Keycloak在集群中高可用部署
Keycloak集群部署
keycloak docker image中对于集群的相关描述
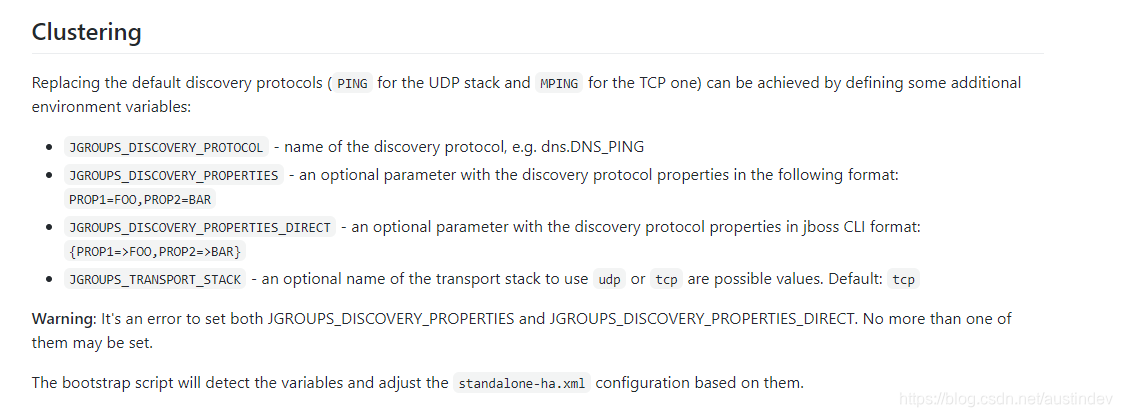
DNS_PING 发现模式
采用 DNS_PING发现的配置如下:
- name: JGROUPS_DISCOVERY_PROTOCOL
value: dns.DNS_PING
- name: JGROUPS_DISCOVERY_PROPERTIES
value: 'dns_query=keycloak-ha-svc.kulchao-public.svc.cluster.local'
但是在该模式下,会出现访问失败的问题
在Red_Hat找到了已知问题,对应的链接也没有很好的解决方式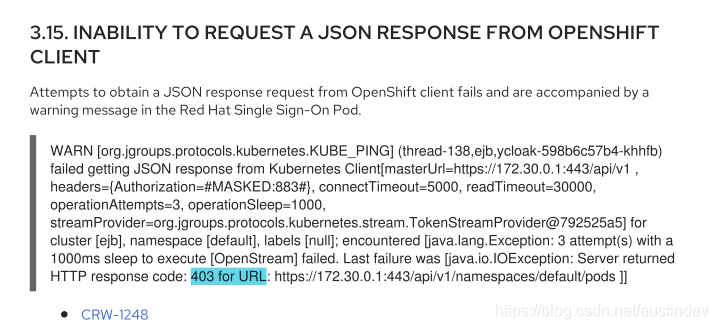
https://issues.redhat.com/browse/CRW-1248
所以暂时决定不使用该模式
KUBE_PING
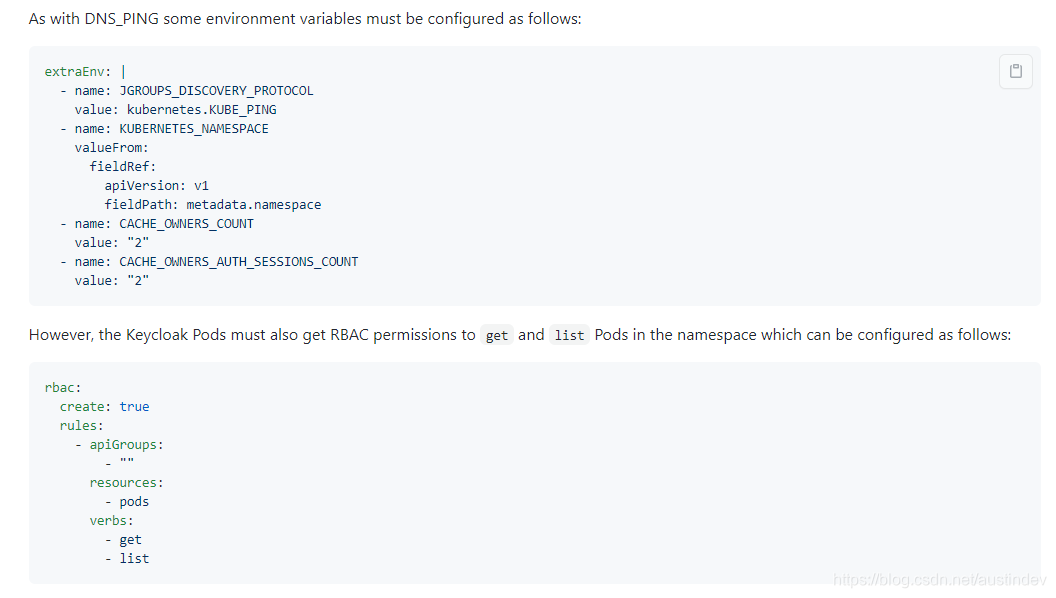
采用KUBE_PING方案,则需要配置下面两项
- name: JGROUPS_DISCOVERY_PROTOCOL
value: kubernetes.KUBE_PING
- name: KUBERNETES_NAMESPACE
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
K8S serveraccount 及 role RBAC 配置
创建ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: my-pod-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
创建ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: pod-default-reader
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: my-pod-reader
subjects:
- kind: ServiceAccount
name: default
namespace: product-public
keycloak 主要的环境变量如下:
- name: JGROUPS_DISCOVERY_PROTOCOL
value: kubernetes.KUBE_PING
- name: KUBERNETES_NAMESPACE
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
- name: CACHE_OWNERS_COUNT
value: "2"
- name: CACHE_OWNERS_AUTH_SESSIONS_COUNT
value: "2"