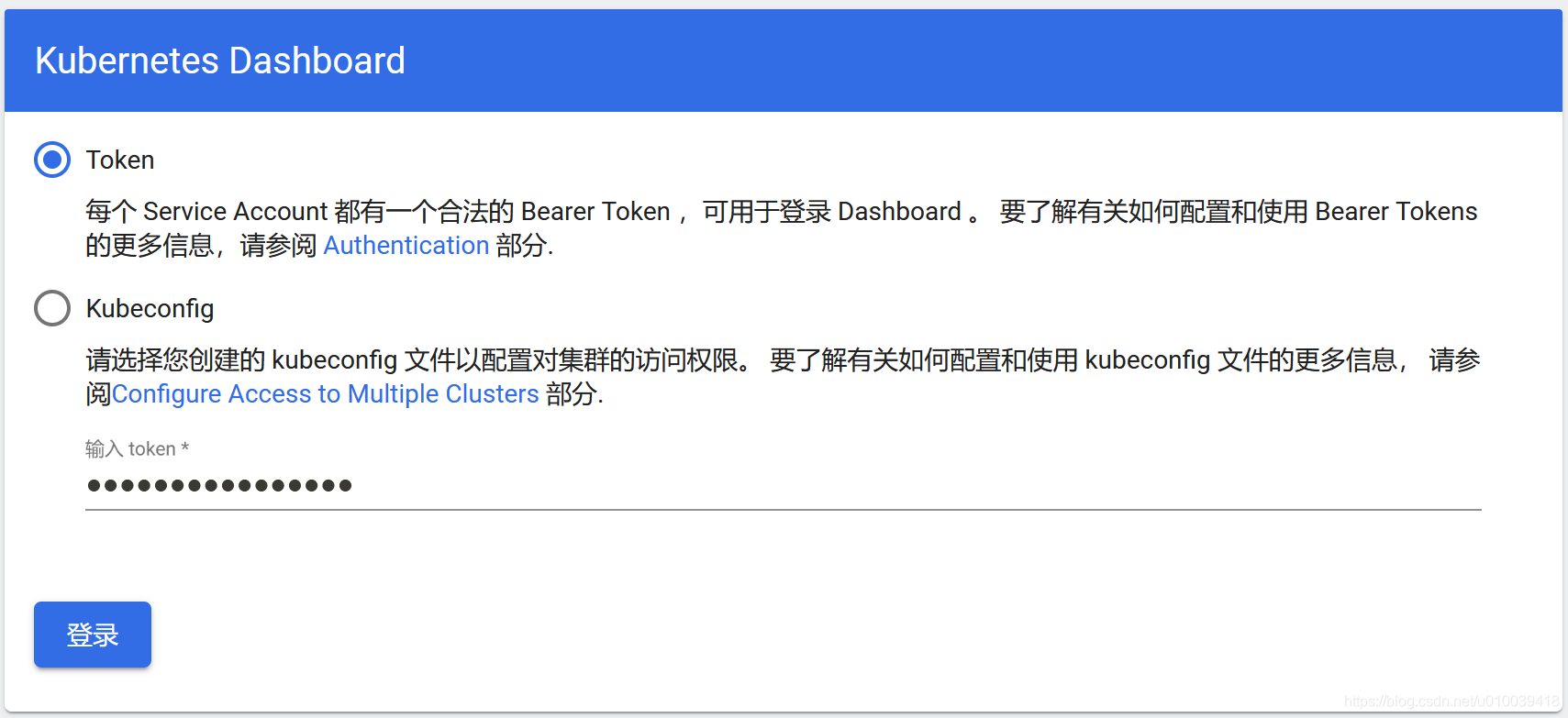
同样设置需要forward的地址,也就是master地址,以及dashboard对应的命名空间和服务名称,最后是映射的端口号,所以最终的结果就是,把dashboard服务forward到address的8080端口,因此我们可以通过以下方式访问,
https://192.168.0.110:8080
3.3 NodePort
这种方式需要修改dashboard服务的yaml文件,增加NodePort属性,
[root@master home]# kubectl patch svc -n kubernetes-dashboard kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}'
service/kubernetes-dashboard patched
然后我们查看对应的port,以及dashboard处于哪个node节点,
[root@master home]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.99.237.14 <none> 8000/TCP 5d12h
kubernetes-dashboard NodePort 10.101.50.252 <none> 443:31722/TCP 5d12h
[root@master home]# kubectl get pod -n kubernetes-dashboard -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
dashboard-metrics-scraper-856586f554-zfczc 1/1 Running 1 5d12h 10.244.1.15 node1 <none> <none>
kubernetes-dashboard-78c79f97b4-wthqj 1/1 Running 1 5d12h 10.244.2.11 node2 <none> <none>
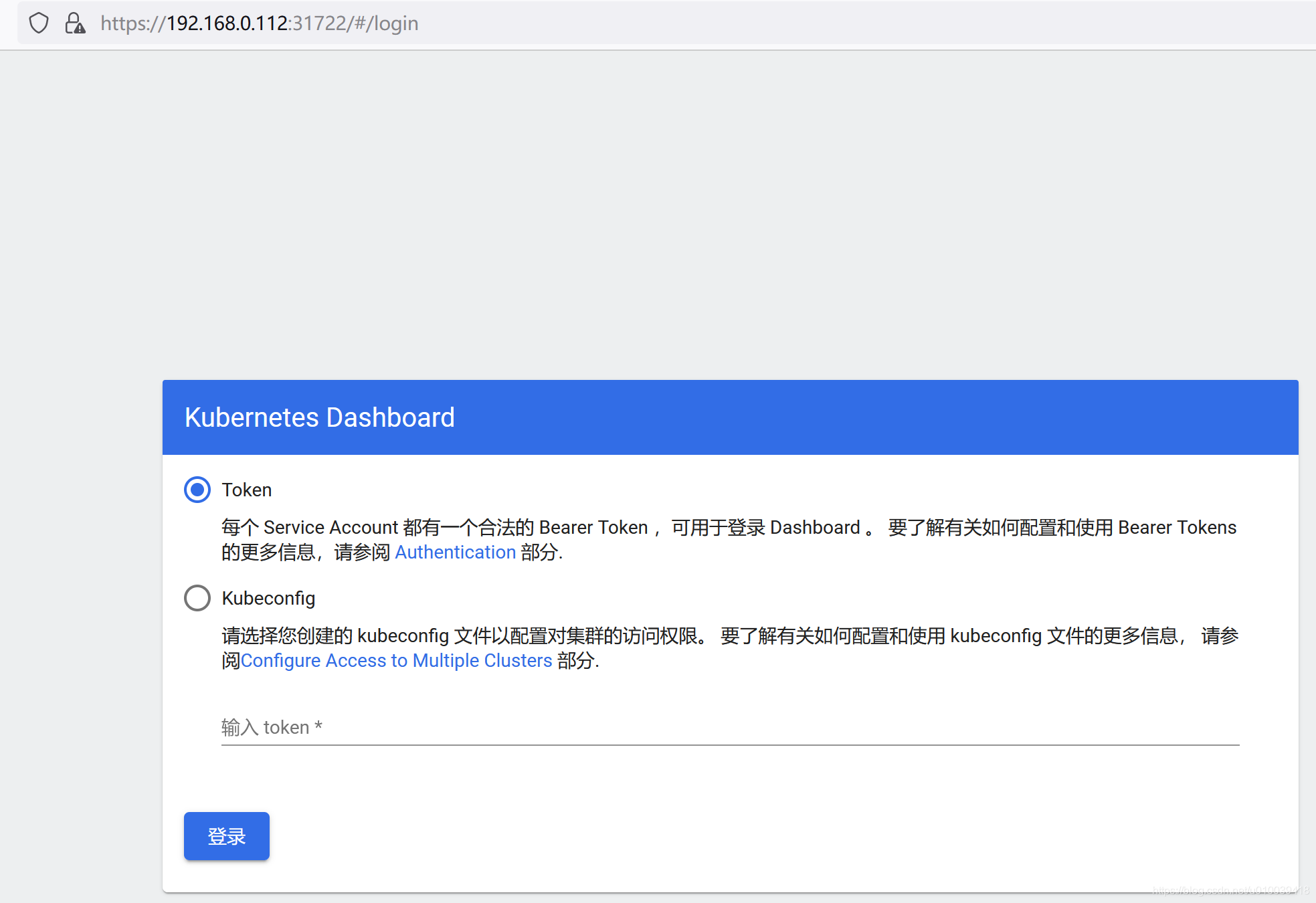
可见端口为31722,运行在node2上,因此需要通过node2的ip去访问,
https://192.168.0.112:31722
3.4 API Server
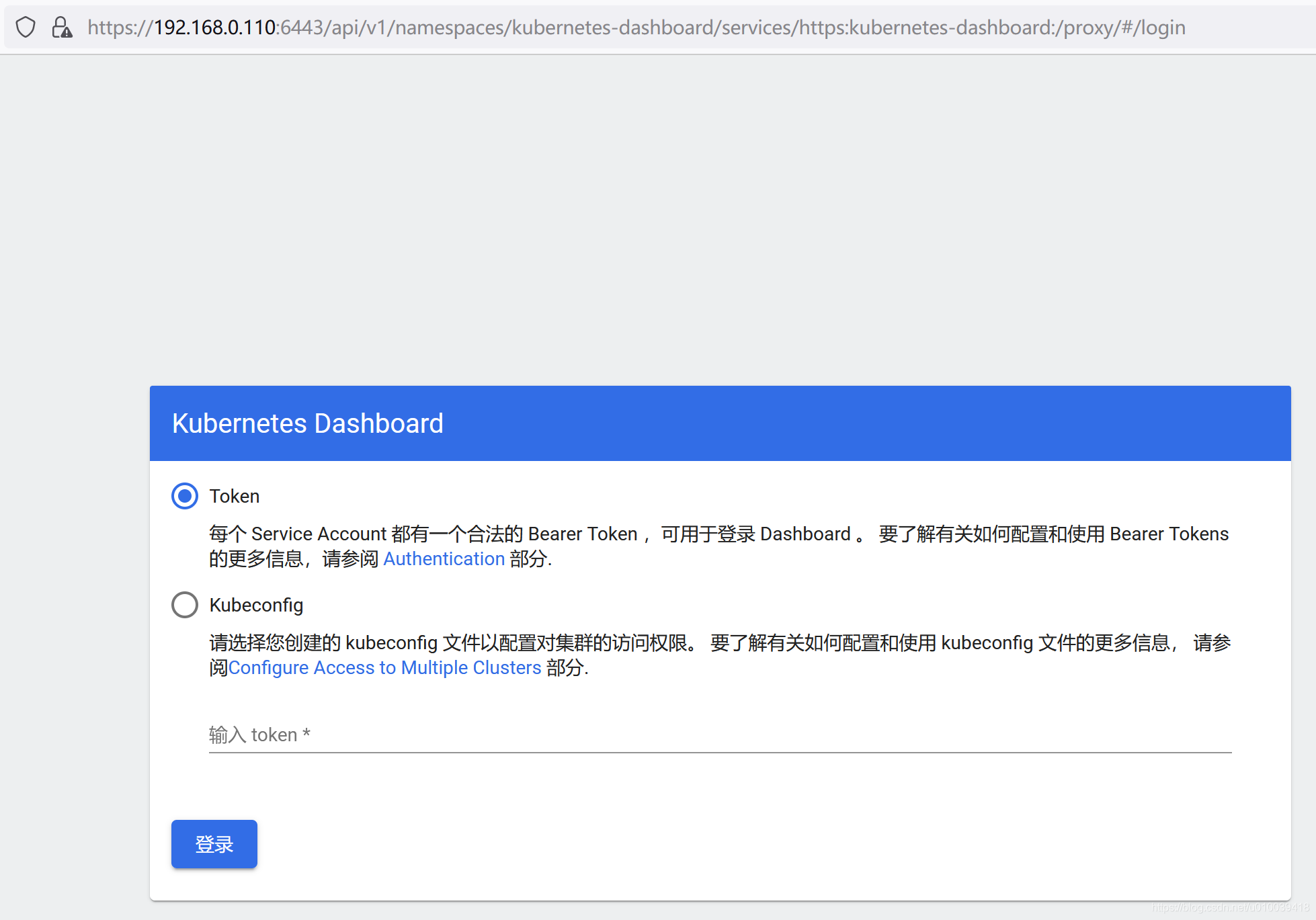
如果master节点上的api-server可以从外部访问,那我们可以直接通过以下url访问,
https://192.168.0.110:6443/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/#/login
其中192.168.0.110是master节点ip,6443是api-server监听端口,
[root@master home]# netstat -ntlp | grep 6443
tcp6 0 0 :::6443 :::* LISTEN 75164/kube-apiserve
3.5 Ingress
这个我们下次再说~~
4 登录
进入登录页面后,有两种登录方式,
- Token
- Kubeconfig
4.1 以token方式登录
先获取对应的token,
[root@master home]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
...
kubernetes-dashboard-token-79mxs kubernetes.io/service-account-token 3 5d12h
[root@master home]# kubectl describe secret -n kubernetes-dashboard kubernetes-dashboard-token-79mxs
...
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImdZLUM2OENuNDJJNnQ0WUdBV0Y2NFhIZzVKQmZQZlotMTZKcEFTZ0hoNncifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi03OW14cyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjJhZjg3MGU0LTQ1ZjMtNDExYy04YmQzLWJhMTEyYjc2NjE5MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.BLdxnP8dZVckvJvXTn-S4ta6kMc5oEATrs3BB-Nc-I3rjapAHp198i7cDhXV_k-YotYtl7fC5-SpImUoRsKZfJYQTLKwZwZ5fvpZvaCTM2uItIoVsl440AXwHy2HtOrzeCVwoHTeABeV395FTHwyCM9beJG0v9sTK2dOIVbchq6BfegvXgE_HkglzqRCLkiUBw20G45jzgXvB_yio5cA65rGUeMICXhDmVkegIsXT0aMK4YJOsFk3u1WLZ2K43v7kS3vEdYTkBQU8mKQLT0h-btVxOR1tt4N2osxfaLbBNlyFjj_hCNePjTUXzDLkqgfM1rkMObxqp1uHIm6n0JHpQ
使用该token登录后,你会发现右上角有很多消息,点开后是各种报错,
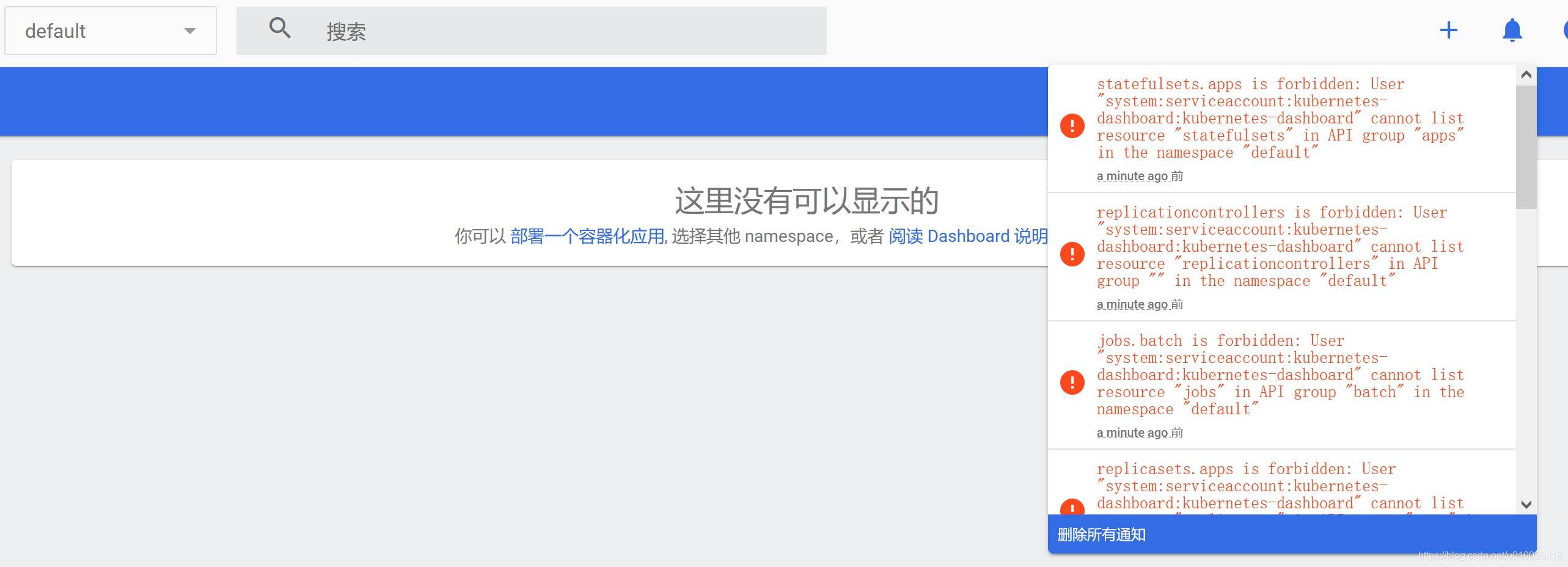 这其实就是因为我们从官网获取的dashboard yaml文件中,给dashboard这个role的权限不够,导致我们无法获取k8s集群状态。
这其实就是因为我们从官网获取的dashboard yaml文件中,给dashboard这个role的权限不够,导致我们无法获取k8s集群状态。
有两种解决方案,
- 自己创建一个有admin权限的role
- 修改yaml文件,重新部署dashboard
4.1.1 创建新的role
- 创建dashboard admin服务账号
kubectl create serviceaccount dashboard-admin -n kubernetes-dashboard
- 绑定用户为集群管理用户
kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-admin
- 获取tocken,secret名字会以我们刚创建的serviceaccount开头
[root@master home]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
dashboard-admin-token-hsrr4 kubernetes.io/service-account-token 3 4d11h
...
[root@master home]# kubectl describe secret -n kubernetes-dashboard dashboard-admin-token-hsrr4
获取新的token,登录后,就能查看整个集群的资源,
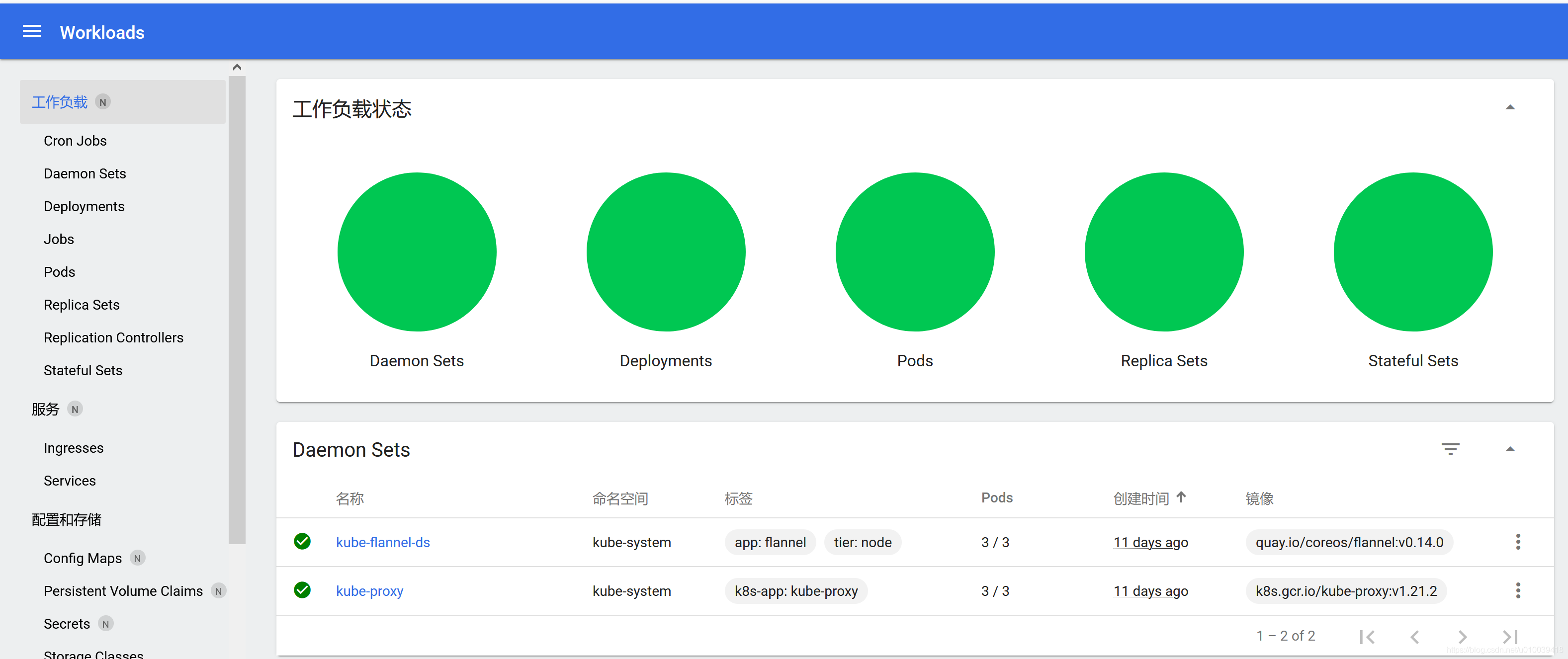
4.1.2 修改yaml文件
将ClusterRoleBinding部分中roleRef的kubernetes-dashboard修改为cluster-admin,这样kubernetes-dashboard这个service-account也就具有了集群admin权限,
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
#name: kubernetes-dashboard
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
然后重新应用yaml文件即可,
kubectl apply -f kube-dashboard.yml
接着就是获取token,这时secret名字会以kubernetes-dashboard这个service-account开头,
[root@master home]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
...
kubernetes-dashboard-token-rg8sn kubernetes.io/service-account-token 3 33h
[root@master home]# kubectl describe secret -n kubernetes-dashboard kubernetes-dashboard-token-rg8sn
Name: kubernetes-dashboard-token-rg8sn
...
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImdZLUM2OENuNDJJNnQ0WUdBV0Y2NFhIZzVKQmZQZlotMTZKcEFTZ0hoNncifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1yZzhzbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjUzNmY3YmI2LWI4ZmItNGEzMi05MjBmLTM5MTVjZjY3YmU0ZCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.qaunGz5APl2fy-7Vqd4GBcUEKQAa4GwLq9cwvAFlmsOfWvPFzyNVo6kblw_98rqkbJzyhL7ahepCXw4PpFti0DWmhldHgLrx2DxtUhkOfjmsaGikRLCVrxl0RAgQmnALbsNzZluSin_N7ufxu4CjKQmCFOg_wo-yBndUUMuDOX4bki3F3UufOQ53dTMRqu1eITyH4150KhaNcuAqYzp8QSl7-Npxd2WCkXKr8XpHOhBmJpFTKC6CDdghyp4wKeep_Wf-e9U4v0C4qBbpgTI8pFtTUV-3C7-ZVv2mhgKPdxTkY8ZPJ5zurew01hPxioBH-QIQTqUSH3DknHmuCCS4Wg
4.2 以Kubeconfig方式登录
需要生成Kubeconfig文件,
- 获取并设置token
DASHBOARD_TOKEN=$(kubectl get secret -n kubernetes-dashboard kubernetes-dashboard-token-rg8sn -o jsonpath={.data.token}|base64 -d)
其中kubernetes-dashboard-token-rg8sn就是有用集群admin权限的dashboard secret,这里其实和上面获取token一样,只是把它设置到变量中,方便后续使用。
- 设置集群名称
kubectl config set-cluster kubernetes --server=192.168.0.110:6443 --kubeconfig=/root/dashbord-admin.conf
其中,
kubernetes 就是我们设置的集群名称,当然,你可以设置为你想要的其他名字
--server后面设置的是kube-apiserver的ip和监听端口,一般就是master的ip
--kubeconfig后面设置的是kubeconfig存放位置,根据需要自己调整
- 设置登录凭证
kubectl config set-credentials dashboard-admin --token=$DASHBOARD_TOKEN --kubeconfig=/root/dashbord-admin.conf
其中,
dashboard-admin可理解为登录用户名
--token就是我们第一步获取的token
- 设置context
kubectl config set-context dashboard-admin@kubernetes --cluster=kubernetes --user=dashboard-admin --kubeconfig=/root/dashbord-admin.conf
其中,
dashboard-admin@kubernetes是我们设置的contex名称,可以根据自己需求调整
--cluster和--user分别指定集群名称和登录用户名,这个要和我们前面设置的保持一致
- 设置当前contex
kubectl config use-context dashboard-admin@kubernetes --kubeconfig=/root/dashbord-admin.conf
这里dashboard-admin@kubernetes,就是我们上一步里设置的contex名称,这里就是指定我们当前这个kubeconfig使用哪个context,毕竟集群可能会存在多个contex,关联的不同用户和登录凭证
最后我们就能获取到用于登录的kubeconfig文件,
apiVersion: v1
clusters:
- cluster:
server: 192.168.0.110:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: dashboard-admin
name: dashboard-admin@kubernetes
current-context: dashboard-admin@kubernetes
kind: Config
preferences: {}
users:
- name: dashboard-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImdZLUM2OENuNDJJNnQ0WUdBV0Y2NFhIZzVKQmZQZlotMTZKcEFTZ0hoNncifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1yZzhzbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjUzNmY3YmI2LWI4ZmItNGEzMi05MjBmLTM5MTVjZjY3YmU0ZCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.qaunGz5APl2fy-7Vqd4GBcUEKQAa4GwLq9cwvAFlmsOfWvPFzyNVo6kblw_98rqkbJzyhL7ahepCXw4PpFti0DWmhldHgLrx2DxtUhkOfjmsaGikRLCVrxl0RAgQmnALbsNzZluSin_N7ufxu4CjKQmCFOg_wo-yBndUUMuDOX4bki3F3UufOQ53dTMRqu1eITyH4150KhaNcuAqYzp8QSl7-Npxd2WCkXKr8XpHOhBmJpFTKC6CDdghyp4wKeep_Wf-e9U4v0C4qBbpgTI8pFtTUV-3C7-ZVv2mhgKPdxTkY8ZPJ5zurew01hPxioBH-QIQTqUSH3DknHmuCCS4Wg
参考:
- https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/
- https://github.com/kubernetes/dashboard/blob/master/docs/user/accessing-dashboard/README.md