1、网络命名空间
1)网络命名空间的实现
网络命名空间是为了隔离网络设备和协议栈的
网络命名空间Net Namespace,简称netns

?私有命名空间只有回环设备,其他设备不存在,如果需要要自己创建。
所有网络设备都只能属于一个命名空间,物理设备只能属于root。虚拟网络设备则可以被关联到指定的命名空间中,而且可以在命名空间中移动。
网络命名空间设备是完全隔离的,没有办法互相通信,使用veth就解决了这个问题。
2)命名空间操作
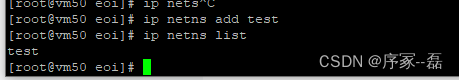
创建一个网络命名空间,新建的网络命名空间可以再/var/run/netns 里看到
ip nets add <name>
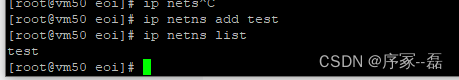
获取列表
ip netns list
在命名空间中运行命令
ip netns? exec <name> <command>
也可以通过bash 进入
ip nets exec <name> bash
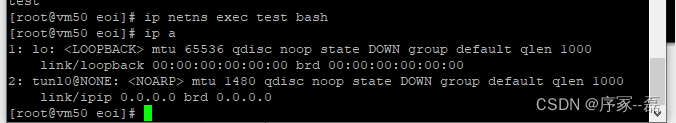
?
3)网络命名空间实战
查看设备列表
ip link
[root@vm50 eoi]# ip link
257: cali6aa84dc711d@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 10
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
258: caliea9d46af5d3@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 11
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEF AULT group default qlen 1000
link/ether 00:50:56:ac:93:32 brd ff:ff:ff:ff:ff:ff
259: calia0649ef1830@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 12
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOW N mode DEFAULT group default
link/ether 02:42:6b:94:d5:2f brd ff:ff:ff:ff:ff:ff
260: cali8bac6c0ff3f@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 13
261: cali1abad8afd57@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 14
262: cali11239f98883@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 15
263: cali4fb26ba7199@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 16
264: calicc16a6d001e@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 17
265: cali07356c57c26@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 5
10: tunl0@NONE: <NOARP,UP,LOWER_UP> mtu 1480 qdisc noqueue state UNKNOWN mode DE FAULT group default qlen 1000
link/ipip 0.0.0.0 brd 0.0.0.0
289: cali0432093e227@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 9
293: calibc6db57c46b@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 6
296: cali9b978cae3c5@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 18
247: calid75abf4f5e0@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 0
248: cali15c7619fccc@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 1
249: cali9d3da864524@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 2
250: cali84ef8fb5f7d@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 3
251: cali05fab0b794e@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 4
255: calib8f88917aee@if4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1480 qdisc noque ue state UP mode DEFAULT group default
link/ether ee:ee:ee:ee:ee:ee brd ff:ff:ff:ff:ff:ff link-netnsid 8
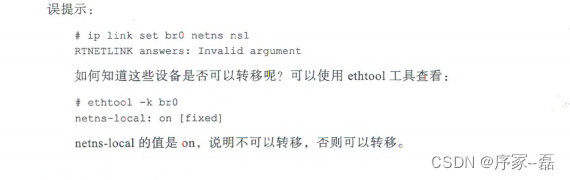
如何知道设备是否可以被转移?
?3.nsenter
我们看到docker也有网络命名空间
[root@vm50 eoi]# ls /var/run/docker/netns/
0b5ecfdaa492 18f1b8cfaa02 659c5c777674 804be5980579 98b3913faea3 9eb67f1bee55 ab10aeef7e19 d8d0b8570c0e e084762b59bf fa6a272e1131
0eef4c74de64 284813d91988 7c3cfb30e588 8970338954ff 9cf691f34593 a7756b687926 ce1774e8eb48 default f5c7b109cea2如果我们使用ip netns 进不去
ip netns exec /var/run/docker/netns/7c3cfb30e588 bash
Invalid netns name "/var/run/docker/netns/7c3cfb30e588"[root@vm50 eoi]# ip netns exec 7c3cfb30e588 bash
Cannot open network namespace "7c3cfb30e588": No such file or directory我们再看nsenter
对于很多场景我们使用exec登陆,有的时候 容器文件系统和操作系统隔离了,bash没有,我们可以用nsenter
我们用nginx 这个pod作为例子
[root@vm50 eoi]# kubectl get pod genlog-6cc499c785-5bch7 -oyaml|grep containerID
cni.projectcalico.org/containerID: ac7dd6b841ba8e6469731ef26081ad68811d736089f42c77856e32d1cfd49c3e
- containerID: docker://df4778b20642842957d4d06a92e09f381109d55ed8f7f126a031c41ce9c27679找出dockerId 对应的pid
[root@vm50 eoi]# docker inspect --format "{{.State.Pid}}" df4778b20642842957d4d06a92e09f381109d55ed8f7f126a031c41ce9c27679
40257nsenter进入
[root@vm50 eoi]# nsenter -u -p -n -t 40257
[root@genlog-6cc499c785-5bch7 eoi]# 登出
[root@vm50 eoi]# nsenter -u -p -n -t 40257
nsenter介绍:
nsenter [options] [program [arguments]]
options:
-t, --target pid:指定被进入命名空间的目标进程的pid
-m, --mount[=file]:进入mount命令空间。如果指定了file,则进入file的命令空间
-u, --uts[=file]:进入uts命令空间。如果指定了file,则进入file的命令空间
-i, --ipc[=file]:进入ipc命令空间。如果指定了file,则进入file的命令空间
-n, --net[=file]:进入net命令空间。如果指定了file,则进入file的命令空间
-p, --pid[=file]:进入pid命令空间。如果指定了file,则进入file的命令空间
-U, --user[=file]:进入user命令空间。如果指定了file,则进入file的命令空间
-G, --setgid gid:设置运行程序的gid
-S, --setuid uid:设置运行程序的uid
-r, --root[=directory]:设置根目录
-w, --wd[=directory]:设置工作目录
总结
网络命名空间可以很好的隔离网络,另外一个利器就是nsenter,调试利器,作为一个unix-tool是在k8s场景上非常有用的调试工具,晚上会继续看linux的cgroup 和namespace