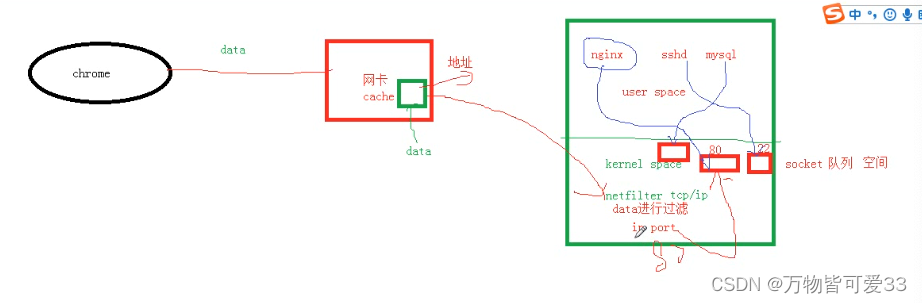
目录
一.网络流量相关的命令
1.dstat命令? ??
可以用来查看网络流量,还可以查看某块网卡的具体带宽
[root@xieshan lianxi]# yum provides dstat #查看dstat是通过哪个包安装过来的
[root@xieshan lianxi]# yum install dstat -y #安装dstat
[root@xieshan lianxi]# dstat
You did not select any stats, using -cdngy by default.
----total-cpu-usage---- -dsk/total- -net/total- ---paging-- ---system--
usr sys idl wai hiq siq| read writ| recv send| in out | int csw
5 0 94 0 0 0| 15k 1823B| 0 0 | 0 0 | 100 85
99 1 0 0 0 0| 0 0 | 186B 830B| 0 0 | 969 104
99 0 0 0 0 1| 0 0 | 186B 350B| 0 0 | 991 110
100 0 0 0 0 0| 0 0 | 366B 350B| 0 0 |1015 107
100 0 0 0 0 0| 0 0 | 246B 350B| 0 0 |1016 111
99 1 0 0 0 0| 0 20k| 403B 350B| 0 0 | 982 112
[root@xieshan lianxi]# dstat -am #加上查看内存的流量
----total-cpu-usage---- -dsk/total- -net/total- ---paging-- ---system-- ------memory-usage-----
usr sys idl wai hiq siq| read writ| recv send| in out | int csw | used buff cach free
6 0 94 0 0 0| 15k 1837B| 0 0 | 0 0 | 104 85 | 287M 2108k 376M 307M
99 1 0 0 0 0| 0 0 | 360B 1042B| 0 0 | 961 71 | 287M 2108k 376M 307M
100 0 0 0 0 0| 0 0 | 517B 426B| 0 0 | 956 74 | 287M 2108k 376M 307M
100 0 0 0 0 0| 0 0 | 180B 426B| 0 0 | 972 64 | 287M 2108k 376M 307M
99 1 0 0 0 0| 0 0 | 240B 426B| 0 0 | 999 70 | 287M 2108k 376M 307M
100 0 0 0 0 0| 0 0 | 120B 426B| 0 0 |1016 76 | 287M 2108k 376M 307M
[root@xieshan lianxi]# dstat -am -N ens33 #查看ens33网卡的流量
----total-cpu-usage---- -dsk/total- -net/ens33- ---paging-- ---system-- ------memory-usage-----
usr sys idl wai hiq siq| read writ| recv send| in out | int csw | used buff cach free
6 0 94 0 0 0| 15k 1834B| 0 0 | 0 0 | 106 85 | 287M 2108k 376M 307M
99 1 0 0 0 0| 0 0 | 300B 1042B| 0 0 | 979 85 | 287M 2108k 376M 307M
100 0 0 0 0 0| 0 0 | 180B 426B| 0 0 | 964 71 | 287M 2108k 376M 307M
100 0 0 0 0 0| 0 0 | 300B 426B| 0 0 | 972 72 | 287M 2108k 376M 307M
99 1 0 0 0 0| 0 0 | 120B 426B| 0 0 | 993 71 | 287M 2108k 376M 307M
[root@xieshan lianxi]#
[root@xieshan lianxi]# dstat --help #查看帮助手册
Usage: dstat [-afv] [options..] [delay [count]]
Versatile tool for generating system resource statistics
Dstat options:
-c, --cpu enable cpu stats
-C 0,3,total include cpu0, cpu3 and total
-d, --disk enable disk stats
-D total,hda include hda and total
-g, --page enable page stats
####ctrl+c退出2.iftop命令
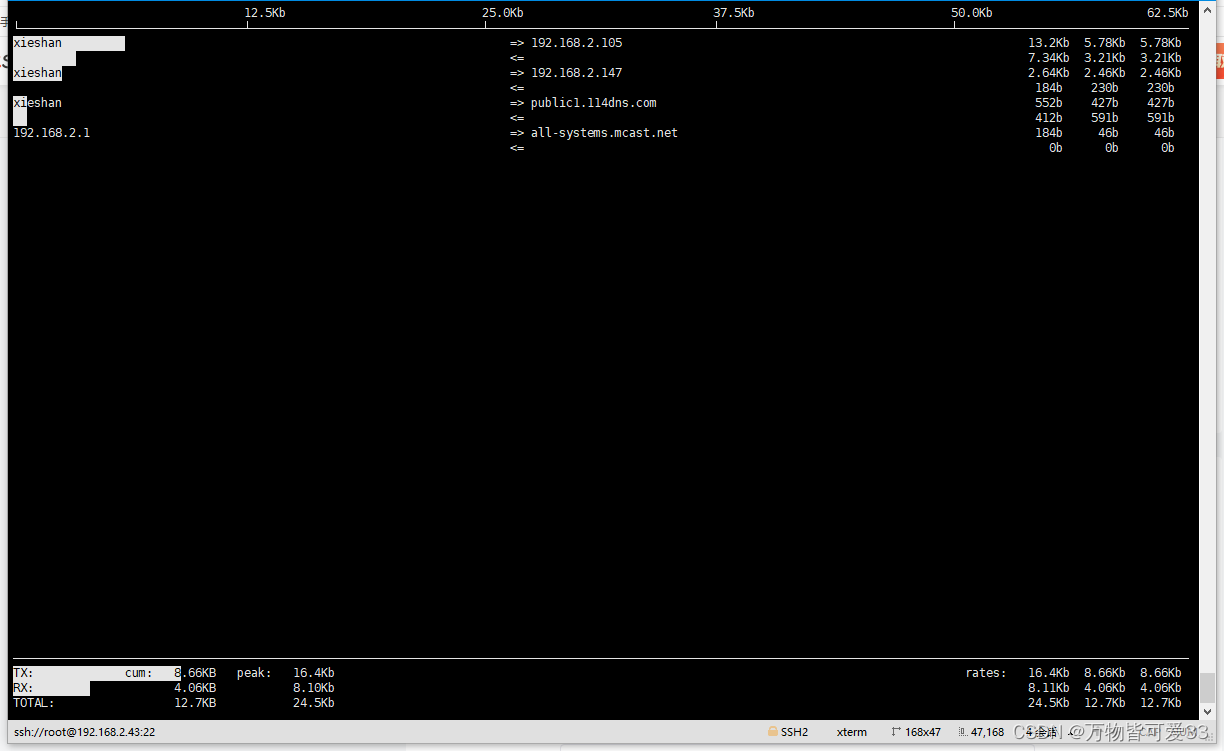
iftop命令可以用来监控网卡的实时流量(可以指定网段,指定网卡,反向解析IP、显示端口信息等)
详细解析:https://baijiahao.baidu.com/s?id=1713064539918696369&wfr=spider&for=pc
通过yum install iftop -y安装iftop命令,在命令行中输入iftop -i ens33命令后,会出现如下图所示的界面:
?3.nethogs命令
可以查看某个具体的进程消耗了多少流量,还能够知道哪些进程和外面进行了通信
[root@xieshan lianxi]# yum install epel-release -y #epel源,一个centos的第三方源,包含的东西非常多
[root@xieshan lianxi]# yum install nethogs -y
[root@xieshan lianxi]# nethogs
在命令行中输入nethogs后,会显示如下界面(按q退出)?

?二.网络监控的相关命令
所谓监控相关的命令,是指监控虚拟机开启了哪些端口,哪个端口被哪个进程占用了之类的
1.netstat命令
netstat可以查看本机开放了哪些端口,但是无法查看别人机器开启了哪些端口
[root@xieshan lianxi]# netstat -anplut
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:9001 0.0.0.0:* LISTEN 5154/nginx: master
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 4086/mysqld
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 3427/rpcbind
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 5154/nginx: master
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 3813/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 4132/master
tcp 0 36 192.168.2.43:22 192.168.2.147:61248 ESTABLISHED 5382/sshd: root@pts
tcp 0 0 192.168.2.43:22 192.168.2.105:53656 ESTABLISHED 6181/sshd: root@pts
tcp6 0 0 :::111 :::* LISTEN 3427/rpcbind
tcp6 0 0 :::22 :::* LISTEN 3813/sshd
tcp6 0 0 ::1:25 :::* LISTEN 4132/master
udp 0 0 0.0.0.0:68 0.0.0.0:* 3739/dhclient
udp 0 0 0.0.0.0:617 0.0.0.0:* 3427/rpcbind
udp 0 0 0.0.0.0:111 0.0.0.0:* 3427/rpcbind
udp 0 0 127.0.0.1:323 0.0.0.0:* 3392/chronyd
udp6 0 0 :::617 :::* 3427/rpcbind
udp6 0 0 :::111 :::* 3427/rpcbind
udp6 0 0 ::1:323 :::* 3392/chronyd
[root@xieshan lianxi]#-anplut参数解析:
????????-a all
????????-n number 以数字的形式显示,不加n就会到/etc/services文件中进行域名解析,会很慢
????????????????[root@slave-mysql ~]# vim /etc/services 记录哪些服务使用哪些端口 --》熟知的端口和登记的端口
????????-p program 程序的名字
????????-l [--listening|-l]正在监听的状态
????????-t [--tcp|-t]tcp协议的
????????-u [--udp|-u]udp协议
netstat输出每一列的含义:
- 第一列:采用的协议,TCP
- 第二列:Recv-Q
- Established: The count of bytes not copied by the user program connected to this socket.
内核空间里的socket队列里还有多少数据没有被用户空间里的进程复制(取)走
说明应用程序非常忙,处理不过来了
Listening: Since Kernel 2.6.18 this column contains the current syn backlog.
- 第三列:Send-Q
- Established: The count of bytes not acknowledged by the remote host.
还有多少字节的数据没有被远程主机确认--》发送出去的数据包还没有收到确认(数据从user space->kernel space->cache,跟上面反过来),可以理解为还有多少等待重传的数据
Listening: Since Kernel 2.6.18 this column contains the maximum size of the syn backlog.
- 第四列:Local Address 本地的IP地址和端口号
- 第五列:Foreign Address 外面访问过来的IP地址跟端口号
- 第六列:State 状态,是建立连接还是监听还是其他
- 第七列:PID/Program name 进程号和进程的名称?
2. lsof命令
lsof查看哪个端口被哪个进程占用了
[root@xieshan lianxi]# lsof -i:22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 3813 root 3u IPv4 27685 0t0 TCP *:ssh (LISTEN)
sshd 3813 root 4u IPv6 27687 0t0 TCP *:ssh (LISTEN)
sshd 5382 root 3u IPv4 56020 0t0 TCP xieshan:ssh->192.168.2.147:61248 (ESTABLISHED)
sshd 6181 root 3u IPv4 84463 0t0 TCP xieshan:ssh->192.168.2.105:53656 (ESTABLISHED)
[root@xieshan lianxi]# lsof -i:80
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
nginx 5154 root 13u IPv4 45505 0t0 TCP *:http (LISTEN)
nginx 5155 lilin 13u IPv4 45505 0t0 TCP *:http (LISTEN)
lsof查看某个进程打开了哪些文件,哪些库以及加载关系
[root@xieshan lianxi]# lsof -p 5154
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
nginx 5154 root cwd DIR 253,0 4096 33574977 /root
nginx 5154 root rtd DIR 253,0 4096 64 /
nginx 5154 root txt REG 253,0 7915608 51051390 /usr/local/sclilin99/sbin/nginx
nginx 5154 root mem REG 253,0 31344 947501 /usr/lib64/libnss_dns-2.17.so
nginx 5154 root mem REG 253,0 61560 251652 /usr/lib64/libnss_files-2.17.so
nginx 5154 root mem REG 253,0 155744 41604 /usr/lib64/libselinux.so.1
nginx 5154 root mem REG 253,0 109976 251955 /usr/lib64/libresolv-2.17.so
nginx 5154 root mem REG 253,0 15688 41684 /usr/lib64/libkeyutils.so.1.5
nginx 5154 root mem REG 253,0 67104 47704 /usr/lib64/libkrb5support.so.0.1
nginx 5154 root mem REG 253,0 210784 47694 /usr/lib64/libk5crypto.so.3.1
nginx 5154 root mem REG 253,0 15856 1463181 /usr/lib64/libcom_err.so.2.1
nginx 5154 root mem REG 253,0 967840 47701 /usr/lib64/libkrb5.so.3.3
nginx 5154 root mem REG 253,0 320720 1463187 /usr/lib64/libgssapi_krb5.so.2.2
nginx 5154 root mem REG 253,0 11392 33506 /usr/lib64/libfreebl3.so
nginx 5154 root mem REG 253,0 2156592 877364 /usr/lib64/libc-2.17.so
nginx 5154 root mem REG 253,0 197088 1506331 /usr/lib64/libGeoIP.so.1.5.0
nginx 5154 root mem REG 253,0 90160 1736050 /usr/lib64/libz.so.1.2.7
nginx 5154 root mem REG 253,0 2520920 227676 /usr/lib64/libcrypto.so.1.0.2k
nginx 5154 root mem REG 253,0 470328 227687 /usr/lib64/libssl.so.1.0.2k
nginx 5154 root mem REG 253,0 402384 41637 /usr/lib64/libpcre.so.1.2.0
nginx 5154 root mem REG 253,0 40600 251642 /usr/lib64/libcrypt-2.17.so
nginx 5154 root mem REG 253,0 142144 251951 /usr/lib64/libpthread-2.17.so
nginx 5154 root mem REG 253,0 19248 251644 /usr/lib64/libdl-2.17.so
nginx 5154 root mem REG 253,0 163312 877356 /usr/lib64/ld-2.17.so
nginx 5154 root DEL REG 0,4 45507 /dev/zero
nginx 5154 root 0u CHR 1,3 0t0 6477 /dev/null
nginx 5154 root 1u CHR 1,3 0t0 6477 /dev/null
nginx 5154 root 2w REG 253,0 23021 16779566 /usr/local/sclilin99/logs/error.log
nginx 5154 root 3u unix 0xffff881379570000 0t0 45508 socket
nginx 5154 root 4w REG 253,0 6571 17384630 /usr/local/sclilin99/logs/access.log
nginx 5154 root 5w REG 253,0 29017 17358693 /usr/local/sclilin99/logs/sc.access.log
nginx 5154 root 6w REG 253,0 926 16777875 /usr/local/sclilin99/logs/song.access.log
nginx 5154 root 7w REG 253,0 280 17584801 /usr/local/sclilin99/logs/song.error.log
nginx 5154 root 8w REG 253,0 92 17584803 /usr/local/sclilin99/logs/huang.access.log
nginx 5154 root 9w REG 253,0 0 17584805 /usr/local/sclilin99/logs/huang.error.log
nginx 5154 root 10w REG 253,0 92 17584808 /usr/local/sclilin99/logs/peng.access.log
nginx 5154 root 11w REG 253,0 0 17576982 /usr/local/sclilin99/logs/peng.error.log
nginx 5154 root 12w REG 253,0 23021 16779566 /usr/local/sclilin99/logs/error.log
nginx 5154 root 13u IPv4 45505 0t0 TCP *:http (LISTEN)
nginx 5154 root 14u IPv4 45506 0t0 TCP *:etlservicemgr (LISTEN)
nginx 5154 root 15u unix 0xffff881379575000 0t0 45509 socket
lsof查看某个文件夹被哪个进程打开
[root@xieshan lianxi]# lsof /lianxi
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
bash 5384 root cwd DIR 253,0 4096 50705641 /lianxi
bash 6183 root cwd DIR 253,0 4096 50705641 /lianxi
lsof 6716 root cwd DIR 253,0 4096 50705641 /lianxi
lsof 6717 root cwd DIR 253,0 4096 50705641 /lianxi
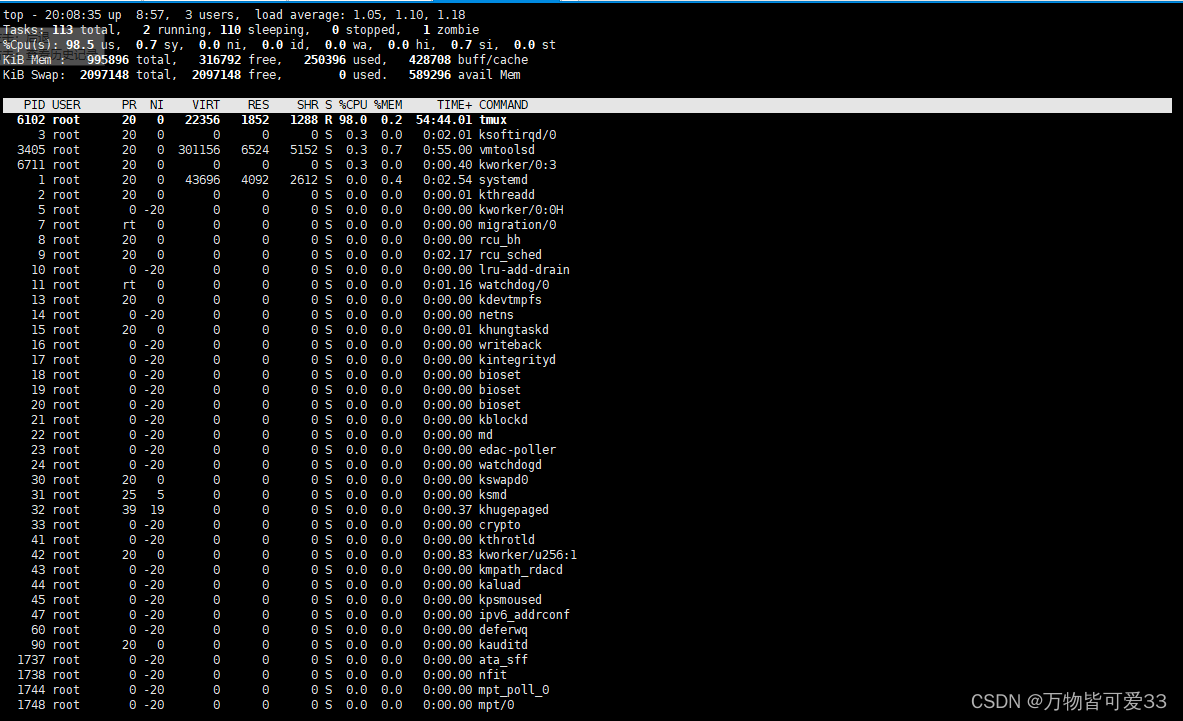
3.top命令
top查看哪个进程在哪个CPU里面运行
? ? ? ? 首先在命令行中输入top命令,进入如下界面
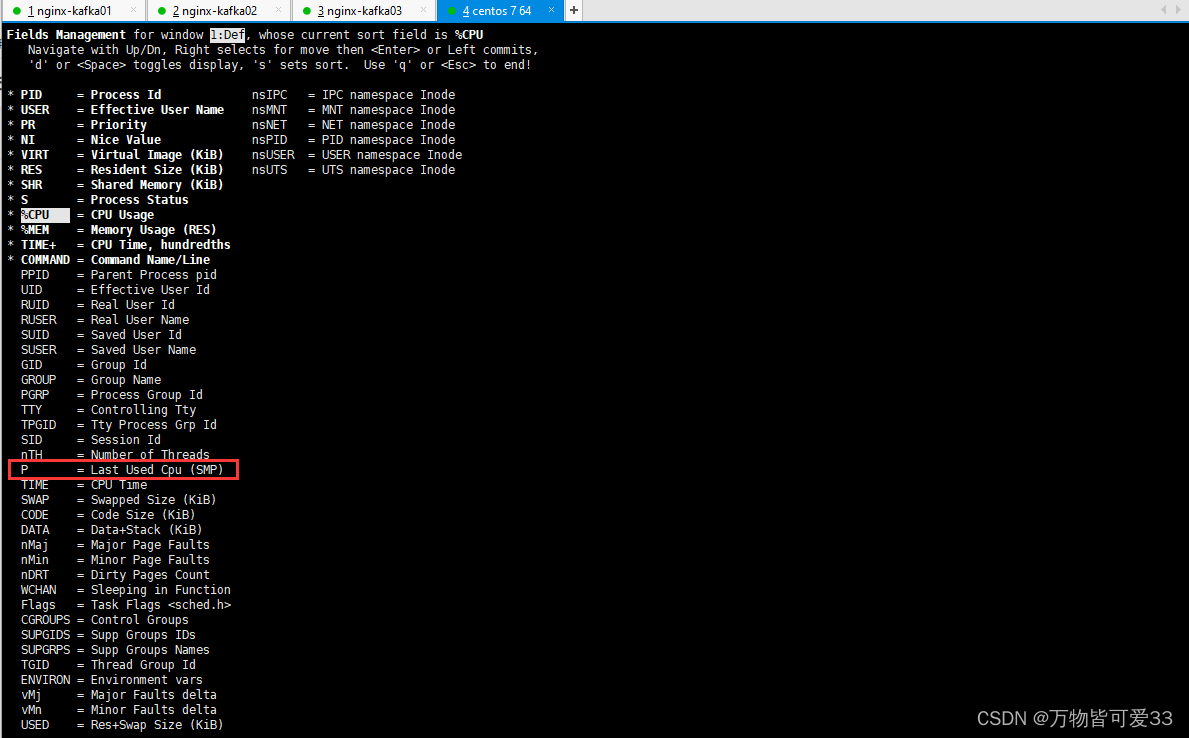
?然后在键盘中按f进入如下界面,并且将光标移到p那个位置,然后按下空格选中,再按q退出
?退出之后便可以看到哪个进程在哪个CPU中运行了
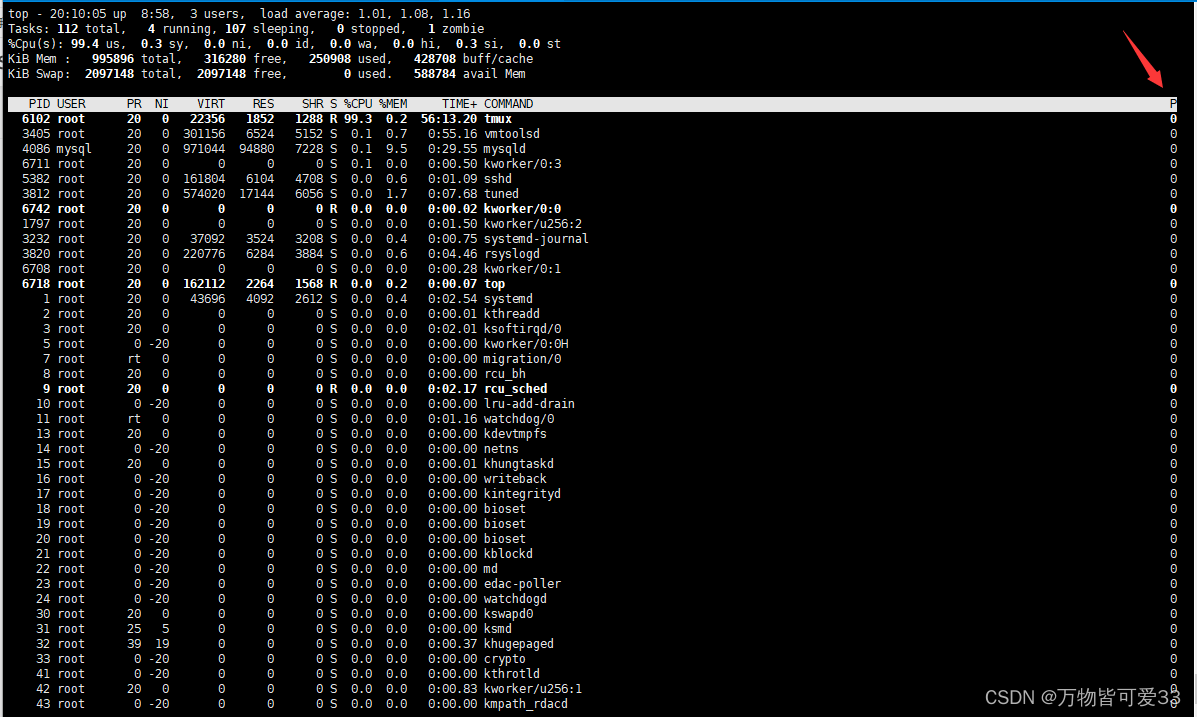
?查看虚拟机有几个CPU的方法是:在命令行中输入top,然后按一下1,观察第三行的结果便可以知道有几个了
能够实时显示系统中各个进程的资源占用状况,类似于Windows的任务管理器,输入会得到如下界面,按f可以查看到更多选项
top命令的详细解析:https://blog.csdn.net/langzi6/article/details/124805024?
4.nc命令
扫描其他机器开放了哪个端口
# -z是指仅仅扫描指定主机的指定端口,但是不向对方发送任何数据包
# -w 是指定超时时间,否则如果对方的指定端口未打开,nc可能会一直卡着不动
[root@xieshan lianxi]# nc -z 192.168.2.43 80
[root@xieshan lianxi]# echo $?
0 #查看上一条命令的执行结果,为0说明执行成功,其他数值则为不成功
[root@xieshan lianxi]# nc -z 192.168.2.43 8080
[root@xieshan lianxi]# echo $?
1
[root@xieshan lianxi]# nc -w 1 -z 192.168.2.23 8080
[root@xieshan lianxi]# echo $?
1
5.nmap命令
namp是网络探测工具和安全、端口扫描器,可以扫描一个局域网内机器开放了哪些端口
Nmap 也就是Network Mapper,最早是Linux下的网络扫描和嗅探工具包)是一个网络连接端扫描软件,用来扫描网上电脑开放的网络连接端。确定哪些服务运行在哪些连接端,并且推断计算机运行哪个操作系统(这是亦称 fingerprinting)
基本功能:
1)主机发现:检测目标主机是否在线
2)端口扫描:检测端口状态和提供的服务
3)版本侦测:检测端口提供服务的包或软件的版本信息
4)操作系统侦测:检测主机使用的操作系统
[root@xieshan lianxi]# nmap 192.168.2.34
Starting Nmap 6.40 ( http://nmap.org ) at 2022-07-15 20:21 CST
Nmap scan report for 192.168.2.34
Host is up (0.00034s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
22/tcp open ssh
MAC Address: 00:0C:29:16:AB:A3 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 28.79 seconds
[root@xieshan lianxi]# nmap 192.168.2.0/24 #扫描一个网段,但是速度会很慢6.glances命令
资源监控工具,显示的系统状态参数比top命令还要详细
在命令行中输入glances会看到如下界面,详细的展示了资源的使用情况
关于glances更加详细的解析:https://blog.csdn.net/icanflyingg/article/details/122877348
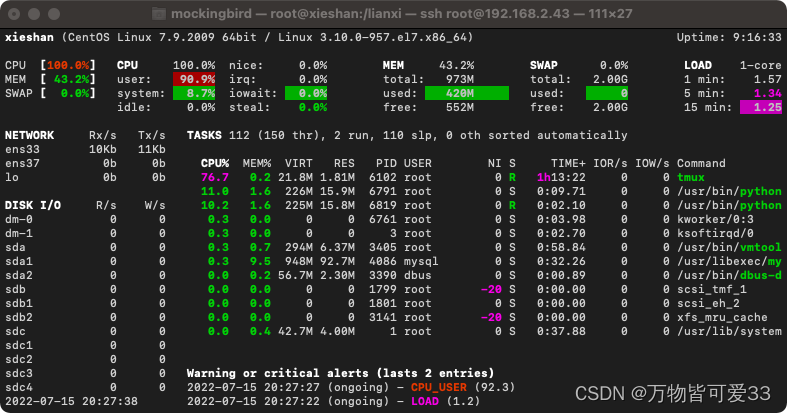
?7.如何得到整个局域网里所有正在使用的电脑的mac地址?
在局域网中,只要你的电脑和别人有通信,就会知道对方的mac地址,ping对方的ip地址就可以得到对方的mac地址
假设整个局域网的IP地址从192.168.0.1~192.168.0.254
[root@cPen_B lianxi]# vim scan_lan.sh
#!/bin/bash
>lan_up.txt
>lan_down.txt
echo $$ #查看当前子bash的进程号
num=$(echo $$)
pstree -p|egrep $num #查看过滤出当前子bash的父进程号
#循环ping整个局域网里的IP地址
for i in {1..10}
do
#启动多进程去ping,提升效率,启动子进程放到后台去执行
(if ping -i 0.1 -c 1 -W 1 192.168.2.$i &>/dev/null;then
echo "192.168.2.$i is up"
# echo "192.168.2.$i" >>lan_up.txt
else
echo "192.168.2.$i is down"
echo "192.168.2.$i" >>lan_down.txt
fi)&
done
#父进程等子进程结束,然后
wait
#将arp缓存表里的记录保存到up.txt
arp -n|awk '/ether/{print $1,$3}' >>up.txt
[root@xieshan lianxi]# time bash scan_lan.sh
[root@xieshan lianxi]# cat up.txt |wc -l
102
[root@xieshan lianxi]# arp -a #注:查看本机的arp缓存表的信息8.fping命令
fping跟ping命令类似,可以用来检测网络通不通,fping可以接网段,然后循环ping?
[root@xieshan lianxi]# fping -g 192.168.2.0/24
192.168.2.1 is alive
192.168.2.33 is alive
192.168.2.34 is alive
192.168.2.35 is alive
192.168.2.43 is alive
192.168.2.2 is unreachable
192.168.2.3 is unreachable
192.168.2.4 is unreachable
[root@xieshan lianxi]# fping -gaq 39.108.0.0/24 #-g指定网段,-a只显示存活的ip地址,-q是只要输出结果
39.108.0.6
39.108.0.8
39.108.0.12
39.108.0.14
39.108.0.15
39.108.0.3
39.108.0.16
39.108.0.18
39.108.0.21
39.108.0.23
39.108.0.36
39.108.0.41
[root@xieshan ~]# fping -f ip.txt #fping可以按照文本中指定的IP地址去ping
三.域名解析命令
域名解析就是通过输入某一个网站的网址,从而得到这个网站的IP地址
1.ping命令
[root@scchen1 ~]# ping www.baidu.com
PING www.a.shifen.com (14.215.177.39) 56(84) bytes of data.
64 bytes from 14.215.177.39 (14.215.177.39): icmp_seq=1 ttl=52 time=5.12 ms
64 bytes from 14.215.177.39 (14.215.177.39): icmp_seq=2 ttl=52 time=5.17 ms
^C
--- www.a.shifen.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 5.128/5.150/5.172/0.022 ms2.host命令
[root@scchen1 ~]# host www.baidu.com
www.baidu.com is an alias for www.a.shifen.com.
www.a.shifen.com has address 14.215.177.38
www.a.shifen.com has address 14.215.177.393.dig命令
[root@scchen1 ~]# dig www.baidu.com
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.9 <<>> www.baidu.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13701
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.baidu.com. IN A
;; ANSWER SECTION:
www.baidu.com. 832 IN CNAME www.a.shifen.com.
www.a.shifen.com. 17 IN A 14.215.177.39
www.a.shifen.com. 17 IN A 14.215.177.38
;; Query time: 0 msec
;; SERVER: 100.100.2.136#53(100.100.2.136)
;; WHEN: 五 4月 08 11:00:13 CST 2022
;; MSG SIZE? rcvd: 904.nslookup命令
[root@scchen1 ~]# nslookup www.baidu.com
Server: 100.100.2.136
Address: 100.100.2.136#53
Non-authoritative answer:
www.baidu.com canonical name = www.a.shifen.com.
Name: www.a.shifen.com
Address: 14.215.177.38
Name: www.a.shifen.com
Address: 14.215.177.39