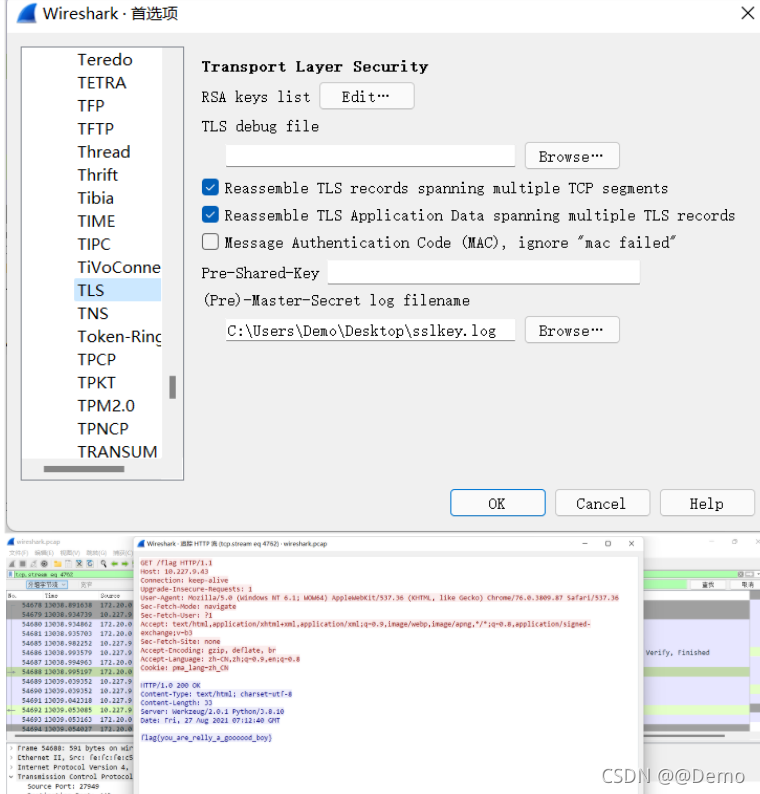
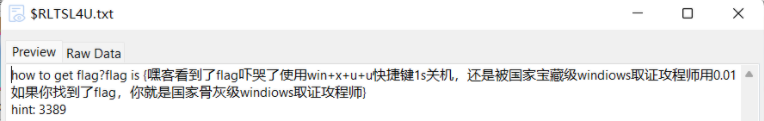
login
示例-副本.txt是伪加密,解出后明文攻击
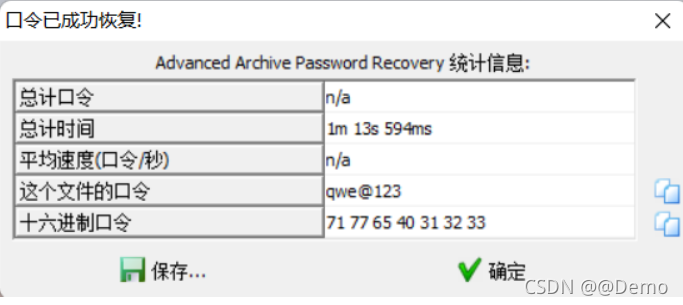
解密password.zip发现是六字符CRC32
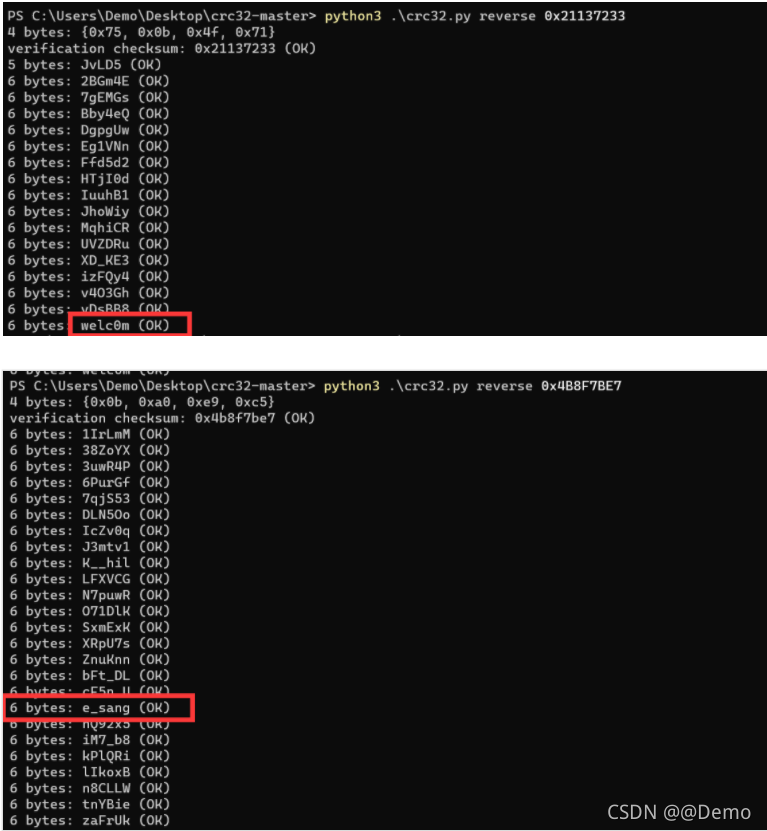
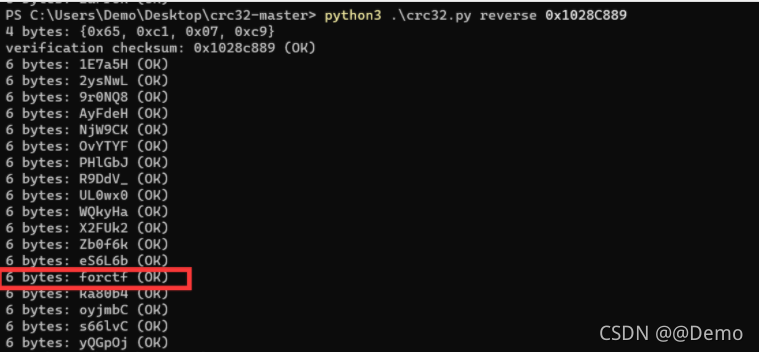
得到密码
welc0me_sangforctf
解密.passwd.swp
家人们以后恢复swp一定要用 !!!!!!!! vim -r 或者 vi -r 不要用cat!!!
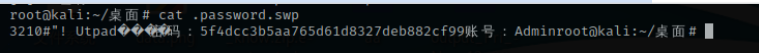
得到账号密码
5f4dcc3b5aa765d61d8327deb882cf99账号:Admin
直接登陆即可
 查看源码获得flag
查看源码获得flag
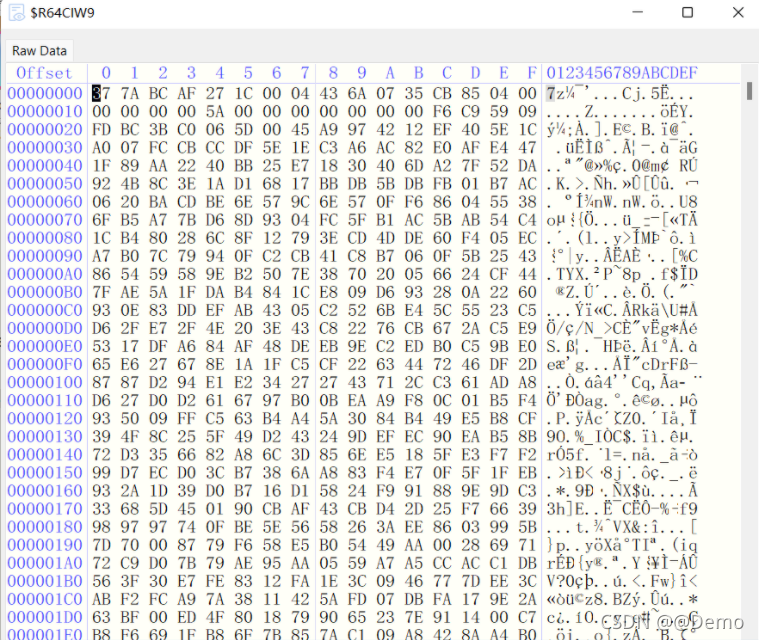
Disk
附件附件名为
zse456tfdyhnjimko0-=[;.,
对应键盘得到密码 pvd
后缀为vera,使用vetaCrypt挂载
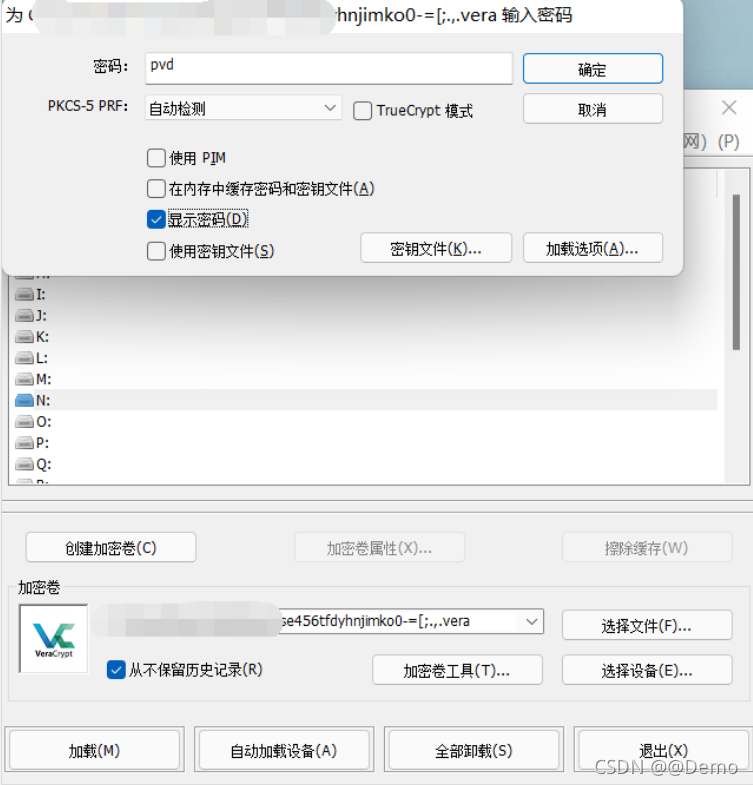
成功挂载后得到两个文件
good.txt
you are gooood, but need more efforts,
010打开good发现是7z,后缀改为7z解压
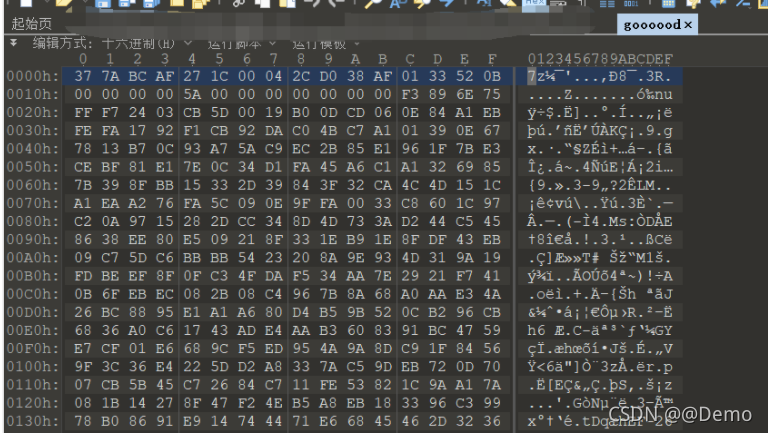
得到两个img文件
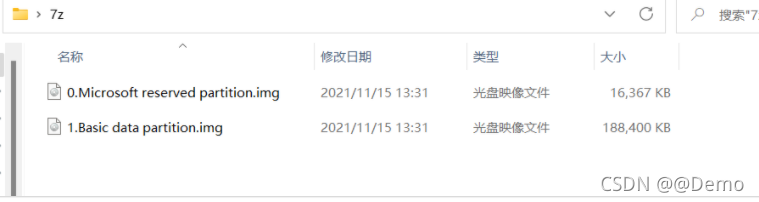
取证大师打开1.Basci data partition.img(DiskGenius同理)
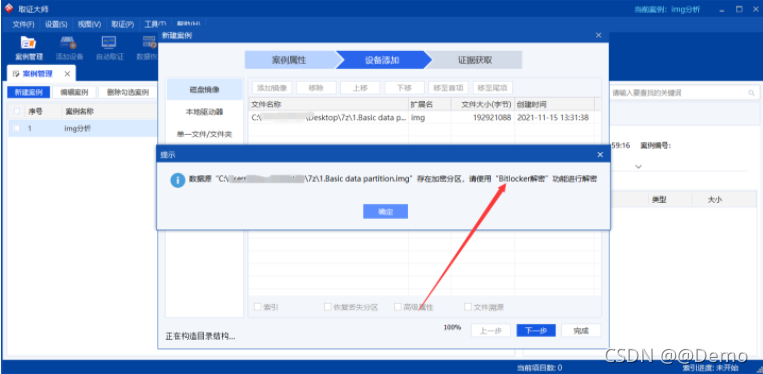
发现被Bitlocker加密了,但是又没有秘钥,尝试使用hashcat进行爆破
使用bitlocker2john获取密码hash(kali自带这个工具)
bitlocker2john -i 1.Basic\ data\ partition.img
得到
Encrypted device 1.Basic data partition.img opened, size 183MB
Signature found at 0x3
Version: 8
Invalid version, looking for a signature with valid version...
Signature found at 0x2200000
Version: 2 (Windows 7 or later)
VMK entry found at 0x22000a5
VMK encrypted with User Password found at 22000c6
VMK encrypted with AES-CCM
UP Nonce: a0348897f591d70103000000
UP MAC: fb026c1039aec7a85c77964d9cf2b63f
UP VMK: 6261579f431dfdb675322ab91e44acab870c75a64b5722be3500b35bcee969dc59e31ffdf88c1cb3a07776fa
VMK entry found at 0x2200185
VMK encrypted with Recovery Password found at 0x22001a6
Salt: 9d0ef79ddd7378938d2e192b0f86c8d3
Searching AES-CCM from 0x22001c2
Trying offset 0x2200255....
VMK encrypted with AES-CCM!!
RP Nonce: a0348897f591d70106000000
RP MAC: de3a14e281933427b5d31f2a1480a08c
RP VMK: 3fa72b249f2305b64dc707f0989d404a9dc05aca6e171eb675584dd0ef24236b88df130c0987f38f1197e056
Signature found at 0x36ab000
Version: 2 (Windows 7 or later)
VMK entry found at 0x36ab0a5
VMK entry found at 0x36ab185
Signature found at 0x4b56000
Version: 2 (Windows 7 or later)
VMK entry found at 0x4b560a5
VMK entry found at 0x4b56185
User Password hash:
$bitlocker$0$16$6c1fbe8314e64b4042110147cb1632d2$1048576$12$a0348897f591d70103000000$60$fb026c1039aec7a85c77964d9cf2b63f6261579f431dfdb675322ab91e44acab870c75a64b5722be3500b35bcee969dc59e31ffdf88c1cb3a07776fa
Hash type: User Password with MAC verification (slower solution, no false positives)
$bitlocker$1$16$6c1fbe8314e64b4042110147cb1632d2$1048576$12$a0348897f591d70103000000$60$fb026c1039aec7a85c77964d9cf2b63f6261579f431dfdb675322ab91e44acab870c75a64b5722be3500b35bcee969dc59e31ffdf88c1cb3a07776fa
Hash type: Recovery Password fast attack
$bitlocker$2$16$9d0ef79ddd7378938d2e192b0f86c8d3$1048576$12$a0348897f591d70106000000$60$de3a14e281933427b5d31f2a1480a08c3fa72b249f2305b64dc707f0989d404a9dc05aca6e171eb675584dd0ef24236b88df130c0987f38f1197e056
Hash type: Recovery Password with MAC verification (slower solution, no false positives)
$bitlocker$3$16$9d0ef79ddd7378938d2e192b0f86c8d3$1048576$12$a0348897f591d70106000000$60$de3a14e281933427b5d31f2a1480a08c3fa72b249f2305b64dc707f0989d404a9dc05aca6e171eb675584dd0ef24236b88df130c0987f38f1197e056
然后使用hashcat爆破bitlocker的秘钥
dict.txt:因为是自己复现把已知的秘钥写进去就好了
hash.txt(也就是User Password hash的第一部分):
$bitlocker$0$16$6c1fbe8314e64b4042110147cb1632d2$1048576$12$a0348897f591d70103000000$60$fb026c1039aec7a85c77964d9cf2b63f6261579f431dfdb675322ab91e44acab870c75a64b5722be3500b35bcee969dc59e31ffdf88c1cb3a07776fa
使用hashcat进行攻击,-m的参数是查看的官方wp,一般常见的可以通过hashcat --help查看
hashcat -m 22100 hash.txt dict.txt --show
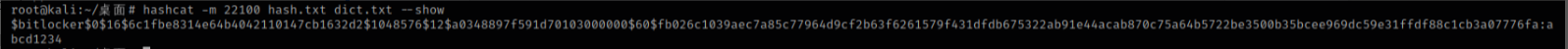
得到秘钥abcd1234,使用DiskGenius解密Bitlocker
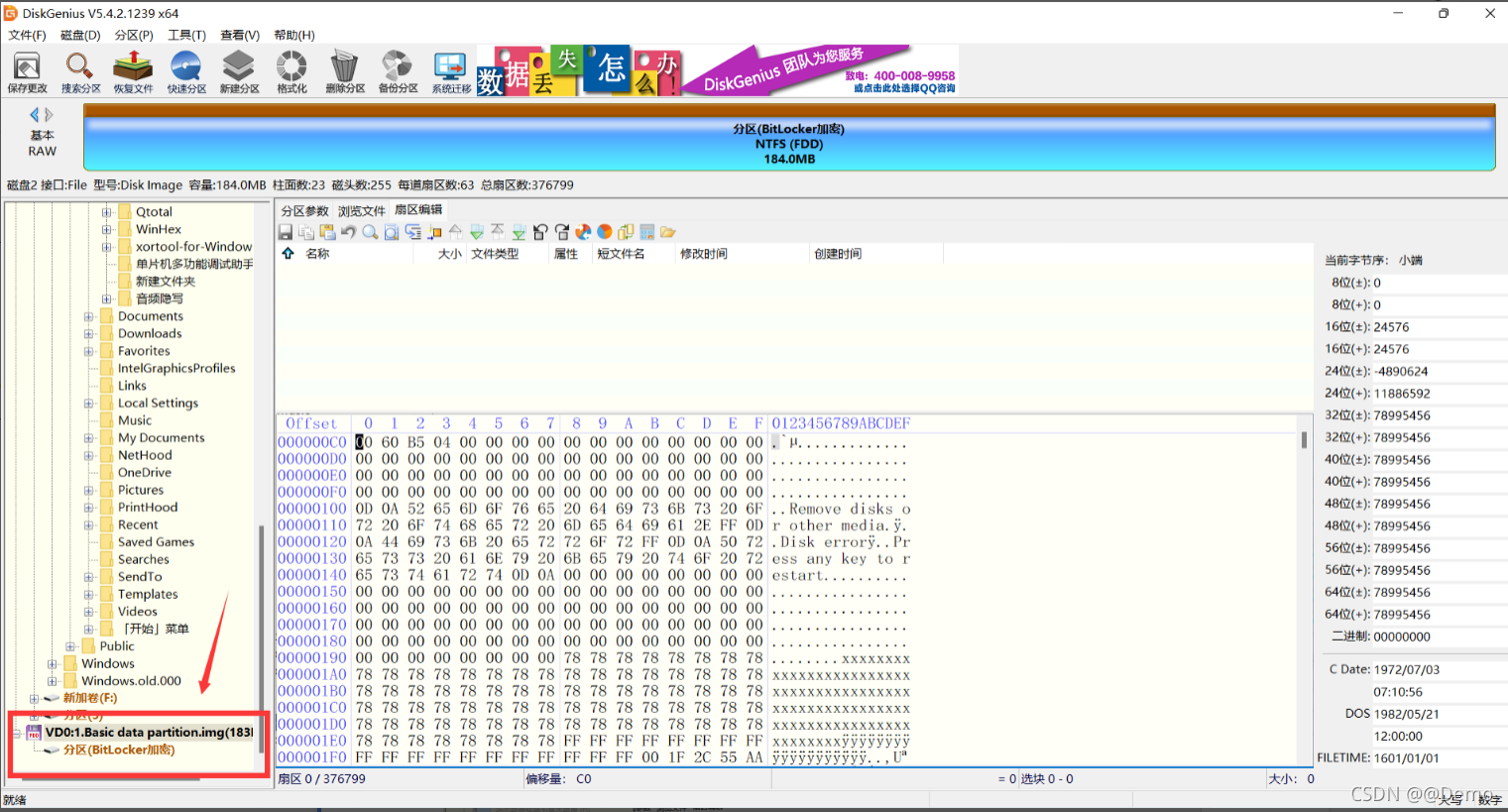
双击
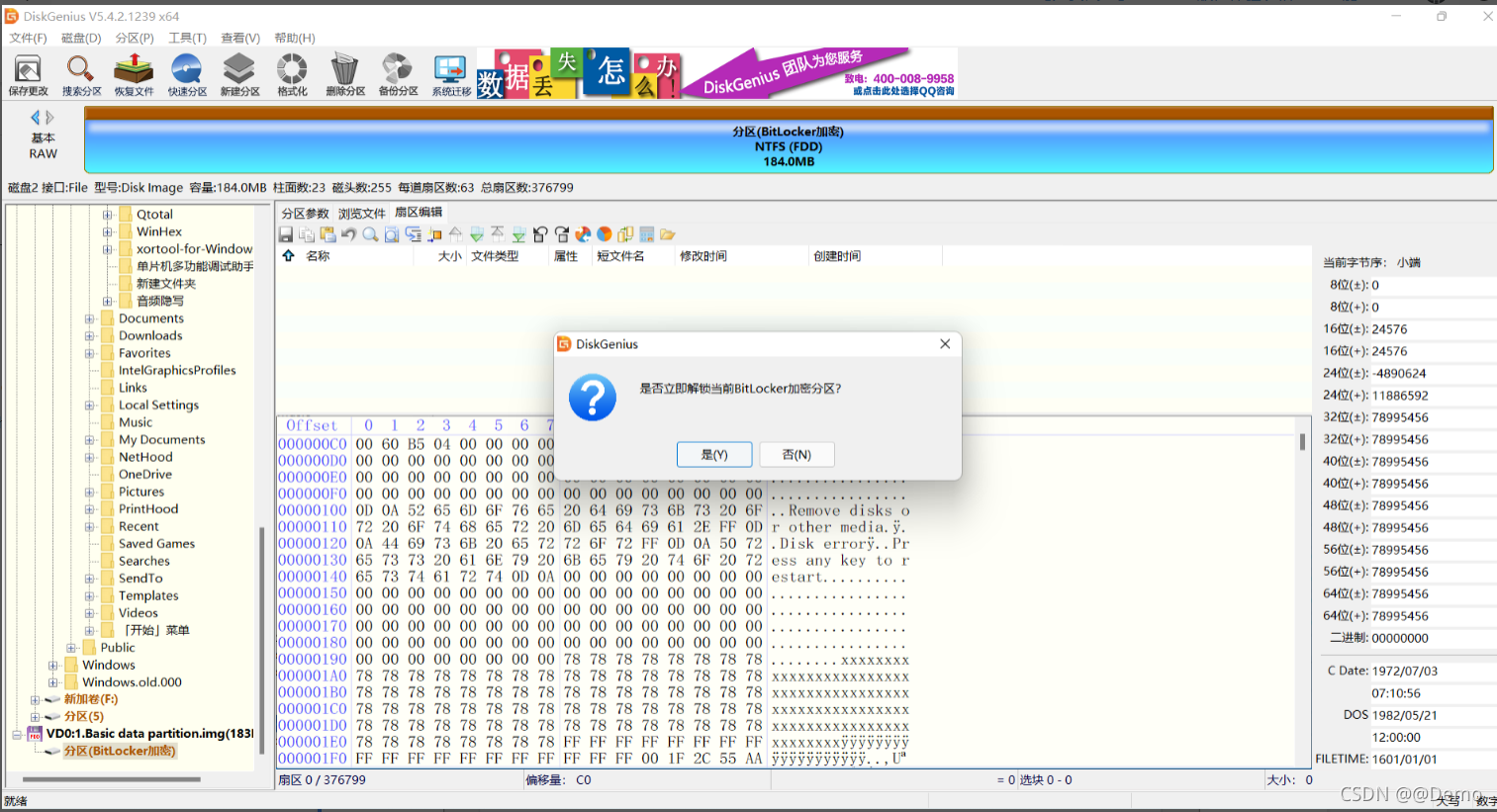
输入密码
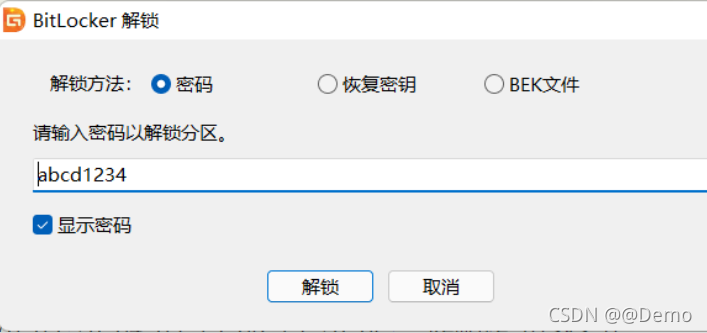
解密之后
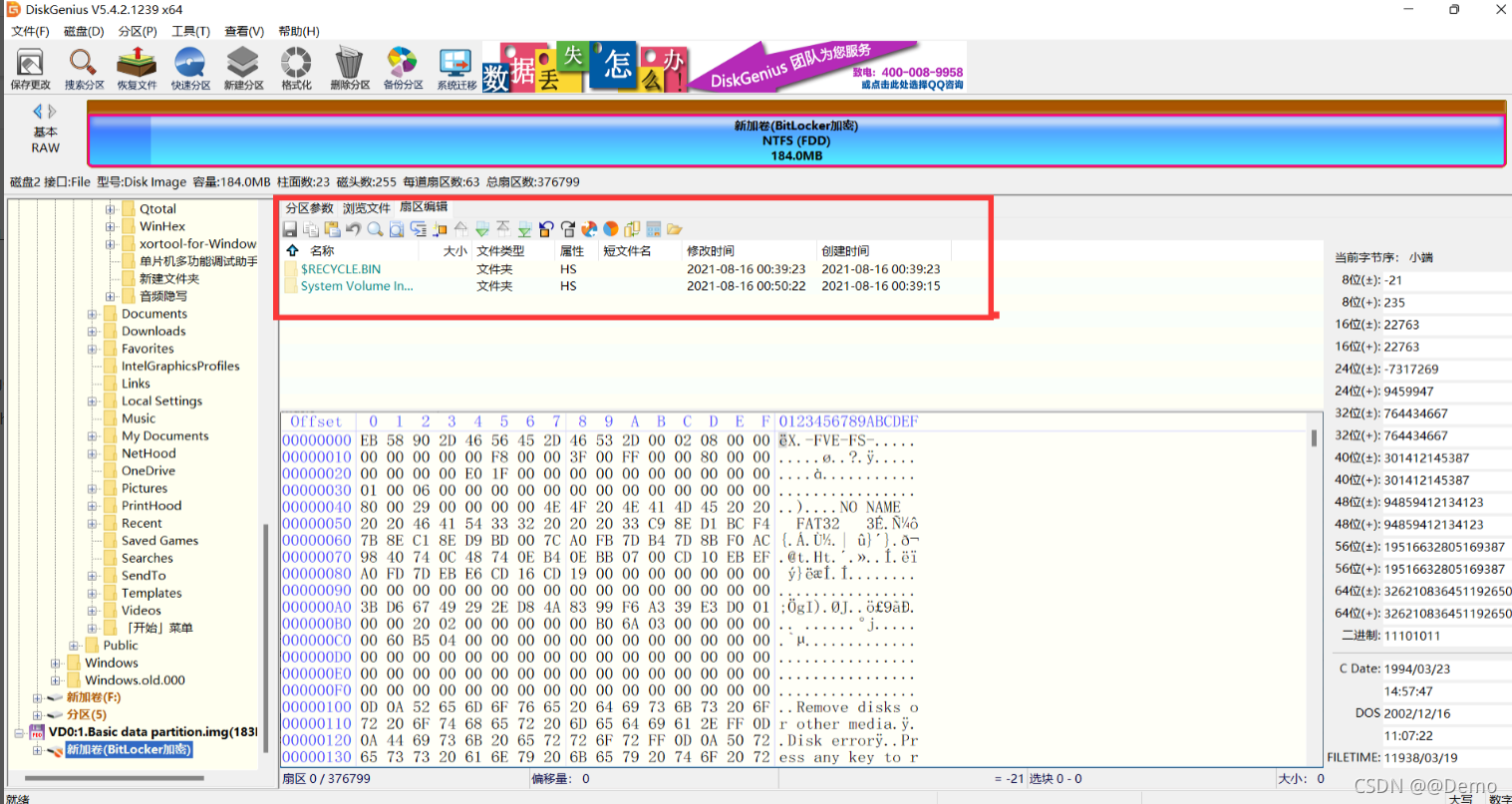
选中得到
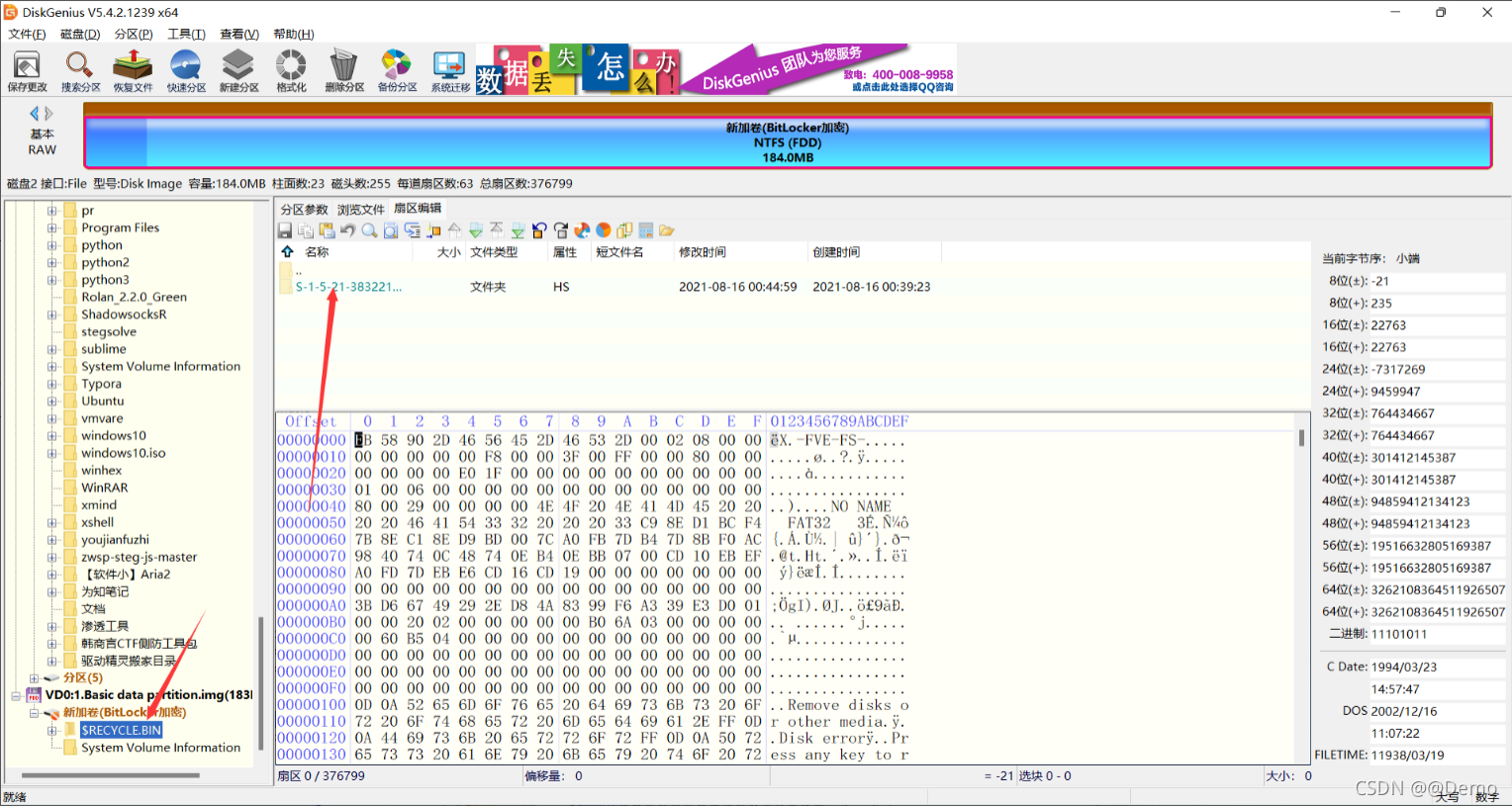
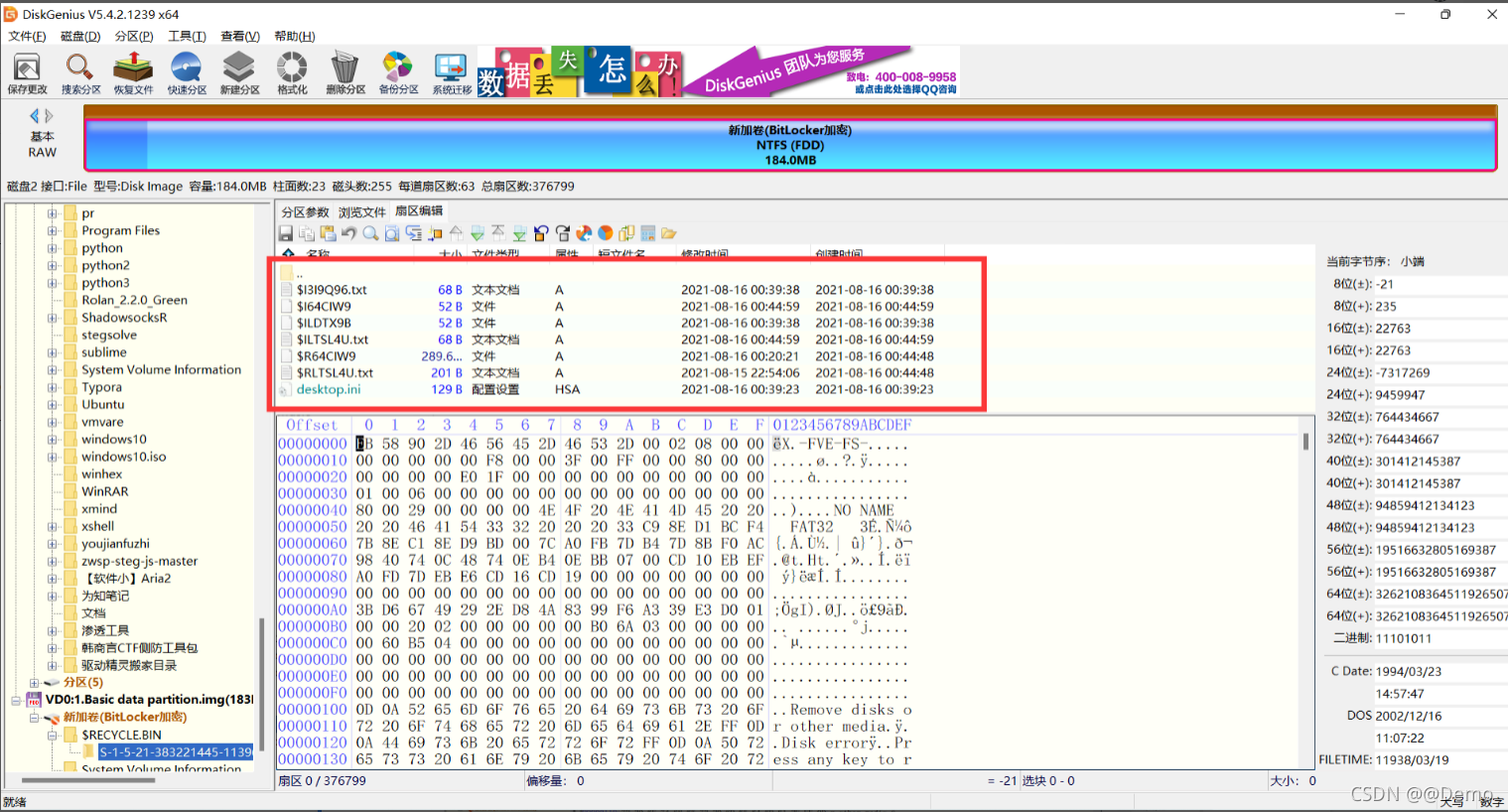
通过查看文件发现有两个重要的文件
txt里是
另一个是7z压缩包
把7z保存出来
可以参考
https://baijiahao.baidu.com/s?id=1705153152225734305&wfr=spider&for=pc
github搜索bmc-tool
新建一个aaa文件夹
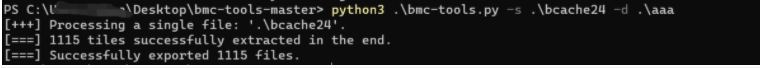
在aaa文件夹生成很多缩略图

拼图拼一下
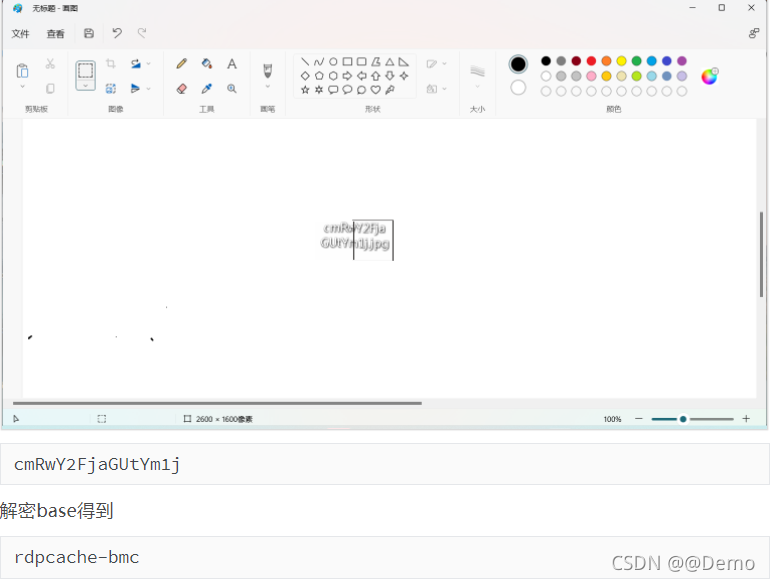
bridge
在bgr0通道发现隐藏图片
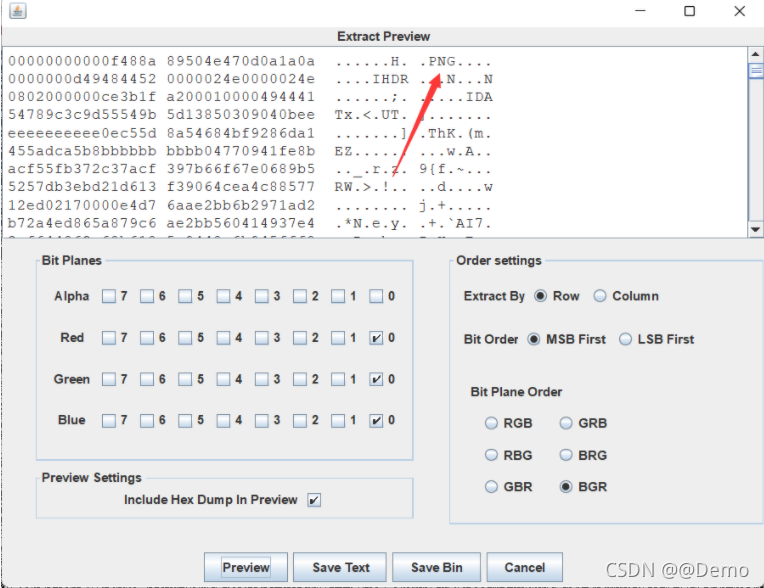
LSB和MSB各有一张,只不过是同一张。保存后删除文件头多余的部分
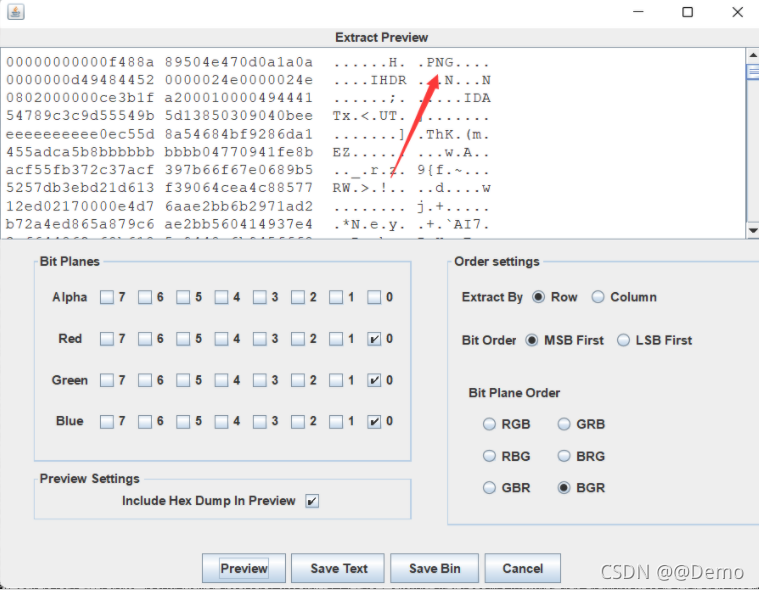
发现后面多了一部分奇怪的数据
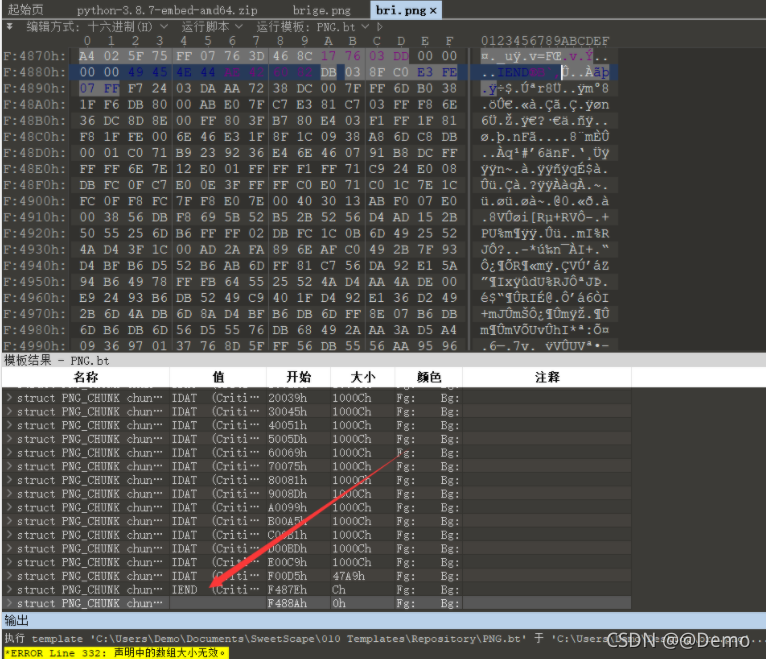
图片的样子也很奇怪,像是刻意修改过的
还能发现原图的IDAT块有问题
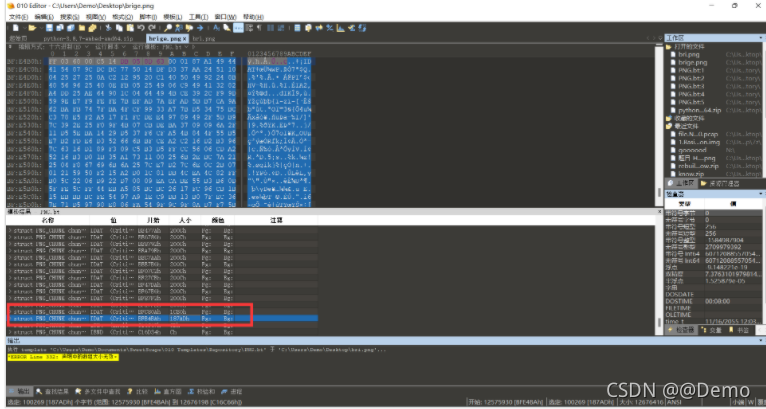
IDAT只有填满后才会开启下一个IDAT,所以能看出明显的有问题
下面是复现环节
exiftool分析原图
exiftool安装
sudo apt install libimage-exiftool-perl
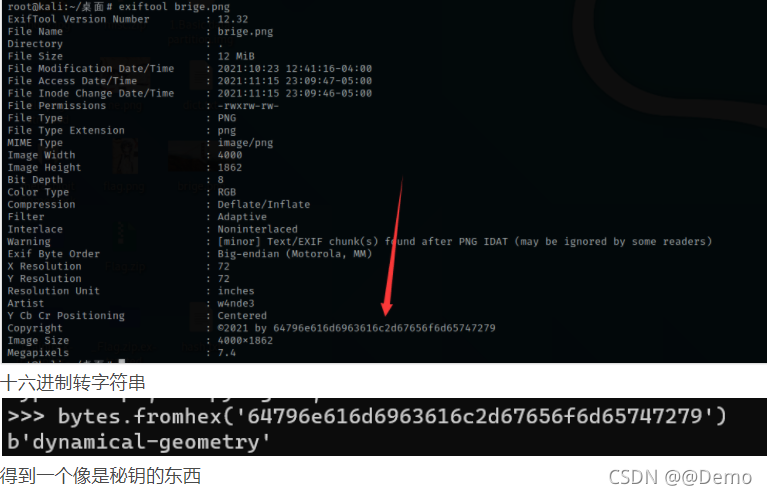
dynamical-geometry
再看原来的IDAT
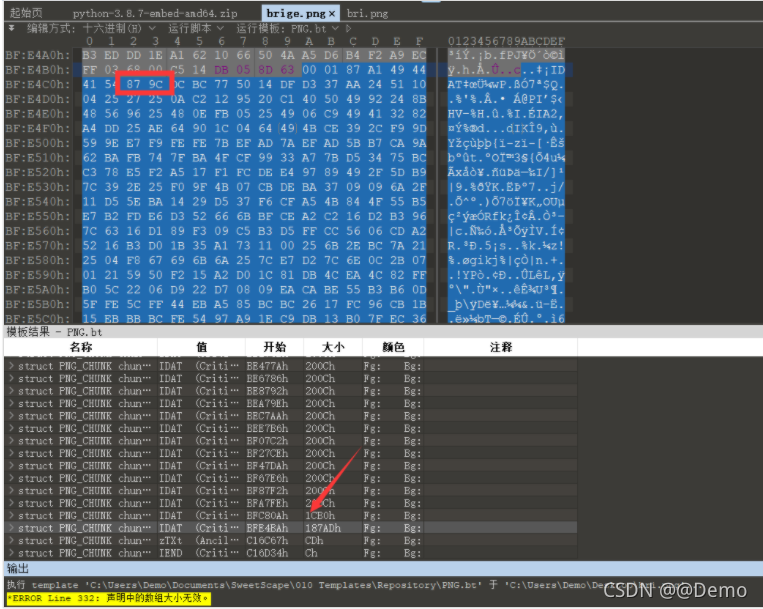
能发现是zlib的文件头,只不过被改成了87 9c,还原一下
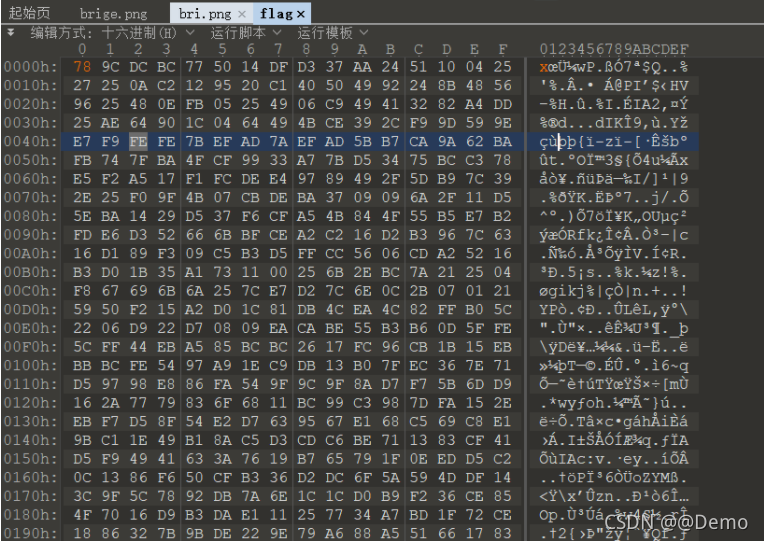
zlib解密一下能发现是rar文件
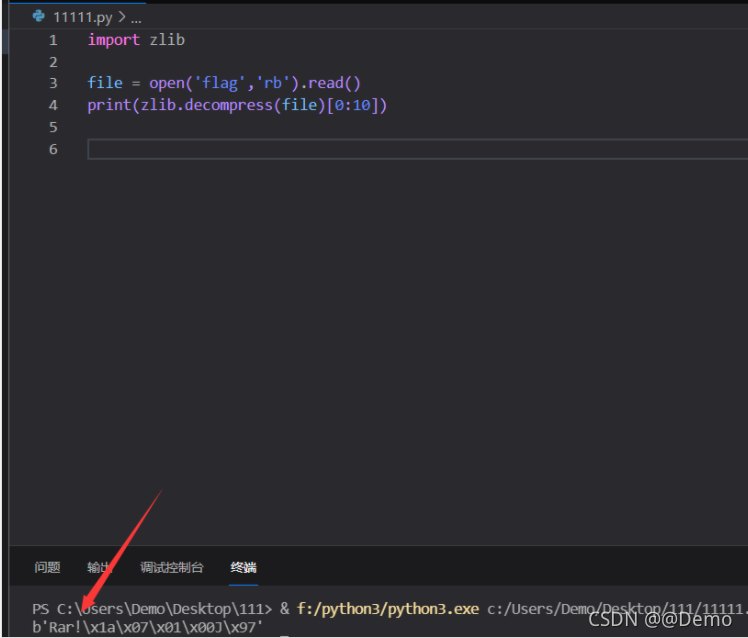
导出一下rar
import zlib
file = open('flag','rb').read()
# print(zlib.decompress(file)[0:10])
data = zlib.decompress(file)
rar = open('1.rar','wb')
rar.write(data)
得到一个提示
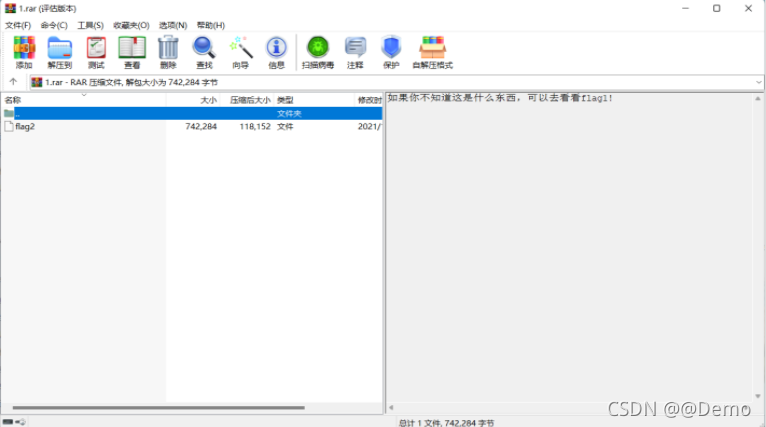
还有lsb隐写提取的图片没有分析。查看LSB隐写啥的没啥东西,010看IDAT块也没啥毛病,把心思放在像素的分析上。
先把像素提取下,放到txt里分析
from PIL import Image
img = Image.open('bri.png')
print(img.size)
height = img.size[0]
width = img.size[1]
pixeltxt = open('pixel.txt','a')
for x in range(height):
for y in range(width):
# print(img.getpixel((x,y)))
pixel = img.getpixel((x,y))
pixeltxt.write(str(pixel) + '\n')
然后发现像素的第三位有问题,将他们转为十六进制。
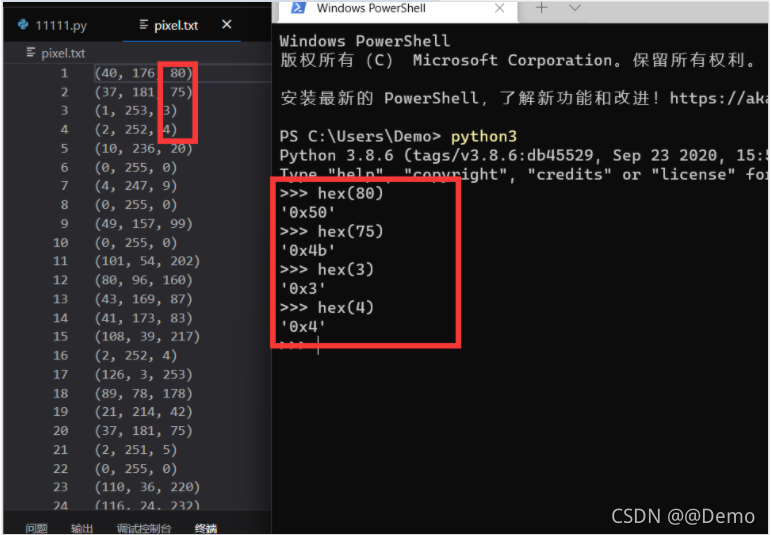
妥妥的zip文件头,那思路就清楚了,提取tunple的第三位即可
from PIL import Image
img = Image.open('bri.png')
print(img.size)
height = img.size[0]
width = img.size[1]
pixeltxt = open('pixel.txt','a')
zipstrings = ''
for x in range(height):
for y in range(width):
# print(img.getpixel((x,y)))
pixel = img.getpixel((x,y))
# pixeltxt.write(str(pixel) + '\n')
# print(type(pixel[2]))
hexnum = hex(pixel[2])
zipstrings += str(hexnum)[2:].zfill(2)
zip = open('1.txt','a')
zip.write(zipstrings)
得到
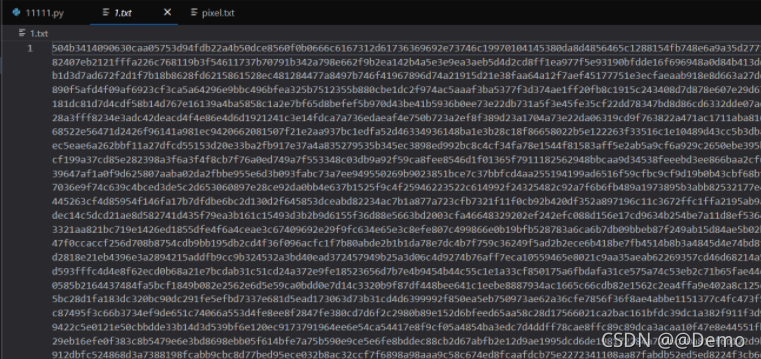
010转成zip即可
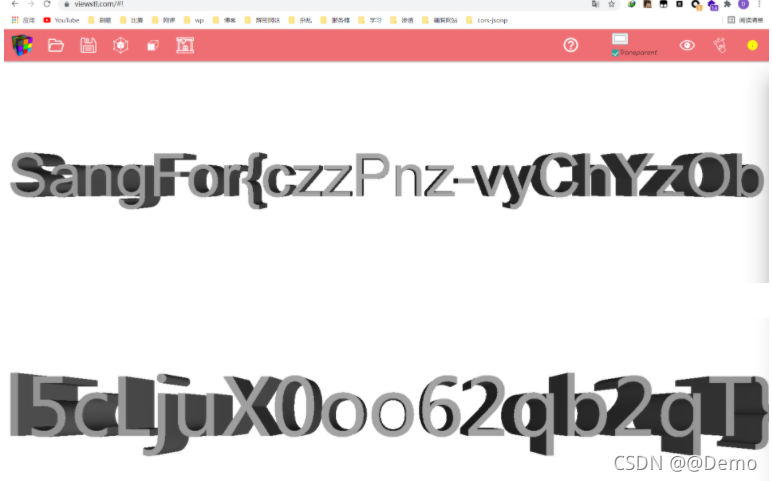
使用在线网站查看stl https://www.viewstl.com/#!
flow hunter
查看各个协议可以发现,存在很多的dns协议,单看这些dns协议是看不出什么信息的。查看出现最多的tcp流,能发现4771条tcp流,是在进行fuzz,基本上前面所有的包都是404,既然前面都是404那其实可以倒着看。
能看到这边是传了一个secret参数,
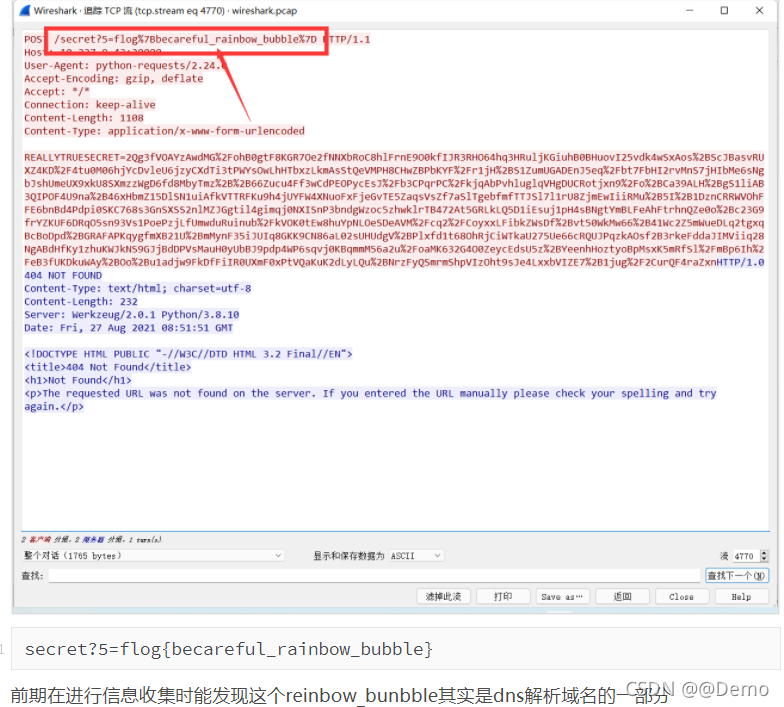
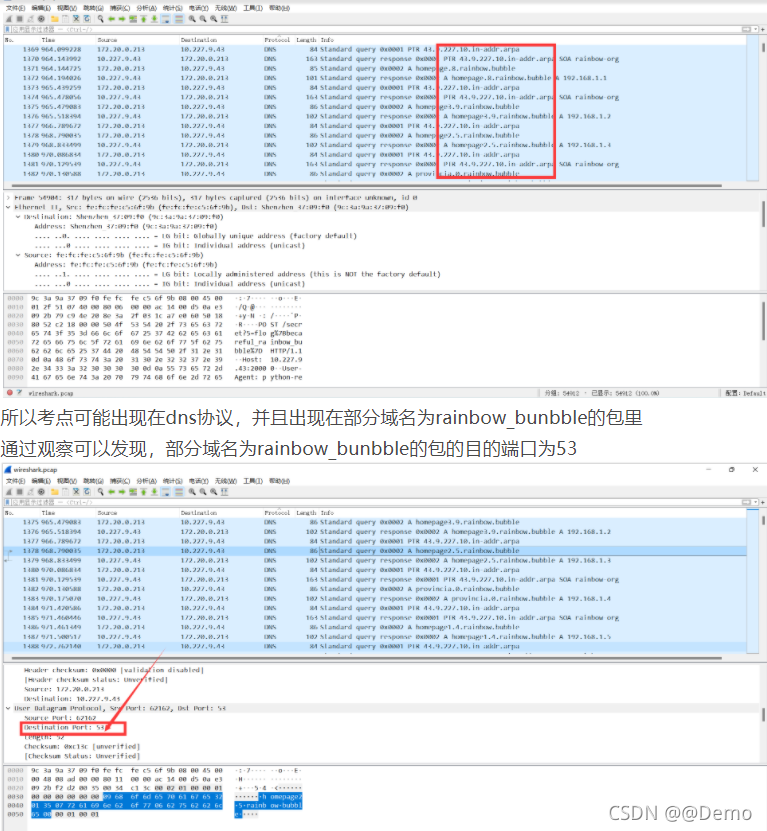
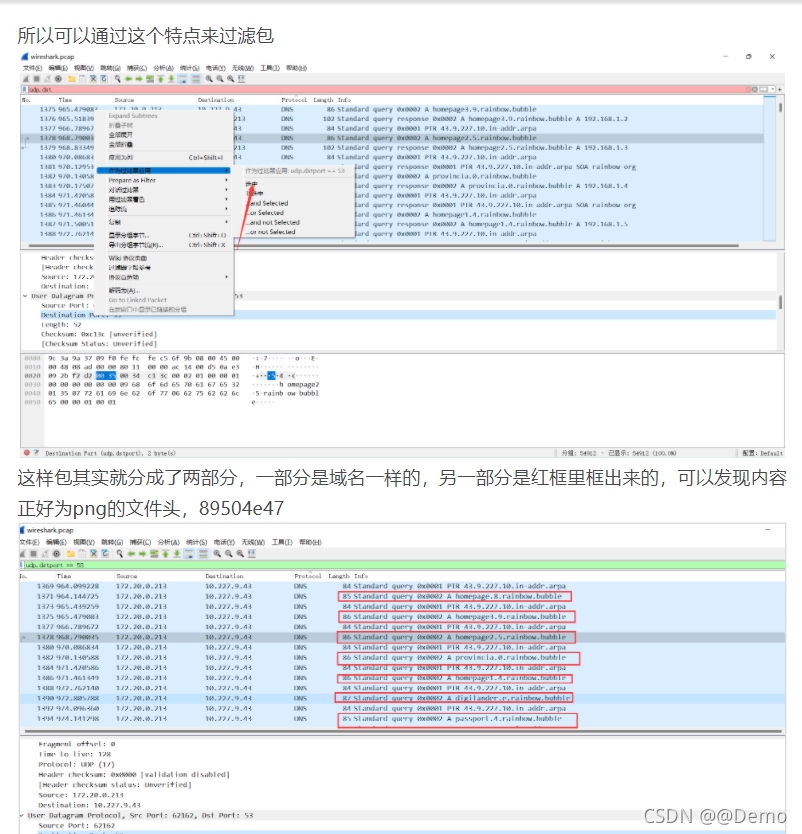
现在要做的就是提取这部分数据包的单独这个字符了
因为我们没法把多余的包给过滤掉,所以只能先提取出来。
所以提取的思路就是,要提取的内容为dns.qry.name,条件就是目的端口为53也就是 udp.dst==53,所以tshark语句为
tshark -r wireshark.pcap -T fields -e dns.qry.name -Y 'udp.dstport==53' > data.txt
提取一下得到
txt = open('data.txt','r').read()
txt = txt.replace('43.9.227.10.in-addr.arpa','')
txt = txt.split('\n')
res = ''
for i in txt:
if i == '':
pass
else:
res += str(i[-16])
print(res)
# s = 'provincia.0.rainbow.bubble'
# print(s[-16])
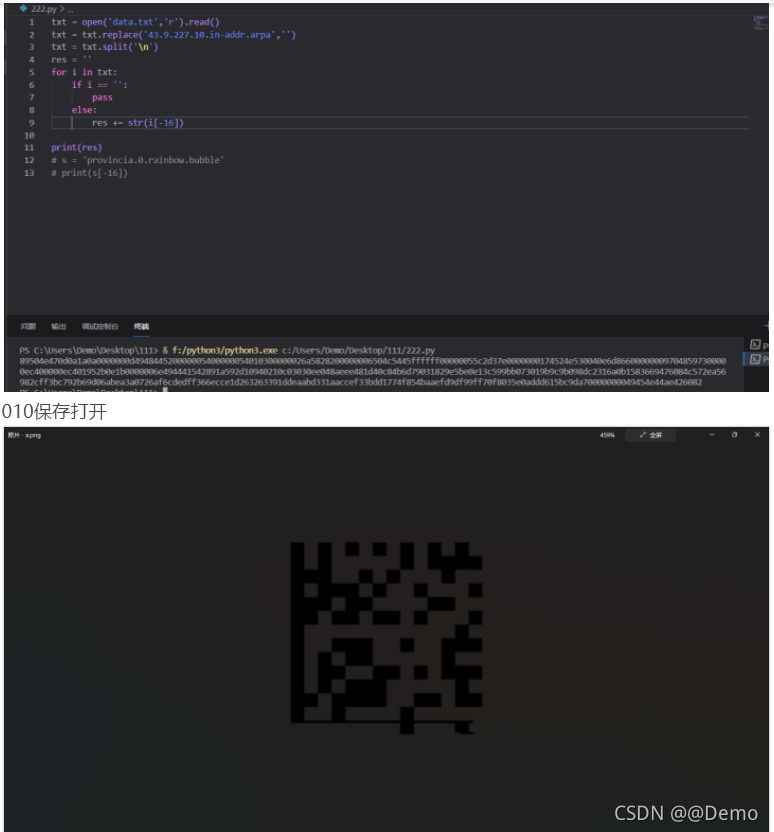
不知道为啥少一位字符,,,
网站扫码https://zxing.org/w/decode(我这个当然是扫不出来的)
扫一下官网wp的
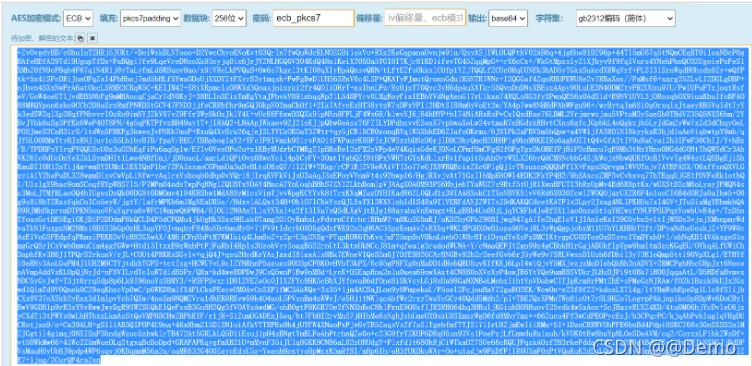
+ZvOvgdyBD/cOhuInTZHRj5JUKt/+DoiWxkDLNTooo+D2YwcChyoKNoKvt03QrIn7fwQuWdcKLNOZGBi1okVu+RXz2KeGqpanaUvnjw9iu/QsyASjIWLOUQFthV02AB6q+4jg6he81DZ96p+44Tl5mU67q5tNQmCEqBT0iIoaNDcP0gHAfeHEfA29Tdl9UgupTfDx+FaBQgi7fe9LqeVreDNsoXk93cyjq0ix6JrJYZNLHGQ0V304KdQ48n1KeiX205Da5TGI8ITKjr81KD1ifevTG45ZqqMpG++rX6cCx+/WkGtMpzslyZiXJkyv9f9fqIVors4YNehPbnQCOZUgoiePxFeS1XMhZ0fN9cPBqh4F67q1N4R1j8yTaLyfmLd8RSunv9ao/x9iVRcLkPVQuS+Ow6s7kgcl3tKI08qXlyEpAQnsvQRN/tLftEZfsOkkxlCOfp1YZjTQQLfZCUc0HqUUNEk3hAD5yTGkxSukcdXRWqVrf+PLSI3lSrnWqdHOhsdn8Zy+wQfPtk+5z4iSPcDRiJnnOPqZxI4PbHbnj7md5bHLf5YwaODoUjXXDYZtFXyrS3ytmqsh+FwFgBwDlUHS6SRnV6c4LSP+QKATyFJmutQrnnnGduiH5NTRIWNc+I2QGGaf4ZqoRHUFEWU8e2v7RBaXoc//PaMsf6+xarg25ZLvLIZDGLgDBP+oJhvn4SXxNwPrA6atOkcL5RMR3CRqW5C+KEIJM42+S8iXRpmclsO8WXd3Qoasjnizzki2fr4QOIiDHrT+nsIbnLFz/Rs0jzT70Qyc3yH6dpAuXATkr55QvnDnDNsXBEszAApy90LuUE3N40DMZtyPRZUUzu97U/PwlUPuFTzjoutRsfeV/GoW4oeUTljvdEB5NbFg9mMHAocqCjaCr7dN0KyJ+38ELlnXCizTmRgYtaJFbvkV89inhqqWp2lL548PYrv0LMgEoyFizlEBbYVdNgAenG17rUikxn74RQLo8G3fyXPwnQE56x0AdSid+E9NV1UVL3jORosqbOX9iuaKbuIfoBFAO88MRQYpon6xbo9CCb2D8aSrzRmfPNWDStGCV47FND3jjfeCRRbfhr9mGQJOkpN02maCkOf1+2lk7AfycEzBT38ytzW7xDFxVPIi2HDtSI88m6yVoEt2w/YA4p7ww8NHHdFAhWFgu96+/wrBytqIm6Si0gOrxqlxJtaeyRB5VuIdt7yYk3edSW2qlXp2HqfFNbvvrl0cRo9imNYJZkV87vZ9Ffr3Wy8kOzJklY4U+vUcK6F6xwDXQXk9ipNNn9FFLjF4Wx68/klwvNJ6j84hHVP+bl7ANiARxRsPvCxlQxdEae76LBML2Yrjmrwsjau5VPtuM3ySaeSb0THdVZ35Q5NXS6hm/2YBvJYhk6uSg3PfKk6WeP4OT8PN/4g5qPKTPfvzBH49uy1T+jlRAQ2+LNAApJWkaev9ZJ21sKJjpQbw0eAssT6FZILYDPdhsvvESeuX7ypbwaXeLw24vtmaR7nBGdzkRHvtCXns6gfcJGpbkL4oQgkzjb5LyJdGmZyWw7xZd3dChqyOeLPOSJmeS2CnH3lrS/1tdWn5FHKFg3kweoJvPNKh7msF+RxuQdXvSrk26qjeJSLTYUkOKOaT3ZWtr+qy5jCEl5CE0zonqBYqiW5XbhED6ZIufoOKrms/6JSlPk2aFBV5m5hQpw+a4VW1jfA3ROlNI8kyykxR3bjdiuAnViqbwtpY9mb/qJf5LO0RMwTtyBJxRNJjuy1c55Lh1byB7B/fpaV/EEC/TBBpbogIaY2+YFcIPRlVmzk9SirvFAOitFWPauyK8BPIzJCWSxzbDSzD6rjlDBC3hyQmcHZ0EHFig9knMNKEIRo6agbOZItQ4vGfA2tIV9uNaCyaiZh3IFwF30ChlJ/Y+hBz/E/TPDBPsYIrqPYQQUScU0z3uO2bEqfiPu6aqOg1w/EfIv0VexOFo2u+z1KByMUdrbCTMRg2IpBBsEel2zFM2xVFp4eV4KqizGdeKJDNoLCPmf0mCPg92fOPgTpzDkOBEfPjBiP2cBmcu7qE9Mh3tHzYHno0HGddG0HtThQWSdCr3AbVKZ6Ic0dUcDnYeXZkLSymDHlt1Lwe4NBfUmj/jD0nucL/amrLd1QPiOvz0RwoYcij4p5CyFY+30mtIYghQZf8tBPxNWHTzGYzKdLlxrEv1fupit5uhhOyyWXLXZ6byQdCM8NcbbG4SjkWojxNbwQUKfOcBlVvvTg4W4stLQSBgEjiShKmuDII0H12nTij4m+wm8YSUMcLlEXIQnP1be7ZPA1nsaoCGPmnUa3uSvBLtoU6sQ7/ilZlW+TEkp/rCF1EjZV9eWAiVTISo77eGJX8WRQEcixZXc6PlgQj1rTWsuzcpQQQbFflX+FxpxSQrvgmlWVOTnjv7AYEFASX/O6xffsnQXVLGzyiAiY2hePuDL3Z8wgmDlxvCwVpLiNfw+yAqlrxVsboqb0dhp0vYQri8jlrqKVFkViJxU3aAqJ3xEFoyVVnmVt4s92bwp16/HgjRXvjvAt71GzIlbMpH8OWl4EDK2FkYP4H2/9hSAxcsZMP3vCvbxvq7ThTEqqUjG81fOVFeRk1otbQl/UlslgX9bac9omSCoqfRYpWBS7l5/P7MFm04ndsTwpFqHNglZQUBTxNOAY4HncA7YnUoqhBHhS7ZNIZLkhBomlpVJAAgX0A0M93PS6HbjehTYaWUZ7s9Rtf5tUjR1XwnHFUTI3bRzUpMv4Ed6R8ptKx/wUXStD2cM6oLyayJFMQN4sc3MoLJTMfBLaoOQ4bIUgesDxQk00DG8t0DMOmv4184KHShw1MdA8SyMicsVimTjvvWpgKCYYvk8tTrxKXqMZazDYBlKad86ZL0QLd1z38IAA8XokC1TXoNBVK5ivV6Rd6X030ZcwlZWOQOjarUXZR6F4n1osCI6B4dORJa0aIhw5+O0g9s8i8bTZRxsfqkCnICo5eyW/jgtY/lafrMFKh6m1MgNEaUR5s//HdxvlALQxt34H+0b1O7lCbkVszQJL5xTX13WXNlohId1S4Ra9TlVERFdANJZWITsZ9dKAKQCdcetKATF1x2Lpy2Jxag4NLlPKHUu7xI4GV+JTuSiaMgYEbmkbQA89RJMh0kprvmDTPKN5ouoVFuYqrva6vWFC1WmpwQ6PWB4/8J0Ui2N9AnTLlsYNXnI+k2f13lXu7xQSdLXgVjtBJg188ayahuVnKwmgx+KLgEBb4Un0BjLjqYCRFh4JeRfSX1lao0nze5tiqYHZwsfYNUFPSUPqxVowbUvE4g+/TzD5nTfousGctDE5EgiGKjDiP2DDdmP8kQCLD4F5dCPQMu4jkUgHk3Szx9HLuk0Tamg2OlOyRmhzLyPdvrnCffrbciRHmW2+mRKuSG5mRJ/aKDZhyGPkZ90Bljwq947gAlTeZhqElcVIJIAn1eKxI29G5ybz5yltIjWSDs3vjnjXMbnpmyWdvaTkNlFuxpzNM2NMzi0BXS3bGpOzHL3upYFOJvmqbyF84MoNBc6muMyO+7iFV9tIdcybO9D5gQdxfWK92o2qH6AC3SpzKomAvZvEX5q+WKLMPGHX0wB1oze96VejRL3yWpQgpjobxM11U7bYLKHBbT2ft/DPyaNdbeUoskjZ+YF9W0cAzE1VnG5FEdpfqPKmxiFEKKOvVcH82GXwAX/4M6jCPnNhFtM7WMlkiq4Lkm8oZ+zZp+U5p2NSg+PTqpROW6TbKvxjuF25np8nVBknLoebOiW8rBTs1DyqdYeXsPzDMClKtygpCG0DToxOxD2svcIYmDYzh0+l/nhNqKBI4VAkxgeS1omgGrQSrICxVwb0mwuCim4ggfGWw+Htdi3ItxxE9zWnbPtFjFaRbI4Hpls3UzobVyySougB5S2rnUtU3ktnUkNCcJ81m+qfeaig3radodWUNA+Y/cNmaQEFJtZgn99z4gCBhkH1rGgjABUkflpYpw9hmltm3zcKGqEU/OYkqALfUWiCh3nphfKv3H6J1TPQrS2rkunV/rJL+COUt4PRKKxSGy1v+qjQ4J+qsu2HcdKrYAsJaxdI8iuxAlx8Bk7EWneVIQeSSm0J7DfE9B2GCArBNGEv92b2r2eefGvb6rJ5yWe9v7SRLVwssDlUsh6fDhil3y73E1oQmp5tti90VpXLg1/ETHYfi0eBNy3AoLGuPM4J1UHZM9CTYjtdkhTGPS+tctIsg+HCWUYvL9clZYNRhnP5azues9OO3pCF8KOvHVbT3kPX/6c95gP8FXg0nMaDD1dHobQBU5uvKIfKKj6Lpl4wiQjvY5MXjezjzMoDIehQkBh3nADVX+2RMCPgbHhcUHpJxt6NocenAVmpAddVxKLOpQjNyJd+nF8VILydTcluWTdidB5Pz/QRa+kd4weRDPDwJ9CsQ5wnFlEw9nMBd+LycK+DSEapHnu2n1u0uea69nwXAzt4CN8B0nXVcXyP4owJE6YtYQe9umR8SVDkrJLHsDJPi9t0Bk7iHO0JqqaAtL/D5HDfaHvmvxNDC5yGyJwf+T3jt6rrqSdp8p6Lk9I96noYsSBMY3/+RSFPSvxr1DBlZVEZeOcOJlXZFYc8HK5cBbXJYfovaB6dfOneSiSkVsyLGj8xUa98GaNXNBeLMobxIihtYnVDabwCITJpKrm8rPMtZhE+sPMeGzNJRAw/fO2k1Bxsk9kUJx2Gxwd1QimTd9V0Qnek0CZ9eqKhzcVp0wC/p6WKDRm1fX4FLCkxPEeceUM0AvCnSXF1fMC3AkWQe+3s35+1jm4ACSaJLon9y8FmpekaU/F5oelZPcjouHaY72gaEO2EK/WcwOn+eZ3f8fZZ+kdoxLX7l4g/ltYBmWshEpeDg1Llc8fSlijbCXx8V37nXSkb2yEnx3dImlpvYch7QXw/4neXm9NQMZVra1dhER8RKvw59k4O4uoL5PVsnBm4zWWvJ/e5Hj1tNWlqcAbfWc2rxyTwaYcGCy40Qdd5Mdh2/pI+TBEZQzXPMnTWn8icOt7rSL9HZo7LogvpPAkjnpikoSp8DpWv6DoCBylBwV9GDB1p9rR3xYNvRwwJwyDgR9SWZSUQkElQeFsxB3Gn8H2Qg3fVOAYzAwdMG/ohB0gtF8KGR7Oe2fNNXbRoC8hlFrnE9O0kfIJR3RHO64hq3HRuljKGiuhB0BHuovI25vdk4wSxAos+ScJBasvRUXZ4KD/4tu0M06hjYcDvleU6jzyCXdTi3tPWYsOwLhHTbxzLkmAsStQeVMPH8CHwZBPbKYF/r1jH+S1ZumUGADEnJ5eq/bt7FbHI2rvMnS7jHIbMe6sNgbJshUmeUX9xkU8SXmzzWgD6fd8MbyTmz++66Zucu4Ff3wCdPEOPycEsJ/b3CPqrPC/kjqAbPvhluglqVHgDUCRotjxn9/o+Ca39ALH+gS1liAB3QIPOF4U9na+46xHbmZ15DlSN1uiAfkVTTRFKu9h4jUYFW4XNuoFxFjeGvTE5ZaqsVsZf7aSlTgebfmfTTJSl7l1rU8ZjmEwIiiRMu+5I+1DznCRRWVOhFFE6bnBd4Pdpi0SKC768s3GnSXSS2nlMZJGgtil4gimqj0NXISnP3bndgWzoc5zhwklrTB472At5GRLkLQ5D1iEsuj1pH4sBNgtYmBLFeAhFtrhnQZe0o+c23G9frYZKUF6DRqO5sn93Vs1PoePzjLfUmwduRuinub/kVOK0tEw8huYpNLOeSDeAVM/cq2/CoyxxLFibkZWsDf+vt50WkMw66+41Wc2Z5mWueDLq2tgxqBcBoDpd+GRAFAPKqygfmXB21U+mMynF35iJUIq8GKK9CN86aL02sUHUdgV+Plxfd1t68OhRjCiWTkaU275Ue66cRQUJPqzkAOsf2B3rkeFddaJIMViiq28NgABdHfKy1zhuKWJkNS9GJjBdDPVsMauH0yUbBJ9pdp4WP6sqvj0KBqmmM56a2u/oaMK632G4O0ZeycEdsU5z+YeenhHoztyoBpMsxK5mRfSl/mBp6Ih/eB3fUKDkuWAy+Oo+u1adjw9FkDfFiIR0UXmF0xPtVQaKuK2dLyLQu+NrzFyQSmrmShpVIzOht9sJe4LxxbVIZE7+1jug/2CurQF4raZxn
CLIENT_HANDSHAKE_TRAFFIC_SECRET 137f16f427985d857e067b4fd3bd5402e9fd5ec906055871bf28277b611d9c5c 28217a6fd7929e49b0ade15e376a21e3a3df53196654ccda04445fdeca157343
SERVER_HANDSHAKE_TRAFFIC_SECRET 137f16f427985d857e067b4fd3bd5402e9fd5ec906055871bf28277b611d9c5c db964f3464d3cee88100c5e429ed65402660b56a84127ce4b8806ee690543d2d
CLIENT_HANDSHAKE_TRAFFIC_SECRET 0b4fb220affbcef39618d220d5486133a6d5052b2bf904f8622651fbc38678cb 09b0a9d636bb229b8c359ce987857e5c423996ef60879a366b403dcc93f35f52
SERVER_HANDSHAKE_TRAFFIC_SECRET 0b4fb220affbcef39618d220d5486133a6d5052b2bf904f8622651fbc38678cb 66d8a8a2711968c04153bb5f990c3709f9b5d16cd9c58f2009b3498fd950c63e
CLIENT_TRAFFIC_SECRET_0 137f16f427985d857e067b4fd3bd5402e9fd5ec906055871bf28277b611d9c5c b6f6123d1a42a4cb2c018b8ff7fa728d283703af0d122f521e3dcd97df4e8414
SERVER_TRAFFIC_SECRET_0 137f16f427985d857e067b4fd3bd5402e9fd5ec906055871bf28277b611d9c5c c6422b91b04251001fce99d35db7c376297257221836d19e4f9ae93e5afad357
EXPORTER_SECRET 137f16f427985d857e067b4fd3bd5402e9fd5ec906055871bf28277b611d9c5c b443daf04fbbdf64fe725a911c379e4df00c7df17d2e52567e5bff4d09d33220
CLIENT_TRAFFIC_SECRET_0 0b4fb220affbcef39618d220d5486133a6d5052b2bf904f8622651fbc38678cb c7202d688e7969ce50040054066603fd7c0668437dca550ab21adc1f985d6eac
SERVER_TRAFFIC_SECRET_0 0b4fb220affbcef39618d220d5486133a6d5052b2bf904f8622651fbc38678cb 0c727c1948914a34842df2b168fa1006f3de27c5b2f8542d283d421bd4eae346
EXPORTER_SECRET 0b4fb220affbcef39618d220d5486133a6d5052b2bf904f8622651fbc38678cb e1460bb32f804d8dfcbd318bf8d9d1f5abdd59970d6c6d0cc188568205487e44
CLIENT_HANDSHAKE_TRAFFIC_SECRET dbf6b8159689f89a7207cbdd8b0c6063c92e39062d508b741c9252aea74651fa cb1a589f050efbfc953edacc346d9fda7cb9838f17be93cb5333c013692a1e2b2a3ffdd121e5f2723788bc061f3ba477
SERVER_HANDSHAKE_TRAFFIC_SECRET dbf6b8159689f89a7207cbdd8b0c6063c92e39062d508b741c9252aea74651fa 713ac5e1a42c8912f327f317d4e6524663e46fdd68982b264d89a10c4fb9d016de9e899cfe0f5604d8e0bea606356c5e
CLIENT_HANDSHAKE_TRAFFIC_SECRET 897ebad2564d3b3928705680ac786a1c7ef3ea71e72de0f2d6b48b2af1897b89 74540257c2413c799359bb0332d85067a85eb1046f018a09509ada89cb7f94f815e1c94caa01417e0e03e3b658b5ea3f
SERVER_HANDSHAKE_TRAFFIC_SECRET 897ebad2564d3b3928705680ac786a1c7ef3ea71e72de0f2d6b48b2af1897b89 5779a510ce777aa7d45dca823daa9a67b227fa9f1c903102ef0fcc5d2db0f245093e7f6590da85beff8e7197b02722b7
CLIENT_HANDSHAKE_TRAFFIC_SECRET 80192eea6317c32f14cc0af472472485c3cbfc46432652f882554f17cd23c680 02a6d140011aaaf45816e55838c35a31ca426c2ef093969e15385e60461b3513f4d025749496375f5923baa40fa9f915
SERVER_HANDSHAKE_TRAFFIC_SECRET 80192eea6317c32f14cc0af472472485c3cbfc46432652f882554f17cd23c680 78aff47910dd769ac05ab4af7970be977a1ea9fb93ee97e5f2e019d3ce0e9f03eb1336f0ed72e5fc4866367f240e9366
CLIENT_TRAFFIC_SECRET_0 80192eea6317c32f14cc0af472472485c3cbfc46432652f882554f17cd23c680 1e30da37782480334efdbc34a94e40d1771121162b71630181f4b0135eec064a3f8fac19203492982c43ea53c92c2b86
SERVER_TRAFFIC_SECRET_0 80192eea6317c32f14cc0af472472485c3cbfc46432652f882554f17cd23c680 db72e91cf285d17307ad0487b5ce7a45f8e545a463f396b9657fbffbc63daa7f70c37ecf2bd6205ac5d2534af412b9be
EXPORTER_SECRET 80192eea6317c32f14cc0af472472485c3cbfc46432652f882554f17cd23c680 2493b3e3803ca1ef62952898e2067f37e22387568faf3e8f0072529156af662114508ea0dc3f0385680a81581d851e2b
CLIENT_HANDSHAKE_TRAFFIC_SECRET f401e372d0ac12f84cdeef562b0d30d56120920659d62a2764cc9a39e71659f6 830fdef34900df22a30bed925c06a4c6db8d6f0d8999922d30d8146348d6a2926d11a4b16b706337b59c44bd0e73c1b1
SERVER_HANDSHAKE_TRAFFIC_SECRET f401e372d0ac12f84cdeef562b0d30d56120920659d62a2764cc9a39e71659f6 5eb65c2f2d3f1c6576707ea100a60c57ce749655ae8bef4c0dfdc62cccf8ed1f591f2dcf6102f9f811bf8003034350f0
CLIENT_HANDSHAKE_TRAFFIC_SECRET 526a9b23c7c53d050445cf4f75e36b4eb574242c1109833f8523fd1bc71aee30 81356894cbcf6296f5fafe0c6766871bf92562f1b1835810ccb8f80acdd6bd4b5195a1e4296d8ed556eff
保存为sslkey.log导入