Java操作dockerAPI
https://github.com/docker-java/docker-java
开放docker端口
操作步骤:
-
docker安装
-
进入docker.service
cd /lib/systemd/system/ vim docker.service -
修改docker.service
找到Execstart=/usr/bin/dockerd 不管其之后是什么在这句话的最后加上
注意:是加上,不修改原有的内容,只是增添
-H tcp://0.0.0.0:2375 -H unix://var/run/docker.sock保存:wq
-
重启docker服务
systemctl daemon-reload//重新加载docker服务的配置文件 service docker restart//重启启动docker systemctl stats docker//可以查看相关内容,看看2375是否已经设置好 netstat -nlp |grep 2375//可以查看2375是否已经被监听 -
开放防火墙2375端口
#查看防火墙端口信息
firewall-cmd --list-ports
#开放端口
firewall-cmd --zone=public --add-port=2375/tcp -permanent
--zone #作用域
--add-port=80/tcp #添加端口,格式为:端口/通讯协议
--permanent #永久生效,没有此参数重启后失效
#重启防火墙
service firewalld restart
? 6.在浏览器中输入 服务器IP:2375/info,获得json数据,检查是否开启成功
直接开放0.0.0.0端口存在一定被入侵风险, 容易被恶意脚本袭击(亲测)
解决方案:自制安全密钥文件 进行安全连接
-
创建安全密钥
-
创建文件夹存放安全密钥文件的地方
[root@jay certs] mkdir /home/user/certs [root@jay certs] cd /home/user/certs -
生成CA私钥
[root@jay certs] openssl genrsa -aes256 -out ca-key.pem 4096 Generating RSA private key, 4096 bit long modulus ...................++ ...............................................................................................................................................................++ e is 65537 (0x10001) Enter pass phrase for ca-key.pem: #此处要求输入密码,后续步骤会用到 Verifying - Enter pass phrase for ca-key.pem: -
生成CA公钥证书
[root@jay certs] openssl req -new -x509 -days 365 -key ca-key.pem -sha256 -out ca.pem Enter pass phrase for ca-key.pem: #输入密码 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- #填写信息,除ip外其他皆可随便填 Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:cn Locality Name (eg, city) [Default City]:cn Organization Name (eg, company) [Default Company Ltd]:cn Organizational Unit Name (eg, section) []:cn #ip地址为自己docker所在服务器的ip地址 Common Name (eg, your name or your server's hostname) []:192.168.83.130 Email Address []: -
生成服务器私钥
[root@jay certs] openssl genrsa -out server-key.pem 4096 Generating RSA private key, 4096 bit long modulus ....................................++ .......................++ e is 65537 (0x10001) -
用私钥生成服务器公钥请求文件
[root@jay certs] openssl req -subj "/CN=192.168.83.130" -sha256 -new -key server-key.pem -out server.csr #ip地址为前面设置的服务器ip地址 -
配置可访问主机
[root@jay certs] echo subjectAltName = DNS:192.168.83.130,IP:192.168.83.130,IP:0.0.0.0,IP:127.0.0.1 >> extfile.cnf #DNS:服务器ip地址 IP:开放主机的ip 0.0.0.0表示所有主机都可访问 -
将Docker守护程序密钥的扩展使用属性设置为仅用于服务器身份验证
[root@jay certs] echo extendedKeyUsage = serverAuth >> extfile.cnf -
将生成信息写入文件
[root@jay certs] openssl x509 -req -days 365 -sha256 -in server.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem -extfile extfile.cnf Signature ok subject=/CN=192.168.83.130 Getting CA Private Key Enter pass phrase for ca-key.pem: #输入密码 -
生成客户端私钥
[root@jay certs] openssl genrsa -out key.pem 4096 Generating RSA private key, 4096 bit long modulus .........................................................................................................++ ..........................++ e is 65537 (0x10001) -
生成客户端证书请求文件
[root@jay certs] openssl req -subj '/CN=client' -new -key key.pem -out client.csr -
将Docker守护程序密钥的扩展使用属性设置为仅用于客户端身份验证
[root@jay certs] echo extendedKeyUsage = clientAuth >> extfile.cnf -
用 CA 为客户端签署证书文件
[root@jay certs] openssl x509 -req -days 365 -sha256 -in client.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out cert.pem -extfile extfile.cnf Signature ok subject=/CN=client Getting CA Private Key Enter pass phrase for ca-key.pem: #输入密码 -
删除临时文件
[root@jay certs] rm -v client.csr server.csr rm: remove regular file ‘server.csr’? y removed ‘server.csr’ -
配置证书权限
[root@jay certs] chmod -v 0400 ca-key.pem key.pem server-key.pem mode of ‘ca-key.pem’ changed from 0644 (rw-r--r--) to 0400 (r--------) mode of ‘key.pem’ changed from 0644 (rw-r--r--) to 0400 (r--------) mode of ‘server-key.pem’ changed from 0644 (rw-r--r--) to 0400 (r--------) [root@jay certs] chmod -v 0444 ca.pem server-cert.pem cert.pem mode of ‘ca.pem’ changed from 0644 (rw-r--r--) to 0444 (r--r--r--) mode of ‘server-cert.pem’ changed from 0644 (rw-r--r--) to 0444 (r--r--r--) mode of ‘cert.pem’ changed from 0644 (rw-r--r--) to 0444 (r--r--r--) -
查看 /home/user/certs 下的文件,一共应该有 8 个文件
[root@jay certs] ls ca-key.pem ca.srl extfile.cnf server-cert.pem ca.pem cert.pem key.pem server-key.pem
-
-
服务端设置
-
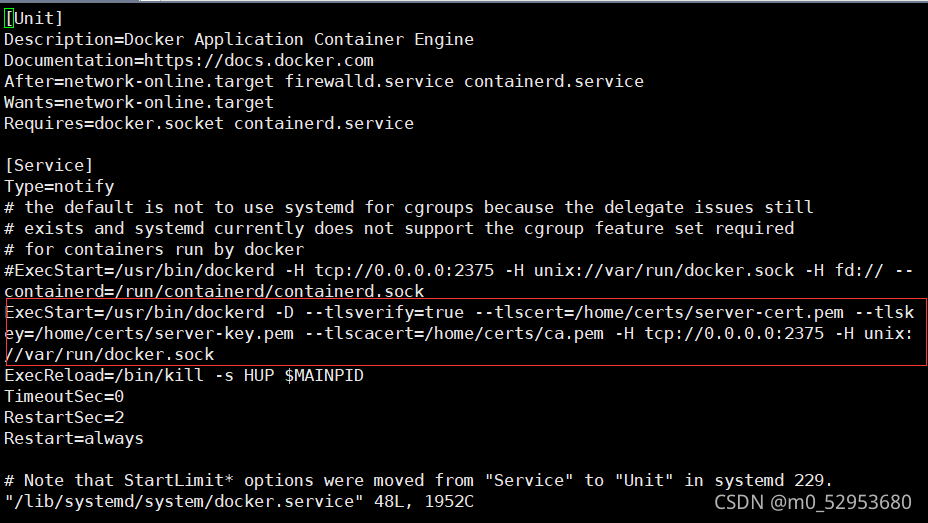
修改docker.service文件
[root@jay certs] vim /lib/systemd/system/docker.service #修改 ExecStart=/usr/bin/dockerd -D --tlsverify=true --tlscert=/home/certs/server-cert.pem --tlskey=/home/certs/server-key.pem --tlscacert=/home/certs/ca.pem -H tcp://0.0.0.0:2375 -H unix://var/run/docker.sock
-
重启docker
[root@jay certs] systemctl daemon-reload [root@jay certs] service docker restart Redirecting to /bin/systemctl restart docker.service -
查看docker状态
[root@jay certs] systemctl status docker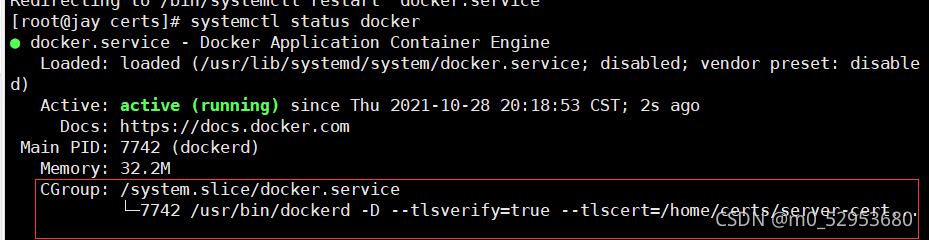
-
-
客户端设置
-
将ca-key.pem、ca.pem、cert.pem、key.pem 这 4 个密钥文件下载到本机的磁盘上
-
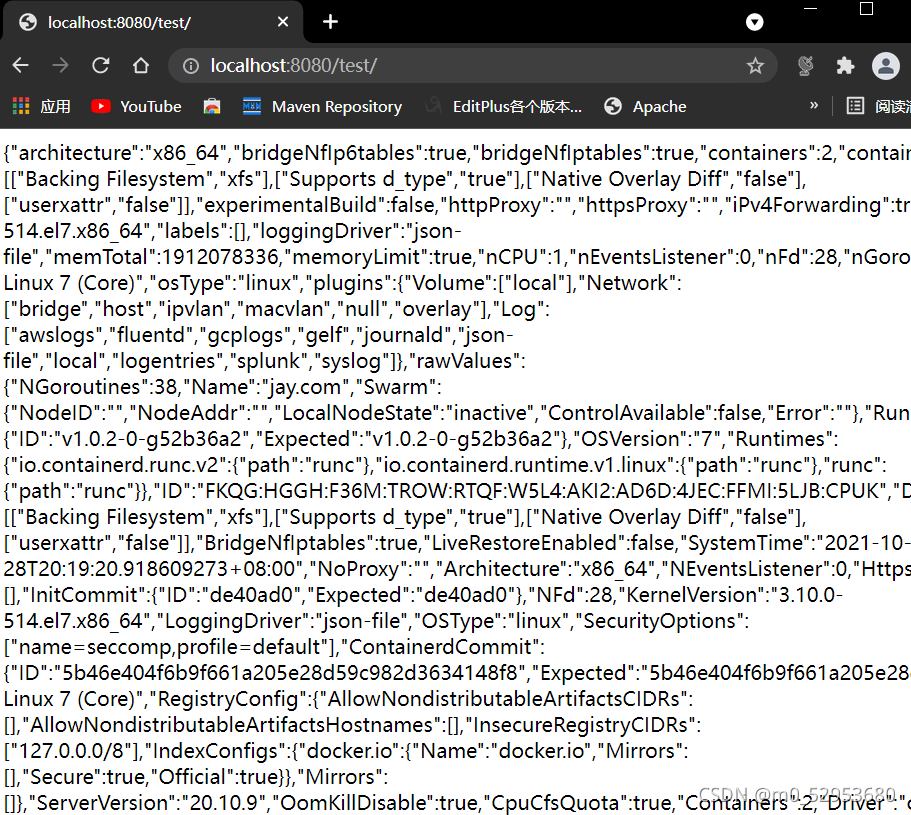
java连接docker服务器测试(注意引入docker-java依赖,参考-docker-java集成使用)
@RestController public class TestController { @GetMapping("/test") public String test(){ DockerClientConfig config = DefaultDockerClientConfig.createDefaultConfigBuilder() .withDockerTlsVerify(true) .withDockerCertPath("D:/Java/certs/") //密钥文件所在位置 .withDockerHost("tcp://192.168.83.130:2375") .withDockerConfig("D:/Java/certs/") .build(); DockerClient dockerClient = DockerClientBuilder.getInstance(config).build(); Info info = dockerClient.infoCmd().exec(); String infoStr = JSONObject.toJSONString(info); return infoStr; } -
运行结果
-
docker-java集成使用
Dependencies:
<dependency>
<groupId>com.github.docker-java</groupId>
<artifactId>docker-java</artifactId>
<!-- use latest version https://github.com/docker-java/docker-java/releases -->
<version>3.2.12</version>
</dependency>
Service:
package com.jay.docker.service;
import com.alibaba.fastjson.JSONObject;
import com.github.dockerjava.api.DockerClient;
import com.github.dockerjava.api.command.CreateContainerResponse;
import com.github.dockerjava.api.model.ExposedPort;
import com.github.dockerjava.api.model.Info;
import com.github.dockerjava.api.model.Ports;
import com.github.dockerjava.core.DockerClientBuilder;
import static com.github.dockerjava.api.model.HostConfig.newHostConfig;
public class DockerClientService {
/**
* 连接docker服务器
* @return
*/
public DockerClient connectDocker(){
DockerClient dockerClient = DockerClientBuilder.getInstance("tcp://xxxx:2375").build();
Info info = dockerClient.infoCmd().exec();
String infoStr = JSONObject.toJSONString(info);
System.out.println("docker的环境信息如下:=================");
System.out.println(info);
return dockerClient;
}
/**
* 创建容器
* @param client
* @return
*/
public CreateContainerResponse createContainers(DockerClient client,String containerName,String imageName){
//映射端口8088—>80
ExposedPort tcp80 = ExposedPort.tcp(80);
Ports portBindings = new Ports();
portBindings.bind(tcp80, Ports.Binding.bindPort(8088));
CreateContainerResponse container = client.createContainerCmd(imageName)
.withName(containerName)
.withHostConfig(newHostConfig().withPortBindings(portBindings))
.withExposedPorts(tcp80).exec();
return container;
}
/**
* 启动容器
* @param client
* @param containerId
*/
public void startContainer(DockerClient client,String containerId){
client.startContainerCmd(containerId).exec();
}
/**
* 删除容器
* @param client
* @param containerId
*/
public void removeContainer(DockerClient client,String containerId){
client.removeContainerCmd(containerId).exec();
}
}
docker-java详解
Dependencies
-
com.github.docker-java:docker-java-core 用于 DockerClient连接
-
one of com.github.docker-java:docker-java-transport-* 与 Docker 守护进程通信
实例化DockerClientConfig
- 您将需要一个 DockerClientConfig 实例来告诉库如何访问 Docker,使用哪些凭据从 Docker 注册表中提取
- 构建器可用,并允许您配置客户端的每个属性
DockerClientConfig standard = DefaultDockerClientConfig.createDefaultConfigBuilder().build();
DockerClientConfig custom = DefaultDockerClientConfig.createDefaultConfigBuilder()
//Docker 主机 URL
.withDockerHost("tcp://docker.somewhere.tld:2376")
//启用/禁用 TLS 验证(在 http 和 https 协议之间切换)
.withDockerTlsVerify(true)
//TLS 验证所需证书的路径
.withDockerCertPath("/home/user/.docker")
//您的注册表用户名(推送容器所需)
.withRegistryUsername(registryUser)
//您的注册表密码
.withRegistryPassword(registryPass)
//您的注册邮箱
.withRegistryEmail(registryMail)
//您的注册地址
.withRegistryUrl(registryUrl)
.build();
//DOCKER_CONFIG 其他 docker 配置文件的路径(如 .dockercfg)
//api.version API 版本,例如1.23
参考: