前言:Docker直接开启2375端口是不安全的,别人只要连上之后就可以任意操作,下面是开启Docker的TLS和CA认证方法,并使用Jenkins和Portainer连接。
一、生成证书
查看服务器主机名
hostname
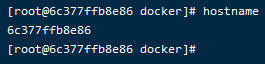
auto-generate-docker-tls-ca.sh
# !/bin/bash
# 一键生成TLS和CA证书
# Create : 2021-08-25
# Update : 2021-08-25
# @Autor : wuduoqiang
# 服务器主机名
SERVER="6c377ffb8e86"
# 密码
PASSWORD="2cx&BUjsV4u%3TW9"
# 国家
COUNTRY="CN"
# 省份
STATE="海南省"
# 城市
CITY="海口市"
# 机构名称
ORGANIZATION="小强崽公司"
# 机构单位
ORGANIZATIONAL_UNIT="小强崽单位"
# 邮箱
EMAIL="875667601@qq.com"
# 生成CA密钥
openssl genrsa -aes256 -passout pass:$PASSWORD -out ca-key.pem 2048
# 生成CA证书
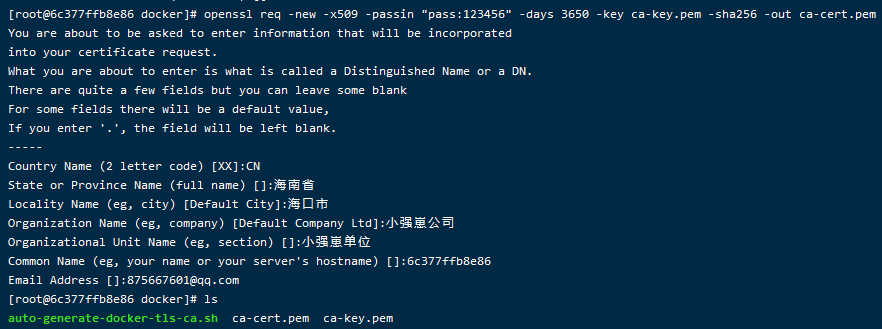
openssl req -new -x509 -passin "pass:$PASSWORD" -days 3650 -key ca-key.pem -sha256 -out ca-cert.pem -subj "/C=$COUNTRY/ST=$STATE/L=$CITY/O=$ORGANIZATION/OU=$ORGANIZATIONAL_UNIT/CN=$SERVER/emailAddress=$EMAIL"
# 生成服务端密钥
openssl genrsa -out server-key.pem 2048
# 生成服务端证书签名的请求文件
openssl req -subj "/CN=$SERVER" -new -key server-key.pem -out server-req.csr
# 生成服务端证书
openssl x509 -req -days 3650 -in server-req.csr -CA ca-cert.pem -CAkey ca-key.pem -passin "pass:$PASSWORD" -CAcreateserial -out server-cert.pem
# 生成客户端密钥
openssl genrsa -out client-key.pem 2048
# 生成客户端证书签名的请求文件
openssl req -subj '/CN=client' -new -key client-key.pem -out client-req.csr
# 生成客户端证书
sh -c 'echo "extendedKeyUsage=clientAuth" >> extfile.cnf'
openssl x509 -req -days 3650 -in client-req.csr -CA ca-cert.pem -CAkey ca-key.pem -passin "pass:$PASSWORD" -CAcreateserial -out client-cert.pem -extfile extfile.cnf
# 更改密钥权限
chmod 0400 ca-key.pem server-key.pem client-key.pem
# 更改证书权限
chmod 0444 ca-cert.pem server-cert.pem client-cert.pem
# 删除无用文件
# rm ca-cert.srl client-req.csr server-req.csr extfile.cnf
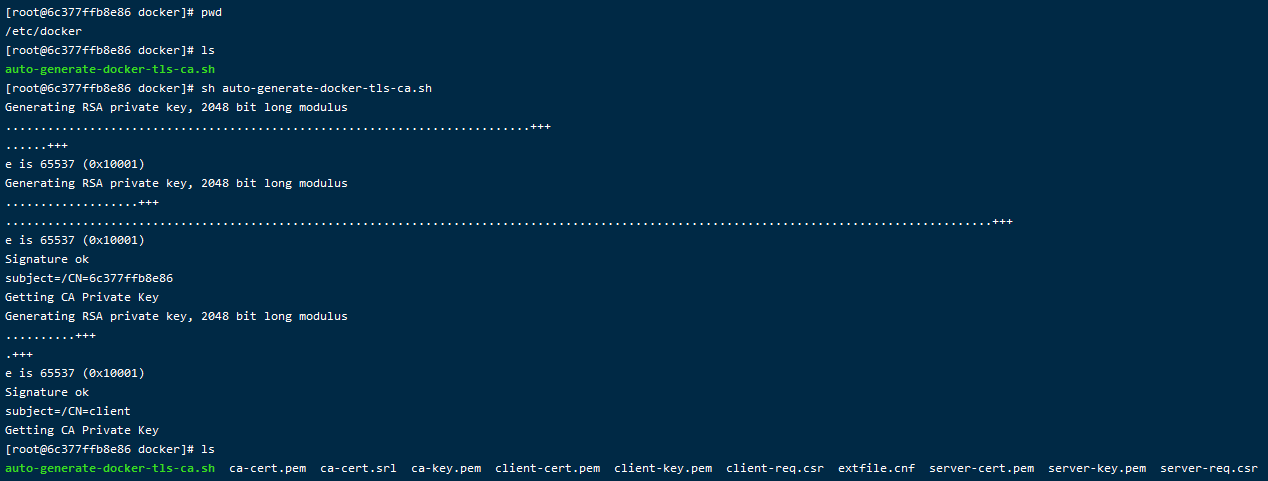
文件说明
ca.srl:CA签发证书的序列号记录文件
ca-cert.pem:CA证书
ca-key.pem:CA密钥
server-key.pem:服务端密钥
server-req.csr:服务端证书签名请求文件
server-cert.pem:服务端证书
client-key.pem:客户端密钥
extfile.cnf:客户端证书扩展配置文件
client-req.csr:客户端证书签名请求文件
client-cert.pem:客户端证书
命令解析
# -subj /C=$COUNTRY/ST=$STATE/L=$CITY/O=$ORGANIZATION/OU=$ORGANIZATIONAL_UNIT/CN=$SERVER/emailAddress=$EMAIL
-subj 是 指定证书申请人的信息
C 是 Country Name
ST 是 State or Province Name
L 是 Locality Name
O 是 Organization Name
OU 是 Organizational Unit Name
CN 是 Common Name
emailAddress 是 Email Address
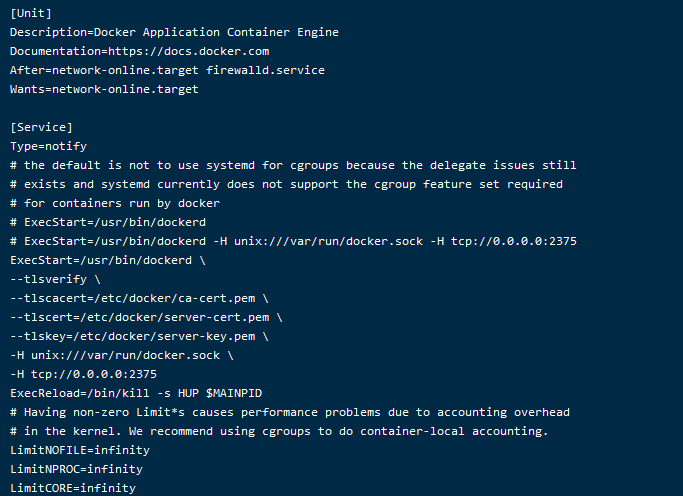
二、开启远程
开启Docker的远程访问API
# 编辑文件
vim /etc/systemd/system/docker.service
# 修改内容,注意证书的指定位置
ExecStart=/usr/bin/dockerd \
--tlsverify \
--tlscacert=/etc/docker/ca-cert.pem \
--tlscert=/etc/docker/server-cert.pem \
--tlskey=/etc/docker/server-key.pem \
-H unix:///var/run/docker.sock \
-H tcp://0.0.0.0:2375
# 重启服务
systemctl daemon-reload && systemctl restart docker
如果没有密钥和证书是连不上的
docker -H 192.168.8.248:2375 images
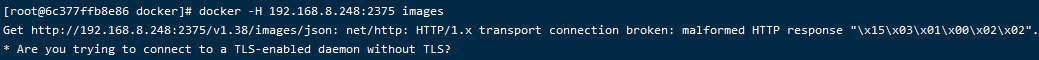
使用主机名没有密钥和证书也是连不上的
docker -H 6c377ffb8e86:2375 images
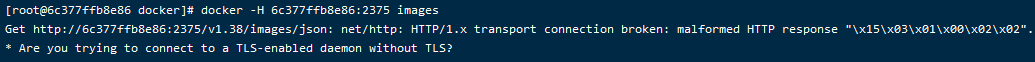
加上密钥和证书没有使用主机名也是连不上
curl https://192.168.8.248:2375/info --cert ./client-cert.pem --key ./client-key.pem --cacert ./ca-cert.pem
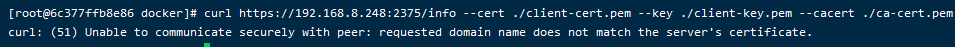
加上密钥和证书并且使用主机名就能访问
curl https://6c377ffb8e86:2375/info --cert ./client-cert.pem --key ./client-key.pem --cacert ./ca-cert.pem
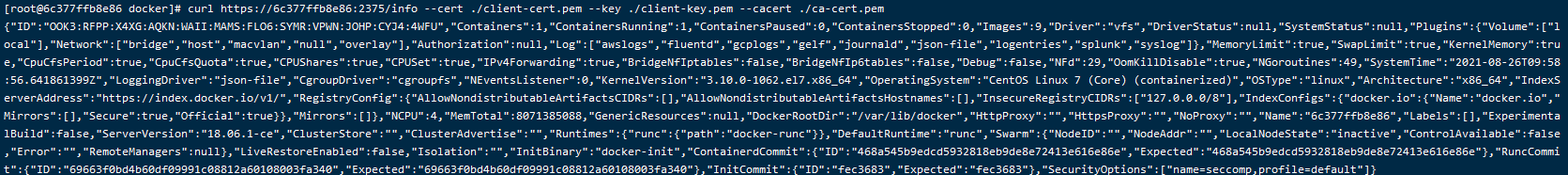
三、远程连接
3.1 Jenkins连接
添加凭证
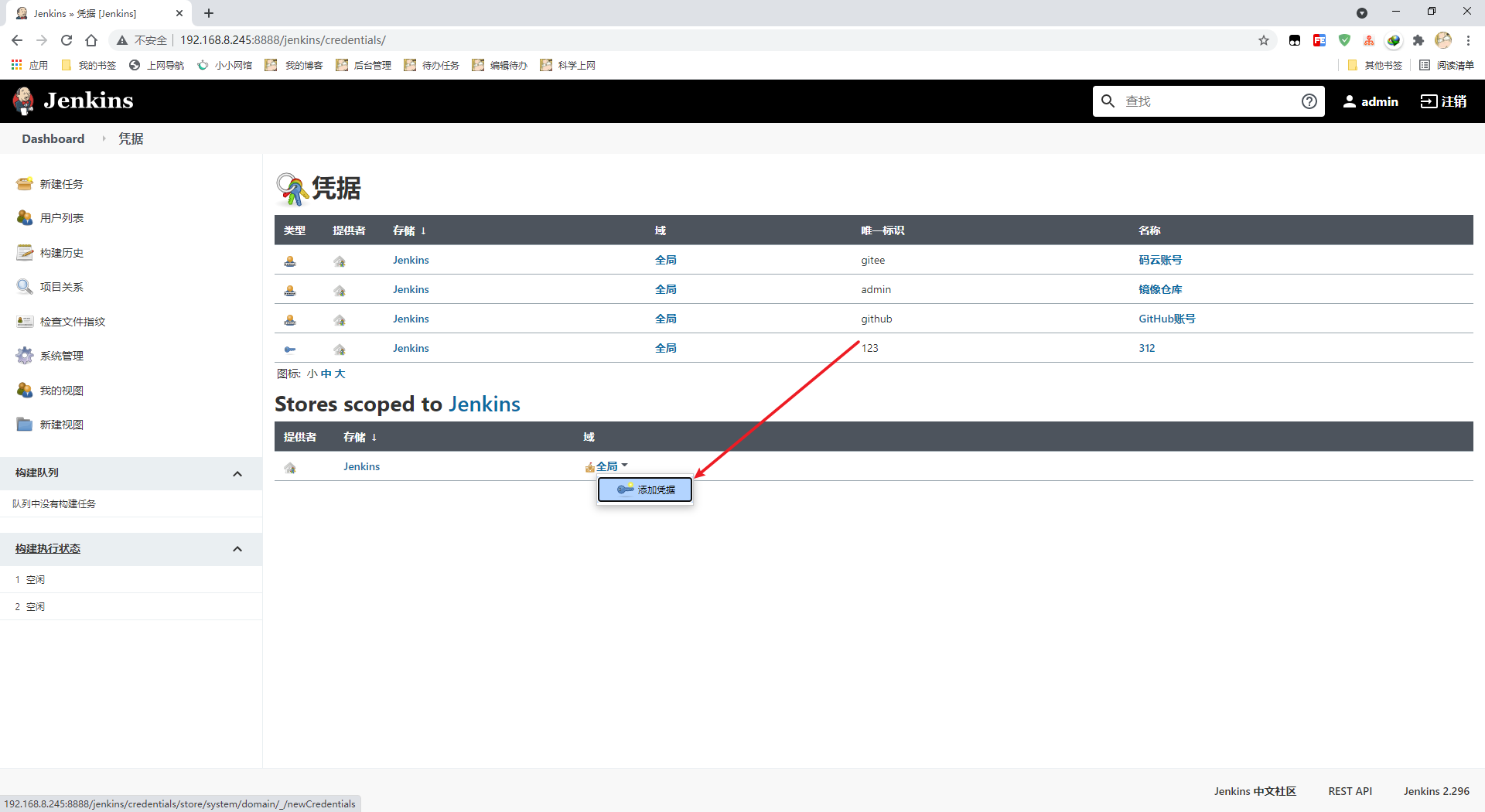
填写信息
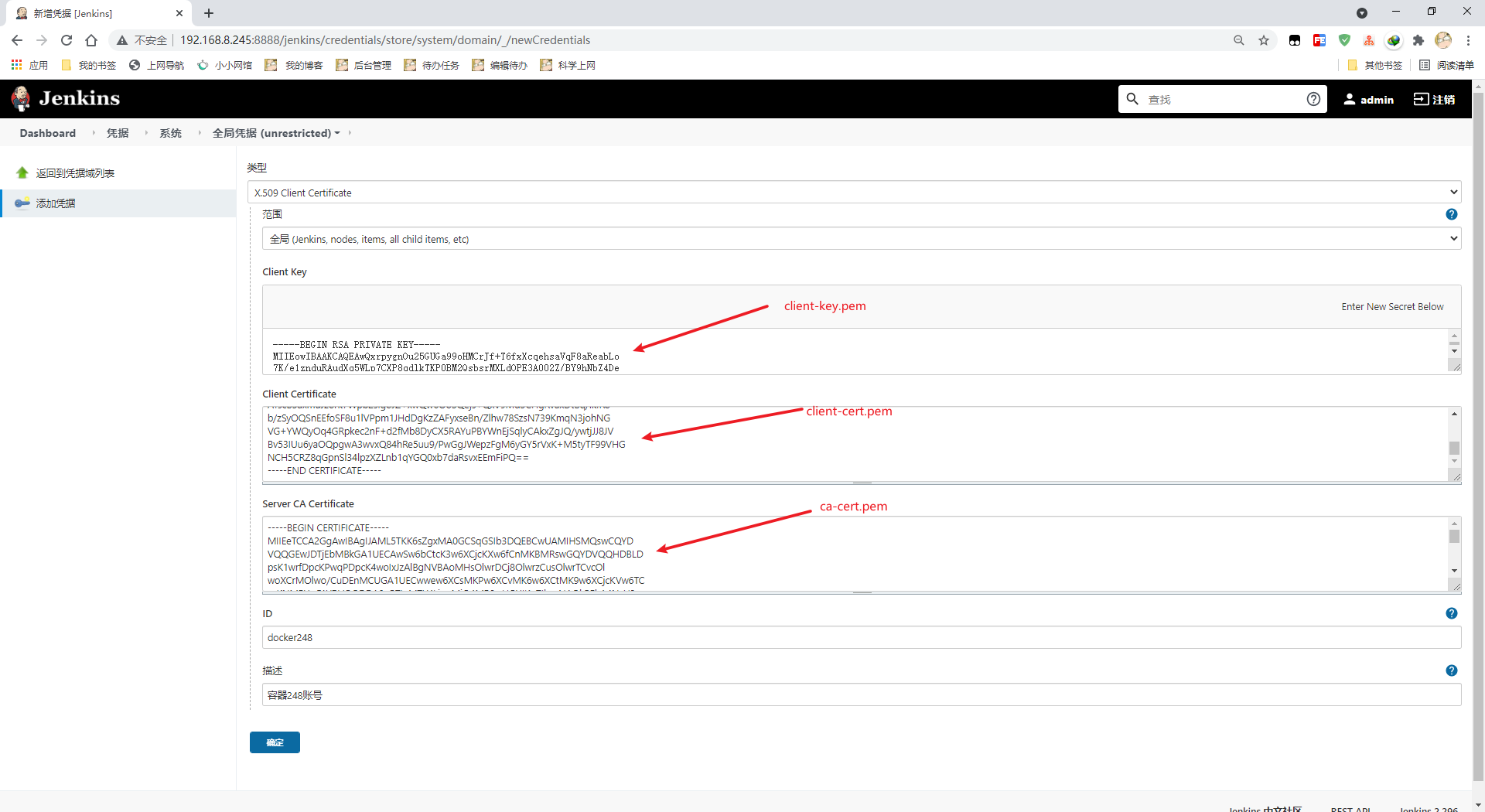
测试连接,注意这里要使用主机名
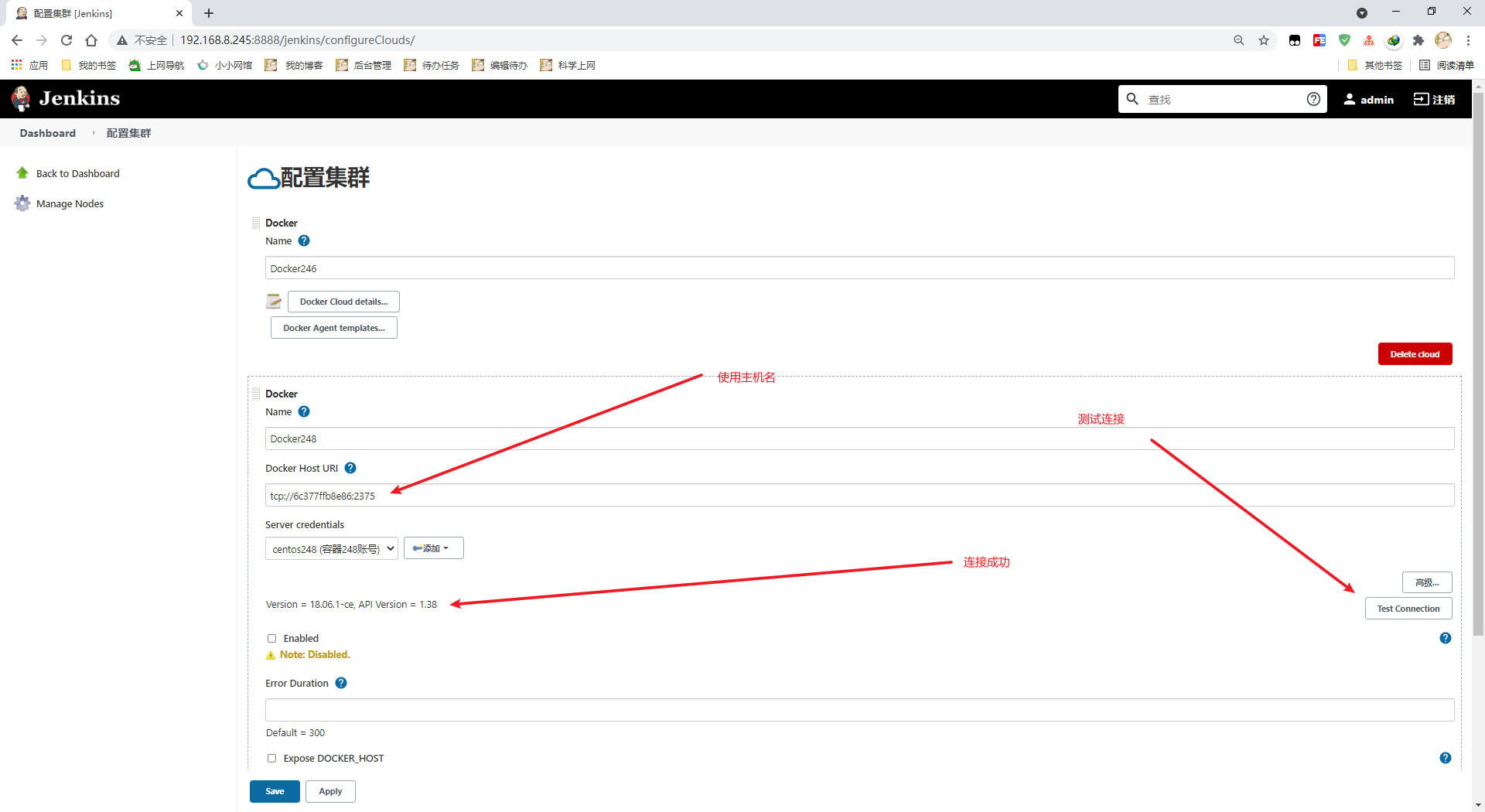
如果是docker安装的jenkins,则需要映射主机名
version: '3'
services:
jenkins:
restart: always
image: 192.168.8.247/xiaoqiangzai/jenkins:latest
container_name: jenkins
ports:
- '8888:8080'
- '50000:50000'
volumes:
- ./data/jenkins_home:/var/jenkins_home
- ./data/war/jenkins.war:/usr/share/jenkins/jenkins.war
environment:
JENKINS_OPTS: "--prefix=/jenkins"
extra_hosts:
- "6c377ffb8e86:192.168.8.248"
3.2 Portainer连接
选择客户端密钥和证书以及CA证书
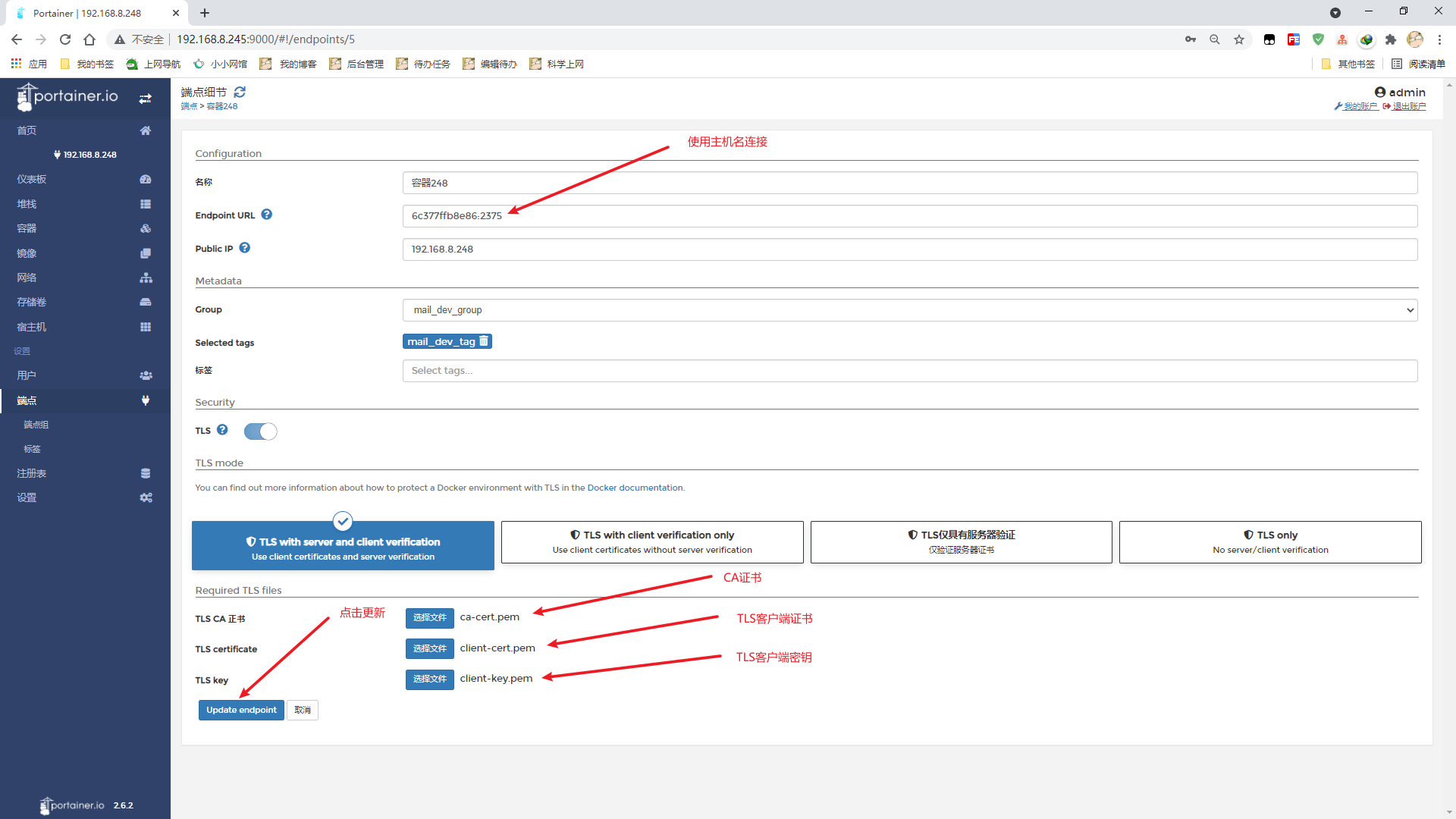
连接正常
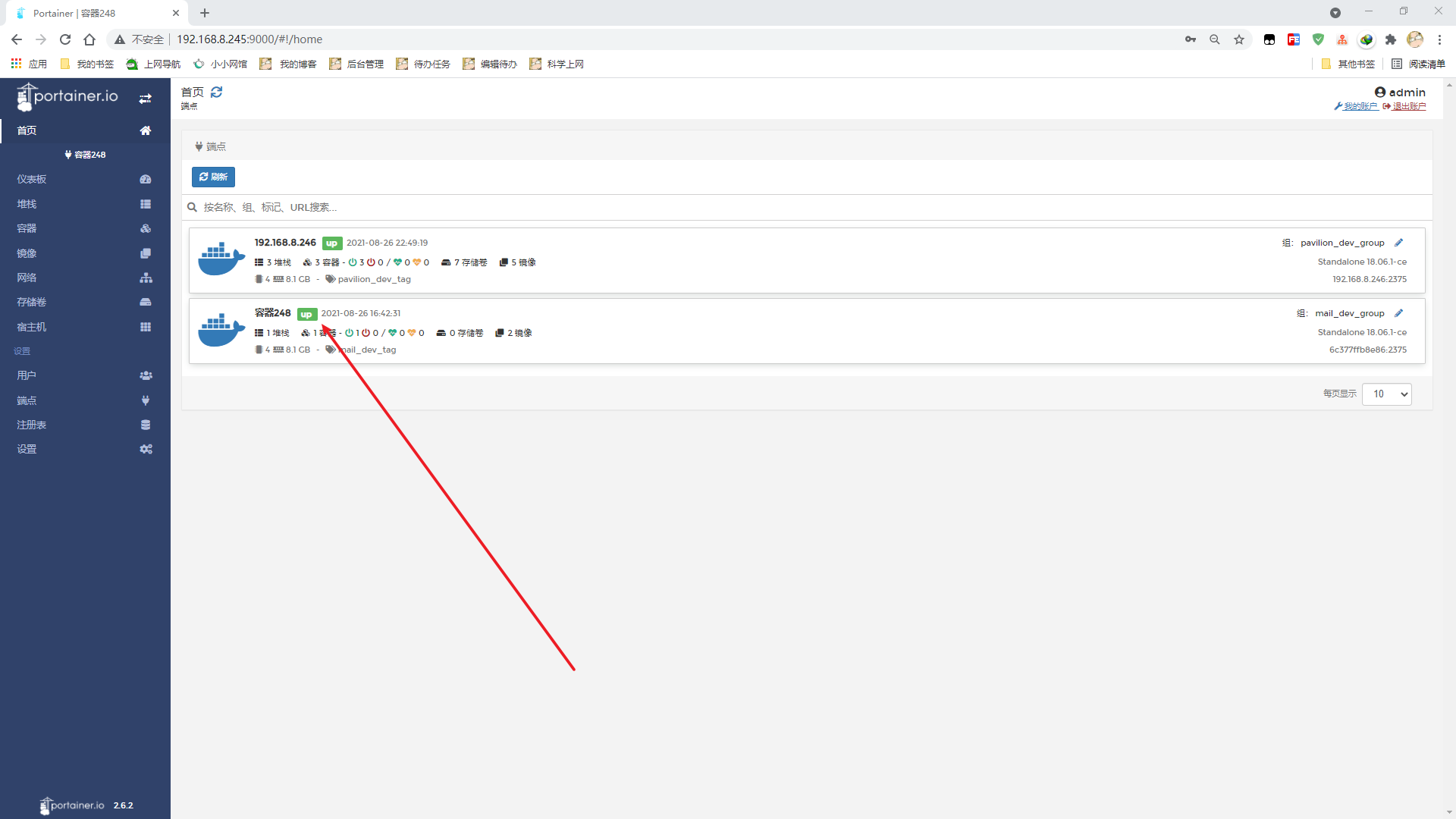
如果是docker安装的Portainer,则需要映射主机名
version: '3'
services:
portainer:
restart: always
image: portainer/portainer-ce:latest
container_name: portainer
privileged: true
ports:
- '9000:9000'
volumes:
- ./data/data:/data
- ./data/public:/public
extra_hosts:
- "6c377ffb8e86:192.168.8.248"
作者(Author):小强崽
来源(Source):https://www.wuduoqiang.com/archives/Docker开启TLS和CA认证
协议(License):署名-非商业性使用-相同方式共享 4.0 国际 (CC BY-NC-SA 4.0)
版权(Copyright):商业转载请联系作者获得授权,非商业转载请注明出处。 For commercial use, please contact the author for authorization. For non-commercial use, please indicate the source.