
1.配置各接口的IP地址
(1)配置AR1
[AR1]int LoopBack 0
[AR1-LoopBack0]ip add 3.3.3.3 32
[AR1-GigabitEthernet0/0/0]ip add 10.1.1.3 24
[AR1-GigabitEthernet0/0/1]ip add 20.1.1.3 24
[AR1-GigabitEthernet0/0/2]ip add 10.1.32.3 24
(2)配置AR2
[AR2]int LoopBack 0
[AR2-LoopBack0]ip add 4.4.4.4 32
[AR2-GigabitEthernet0/0/0]ip add 10.1.2.4 24
[AR2-GigabitEthernet0/0/2]ip add 10.1.41.4 24
[AR2-GigabitEthernet0/0/1]ip add 20.1.2.4 24
(3)配置FW1
[FW1]int LoopBack 0
[FW1-LoopBack0]ip add 1.1.1.1 32
[FW1-GigabitEthernet1/0/0]ip add 10.1.1.1 24
[FW1-GigabitEthernet1/0/1]ip add 10.1.3.1 24
[FW1-GigabitEthernet1/0/2]ip add 10.1.14.1 24
[FW1-GigabitEthernet1/0/4]ip add 10.1.41.1 24
[FW1-GigabitEthernet1/0/6]ip add 10.1.12.1 24
(4)配置FW2
[FW2]int LoopBack 0
[FW2-LoopBack0]ip add 2.2.2.2 32
[FW2-GigabitEthernet1/0/0]ip add 10.1.2.2 24
[FW2-GigabitEthernet1/0/1]ip add 10.1.23.2 24
[FW2-GigabitEthernet1/0/2]ip add 10.1.4.2 24
[FW2-GigabitEthernet1/0/3]ip add 10.1.41.2 24
[FW2-GigabitEthernet1/0/6]ip add 10.1.12.2 24
(5)配置LSW1
[LSW1-LoopBack0]ip address 3.3.3.5 32
[LSW1]vlan batch 30 31 32 34 35 36 37
[LSW1-GigabitEthernet0/0/1]port link-type access
[LSW1-GigabitEthernet0/0/1]port default vlan 31
[LSW1-GigabitEthernet0/0/2]port link-type access
[LSW1-GigabitEthernet0/0/2]port default vlan 32
[LSW1-GigabitEthernet0/0/3]port link-type trunk
[LSW1-GigabitEthernet0/0/3]port trunk allow-pass vlan 35
[LSW1-GigabitEthernet0/0/4]port link-type trunk
[LSW1-GigabitEthernet0/0/4]port trunk allow-pass vlan 36
[LSW1-GigabitEthernet0/0/5]port link-type access
[LSW1-GigabitEthernet0/0/5]port default vlan 30
[LSW1-GigabitEthernet0/0/6]port link-type trunk
[LSW1-GigabitEthernet0/0/6]port trunk allow-pass vlan all
[LSW1-Vlanif31]ip add 10.1.3.3 24
[LSW1-Vlanif32]ip add 10.1.23.3 24
[LSW1-Vlanif35]ip add 10.1.5.3 24
[LSW1-Vlanif36]ip add 10.1.36.3 24
[LSW1-Vlanif37]ip add 10.1.7.3 24
[LSW1-Vlanif34]ip add 10.1.34.3 24
(6)配置LSW2
[LSW2-LoopBack0]ip add 4.4.4.6 32
[LSW2]vlan batch 41 to 43 45 46
[LSW2-GigabitEthernet0/0/1]port link-type access
[LSW2-GigabitEthernet0/0/1]port default vlan 41
[LSW2-GigabitEthernet0/0/2]port link-type access
[LSW2-GigabitEthernet0/0/2]port default vlan 42
[LSW2-GigabitEthernet0/0/3]port link-type trunk
[LSW2-GigabitEthernet0/0/3]port trunk allow-pass vlan 45
[LSW2-GigabitEthernet0/0/4]port link-type trunk
[LSW2-GigabitEthernet0/0/4]port trunk allow-pass vlan 46
[LSW2-GigabitEthernet0/0/6]port link-type trunk
[LSW2-GigabitEthernet0/0/6]port trunk allow-pass vlan all
[LSW2-Vlanif41]ip add 10.1.14.4 24
[LSW2-Vlanif42]ip add 10.1.4.4 24
[LSW2-Vlanif45]ip add 10.1.45.4 24
[LSW2-Vlanif46]ip add 10.1.46.4 24
[LSW2-Vlanif43]ip add 10.1.43.4 24
(7)配置LSW3
[LSW3-LoopBack0]ip add 5.5.5.3 32
[LSW3]vlan batch 10 35 45
[LSW3-GigabitEthernet0/0/1]port link-type trunk
[LSW3-GigabitEthernet0/0/1]port trunk allow-pass vlan 10 35
[LSW3-GigabitEthernet0/0/2]port link-type trunk
[LSW3-GigabitEthernet0/0/2]port trunk allow-pass vlan 10 45
[LSW3-GigabitEthernet0/0/3]port link-type access
[LSW3-GigabitEthernet0/0/3]port default vlan 10
[LSW3-GigabitEthernet0/0/3]stp edged-port enable
[LSW3-Vlanif10]ip add 10.1.10.5 24
[LSW3-Vlanif35]ip add 10.1.5.5 24
[LSW3-Vlanif45]ip add 10.1.45.5 24
[LSW3]stp bpdu-protection //配置BPDU保护功能,加强网络的稳定性
(8)配置LSW4
[LSW4-LoopBack0]ip add 6.6.6.4 32
[LSW4]vlan batch 20 36 46
[LSW4-GigabitEthernet0/0/1]port link-type trunk
[LSW4-GigabitEthernet0/0/1]port trunk allow-pass vlan 20 36
[LSW4-GigabitEthernet0/0/2]port link-type trunk
[LSW4-GigabitEthernet0/0/2]port trunk allow-pass vlan 20 46
[LSW4-GigabitEthernet0/0/3]port link-type access
[LSW4-GigabitEthernet0/0/3]port default vlan 20
[LSW4-GigabitEthernet0/0/3]stp edged-port enable
[LSW4-Vlanif20]ip add 10.1.20.6 24
[LSW4-Vlanif36]ip add 10.1.36.6 24
[LSW4-Vlanif46]ip add 10.1.6.6 24
[LSW4]stp bpdu-protection //配置BPDU保护功能,加强网络的稳定性
(9)配置AR3
[AR3-GigabitEthernet0/0/1]ip add 20.1.1.1 24
[AR3-GigabitEthernet0/0/2]ip add 20.1.2.1 24
[AR3-LoopBack0]ip add 10.10.10.10 32
2.配置防火墙
(1)将各接口加入到安全区域
[FW1]firewall zone trust
[FW1-zone-trust]add interface g1/0/1
[FW1-zone-trust]add interface g1/0/2
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface g1/0/0
[FW1-zone-untrust]add interface g1/0/4
[FW1]firewall zone dmz
[FW1-zone-dmz]add interface g1/0/6
[FW2]firewall zone trust
[FW2-zone-trust]add interface g1/0/1
[FW2-zone-trust]add interface g1/0/2
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface g1/0/0
[FW2-zone-untrust]add interface g1/0/3
[FW2]firewall zone dmz
[FW2-zone-dmz]add interface g1/0/6
(2)配置FW1的安全策略
[FW1]security-policy
[FW1-policy-security]rule name un_to_l //允许untrust区域的设备访问防火墙
[FW1-policy-security-rule-un_to_l]source-zone untrust
[FW1-policy-security-rule-un_to_l]source-address 10.1.1.0 24
[FW1-policy-security-rule-un_to_l]source-address 10.1.41.0 24
[FW1-policy-security-rule-un_to_l]destination-zone local
[FW1-policy-security-rule-un_to_l]action permit
[FW1-policy-security]rule name tr_to_l //允许trunst区域的设备访问防火墙
[FW1-policy-security-rule-tr_to_l]source-zone trust
[FW1-policy-security-rule-tr_to_l]source-address 10.1.3.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.5.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.45.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.7.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.36.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.34.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.10.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.14.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.6.0 24
[FW1-policy-security-rule-tr_to_l]source-address 10.1.20.0 24
[FW1-policy-security-rule-tr_to_l]destination-zone local
[FW1-policy-security-rule-tr_to_l]action permit
[FW1-policy-security]rule name un_to_tr //允许untrust区域设备访问trust区域
[FW1-policy-security-rule-un_to_tr]source-zone untrust
[FW1-policy-security-rule-un_to_tr]source-address 10.1.1.0 24
[FW1-policy-security-rule-un_to_tr]source-address 10.1.41.0 24
[FW1-policy-security-rule-un_to_tr]destination-zone trust
[FW1-policy-security-rule-un_to_tr]action permit
[FW1-policy-security]rule name tr_to_un //允许A访问外网
[FW1-policy-security-rule-tr_to_un]source-zone trust
[FW1-policy-security-rule-tr_to_un]source-address 10.1.10.0 24
[FW1-policy-security-rule-tr_to_un]destination-zone untrust
[FW1-policy-security-rule-tr_to_un]action permit
(3)配置FW2的安全策略
[FW2]security-policy
[FW2-policy-security]rule name un_to_l
[FW2-policy-security-rule-un_to_l]source-zone untrust
[FW2-policy-security-rule-un_to_l]source-address 10.1.2.0 24
[FW2-policy-security-rule-un_to_l]source-address 10.1.32.0 24
[FW2-policy-security-rule-un_to_l]destination-zone local
[FW2-policy-security-rule-un_to_l]action permit
[FW2-policy-security]rule name tr_to_l
[FW2-policy-security-rule-tr_to_l]source-zone trust
[FW2-policy-security-rule-tr_to_l]source-address 10.1.4.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.23.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.34.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.6.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.36.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.20.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.7.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.45.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.5.0 24
[FW2-policy-security-rule-tr_to_l]source-address 10.1.10.0 24
[FW2-policy-security-rule-tr_to_l]destination-zone local
[FW2-policy-security-rule-tr_to_l]action permit
[FW2-policy-security]rule name tr_to_un
[FW2-policy-security-rule-tr_to_un]source-zone trust
[FW2-policy-security-rule-tr_to_un]source-address 10.1.10.0 24
[FW2-policy-security-rule-tr_to_un]destination-zone untrust
[FW2-policy-security-rule-tr_to_un]action permit
[FW2-policy-security]rule name un_to_tr
[FW2-policy-security-rule-un_to_tr]source-zone untrust
[FW2-policy-security-rule-un_to_tr]source-address 10.1.2.0 24
[FW2-policy-security-rule-un_to_tr]source-address 10.1.32.0 24
[FW2-policy-security-rule-un_to_tr]destination-zone trust
[FW2-policy-security-rule-un_to_tr]action permit
3.部署路由
(1)配置area 0区域
[AR1]router id 3.3.3.3
[AR1]ospf 1
[AR1-ospf-1]area 0
[AR1-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 10.1.32.0 0.0.0.255
[AR2]router id 4.4.4.4
[AR2]ospf 1
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]network 10.1.2.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 10.1.41.0 0.0.0.255
[FW1]router id 1.1.1.1
[FW1]ospf 1
[FW1-ospf-1]area 0
[FW1-ospf-1-area-0.0.0.0]network 10.1.1.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 10.1.41.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 10.1.14.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 10.1.3.0 0.0.0.255
[FW2]router id 2.2.2.2
[FW2]ospf 1
[FW2-ospf-1]area 0
[FW2-ospf-1-area-0.0.0.0]network 10.1.2.0 0.0.0.255
[FW2-ospf-1-area-0.0.0.0]network 10.1.32.0 0.0.0.255
[FW2-ospf-1-area-0.0.0.0]network 10.1.23.0 0.0.0.255
[FW2-ospf-1-area-0.0.0.0]network 10.1.4.0 0.0.0.255
[LSW1]router id 3.3.3.5
[LSW1]ospf 1
[LSW1-ospf-1]area 0
[LSW1-ospf-1-area-0.0.0.0]network 10.1.3.0 0.0.0.255
[LSW1-ospf-1-area-0.0.0.0]network 10.1.23.0 0.0.0.255
[LSW1-ospf-1-area-0.0.0.0]network 10.1.7.0 0.0.0.255
[LSW2]router id 4.4.4.6
[LSW2]ospf 1
[LSW2-ospf-1]area 0
[LSW2-ospf-1-area-0.0.0.0]network 10.1.4.0 0.0.0.255
[LSW2-ospf-1-area-0.0.0.0]network 10.1.14.0 0.0.0.255
(2)配置area 1区域
[LSW1]ospf 1
[LSW1-ospf-1]area 1
[LSW1-ospf-1-area-0.0.0.1]network 10.1.5.0 0.0.0.255
[LSW1-ospf-1-area-0.0.0.1]nssa
[LSW2]ospf 1
[LSW2-ospf-1]area 1
[LSW2-ospf-1-area-0.0.0.1]
[LSW2-ospf-1-area-0.0.0.1]network 10.1.45.0 0.0.0.255
[LSW2-ospf-1-area-0.0.0.1]nssa
[LSW3]ospf 1
[LSW3-ospf-1]area 1
[LSW3-ospf-1-area-0.0.0.1]network 10.1.5.0 0.0.0.255
[LSW3-ospf-1-area-0.0.0.1]network 10.1.45.0 0.0.0.255
[LSW3-ospf-1-area-0.0.0.1]network 10.1.10.0 0.0.0.255
(3)配置area 2区域
[LSW2-ospf-1]area 2
[LSW2-ospf-1-area-0.0.0.2]network 10.1.6.0 0.0.0.255
[LSW2-ospf-1-area-0.0.0.2]nssa
[LSW4]ospf 1
[LSW4-ospf-1]area 2
[LSW4-ospf-1-area-0.0.0.2]network 10.1.6.0 0.0.0.255
[LSW4-ospf-1-area-0.0.0.2]network 10.1.36.0 0.0.0.255
[LSW4-ospf-1-area-0.0.0.2]nssa
[LSW1-ospf-1]area 2
[LSW1-ospf-1-area-0.0.0.2]network 10.1.36.0 0.0.0.255
[LSW1-ospf-1-area-0.0.0.2]nssa
4.配置缺省路由:负载均衡方式
[AR1]ip route-static 0.0.0.0 0.0.0.0 20.1.1.1
[AR2]ip route-static 0.0.0.0 0.0.0.0 20.1.2.1
[FW1]ip route-static 0.0.0.0 0.0.0.0 10.1.1.3
[FW1]ip route-static 0.0.0.0 0.0.0.0 10.1.41.4
[FW2]ip route-static 0.0.0.0 0.0.0.0 10.1.2.4
[FW2]ip route-static 0.0.0.0 0.0.0.0 10.1.32.4
[LSW1]ip route-static 0.0.0.0 0.0.0.0 10.1.3.1
[LSW1]ip route-static 0.0.0.0 0.0.0.0 10.1.23.2
[LSW2]ip route-static 0.0.0.0 0.0.0.0 10.1.4.2
[LSW2]ip route-static 0.0.0.0 0.0.0.0 10.1.14.1
5.检查配置结果



-
配置DHCP
(1)配置LSW1
[LSW1]dhcp enable
[LSW1]int Vlanif 35 //为A配置IP地址
[LSW1-Vlanif35]dhcp select global
[LSW1]int Vlanif 36 //为B配置IP地址
[LSW1-Vlanif36]dhcp select global
[LSW1]ip pool poola //A的地址池
[LSW1-ip-pool-poola]network 10.1.10.0 mask 24
[LSW1-ip-pool-poola]gateway-list 10.1.10.5
[LSW1]ip pool poolb //B的地址池
[LSW1-ip-pool-poolb]network 10.1.20.0 mask 24
[LSW1-ip-pool-poolb]gateway-list 10.1.20.6
(2)配置LSW2
[LSW2]dhcp enable
[LSW2]int Vlanif 46
[LSW2-Vlanif46]dhcp select global
[LSW2]int Vlanif 45
[LSW2-Vlanif45]dhcp select global
[LSW2]ip pool poola
[LSW2-ip-pool-poola]network 10.1.10.0 mask 24
[LSW2-ip-pool-poola]gateway-list 10.1.10.5
[LSW2]ip pool poolb
[LSW2-ip-pool-poolb]network 10.1.20.0 mask 24
[LSW2-ip-pool-poolb]gateway-list 10.1.20.6
(3)配置DHCP中继
[LSW3]dhcp enable
[LSW3-Vlanif10]dhcp select relay
[LSW3-Vlanif10]dhcp relay server-ip 10.1.5.3
[LSW3-Vlanif10]dhcp relay server-ip 10.1.45.4
[LSW4]dhcp enable
[LSW4]int Vlanif 20
[LSW4-Vlanif20]dhcp select relay
[LSW4-Vlanif20]dhcp relay server-ip 10.1.6.4
[LSW4-Vlanif20]dhcp relay server-ip 10.1.36.3 -
在出口路由器配置NAT
(1)在AR1上配置NAT
[AR1]nat address-group 1 20.1.1.4 20.1.1.10
[AR1]acl 2000
[AR1-acl-basic-2000]rule permit source 10.1.10.0 0.0.0.255
[AR1-GigabitEthernet0/0/1]nat outbound 2000 address-group 1
(2)在AR2上配置NAT
[AR2]nat address-group 1 20.1.1.4 20.1.1.10
[AR2]acl 2000
[AR2-acl-basic-2000]rule permit source 10.1.10.0 0.0.0.255
[AR2-GigabitEthernet0/0/1]nat outbound 2000 address-group 1
(3)配置NAT server,保证外部用户能够访问内网HTTP服务器
[AR1-GigabitEthernet0/0/1]nat server protocol tcp global 20.1.1.2 inside 10.1.7.30
[AR2-GigabitEthernet0/0/1]nat server protocol tcp global 20.1.2.3 inside 10.1.7.30
8.配置防火墙双机热备
(1)在防火墙上配置VGMP组监控上下行业务接口
[FW1]hrp track interface GigabitEthernet 1/0/0
[FW1]hrp track interface GigabitEthernet 1/0/4
[FW1]hrp track interface GigabitEthernet 1/0/2
[FW1]hrp track interface GigabitEthernet 1/0/1
[FW2]hrp track interface GigabitEthernet 1/0/0
[FW2]hrp track interface GigabitEthernet 1/0/3
[FW2]hrp track interface GigabitEthernet 1/0/1
[FW2]hrp track interface GigabitEthernet 1/0/2
(2)在防火墙配置根据HRP状态调整OSPF的相关COST值的功能
[FW1]hrp adjust ospf-cost enable
[FW2]hrp adjust ospf-cost enable
(3)在防火墙上指定心跳接口,启用双机热备
[FW1]hrp interface g1/0/6 remote 10.1.12.2
[FW1]hrp enable //启动HRP双机热备份功能
HRP_S[FW1]hrp mirror session enable //启动会话快速备份功能, 防火墙工作于双机热备份组网环境下,如果报文的来回路径不一致,通过配置会话快速备份功能,能够保证主用防火墙的会话信息立即同步至备用防火墙。当主用防火墙出现故障时,报文能够被备用防火墙转发出去,从而保证内外部用户的会话不中断
[FW2]hrp interface g1/0/6 remote 10.1.12.1
[FW2]hrp enable
HRP_S[FW2]hrp mirror session enable
(4)检查配置结果:本端和对端优先级相同,且状态都为active,说明两台防火墙处于负载分担状态
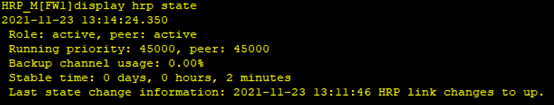
-
防火墙配置攻击防范:对于内部服务器,可能会遭受SYN Flood、HTTP Flood攻击,所以在防火墙上开启SYN Flood、HTTP Flood攻击防范功能,保护内部服务器不受攻击。
HRP_M[FW1]firewall defend udp-flood base-session max-rate 1500 (+B)
HRP_M[FW1]firewall defend icmp-unreachable enable (+B)
HRP_M[FW1]firewall blacklist enable (+B)
HRP_M[FW1]firewall blacklist enable (+B)
HRP_M[FW1]firewall defend ip-sweep max-rate 4000 (+B)
HRP_M[FW1]firewall defend port-scan enable (+B)
HRP_M[FW1]firewall defend port-scan max-rate 4000 (+B)
HRP_M[FW1]firewall defend ip-fragment enable (+B)
HRP_M[FW1]firewall defend ip-spoofing enable (+B)
10.验证:A可以ping 通外网
