ssh服务介绍
ssh服务(secure shell)是一个应用层的协议,用来远程控制服务器。
默认端口:TCP 22
SSH基于公钥加密(非对称加密)技术
·数据加密传输
·客户端和服务器的身份验证
ssh常见的2种登陆方式:
1、密码登陆
2、密钥登陆(免密码登录) # 注:不需要密码
查看ssh服务是否启动
配置免密通道
实现公钥认证,免密码登录
A ==》 B ,从A机器登录到B机器上
- A机器生成公钥对。在A机器上生成公钥对(如果有公钥对,则不需要重新生成),默认会放在当前用户家目录下的.ssh/文件下生成一个id_rsa(私钥),id_rsa.pub(公钥)
- 将公钥发送给B机器。将A机器的公钥复制传送给B机器,保存在目标用户~/.ssh/authorized_keys
并且确保这个文件的权限设为600 - 查看公钥认证是否成功。在A机器上执行 ssh root@B机器的ip,是否成功登录
具体操作
1、A机器上面执行 ssh-keygen,整个过程一直敲回车即可
[root@wlf ~]# ssh-keygen # 注:创建密钥对
Generating public/private rsa key pair. #注:rsa算法生成公钥和私钥的钥匙对(钥匙有2把不是同一把)
Enter file in which to save the key (/root/.ssh/id_rsa): # 注:存放公私钥的路径,root用户的
Enter passphrase (empty for no passphrase): #注:设置密钥密码(无需设置)
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:JZh0IhlTUDkIvuXuv7Iw7zYsoucwfLjpPWrHYN7P63g root@wlf # 注:算法hash算法
The key's randomart image is: # 注:信息摘要 用的 SHA256 hash算法
+---[RSA 2048]----+
| ..=B=.. |
| . o+o= |
| . . o.. . |
| + o |
| . . S |
|.o.. |
|=o*o. |
|.=BXBE |
|=O+*XX+. |
+----[SHA256]-----+
[root@wlf ~]#
此时我们可以进入~/.ssh目录下查看是否有密钥对,id_rsa(私钥)和 id_rsa.pub(公钥)
[root@wlf ~]# cd ~/.ssh
[root@wlf .ssh]# ls
id_rsa id_rsa.pub known_hosts
2、将A机器的公钥复制传送给B机器。在A机器上执行 ssh-copy-id -i id_rsa.pub root@ip即可将公钥传送给B机器,并且该条语句可以直接将公钥保存在B机器的**~/.ssh/authorized_keys**里,无需自己去创建文件,非常便捷。
[root@wlf .ssh]# ssh-copy-id -i id_rsa.pub root@192.168.10.130
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_rsa.pub"
The authenticity of host '192.168.10.130 (192.168.10.130)' can't be established.
ECDSA key fingerprint is SHA256:Q/qTNMSV2LTErqZtcIkgAe3Tv45HazIwdIxx03SFc4U.
ECDSA key fingerprint is MD5:06:af:ee:59:94:a1:04:bf:4e:bc:71:f6:9c:af:3e:19.
Are you sure you want to continue connecting (yes/no)? yes # 输入yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.10.130's password: # 这里输入B机器的密码
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.10.130'"
and check to make sure that only the key(s) you wanted were added.
[root@wlf .ssh]#
在B机器上面查看是否有**~/.ssh/authorized_keys**,及该文件的权限(使用上述方法不需要去修改文件的权限,文件权限已经是600)
[root@nginx-kafka01 ~]# cd ~/.ssh
[root@nginx-kafka01 .ssh]# ls
authorized_keys
[root@nginx-kafka01 .ssh]# ll
总用量 4
-rw------- 1 root root 390 7月 28 19:42 authorized_keys
3、测试是否可以免密登录。在A机器上尝试用ssh登录B机器,看是否需要密码
[root@wlf .ssh]# ssh root@192.168.10.130
Last login: Thu Jul 28 19:42:30 2022 from 192.168.10.1
[root@nginx-kafka01 ~]#
# 无需输入密码即可成功登录B机器。
[root@nginx-kafka01 ~]# exit
登出
Connection to 192.168.10.130 closed.
[root@wlf .ssh]#
# exit退出B机器
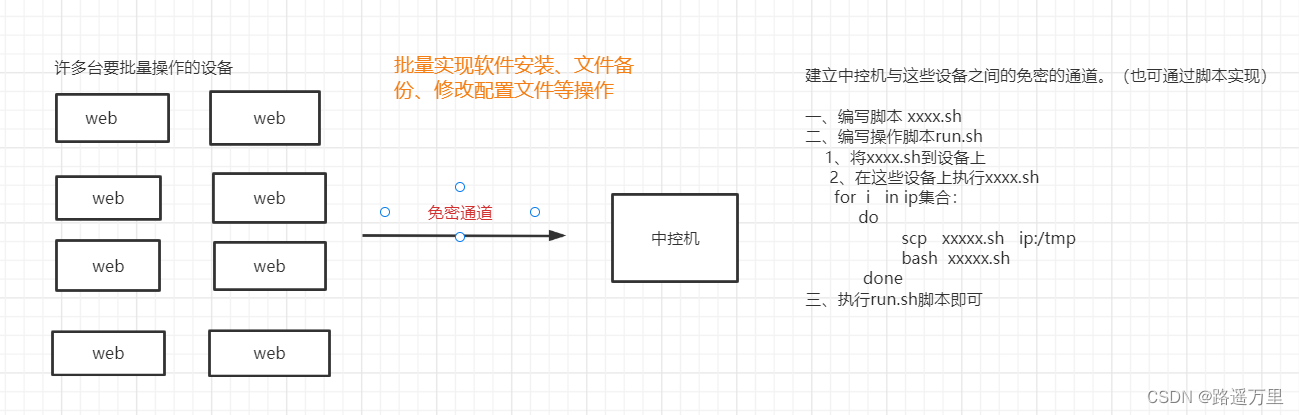
免密通道的用处
当我们需要对多台机器进行批量操作时配置了免密通道就非常的便捷。比如我们需要在多台机器上安装同一个软件,一个一个机器去安装非常耽误时间且繁琐,此时,我们可以将安装软件过程编写成安装脚本。然后再编写一个执行安装的脚本,编写for循环,利用ssh免密通道在这些机器进行安装软件。