一.LVS
????????LVS(Linux Virtual Server)即Linux虚拟服务器,是一个虚拟的服务器集群系统,在unix/linux平台下实现负载均衡集群功能。LVS是一种集群(Cluster)技术,采用IP负载均衡技术和基于内容请求分发技术。调度器具有很好的吞吐率,将请求均衡地转移到不同的服务器上执行,且调度器自动屏蔽掉服务器的故障,从而将一组服务器构成一个高性能的、高可用的虚拟服务器。整个服务器集群的结构对客户是透明的,而且无需修改客户端和服务器端的程序。
????????根据LVS工作模式的不同,真实服务器会选择不同的方式将用户需要的数据发送到终端用户,其工作模式分为NAT模式、TUN模式、以及DR模式。
4层Load Balance
– 基于传输层信息进行 调度
– 调度算法:WRR/WLC 等
– 工作模式:NAT/DR/TUNNEL
– 传输协议:TCP/UDP
二、使用DR模式实现负载均衡
1.实验环境配置:server1为调度器,负载流量均衡(基于4层即传输层进行调度,调度算法有WRR/WLC等,传输协议为TCP/UDP),server2和server3为真实服务器节点。
2.server1安装ipvsadm(用于用户端管理LVS的策略规则)
[root@server1 ~]# yum install -y ipvsadm
3.?? ipvsadm -A 添加规则;-t tcp协议;-s 调度;rr 轮叫
-a向tcp虚拟服务添加
-r real server
-g 直连即DR模式
ipvsadm -ln:查看当前连接情况(-ln不用解析)
[root@server1 ~]# ipvsadm -L
[root@server1 ~]# ipvsadm -Ln
[root@server1 ~]# ipvsadm -ln ##查看当前连接情况(-ln不用解析)
[root@server1 ~]# ipvsadm -A -t 172.25.52.100:80 -s rr
[root@server1 ~]# ipvsadm -a -t 172.25.52.100:80 -r 172.25.52.2:80 -g
[root@server1 ~]# ipvsadm -a -t 172.25.52.100:80 -r 172.25.52.3:80 -g
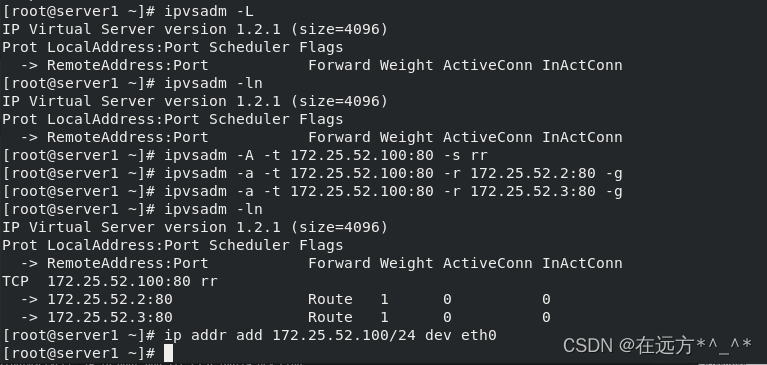
4.书写策略:在server1上添加虚拟一个对外访问的IP:172.25.52.100(vip),即提供虚拟服务的ip地址,也可以直接用原有IP,但最好独立出来?
[root@server1 ~]# ip addr add 172.25.52.100/24 dev eth0
[root@server1 ~]# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
? -> RemoteAddress:Port?????????? Forward Weight ActiveConn InActConn
TCP? 172.25.52.100:80 rr
? -> 172.25.52.2:80?????????????? Route?? 1????? 0????????? 0??????? ?
? -> 172.25.52.3:80?????????????? Route?? 1????? 0????????? 0????????
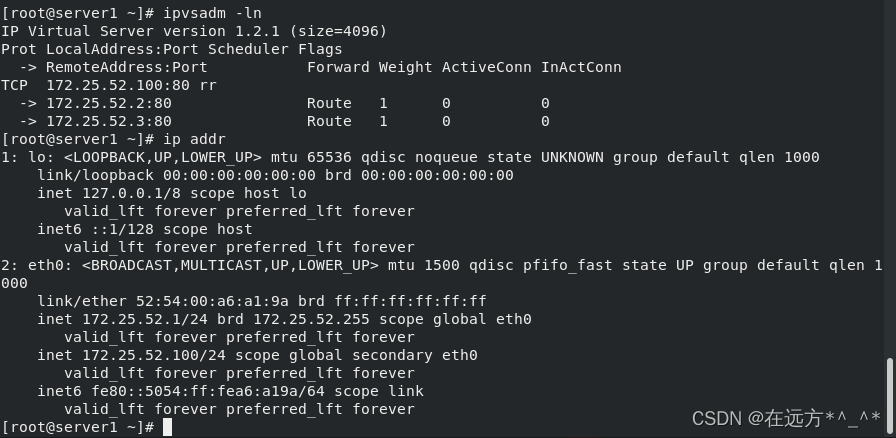
?在server2和server3中:
安装httpd服务,编写默认访问页面,开启服务
给server2和server3分别添加vip 172.25.52.100/32
[root@server2 ~]# yum install -y httpd
[root@server2 ~]# echo server2 >/var/www/html/index.html
[root@server2 ~]# systemctl start httpd
[root@server2 ~]# curl localhost
server2
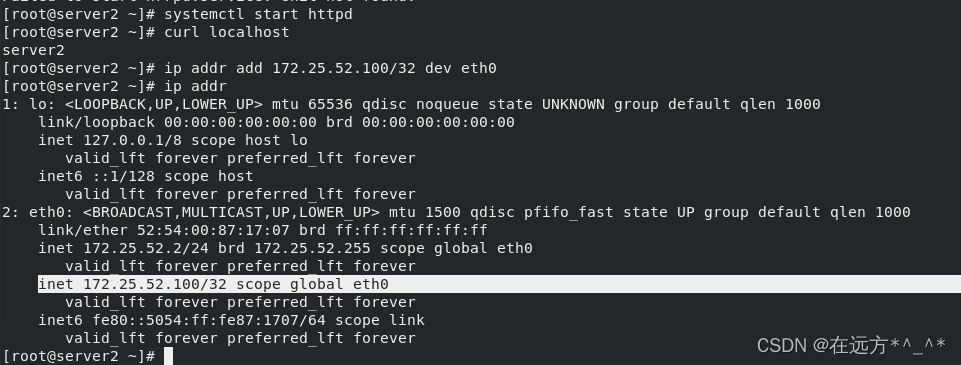
[root@server2 ~]# ip addr add 172.25.52.100/32 dev eth0
[root@server3 ~]# yum install -y httpd
[root@server3 ~]# echo server3 >/var/www/html/index.html
[root@server3 ~]# systemctl restart httpd
[root@server3 ~]# curl localhost
server3
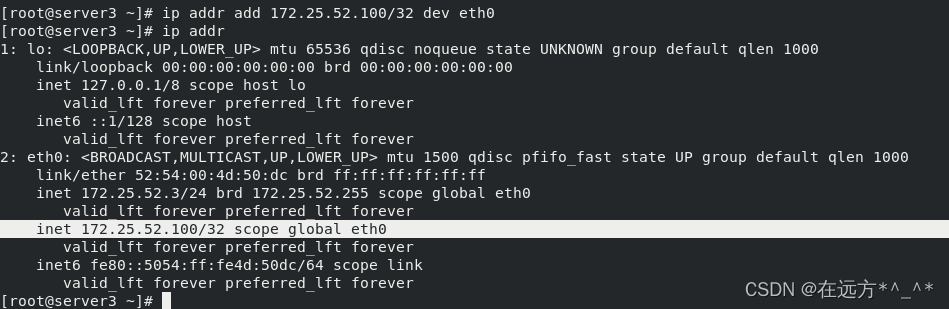
[root@server3 ~]# ip addr add 172.25.52.100/32 dev eth0
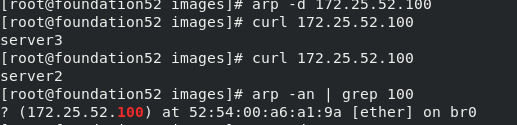
?此时在真机中(客户端)curl 172.25.52.100,出现轮叫:
curl 172.25.52.100
curl 172.25.52.100
curl 172.25.52.100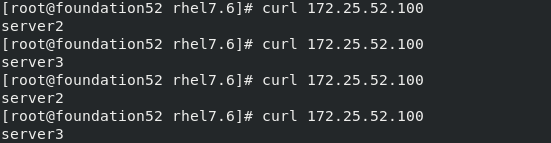
ARP协议是将IP地址映射为MAC地址的协议,其在协议上使用ARP请求及ARP应答报文来实现。
arp -an | grep 100 ##查看本地ARP缓存的172.25.52.100对应的MAC地址为调度器server1的地址
arp -d 172.25.52.100 ##删除指定虚拟IP的ARP缓存
ping 172.25.52.100
arp -d是删除ARP缓存列表的命令,可以删除所有的ARP缓存,也可以删除指定的ARP缓存
此时使用arp -an查看本地ARP缓存的172.25.52.100对应的MAC地址为调度器server1的地址,当真机执行arp -d 删除指定虚拟IP的ARP缓存后,此时不能过滤得到172.25.52.100的MAC地址。再次ping之后又可以得到(是server2的地址),但不是调度器的地址(谁先响应就缓存谁的MAC地址) 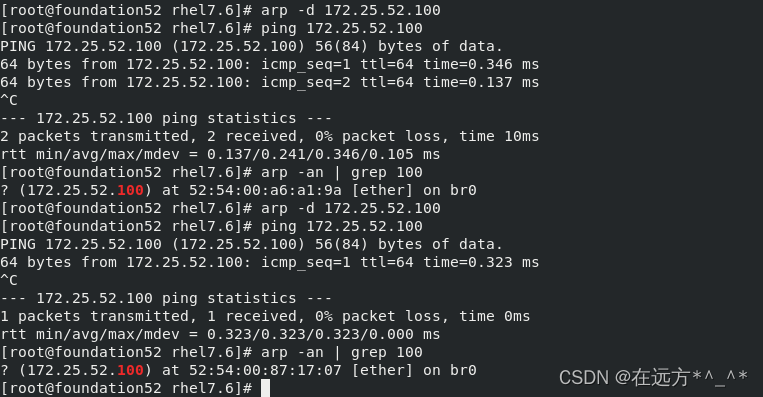
?为了解决这一问题,给server2和server3安装ARP防火墙arptables(用于管理内核中的ARP包过滤规则表)
[root@server2 ~]# yum install -y arptables
[root@server2 ~]# arptables -L
Chain INPUT (policy ACCEPT)
Chain OUTPUT (policy ACCEPT)
Chain FORWARD (policy ACCEPT)
[root@server3 ~]# yum install -y arptables
[root@server3 ~]# arptables -L
Chain INPUT (policy ACCEPT)
Chain OUTPUT (policy ACCEPT)
Chain FORWARD (policy ACCEPT)
设定APR配置规则,DR模式要求服务器节点应该禁掉设备的APR响应
arptable_filter 只有一个表 filter ,不指定 -t 表名时默认就是 filter 表。
filter表有三个链,一个是INPUT,表示外面发进来的ARP包;另外一个是OUTPUT,表示本机发出的ARP包;第三个是FORWARD,转发ARP包。
-A:向规则链中追加规则;
-d:指定要匹配ARP包的目的IP地址;
-j:指定满足添加的规则时执行的动作;
-s:指定要匹配ARP包的源ip地址;
-g:直连
-r:真实服务器地址
当数据包的目的地址是100时就丢弃该数据包,当从本机发送出的数据包IP是100时,mangle转换数据包源地址,伪装源地址IP为172.25.52.2。
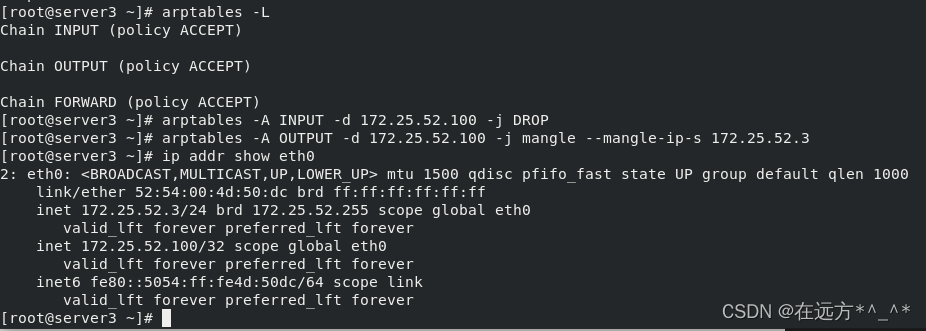
[root@server2 ~]# arptables -A INPUT -d 172.25.52.100 -j DROP
[root@server2 ~]# arptables -A OUTPUT -d 172.25.52.100 -j mangle --mangle-ip-s 172.25.52.2
[root@server2 ~]# ip addr show eth0
[root@server3 ~]# arptables -A INPUT -d 172.25.52.100 -j DROP
[root@server3 ~]# arptables -A OUTPUT -d 172.25.52.100 -j mangle --mangle-ip-s 172.25.52.3
[root@server3 ~]# ip addr show eth0
?
 ?
?
?在客户端访问: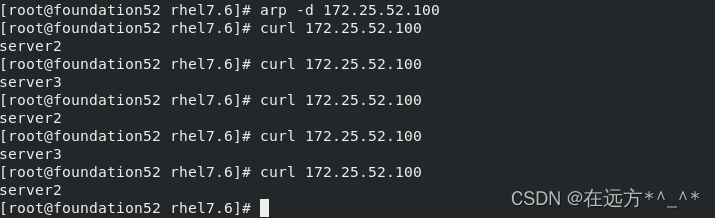
?四.高可用
创建虚拟机test4,设置主机名和ip等:
[root@server1 ~]# ssh-keygen
[root@server1 ~]# ssh-copy-id server4
1.健康检测
ipvsadm没有健康检测功能,即检测策略对应的后端服务是否正常,因此我们需要安装keepalived?
[root@server1 ~]# yum install -y keepalived?? ##健康检测
[root@server1 ~]# yum install -y mailx??? ##邮件
2.编写keepalived配置文件:
[root@server1 ~]# cd /etc/keepalived/
[root@server1 keepalived]# ls
keepalived.conf
[root@server1 keepalived]# vi keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
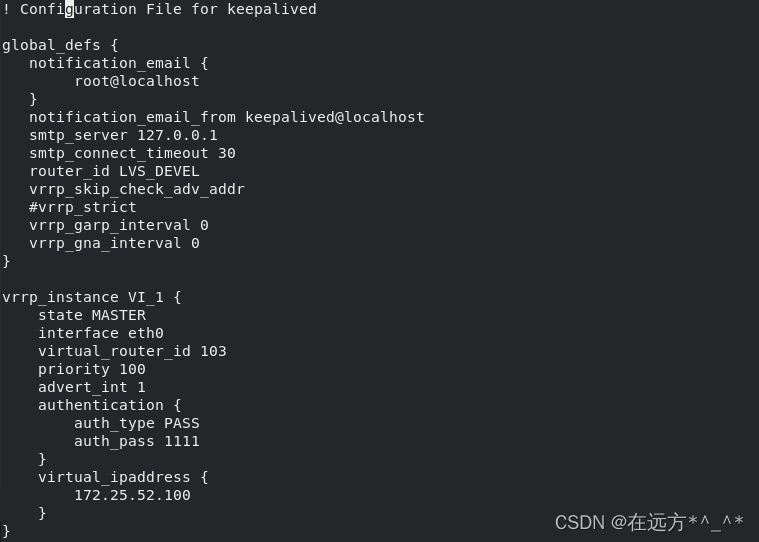
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 103
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.52.100
}
}
virtual_server 172.25.52.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
#persistence_timeout 50
protocol TCP
real_server 172.25.52.2 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
real_server 172.25.52.3 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
}
[root@server1 keepalived]# iptables -A INPUT -d 172.25.52.100 -j DROP
[root@server1 keepalived]# iptables -nL
[root@server1 keepalived]# iptables -F ##清除
[root@server1 keepalived]# iptables -nL
? 
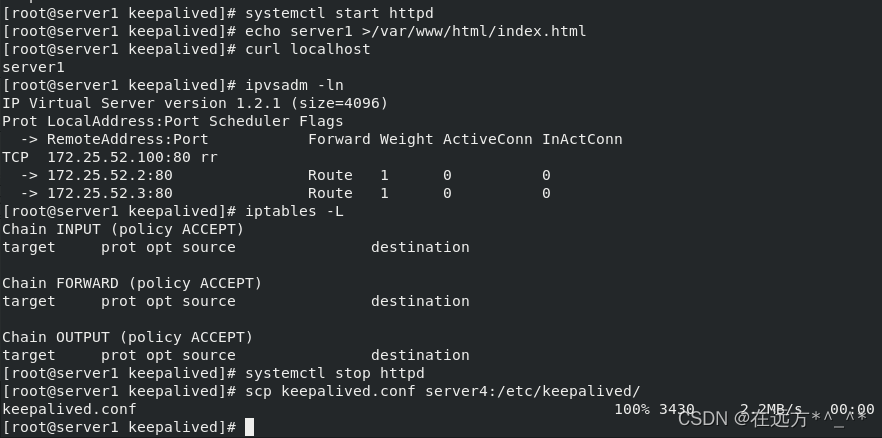
[root@server1 keepalived]# yum install httpd -y
[root@server1 keepalived]# systemctl start httpd
[root@server1 keepalived]# echo server1 >/var/www/html/index.html
[root@server1 keepalived]# curl localhost
server1
[root@server1 keepalived]# ipvsadm -ln
[root@server1 keepalived]# systemctl stop httpd
[root@server1 keepalived]# scp keepalived.conf server4:/etc/keepalived/
3.在主机server4中:
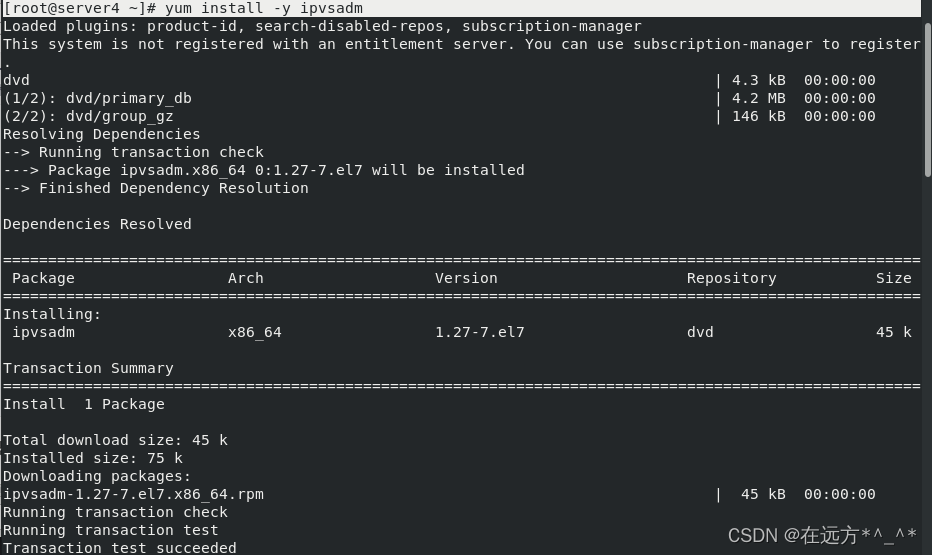
root@server4 ~]# yum install -y ipvsadm
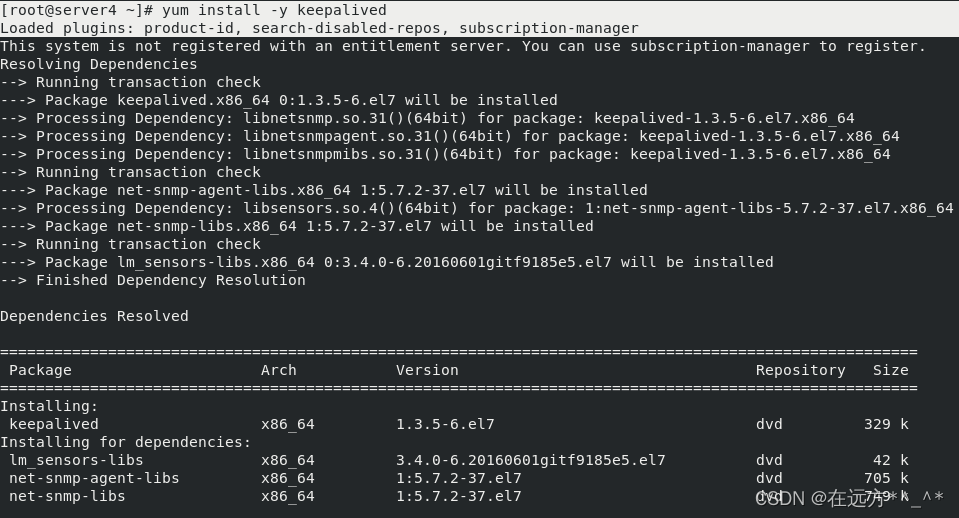
[root@server4 ~]# yum install -y keepalived
?
[root@server4 keepalived]# vi keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
#vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state BACKUP ##备用
interface eth0
virtual_router_id 103
priority 50 ##priority应该小于100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.52.100
}
}
virtual_server 172.25.52.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
#persistence_timeout 50
protocol TCP
real_server 172.25.52.2 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
real_server 172.25.52.3 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
}4. 在调度器server1中:
删掉server1上手动设置的虚拟ip172.25.52.100
ipvsadm -C清除设置的规则,
启动keepalived软件(在配置文件中已设置,需将手动添加的ip删除)
[root@server1 keepalived]# ipvsadm -C ##清除设置的规则
[root@server1 keepalived]# ipvsadm -l ##查看规则
[root@server1 keepalived]# systemctl start keepalived.service ##开启服务
[root@server1 keepalived]# ipvsadm -l
[root@server1 keepalived]# ipvsadm -ln
[root@server1 keepalived]# ip addr del 172.25.52.100/32 dev eth0
[root@server1 keepalived]# ip addr
[root@server1 keepalived]# systemctl restart keepalived.service
[root@server1 keepalived]# ipvsadm -ln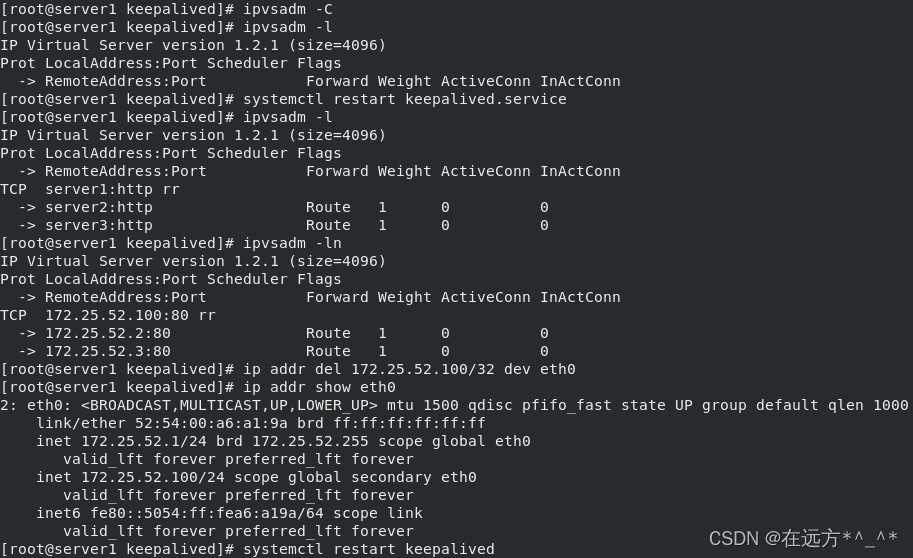
?5.测试
[root@server1 keepalived]# systemctl stop keepalived.service?
[root@server4 keepalived]# systemctl start keepalived.service
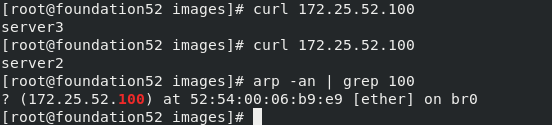
?当server1的keepalived服务停止后,server4是MASTER
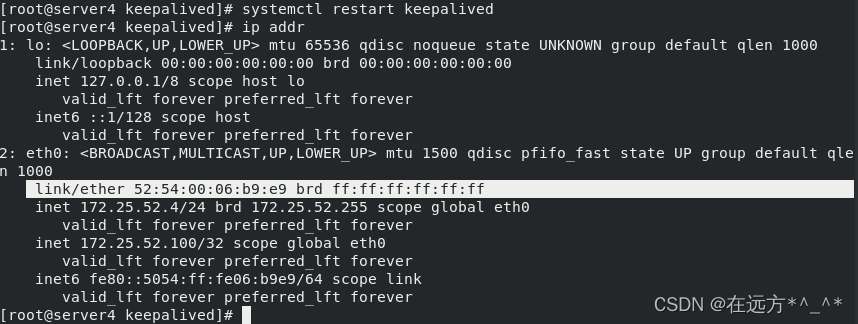
?
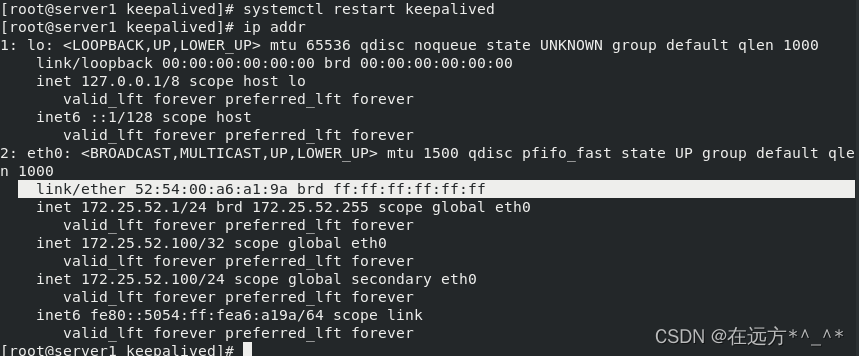
开启server1的 keepalived服务之后,172.25.52.100的MAC地址是server1的MAC地址,此时server4为BACKUP
?
?