@app.route('/getUrl', methods=['GET', 'POST'])
def getUrl():
url = request.args.get("url")
host = parse.urlparse(url).hostname #解析主机名
if host == 'suctf.cc':
return "我扌 your problem? 111"
parts = list(urlsplit(url))
host = parts[1] #拆分再解析主机名
if host == 'suctf.cc':
return "我扌 your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))#idna编码,再utf-8解码
parts[1] = '.'.join(newhost) #组合好解码后的主机名
#去掉 url 中的空格
finalUrl = urlunsplit(parts).split(' ')[0]
host = parse.urlparse(finalUrl).hostname #解析出主机名,要等于suctf.cc
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
else:
return "我扌 your problem? 333"
不让连suctf.cc
发现后面用idna了
idna编码
这就要找个能encode成c的特殊字符
看别的大佬都是跑代码试出来的
贴一个大佬的脚本
str: ? unicode: \u2102
str: ? unicode: \u212d
str: ? unicode: \u216d
str: ? unicode: \u217d
str: ? unicode: \u24b8
str: ? unicode: \u24d2
str: C unicode: \uff23
str: c unicode: \uff43
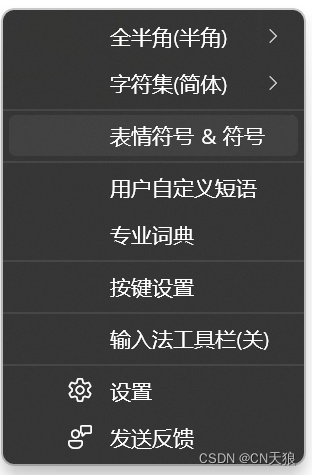
其实在字符表里找一个看着像c的就可以
微软输入法自带的字符表里就有好几个
这样就绕过host检查了
Nginx 重要文件目录
- 配置文件存放目录:/etc/nginx
- 主要配置文件:/etc/nginx/conf/nginx.conf
- 管理脚本:/usr/lib64/systemd/system/nginx.service
- 模块:/usr/lisb64/nginx/modules
- 应用程序:/usr/sbin/nginx
- 程序默认存放位置:/usr/share/nginx/html
- 日志默认存放位置:/var/log/nginx
- Nginx配置文件:/usr/local/nginx/conf/nginx.conf
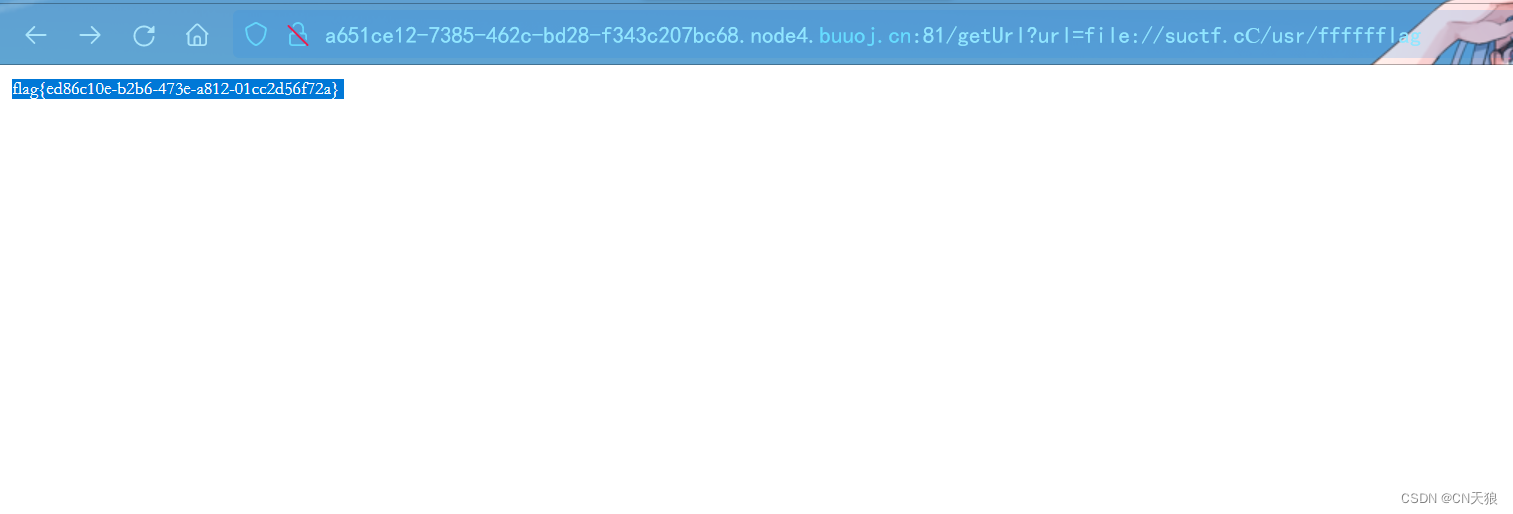
file协议看看主配置文件:
 发现flag目录
发现flag目录
继续file伪协议查看: