openssl的配置文件:/etc/pki/tls/openssl.cnf
三种策略:
match:要求申请填写的信息跟CA设置信息必须一致
optional:可有可无,跟CA设置信息可不一致
supplied:必须填写这项申请信息
openssl部分配置文件参考:
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several ctificates with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
1、创建CA所需要的文件
#生成证书索引数据库文件
touch /etc/pki/CA/index.txt
?
#指定第一个颁发证书的序列号
echo 01 > /etc/pki/CA/serial
2、 生成CA私钥
cd /etc/pki/CA/
umask 066; openssl genrsa -out private/cakey.pem 2048
3、生成CA自签名证书
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
选项说明:
-new:生成新证书签署请求
-x509:专用于CA生成自签证书
-key:生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路径
[root@centos7 CA]#openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:guangzhou
Organization Name (eg, company) [Default Company Ltd]:linuxca
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:ca.linuxca.com
Email Address []:admin@linuxca.com
4、把cacert.pem文件下载到windows桌面:sz cacert.pem,把cacert.pem文件重命名为cacert.pem.cer让windows系统识别。在windows系统上打开证书查看相关信息。
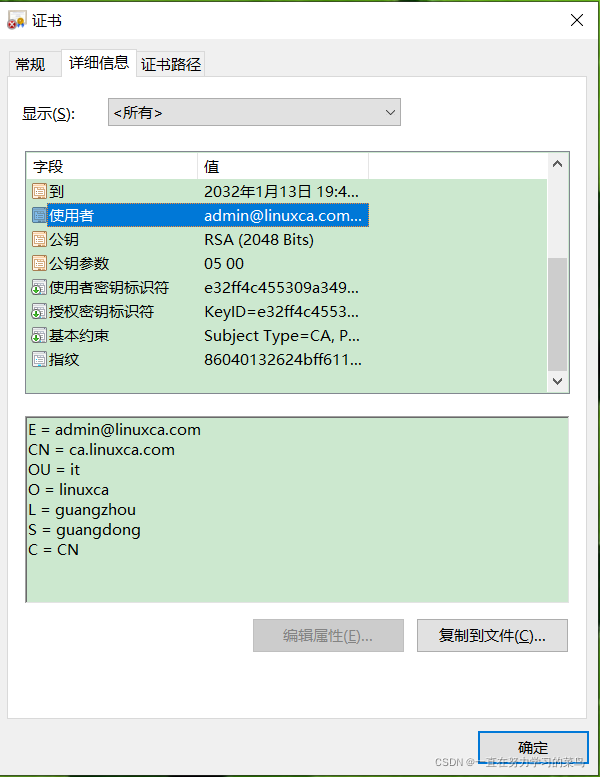
?
5、生成私钥
[root@centos7 CA]#mkdir /data/app1
[root@centos7 CA]#cd /data/app1
[root@centos7 app1]#pwd
/data/app1
[root@centos7 app1]#(umask 066; openssl genrsa -out /data/app1/app1.key 2048)
Generating RSA private key, 2048 bit long modulus
.......+++
............................+++
e is 65537 (0x10001)
6、生成证书申请文件
[root@centos7 app1]#openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:guangzhou
Organization Name (eg, company) [Default Company Ltd]:linuxca
Organizational Unit Name (eg, section) []:sale
Common Name (eg, your name or your server's hostname) []:www.linuxca.com
Email Address []:sale@linuxca.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@centos7 app1]#ll
total 8
-rw------- 1 root root 1062 Jan 15 21:14 app1.csr
-rw------- 1 root root 1675 Jan 15 20:56 app1.key
注意:默认有三项内容必须和CA一致:国家,省份,组织
?
7、颁发证书
[root@centos7 app1]#openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jan 15 13:24:47 2022 GMT
Not After : Oct 11 13:24:47 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = guangdong
organizationName = linuxca
organizationalUnitName = sale
commonName = www.linuxca.com
emailAddress = sale@linuxca.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
DD:05:D9:9D:02:19:DC:37:31:DD:7F:5C:2F:08:CA:D4:F1:1E:2A:AB
X509v3 Authority Key Identifier:
keyid:E3:2F:F4:C4:55:30:9A:34:91:00:03:91:FE:05:4C:BF:6D:D2:90:C1
Certificate is to be certified until Oct 11 13:24:47 2024 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
8、查看指定编号对应证书的有效性
[root@centos7 app1]#tree /etc/pki/CA
/etc/pki/CA
├── cacert.pem
├── certs
│?? └── app1.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│?? └── 01.pem
├── private
│?? └── cakey.pem
├── serial
└── serial.old
4 directories, 9 files
[root@centos7 app1]#cat /etc/pki/CA/index.txt
V 241011132447Z 01 unknown /C=CN/ST=guangdong/O=linuxca/OU=sale/CN=www.linuxca.com/emailAddress=sale@linuxca.com
[root@centos7 app1]#openssl ca -status 01
Using configuration from /etc/pki/tls/openssl.cnf
01=Valid (V)
9、sz /etc/pki/CA/certs/app1.crt,把/etc/pki/CA/certs/app1.crt文件下载到windows桌面,安装证书。
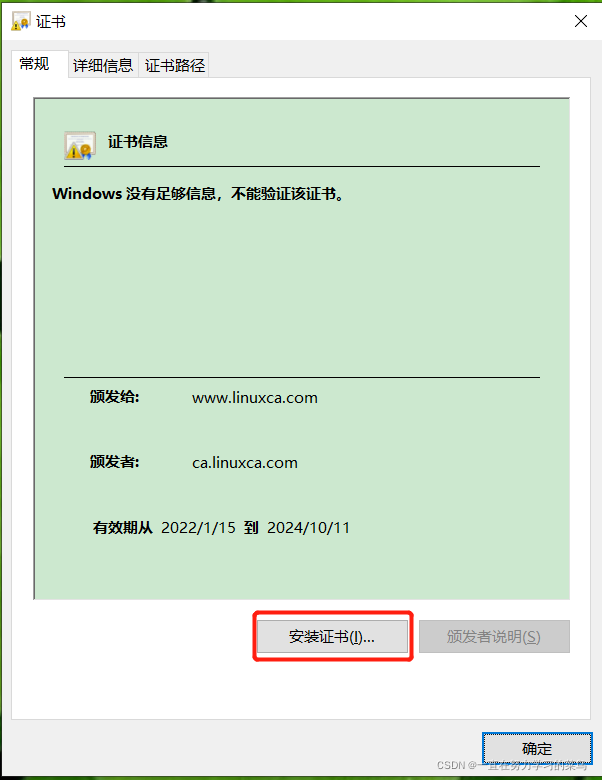
?
?
?
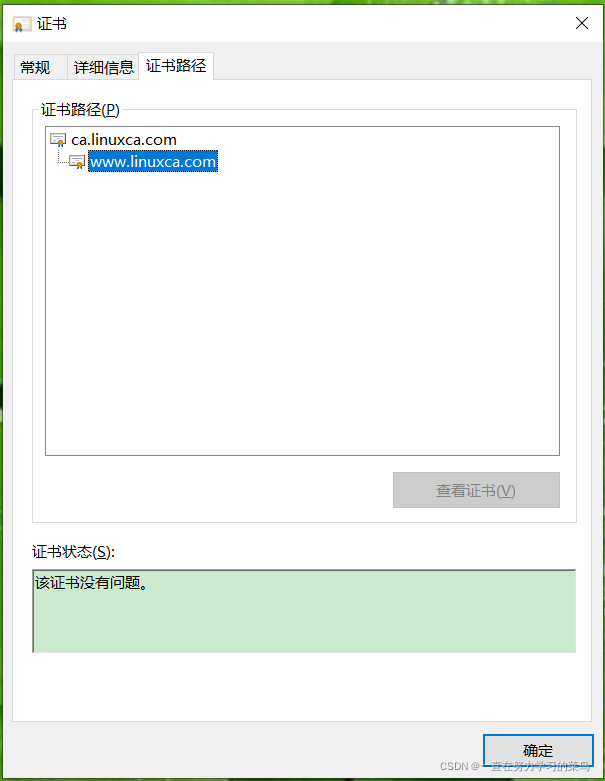
?10、在windows系统上打开app1.crt证书,查看证书状态。
?
?
?