一、前文
本文直接进行Linux系统firewalld防火墙的应用实操
- 对外端口开放使用
- 对内端口限制ip地址使用
- 不使用端口默认关闭
基础知识请查阅:Linux系统firewalld防火墙的基本操作
应用实操请查阅:Linux系统firewalld防火墙的应用实操(对外端口开放使用,对内端口限制ip地址使用,不使用端口默认关闭)
二、启动firewalld
- firewalld 默认不启动
systemctl status firewalld
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled)
Active: inactive (dead)
Docs: man:firewalld(1)
- firewalld的规则是默认拒绝访问
systemctl start firewalld
systemctl status firewalld
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# systemctl start firewalld
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled)
Active: active (running) since Sun 2022-08-14 23:10:53 CST; 6s ago
Docs: man:firewalld(1)
Main PID: 14774 (firewalld)
Tasks: 2 (limit: 26213)
Memory: 21.7M
CGroup: /system.slice/firewalld.service
└─14774 /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid
Aug 14 23:10:53 iZ2ze30dygwd6yh7gu6lskZ systemd[1]: Starting firewalld - dynamic firewall daemon...
Aug 14 23:10:53 iZ2ze30dygwd6yh7gu6lskZ systemd[1]: Started firewalld - dynamic firewall daemon.
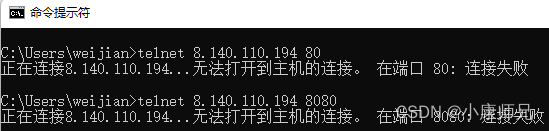
- 所以启动firewalld后,虽然服务器ip还能ping得通。
- 但是,端口却telnet不通了。
telnet 8.140.110.xxx 80
telnet 8.140.110.xxx 8080
telnet 8.140.110.xxx 443
telnet 8.140.110.xxx 8443
三、开放端口
- 80/8080/443/8443等对外开放的端口,允许所有ip永久访问
firewall-cmd --add-port=80/tcp --permanent
firewall-cmd --add-port=8080/tcp --permanent
firewall-cmd --add-port=443/tcp --permanent
firewall-cmd --add-port=8443/tcp --permanent
firewall-cmd --reload
firewall-cmd --list-all
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --add-port=80/tcp --permanent
success
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --add-port=8080/tcp --permanent
success
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --add-port=443/tcp --permanent
success
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --add-port=8443/tcp --permanent
success
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --reload
success
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports: 80/tcp 8080/tcp 443/tcp 8443/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
- telnet 测试也通了
telnet 8.140.110.xxx 80
telnet 8.140.110.xxx 8080
telnet 8.140.110.xxx 443
telnet 8.140.110.xxx 8443
四、特殊端口限制ip地址开放
- 特殊端口,
- 比如22端口为了给远程连接ssh使用
- 比如3306端口为了mysql数据库
- 比如6379端口为了redis数据库
- 这些特殊端口仅提供给开发者访问,以及本地java程序访问,所以限制ip地址访问。
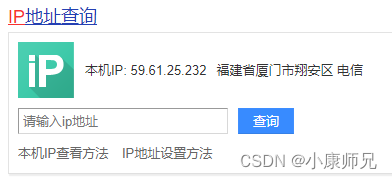
- 首先查询自己的ip,然后把自己的ip添加进规则。
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="127.0.0.1" port protocol="tcp" port="22" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="127.0.0.1" port protocol="tcp" port="3306" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="127.0.0.1" port protocol="tcp" port="6379" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="59.61.25.232" port protocol="tcp" port="22" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="59.61.25.232" port protocol="tcp" port="3306" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="59.61.25.232" port protocol="tcp" port="6379" accept'
firewall-cmd --reload
- 这边放了一个错误,添加了
127.0.0.1的ip地址,但是本机java程序还是无法访问数据库。 - 然后又尝试了
localhost,直接报错。 - 最后添加了本机的ip
8.140.110.xxx才得以成功。
[root@iZ2ze30dygwd6yh7gu6lskZ home]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="localhost" port protocol="tcp" port="22" accept'
Error: INVALID_ADDR: localhost
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="8.140.110.xxx" port protocol="tcp" port="22" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="8.140.110.xxx" port protocol="tcp" port="3306" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="8.140.110.xxx" port protocol="tcp" port="6379" accept'
firewall-cmd --reload
[root@iZ2ze30dygwd6yh7gu6lskZ home]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports: 80/tcp 8080/tcp 443/tcp 8443/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="59.61.25.232" port port="22" protocol="tcp" accept
rule family="ipv4" source address="59.61.25.232" port port="3306" protocol="tcp" accept
rule family="ipv4" source address="59.61.25.232" port port="6379" protocol="tcp" accept
rule family="ipv4" source address="8.140.110.xxx" port port="22" protocol="tcp" accept
rule family="ipv4" source address="8.140.110.xxx" port port="3306" protocol="tcp" accept
rule family="ipv4" source address="8.140.110.xxx" port port="6379" protocol="tcp" accept
- 测试验证
- 使用本地网络(IP:59.61.25.232),则访问数据库ok
- 使用手机热点开启的网络(IP:其他),则访问数据库ng
觉得好,就一键三连呗(点赞+收藏+关注)