Ipsec手动模式
ipsec一共有两种模式:IKE协商模式和手动模式
手动模式需要自己配置SA的全部参数,加密方式,密钥等,并且更新密钥,加密方式都需要用户手动更新,最重要的是,手工配置期限是永久的
所以,手动模式适用于组网较小的网络拓扑
 首先配置需要分为三个部分:
首先配置需要分为三个部分:
1. 配置acl感兴趣流
2. 配置ipsec proposal 提议
3. 配置ipsec policy
4. 应用在接口
首先是acl
acl需要精确匹配到需要走VPN的流量
acl 3000 rule 5 permit ip source 192.168.10.0 0.0.0.255 destination
192.168.20.0 0.0.0.255
配置ipsec提议
ipsec proposal shanghai
encapsulation-mode tunnel
transfrom esp esp
authentication-algorithm sha1
esp encryption-algorithm aes-192
这里用的是ipsec的隧道模式,隧道模式会给原来的包加一个新的ip头部,使包的安全性更高,因为这样露在外面的只有公网地址
而且,采用了ESP加密算法,ESP头部后面的数据都会被加密
配置ipsec policy
ipsec policy shanghai 1 manual
security acl 3000
proposal shanghai
tunnel local 12.0.0.1
tunnel remote 23.0.0.3
sa spi inbound esp 12345
sa string-key inbound esp cipher 123.com
sa spi outbound esp 54321 sa
string-key outbound esp cipher 123.com
在policy里需要调用acl和proposal
并且要指定隧道的地址以及sa的合约书
inbound的序列号和密码要和对端的保持一致
本端的入口,对于对端来说是出口
本端的出口,对于对端来说是入口
接口调用
ip address 12.0.0.1 255.255.255.0
ipsec policy shanghai
nat outbound 3001
注意:
根据匹配流程,router会先匹配NAT策略,但是在经过NAT之后,报文的源地址就被改成了公网地址,无法匹配到ipsec的acl,就无法和对端通信
 这里有两个解决方法:
这里有两个解决方法:
- 把ipsec匹配的acl的源地址改成公网地址
两端都要更改
acl 3000
rule 5 permit ip source 12.0.0.1 0 destination 192.168.20.0 0.0.0.255
- 把匹配NAT的acl进行拒绝
acl 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 10 permit ip
让私网与私网之间的ip协议报文都在NAT中拒绝,并且允许其他所有类型的报文通过,保证私网中其他的用户可以正常上网
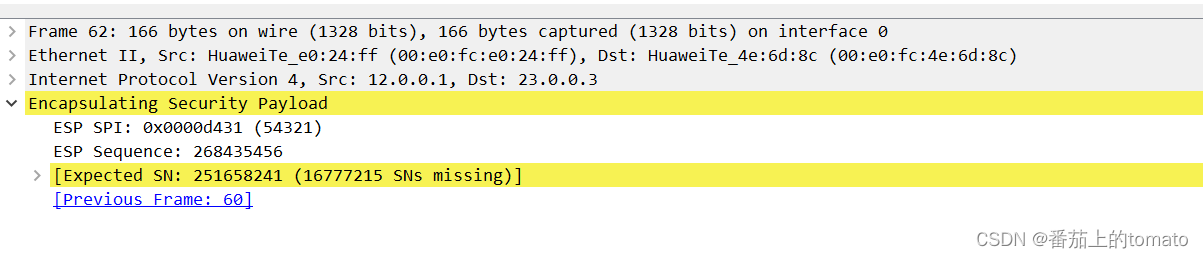
通过抓包可以看出,除了ESP的头部和new ip 头部以外,里面的原始数据都被加密
全部配置:
RT1
dhcp enable
interface GigabitEthernet0/0/0
ip address 192.168.10.254 255.255.255.0
dhcp select interface
interface GigabitEthernet0/0/1
ip address 12.0.0.1 255.255.255.0
ipsec policy shanghai
nat outbound 3001
ip route-static 0.0.0.0 0.0.0.0 12.0.0.2//到达公网的出口路由
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
acl number 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 10 permit ip
ipsec proposal shanghai
encapsulation-mode tunnel
transfrom esp
esp authentication-algorithm sha1
esp encryption-algorithm aes-192
ipsec policy shanghai 1 manual
security acl 3000
proposal shanghai
tunnel local 12.0.0.1
tunnel remote 23.0.0.3
sa spi inbound esp 12345
sa string-key inbound esp cipher 123.com
sa spi outbound esp 54321
sa string-key outbound esp cipher 123.com
RT3
dhcp enable
interface GigabitEthernet0/0/0
ip address 23.0.0.3 255.255.255.0
ipsec policy heifei
nat outbound 3001
interface GigabitEthernet0/0/1
ip address 192.168.20.254 255.255.255.0
dhcp select interface
ip route-static 0.0.0.0 0.0.0.0 23.0.0.2
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
acl number 3001
rule 5 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 10 permit ip
ipsec proposal hefei
esp authentication-algorithm sha1
esp encryption-algorithm aes-192
ipsec policy heifei 1 manual
security acl 3000
proposal hefei
tunnel local 23.0.0.3
tunnel remote 12.0.0.1
sa spi inbound esp 54321
sa string-key inbound esp cipher 123.com
sa spi outbound esp 12345
sa string-key outbound esp cipher 123.com
RT2(公网路由)
interface GigabitEthernet0/0/0
ip address 23.0.0.2 255.255.255.0
interface GigabitEthernet0/0/1
ip address 12.0.0.2 255.255.255.0
interface LoopBack1
ip address 2.2.2.2 255.255.255.255