发现主机就是指探测网络中活动的主机。发现主机是实施渗透测试的第一步,也是最重要的一步。只有先确定目标主机是活动的,才能进一步实施渗透测试。在Nmap中,可以通过不同的方法来发现主机,如 IP发现、ICMP发现、TCP发现和UDP发现等。
一、IP发现
网际协议(Internet Protocol)是tcp/ip体系中的网络层协议。对上可载送传输层的各种协议信息,如TCP/UDP等;对下可将IP数据包放到链路层,通过以太网和令牌网络等各种技术来传送。
为了标识传输层协议类型,IP报文包含一个字段Protocol,用于保存传输层协议编号。
Nmap允许用户基于IP构建探测数据报,用于构建不同类型的传输层数据包。通过字段Protocol,用户可以设置当前包采用哪种传输层协议。一旦目标响应这类数据包,就证明主机存在。
语法:
-PO <protocol list>:使用IP数据包探测目标主机是否开启。
其中protocol list是协议编号列表。
用户可以指定多个IP编号,如:
6-tcp,17-udp,1-ICMP,2-IGMP
多个编号之间使用逗号分隔。
如果没有指定协议,默认协议为1(ICMP)2(IGMP)和4(IP),等同于
-PO 1,2,4
注意:在选项-PO中,O是大写字母O,不是数字0。另外,选项和协议编号之间没有空格。如果指定的协议为ICMP、IGMP、TCP、UDP,则默认添加对应的协议报头作为IP层的数据载荷。如果是其他协议,默认不添加任何数据载荷,除非使用–data、–data-string或者–data-length来指定。
使用默认的IP探测一个不在线的主机,以分析其发送和接收的数据包。
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PO 10.10.1.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 23:35 CST
# 发送了ICMP报文
SENT (0.0738s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=33 seq=0] IP [ttl=45 id=64436 iplen=28 ]
# 发送了IGMP报文
SENT (0.0741s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=37 id=30379 iplen=28
# 发送了IPV4报文
SENT (0.0742s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=40 id=51474 iplen=20
# 接收的ICMP报文
RCVD (0.0743s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26347 iplen=56 ]
# 接收的ICMP报文
RCVD (0.0744s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26348 iplen=48 ]
SENT (2.0790s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=57 id=18487 iplen=20
SENT (2.0792s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=57 id=31605 iplen=28
SENT (2.0794s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=20005 seq=0] IP [ttl=47 id=12773 iplen=28 ]
RCVD (2.0792s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26349 iplen=48 ]
RCVD (2.0792s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26350 iplen=56 ]
# 主机不在线
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.09 seconds
从输出信息中可以看到探测结果
-
Nmap首先依次向目标主机发送了默认的三个IP探测报文,分别是ICMP/IGMP/IPV4
# 发送了ICMP报文 SENT (0.0738s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=33 seq=0] IP [ttl=45 id=64436 iplen=28 ] # 发送了IGMP报文 SENT (0.0741s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=37 id=30379 iplen=28 # 发送了IPV4报文 SENT (0.0742s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=40 id=51474 iplen=20 -
收到两个ICMP不可达的错误数据包
# 接收的ICMP报文 RCVD (0.0743s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26347 iplen=56 ] # 接收的ICMP报文 RCVD (0.0744s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26348 iplen=48 ]其中
Protocol 2和Protocol 4分别对应传输层协议字段值2和4,即对应IGMP和IP,这两个协议类型为3,消息代码为2,表示协议不可达,即没有成功到达目标主机 -
由于第一个ICMP包没有响应,因此Nmap重新发送一遍:
SENT (2.0794s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=20005 seq=0] IP [ttl=47 id=12773 iplen=28 ] -
由于仍然没有收到响应,由此判断目标主机不在线并输出以下信息:
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
使用默认IP探测一个活动主机,以查看发送和接收的数据包
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PO -sn --disable-arp-ping 192.168.137.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 00:01 CST
# 发送ICMP报文
SENT (0.0386s) ICMP [192.168.220.138 > 192.168.137.1 Echo request (type=8/code=0) id=12203 seq=0] IP [ttl=56 id=38437 iplen=28 ]
# 发送IGMP报文
SENT (0.0388s) igmp (2) 192.168.220.138 > 192.168.137.1: ttl=46 id=48232 iplen=28
# 发送IPV4报文
SENT (0.0390s) ipv4 (4) 192.168.220.138 > 192.168.137.1: ttl=48 id=39415 iplen=20
# 接收ICMP响应报文
RCVD (0.0392s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26356 iplen=56 ]
RCVD (0.0393s) ICMP [192.168.137.1 > 192.168.220.138 Echo reply (type=0/code=0) id=12203 seq=0] IP [ttl=128 id=26357 iplen=28 ]
NSOCK INFO [0.0390s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.0390s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.0400s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.0400s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.0400s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.0400s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.0470s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): Q............1.137.168.192.in-addr.arpa.....
NSOCK INFO [0.0470s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.0470s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.0470s] nevent_delete(): nevent_delete on event #34 (type READ)
Nmap scan report for 192.168.137.1
# 主机是活动的
Host is up (0.00075s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
从输出信息中可以看到,Nmap依次向目标主机发送了ICMP、IGMP和IPv4探测报文,并且成功收到一个ICMP响应报文(Echo reply)。其中,该报文是ICMP正确的Ping应答报文,类型和消息代码都为0。由此可以说明目标主机是活动的。
设置使用TCP实施IP发现来探测目标主机的状态
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PO6 -sn --disable-arp-ping 192.168.137.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 00:19 CST
# 发送tcp ack报文
SENT (0.0348s) TCP 192.168.220.138:58382 > 192.168.137.1:80 A ttl=55 id=33234 iplen=40 seq=3525990618 win=1024
# 接收的TCP RST报文
RCVD (0.0351s) TCP 192.168.137.1:80 > 192.168.220.138:58382 R ttl=128 id=26360 iplen=40 seq=1636168757 win=32767
NSOCK INFO [0.0350s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.0350s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.0350s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.0350s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.0350s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.0350s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.0420s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): b............1.137.168.192.in-addr.arpa.....
NSOCK INFO [0.0420s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.0420s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.0420s] nevent_delete(): nevent_delete on event #34 (type READ)
Nmap scan report for 192.168.137.1
# 主机是活动的
Host is up (0.00041s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
在执行的命令中,TCP的协议编号为6。从输出信息中可以看到,Nmap仅向目标主机的80端口发送了一个TCP ACK探测报文来判断目标主机的状态。从显示的结果中可以看到,目标主机的80端口正确响应了一个TCP RST报文。由此可以说明目标主机是活动的。
二、ICMP发现
1. ICMP的工作原理
-
工作原理
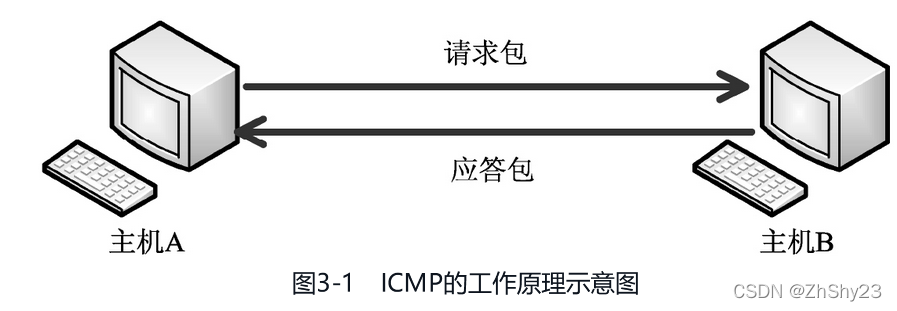
ICMP工作流程:- 当主机A通过ping命令测试是否可以正常通信时,会向主机B发送一个请求包。
- 主机B收到该请求后,将检查它的目的地址,并和本机的ip地址对比。如果符合则接收,否则丢弃。在接收后,将响应一个应答包给主机A,说明主机可达,即目标主机是活动的。
-
报文类型
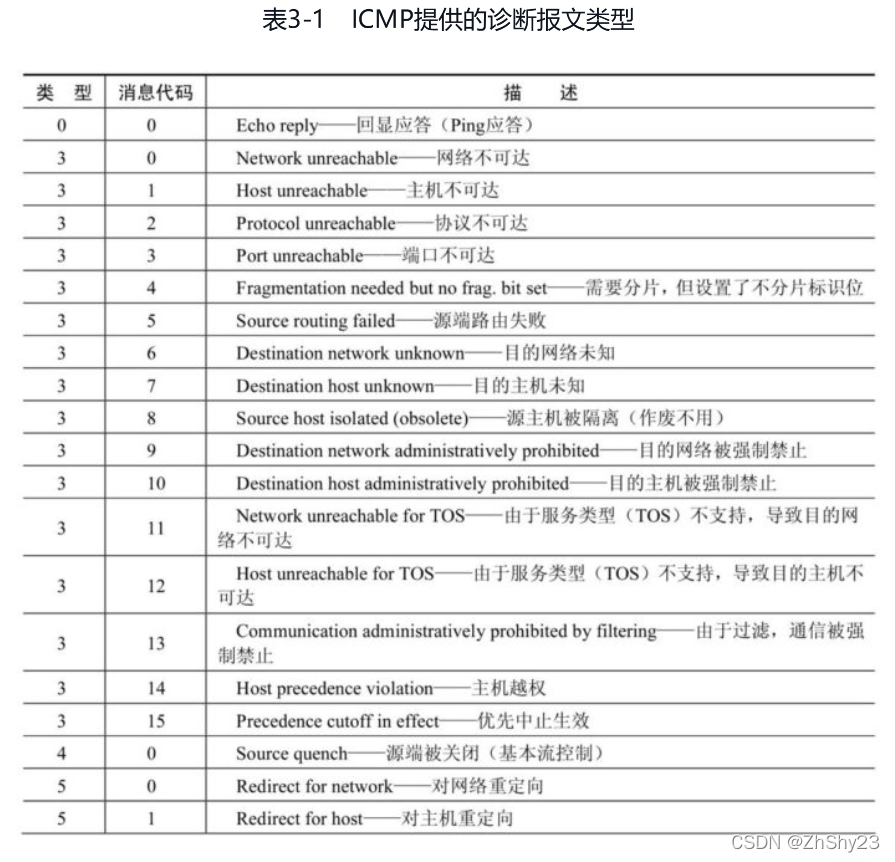
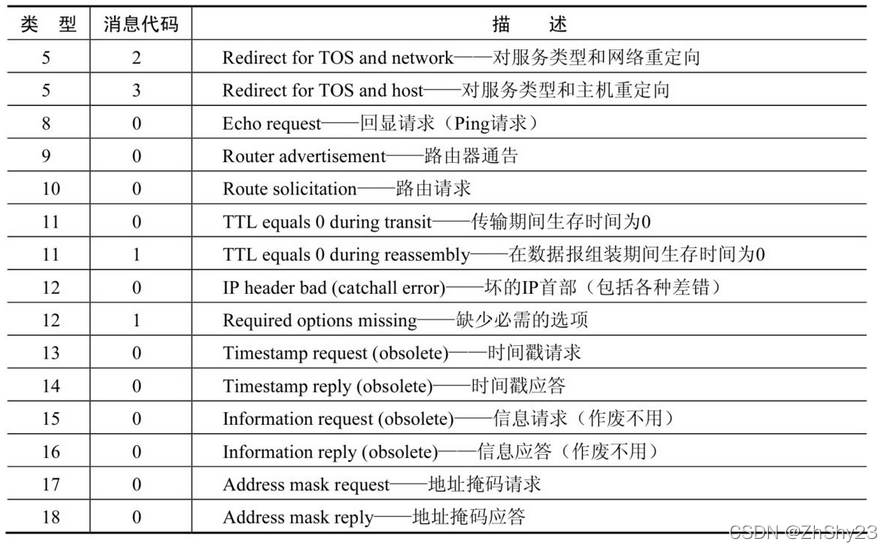
2. ICMP请求
ICMP请求:向目标主机发送一个ping请求,等待目标主机的响应。如果目标主机给予了响应,说明目标主机在线,否则说明不在线。
nmap提供了两个选项实施ICMP请求,以探测目标主机是否活动:
-sn:[实施Ping扫描,禁止端口扫描]
使用该选项时,nmap默认发送4个请求,分别是:ICMP ECHO请求,TCP SYN请求,TCP ACK请求,ICMP时间戳请求。如果不希望使用ARP请求,可以使用--send-ip选项指定发送ip包。-sn选项可以和任何发型探测类型-P*选项结合使用,以达到更高的灵活性。
-PE:[实施ICMP Echo探测请求发现]
如果目标主机响应ICMP Reply报文,则说明目标主机在线,否则不在线。
通过实施Ping扫描,探测目标主机是否在线
┌──(root💀kali)-[~]
└─# nmap --packet-trace -sn www.baidu.com
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:06 CST
# 发送ICMP响应请求
SENT (0.0442s) ICMP [192.168.220.138 > 180.101.49.11 Echo request (type=8/code=0) id=22759 seq=0] IP [ttl=52 id=28777 iplen=28 ]
# 发送 TCP SYN到443
SENT (0.0444s) TCP 192.168.220.138:34194 > 180.101.49.11:443 S ttl=57 id=41984 iplen=44 seq=274922632 win=1024 <mss 1460>
# 发送TCP ack到80
SENT (0.0445s) TCP 192.168.220.138:34194 > 180.101.49.11:80 A ttl=53 id=35602 iplen=40 seq=0 win=1024
# 发送ICMP时间戳请求
SENT (0.0446s) ICMP [192.168.220.138 > 180.101.49.11 Timestamp request (type=13/code=0) id=32360 seq=0 orig=0 recv=0 trans=0] IP [ttl=58 id=18221 iplen=40 ]
# 接收ICMP应答
RCVD (0.0450s) TCP 180.101.49.11:80 > 192.168.220.138:34194 R ttl=128 id=26366 iplen=40 seq=274922632 win=32767
NSOCK INFO [0.0450s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.0450s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.0450s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.0450s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.0450s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.0450s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.0800s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa.....
NSOCK INFO [0.0810s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.0810s] nsock_write(): Write request for 44 bytes to IOD #1 EID 43 [192.168.220.2:53]
NSOCK INFO [0.0810s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 43 [192.168.220.2:53]
NSOCK INFO [0.1140s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 34 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa.....
NSOCK INFO [0.1140s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 50
NSOCK INFO [0.1140s] nsock_write(): Write request for 44 bytes to IOD #1 EID 59 [192.168.220.2:53]
NSOCK INFO [0.1140s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 59 [192.168.220.2:53]
NSOCK INFO [0.1450s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 50 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa.....
NSOCK INFO [0.1450s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 66
NSOCK INFO [0.1450s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.1450s] nevent_delete(): nevent_delete on event #66 (type READ)
Nmap scan report for www.baidu.com (180.101.49.11)
# 主机是活动的
Host is up (0.00054s latency).
Other addresses for www.baidu.com (not scanned): 180.101.49.12
Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
- Nmap首先向目标主机发送了4个探测报文,分别是ICMP、TCP SYN、TCP ACK和ICMP Timestamp request,具体如下:
# 发送ICMP响应请求 SENT (0.0442s) ICMP [192.168.220.138 > 180.101.49.11 Echo request (type=8/code=0) id=22759 seq=0] IP [ttl=52 id=28777 iplen=28 ] # 发送 TCP SYN到443 SENT (0.0444s) TCP 192.168.220.138:34194 > 180.101.49.11:443 S ttl=57 id=41984 iplen=44 seq=274922632 win=1024 <mss 1460> # 发送TCP ack到80 SENT (0.0445s) TCP 192.168.220.138:34194 > 180.101.49.11:80 A ttl=53 id=35602 iplen=40 seq=0 win=1024 # 发送ICMP时间戳请求 SENT (0.0446s) ICMP [192.168.220.138 > 180.101.49.11 Timestamp request (type=13/code=0) id=32360 seq=0 orig=0 recv=0 trans=0] IP [ttl=58 id=18221 iplen=40 ] - 目标主机响应了一个TCP RST报文:
从该报文的地址和端口可以看到,是响应TCP ACK报文的。由于TCP ACK是一个确认报文,没有建立连接,所以目标响应了一个TCP RST报文,证明目标主机在线.# 接收ICMP应答 RCVD (0.0450s) TCP 180.101.49.11:80 > 192.168.220.138:34194 R ttl=128 id=26366 iplen=40 seq=274922632 win=32767
使用ICMP Echo探测请求发现主机
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PE www.baidu.com 3 ?
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:12 CST
SENT (0.1805s) ICMP [192.168.220.138 > 180.101.49.12 Echo request (type=8/code=0) id=37100 seq=0] IP [ttl=37 id=62664 iplen=28 ]
RCVD (0.1976s) ICMP [180.101.49.12 > 192.168.220.138 Echo reply (type=0/code=0) id=37100 seq=0] IP [ttl=128 id=26374 iplen=28 ]
NSOCK INFO [0.1980s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.1980s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.1980s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.1980s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.1990s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.1990s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.2330s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): .X...........12.49.101.180.in-addr.arpa.....
NSOCK INFO [0.2330s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.2330s] nsock_write(): Write request for 44 bytes to IOD #1 EID 43 [192.168.220.2:53]
NSOCK INFO [0.2330s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 43 [192.168.220.2:53]
NSOCK INFO [0.2680s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 34 [192.168.220.2:53] (44 bytes): .Y...........12.49.101.180.in-addr.arpa.....
NSOCK INFO [0.2680s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 50
NSOCK INFO [0.2690s] nsock_write(): Write request for 44 bytes to IOD #1 EID 59 [192.168.220.2:53]
NSOCK INFO [0.2690s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 59 [192.168.220.2:53]
NSOCK INFO [0.3030s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 50 [192.168.220.2:53] (44 bytes): .Z...........12.49.101.180.in-addr.arpa.....
NSOCK INFO [0.3030s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 66
NSOCK INFO [0.3030s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.3030s] nevent_delete(): nevent_delete on event #66 (type READ)
SENT (0.3044s) TCP 192.168.220.138:49172 > 180.101.49.12:80 S ttl=40 id=47411 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3045s) TCP 192.168.220.138:49172 > 180.101.49.12:8080 S ttl=56 id=33278 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3045s) TCP 192.168.220.138:49172 > 180.101.49.12:5900 S ttl=55 id=8525 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3046s) TCP 192.168.220.138:49172 > 180.101.49.12:139 S ttl=47 id=56043 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3055s) TCP 192.168.220.138:49172 > 180.101.49.12:993 S ttl=40 id=23236 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3056s) TCP 192.168.220.138:49172 > 180.101.49.12:8888 S ttl=59 id=11898 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3056s) TCP 192.168.220.138:49172 > 180.101.49.12:1720 S ttl=51 id=16621 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3057s) TCP 192.168.220.138:49172 > 180.101.49.12:113 S ttl=51 id=42562 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (0.3057s) TCP 192.168.220.138:49172 > 180.101.49.12:995 S ttl=50 id=1002 iplen=44 seq=678127315 win=1024 <mss 1460>
.......
SENT (108.7931s) TCP 192.168.220.138:49333 > 180.101.49.12:80 S ttl=42 id=4968 iplen=44 seq=684353138 win=1024 <mss 1460>
SENT (108.9542s) TCP 192.168.220.138:49172 > 180.101.49.12:880 S ttl=50 id=64004 iplen=44 seq=678127315 win=1024 <mss 1460>
SENT (109.1160s) TCP 192.168.220.138:49174 > 180.101.49.12:880 S ttl=52 id=10999 iplen=44 seq=677996241 win=1024 <mss 1460>
Nmap scan report for www.baidu.com (180.101.49.12)
Host is up (0.017s latency).
Other addresses for www.baidu.com (not scanned): 180.101.49.11
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 109.31 seconds
以上输出信息显示了整个扫描过程。在这个过程中,Nmap不仅实施了主机发现,而且还进行了端口扫描。
-
Nmap向目标主机发送了一个ICMP Echo request探测报文:
SENT (0.1805s) ICMP [192.168.220.138 > 180.101.49.12 Echo request (type=8/code=0) id=37100 seq=0] IP [ttl=37 id=62664 iplen=28 ]在该报文中,ICMP请求类型type为8,代码code为0,即一个正常的Ping请求。
-
目标主机响应了一个正常的应答报文ICMP Echo reply:
RCVD (0.1976s) ICMP [180.101.49.12 > 192.168.220.138 Echo reply (type=0/code=0) id=37100 seq=0] IP [ttl=128 id=26374 iplen=28 ]响应类型type为0,代码code为0,即一个正常的Ping应答,由此可以说明目标主机是活动的。
使用Nmap实施主机发现时,默认将进行端口扫描。当扫描大型网络范围内的主机时,如果只希望探测主机的状态,则可以使用-sn选项禁止端口扫描,以节约大量的时间。
3.ICMP时间戳
ICMP时间戳请求允许一个系统向另一个系统查询当前的时间。如果目标主机返回了时间,则说明目标主机是活动的。为了安全起见,在实际应用中,一些主机和防火墙通常都会封锁ICMP响应请求报文,这样用户就无法使用ICMP响应来发现主机了。如果由于管理员失误仅封锁了ICMP响应请求报文,而忘记封锁其他ICMP查询报文,如ICMP时间戳请求,此时就可以通过ICMP时间戳请求来探测主机。Nmap中提供了一个-PP选项,可以用来实施ICMP时间戳Ping扫描。
使用ICMP时间戳探测一个不在线的主机
┌──(root💀kali)-[~]
└─# nmap --packet-trace -sn -PP --send-ip 220.181.38.251 4 ?
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:38 CST
SENT (0.0343s) ICMP [192.168.220.138 > 220.181.38.251 Timestamp request (type=13/code=0) id=45667 seq=0 orig=0 recv=0 trans=0] IP [ttl=42 id=9557 iplen=40 ]
SENT (1.0357s) ICMP [192.168.220.138 > 220.181.38.251 Timestamp request (type=13/code=0) id=16815 seq=0 orig=0 recv=0 trans=0] IP [ttl=47 id=38630 iplen=40 ]
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.04 seconds
4. ICMP地址掩码请求
ICMP地址掩码请求用于无盘系统在引导过程中获取自己的子网掩码。如果收到目标主机的响应,则说明目标主机是活动的。当用户使用ICMP时间戳方式无法探测出目标主机的状态时,则可以尝试使用ICMP地址掩码请求方式。用于实施ICMP地址掩码请求的选项及其含义如下:
-PM:进行ICMP地址掩码Ping扫描。
使用ICMP地址掩码请求进行主机发现
┌──(root💀kali)-[~]
└─# nmap --packet-trace -sn -PM 220.181.38.251 4 ?
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:41 CST
SENT (0.0345s) ICMP [192.168.220.138 > 220.181.38.251 Address mask request (type=17/code=0) id=31595 seq=0 mask=0.0.0.0] IP [ttl=55 id=8706 iplen=32 ]
SENT (1.0404s) ICMP [192.168.220.138 > 220.181.38.251 Address mask request (type=17/code=0) id=3363 seq=0 mask=0.0.0.0] IP [ttl=52 id=4988 iplen=32 ]
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.04 seconds
在以上报文中,ICMP地址掩码请求类型type为17,代码code为0。这里之所以有两个探测报文,是因为Nmap发送第一个报文后没有收到目标主机的响应,所以再次发送了一个报文进行探测,结果仍然没有收到响应。由此可以判断,目标主机不在线。
三、TCP发现
1. TCP工作原理
-
工作原理
 TCP工作流程
TCP工作流程- 客户端发送
SYN(SEQ=x)报文给服务器端,进入SYN_SEND状态。 - 服务器端收到
SYN报文后,将回应一个SYN(SEQ=y)ACK(ACK=x+1)报文,进入SYN_RECV状态。 - 客户端收到服务器端的
SYN报文后,将回应一个ACK(ACK=y+1)报文,进入Established状态。
至此,TCP的三次握手就完成了,TCP客户端和服务器端成功建立了连接。接下来就可以开始传输数据了。
- 客户端发送
-
TCP标识位
- SYN(同步标志):同步序号,用来建立连接。SYN标志位和ACK标志位搭配使用。当发送连接请求的时候,SYN=1,ACK=0;连接被响应的时候,SYN=1,ACK=1。
- FIN(结束标志):双方的数据传送完成,没有数据可以传送了。此时,发送一个带FIN标志位的TCP数据包,连接将被断开。
- ACK(确认标志):应答域有效。
- PUSH(推标志):Push操作。简单地说就是在数据包到达接收端以后,立即传送给应用程序而不是在缓冲区确认。
- RST(复位标志):连接复位请求。该标志位可以用来复位那些发生错误的连接,也被用来拒绝错误和非法的数据包。
- URG(紧急标志):TCP数据包的紧急指针域有效,用来保证TCP连接不被中断,并且督促中间层设备要尽快处理这些数据。
2. TCP SYN发现
TCP SYN发现通过发送一个带TCP SYN标志位的空TCP报文到目标,如果目标主机是活动的,将会收到一个TCP SYN+ACK报文或者RST报文。Nmap提供了一个选项可以用来实施TCP SYN发现,该选项及其含义如下:
-PS <portlist>:实施TCP SYN Ping扫描。
其中,该选项将发送TCP SYN报文到目标的80端口。用户也可以手动指定为其他端口列表,格式为-PS21,22,23。这样每个端口会被并发地扫描。注意,-PS选项和端口之间没有空格。