RBAC角色访问控制
参考: https://www.toutiao.com/i6942467217019666952/?wid=1643459986078
ServiceAccount(服务账号)
参考: https://kubernetes.io/zh/docs/reference/access-authn-authz/authentication/#service-account-tokens
|--- Role --- RoleBinding #只在指定namespace中生效
ServiceAccount ---|
|--- ClusterRole --- ClusterRoleBinding #不受namespace限制,在整个K8s集群中生效
创建ServiceAccount(账号服务)
参考: https://kubernetes.io/zh/docs/reference/access-authn-authz/rbac/#一些命令行工具
https://blog.csdn.net/wangmiaoyan/article/details/102551390
https://www.cnblogs.com/zhaobowen/p/13562487.html#一生成账号
# 在命名空间app-team1中创建账号cicd-token
kubectl create sa cicd-token -n app-team1
# 查看账号是否创建
kubectl get sa cicd-token -n app-team1
# 查看服务账户详情
kubectl describe sa cicd-token -n app-team1
删除ServiceAccount(账号服务)
# 查看命名空间app-team1下的所有用户
kubectl get sa -n app-team1
# 命名空间app-team1下的cicd-token用户
kubectl delete sa cicd-token -n app-team1
role(角色–管理指定资源的用户)
创建role作用域只限于这个指定的资源对象.
例如:
- 创建的账号只能操作指定的namespace
- 创建的账号只能操作指定的pod
- 创建的账号只能操作指定的deployment
- 等等----可以精准的授权
创建role(角色)
参考: https://kubernetes.io/zh/docs/reference/access-authn-authz/rbac/#kubectl-create-role
# 创建名称为 "pod-reader" 的 Role 对象,允许用户对 Pods 执行 get、watch 和 list 操作
kubectl create role pod-reader --verb=get --verb=list --verb=watch --resource=pods
创建RoleBinding(绑定角色)
https://kubernetes.io/zh/docs/reference/access-authn-authz/rbac/#rolebinding-and-clusterrolebinding
角色绑定(Role Binding)是将角色中定义的权限赋予一个或者一组用户。一个 RoleBinding 可以引用同一的名字空间中的任何 Role。
# 将集群角色绑定到账号
## {binding_NAME}=用户名-集群角色名-binding
kubectl create rolebinding {binding_NAME} -- clusterrole={集群角色名} --serviceaccount={命名空间名}:{用户名} -n {命名空间名}
# 在命名空间app-team1中,将ClusterRole(集群角色)deployment-clusterrole绑定到账号cicd-token
kubectl create rolebinding cicd-token-deployment-clusterrole-binding -- clusterrole=deployment-clusterrole --serviceaccount=app-team1:cicd-token -n app-team1
删除RoleBinding
# 查看命名空间app-team1下有哪些rolebinding
kubectl get rolebinding -n app-team1
# 删除命名空间app-team1下名为cicd-token-deployment-clusterrole-binding的rolebinding
kubectl delete rolebinding cicd-token-deployment-clusterrole-binding -n app-team1
ClusterRole(集群角色)
ClusterRole的作用域是个整个集群下.
例如:
- 创建的账号只能查看该集群的信息
- 创建的账号可以修改该集群的信息
- 等等----可以非常精准的授权
创建ClusterRole(集群角色)
ClusterRole 有若干用法。你可以用它来:
- 定义对某命名空间域对象的访问权限,并将在各个命名空间内完成授权;
- 为命名空间作用域的对象设置访问权限,并跨所有命名空间执行授权;
- 为集群作用域的资源定义访问权限。
# 创建ClusterRole(集群角色)deployment-clusterrole,权限限定为:只允许创建deployments,daemonsets,statefulsets
kubectl create clusterrole deployment-clusterrole --verb=create --
resource=deployments,daemonsets,statefulsets
创建clusterrolebinding(绑定集群角色)
# 将账号绑定到集群角色
### {clusterrolebinding_NAME}=用户名-集群角色名-binding
kubectl create clusterrolebinding {binding_NAME} --clusterrole=集群角色名--serviceaccount=kube-system:用户名
# 将账号tiller绑定到集群管理员cluster-admin角色
kubectl create clusterrolebinding tiller-cluster-rule --clusterrole=cluster-admin --serviceaccount=kube-system:tiller
删除clusterrolebinding
# 查看集群中有哪些clusterrolebinding
kubectl get clusterrolebinding |grep {clusterrolebinding_NAME}
# 删除指定clusterrolebinding
kubectl delete clusterrolebinding {clusterrolebinding_NAME}
查看RBAC权限常用命令
参考: https://kubernetes.io/zh/docs/reference/kubectl/overview/#%E8%B5%84%E6%BA%90%E7%B1%BB%E5%9E%8B
# 查看服务账户
kubectl get sa 用户名
# 查看服务账户详情
kubectl describe sa 用户名
# 查看集群角色
kubectl get ClusterRole 集群角色名
# 查看集群角色详情
kubectl describe ClusterRole 集群角色名
# 查看role
kubectl get role 角色名
# 查看role详情
kubectl describe role 角色名
# 查看rolebindings
kubectl get rolebinding 绑定名
# 查看rolebindings详情
kubectl describe rolebinding 绑定名
# 删除rolebindings
kubectl delete rolebinding 绑定名
CKA考试RBAC授权题
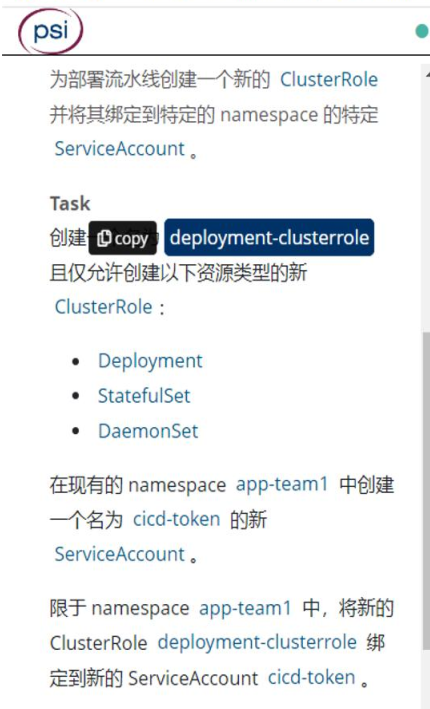
# 在命名空间app-team1中创建账号cicd-token
kubectl create sa cicd-token -n app-team1
# 查看账号是否创建
kubectl get sa cicd-token -n app-team1
# 查看服务账户详情
kubectl describe sa cicd-token -n app-team1
# 创建ClusterRole(集群角色)deployment-clusterrole,权限限定为:只允许创建deployments,daemonsets,statefulsets
kubectl create clusterrole deployment-clusterrole --verb=create -- resource=deployments,daemonsets,statefulsets
# 查看集群角色是否创建成功
kubectl get clusterrole |grep deployment-clusterrole
# 查看集群角色详情
kubectl describe clusterrole deployment-clusterrole
## 将集群角色绑定到账号
## {binding_NAME}=用户名-集群角色名-binding
kubectl create rolebinding {binding_NAME} -- clusterrole={集群角色名} --serviceaccount={命名空间名}:{用户名} -n {命名空间名}
# 在命名空间app-team1中,将ClusterRole(集群角色)deployment-clusterrole绑定到账号cicd-token
kubectl create rolebinding cicd-token-deployment-clusterrole-binding -- clusterrole=deployment-clusterrole --serviceaccount=app-team1:cicd-token -n app-team1
# 查看账号是否绑定成功
kubectl describe rolebinding cicd-token-deployment-clusterrole-binding -n app-team1