nginx访问控制
用于location段
allow:设定允许哪台或哪些主机访问,多个参数间用空格隔开
deny:设定禁止哪台或哪些主机访问,多个参数间用空格隔开
示例:
location ~* ^/abc$ {
deny 192.168.64.129;
echo "wawa";
}
location / {
echo "haha";
<nx/conf/nginx.conf" 126L, 2752C written
[root@nginx ~]# systemctl restart nginx.service

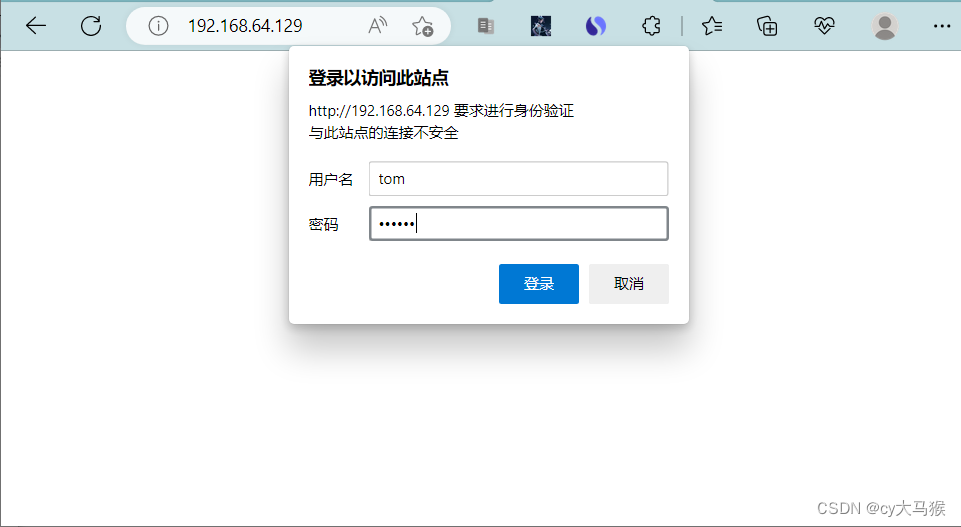
基于用户认证
先安装一下apache的工具安装包
[root@nginx ~]# which htpasswd
/usr/bin/which: no htpasswd in (/usr/local/nginx/sbin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin)
[root@nginx ~]# dnf provides *bin/htpasswd
Last metadata expiration check: 0:38:54 ago on Thu 13 Oct 2022 11:11:45 PM CST.
httpd-tools-2.4.37-41.module_el8.5.0+977+5653bbea.x86_64 : Tools for
...: use with the Apache HTTP Server
Repo : AppStream
Matched from:
Other : *bin/htpasswd
httpd-tools-2.4.37-43.module_el8.5.0+1022+b541f3b1.x86_64 : Tools for
...: use with the Apache HTTP Server
Repo : AppStream
Matched from:
Other : *bin/htpasswd
[root@nginx ~]# dnf -y install httpd-tools
过程省略。。。。。
生成加密文化
[root@nginx ~]# htpasswd -c -m /usr/local/nginx/conf/.htpasswd tom
New password:
Re-type new password:
Adding password for user tom
[root@nginx ~]#
[root@nginx ~]# cd /usr/local/nginx/conf/
[root@nginx conf]# cat .htpasswd
tom:$apr1$E9/TWbvk$4oH9zJd0fcW7R0/yi4tHA1
[root@nginx conf]#
这里的密码为加密后的密码串,建议用htpasswd来创建此文件:
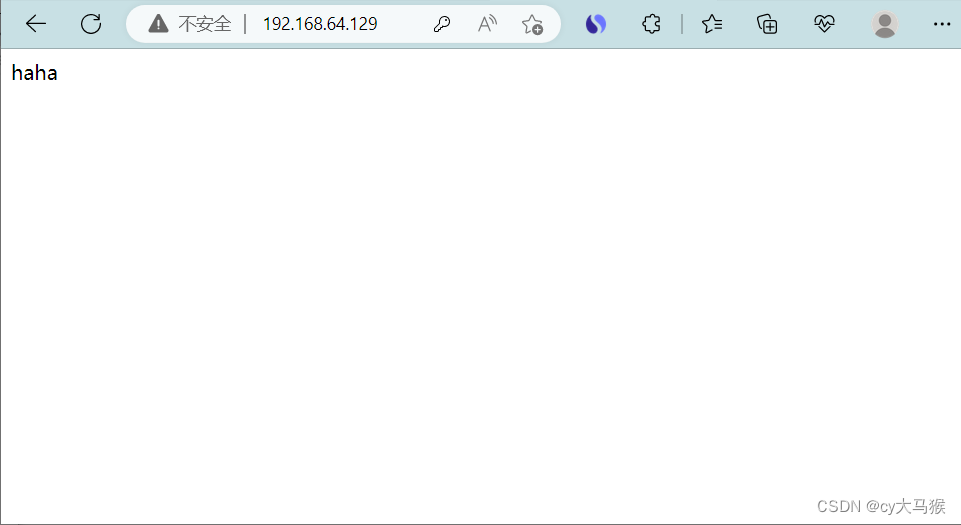
location / {
auth_basic "cys";
auth_basic_user_file .htpasswd;
echo "haha";
}
[root@nginx conf]# systemctl restart nginx.service
https配置
创建密匙存放目录
[root@nginx conf]# mkdir -p /etc/pki/CA
[root@nginx conf]# cd /etc/pki/CA/
[root@nginx CA]#
[root@nginx CA]# mkdir private
[root@nginx CA]# ls
private
生成密钥
[root@nginx CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
...................................+++++
........................+++++
e is 65537 (0x010001)
[root@nginx CA]# ls private/
cakey.pem
[root@nginx CA]#
CA生成自签署证书
[root@nginx CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
[root@nginx CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:www.cys.com
Organizational Unit Name (eg, section) []:www.cys.com
Common Name (eg, your name or your server's hostname) []:www.cys.com
Email Address []:1@2.com
[root@nginx CA]#
[root@nginx CA]# mkdir certs newcerts crl
[root@nginx CA]# touch index.txt && echo 01 > serial
[root@nginx CA]# ls
cacert.pem certs crl index.txt newcerts private serial
[root@nginx CA]#
客户端(例如httpd服务器)生成密钥
[root@nginx ~]# cd /usr/local/nginx/
[root@nginx nginx]# ls
client_body_temp fastcgi_temp logs sbin uwsgi_temp
conf html proxy_temp scgi_temp
[root@nginx nginx]# cd conf/
[root@nginx conf]# mkdir ssl
[root@nginx conf]# cd ssl/
[root@nginx ssl]# (umask 077;openssl genrsa -out nginx.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
..........................................................................................................................................+++++
.......................+++++
e is 65537 (0x010001)
[root@nginx ssl]#
客户端生成证书签署请求
[root@nginx ssl]# openssl req -new -key nginx.key -days 365 -out nginx.csr
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:www.cys.com
Organizational Unit Name (eg, section) []:www.cys.com
Common Name (eg, your name or your server's hostname) []:www.cys.com
Email Address []:1@2.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@nginx ssl]#
CA签署提交上来的证书
[root@nginx ssl]# openssl ca -in nginx.csr -out nginx.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Oct 13 16:19:51 2022 GMT
Not After : Oct 13 16:19:51 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = www.cys.com
organizationalUnitName = www.cys.com
commonName = www.cys.com
emailAddress = 1@2.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
02:39:C2:56:17:49:42:BD:56:67:E4:12:1A:58:71:95:92:C6:CC:AF
X509v3 Authority Key Identifier:
keyid:BE:18:8B:82:13:9F:7E:25:F1:17:AF:B3:F4:CE:4E:AF:C1:2B:77:BA
Certificate is to be certified until Oct 13 16:19:51 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@nginx ssl]# ls
nginx.crt nginx.csr nginx.key
[root@nginx ssl]#
[root@nginx ssl]# rm -f *.csr
[root@nginx ssl]# ls
nginx.crt nginx.key
[root@nginx ssl]#
生成私钥,生成证书签署请求并获得证书,然后在nginx.conf中配置如下内容:
[root@nginx ssl]# cd ..
[root@nginx conf]# ls
fastcgi.conf mime.types ssl
fastcgi.conf.default mime.types.default uwsgi_params
fastcgi_params nginx.conf uwsgi_params.default
fastcgi_params.default nginx.conf.default win-utf
koi-utf scgi_params
koi-win scgi_params.default
[root@nginx conf]# vim nginx.conf
#把注释都取消掉
# HTTPS server
#
server {
listen 443 ssl;
server_name www.cys.com;
ssl_certificate ssl/nginx.crt;
ssl_certificate_key ssl/nginx.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
}
重启
[root@nginx conf]# systemctl restart nginx.service
[root@nginx conf]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:443 0.0.0.0:*
LISTEN 0 128 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
[root@nginx conf]#
免费https证书申请
阿里云购买
https://promotion.aliyun.com/ntms/act/sslbuy.html?spm=5176.21213303.782131.6.38fa53c9fGENj0&scm=20140722.S_card@@%E4%BA%A7%E5%93%81@@233187.S_cardgbdt.ID_card@@%E4%BA%A7%E5%93%81@@233187-RL_%E8%AF%81%E4%B9%A6-OR_ser-V_2-P0_0
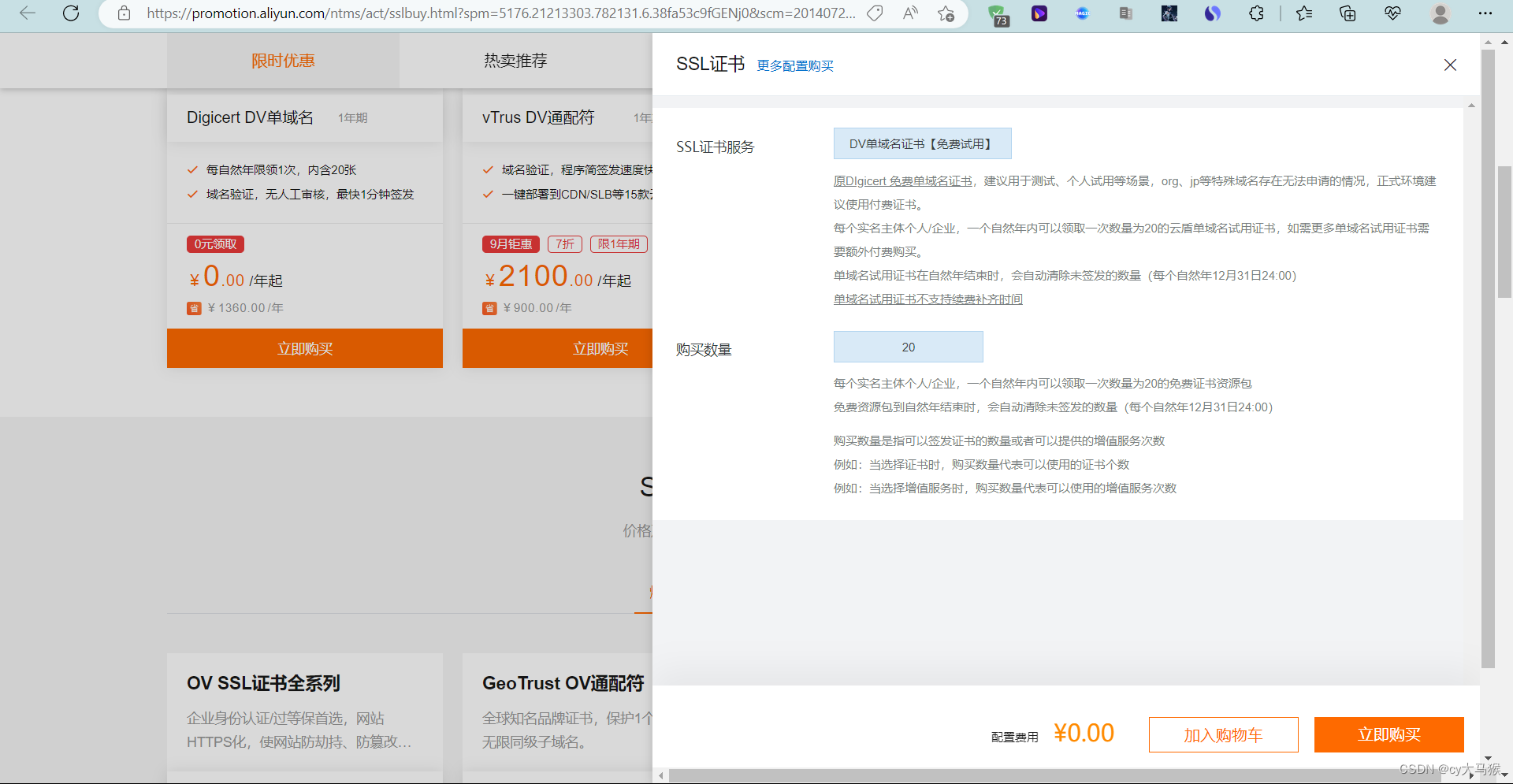
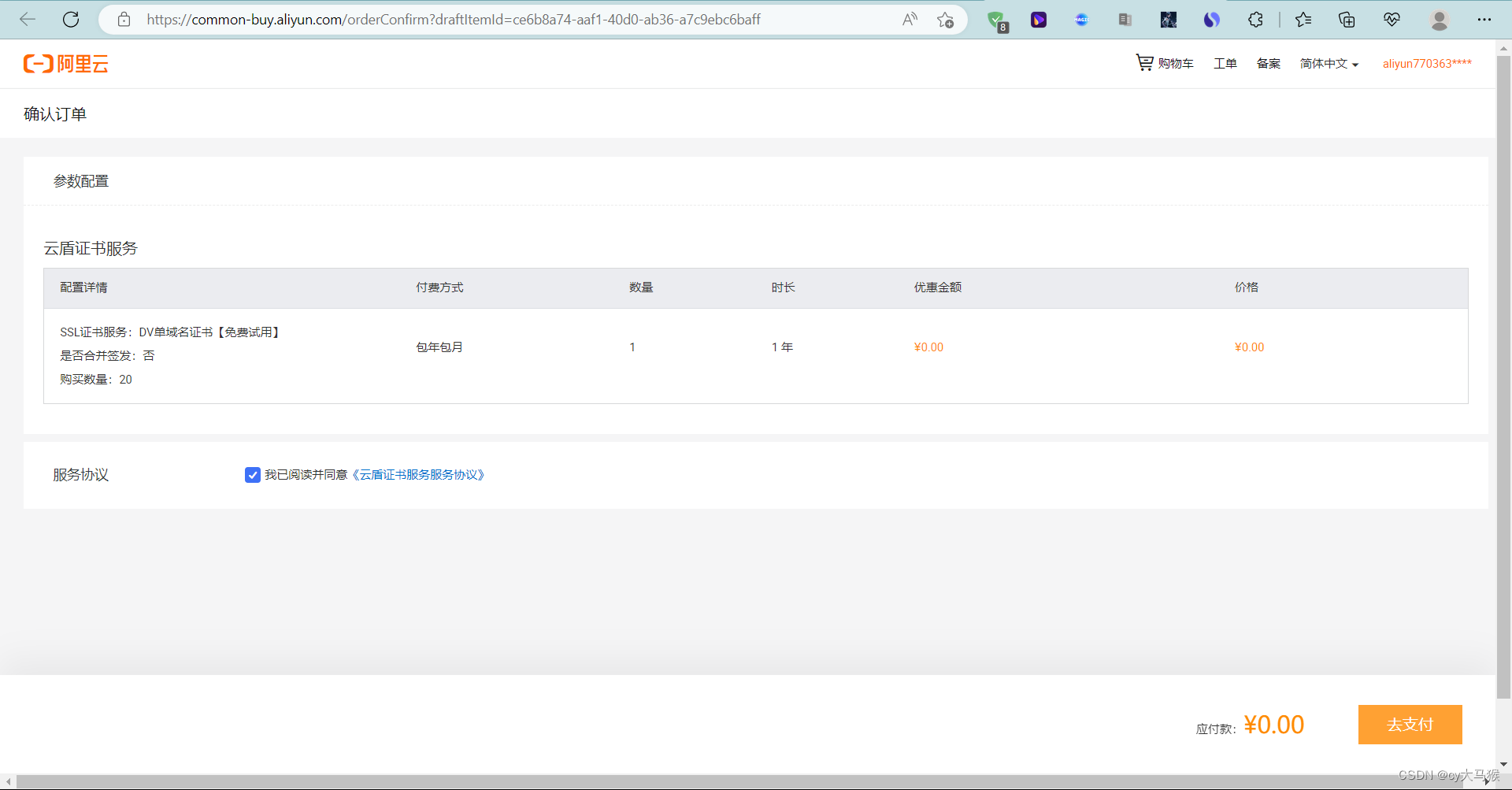
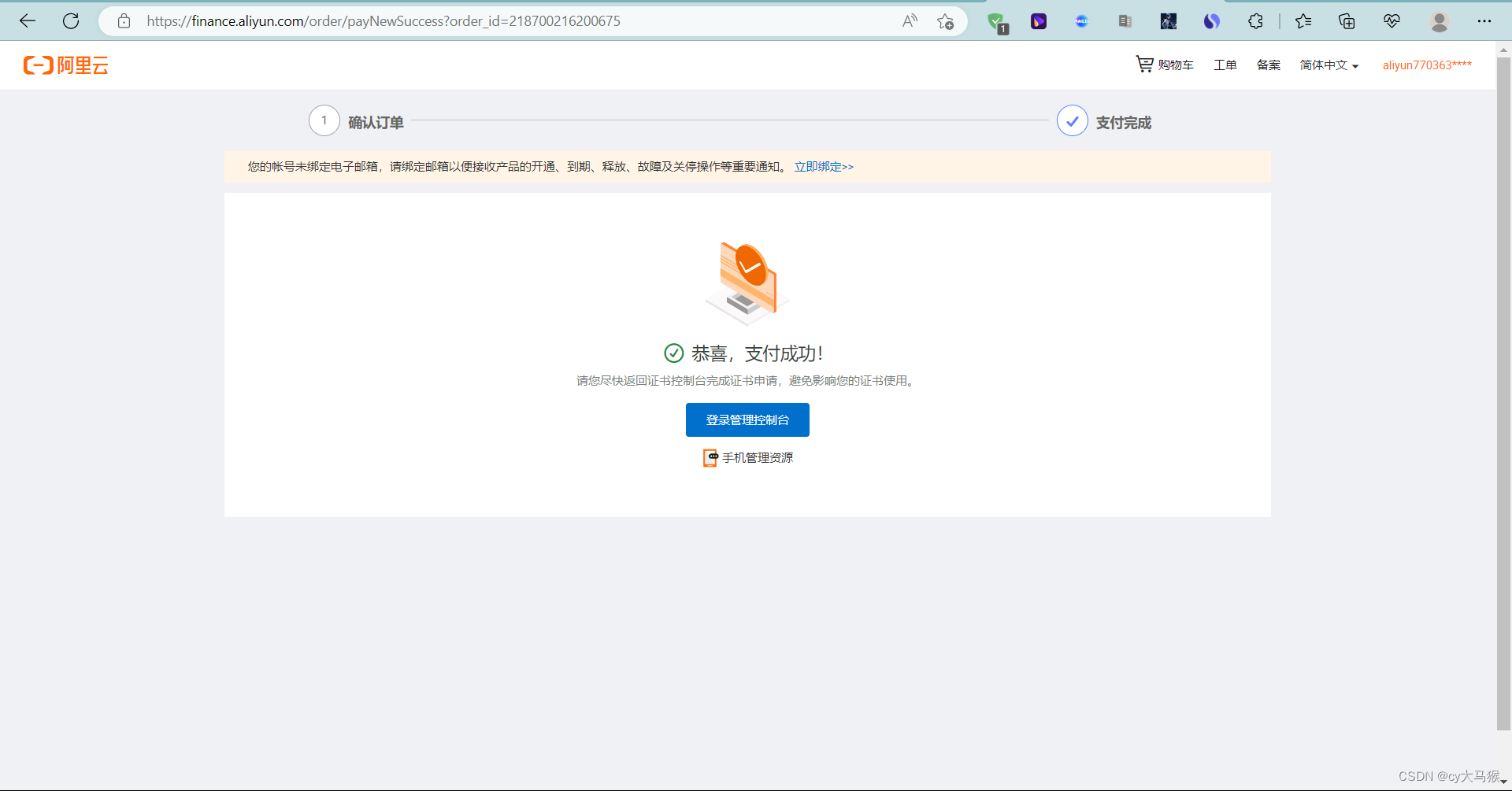



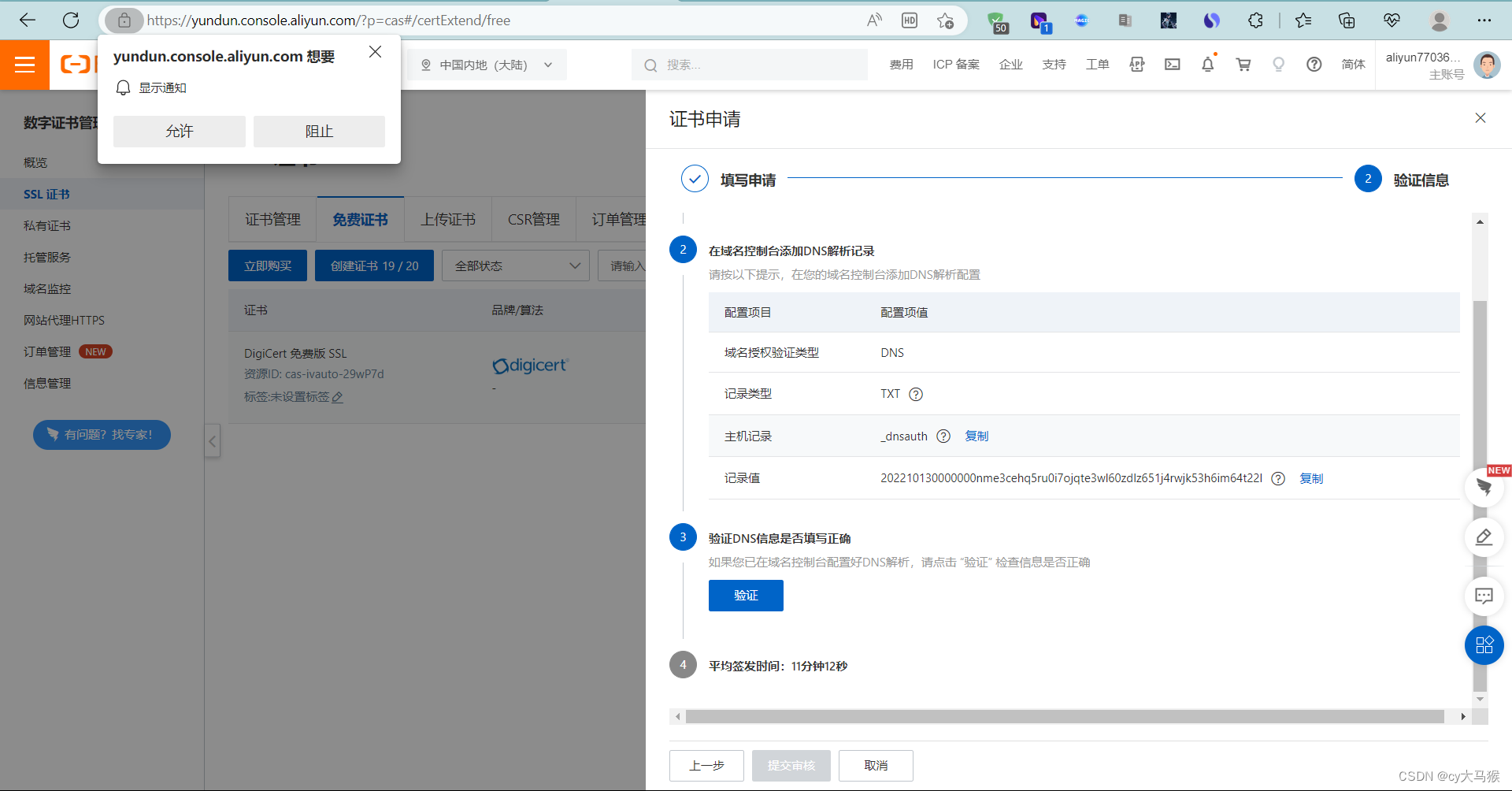
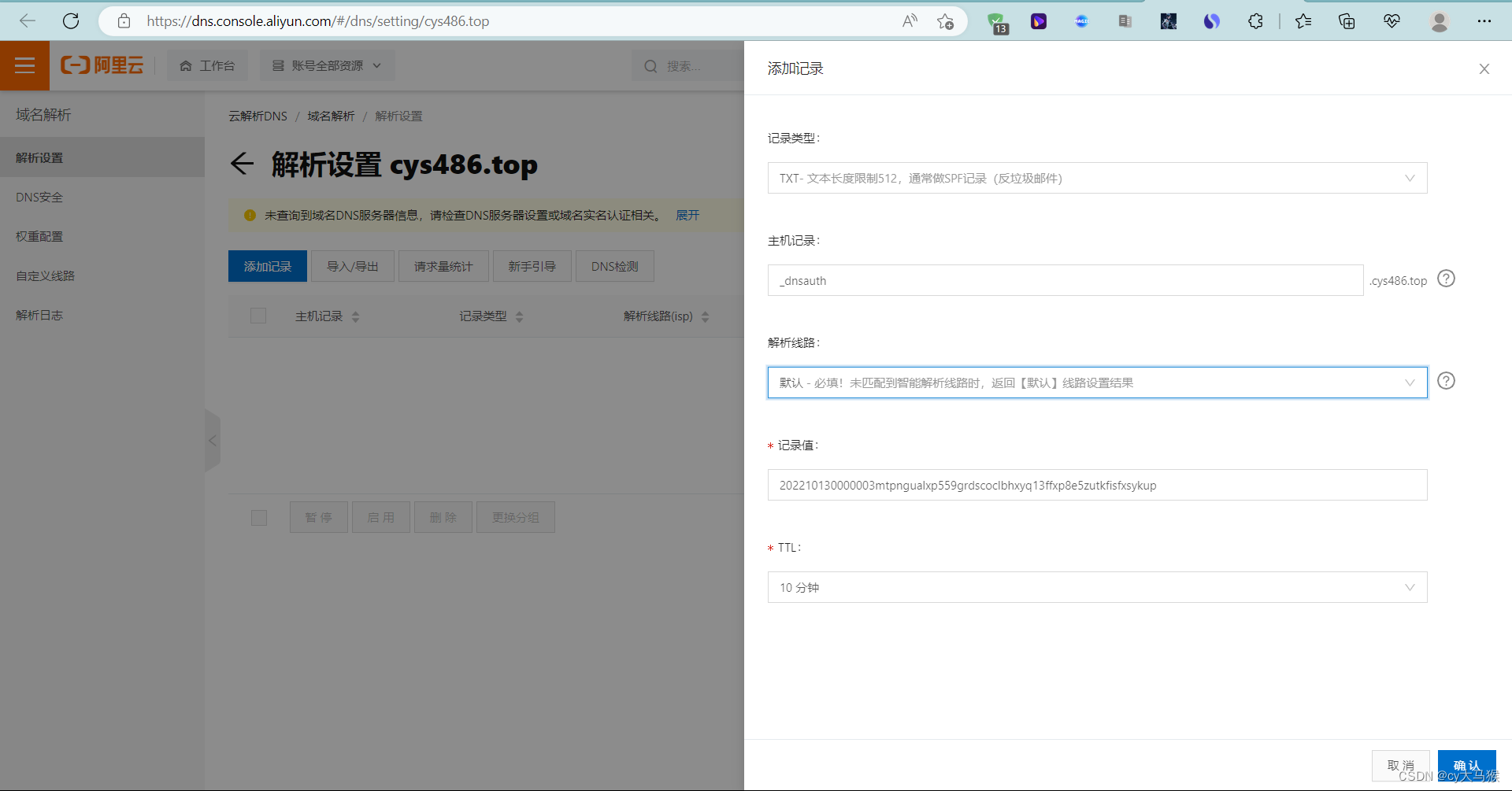

自己服务器使用点下载
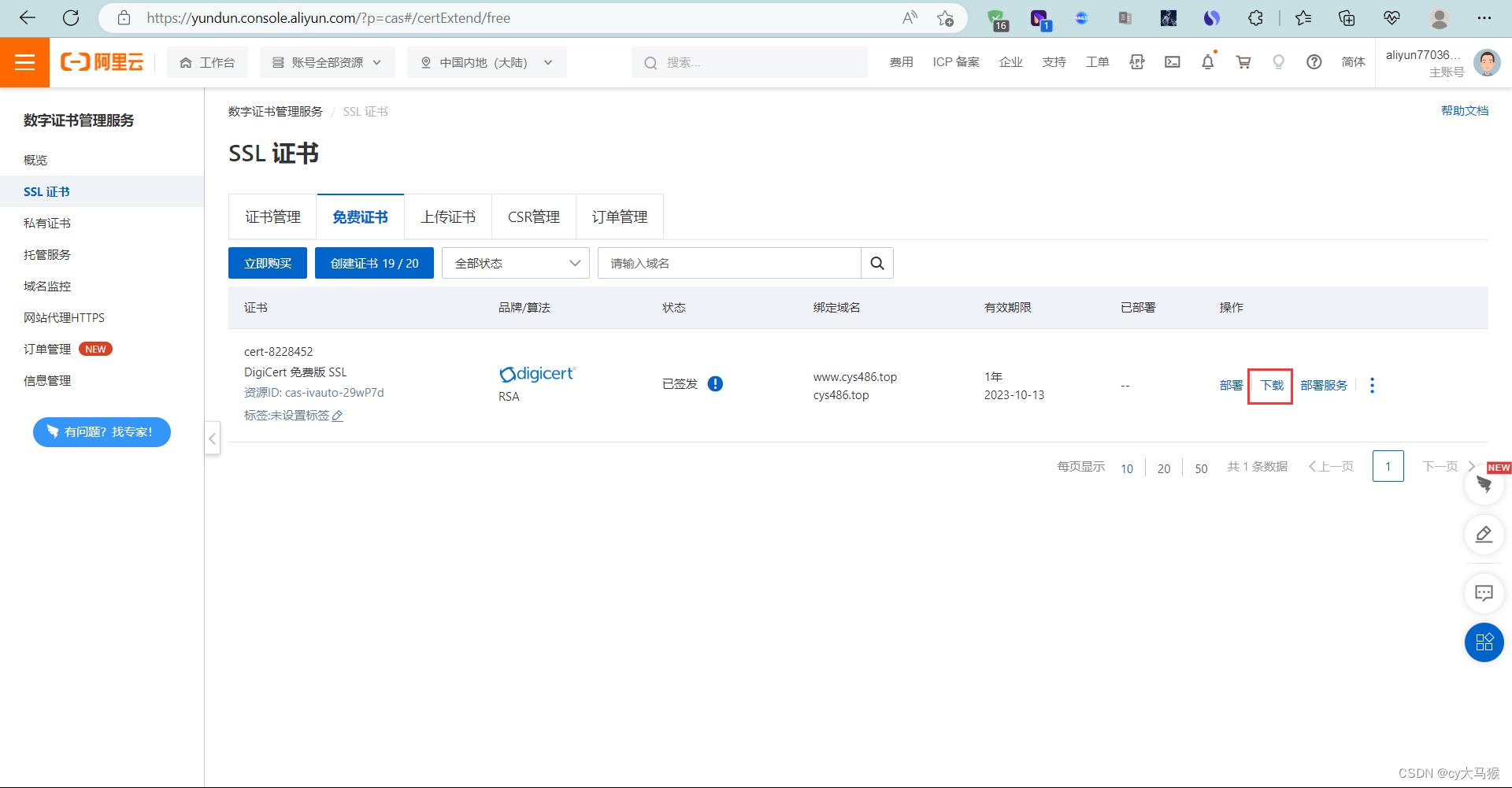

申请成功了有这个文件,拉到虚拟机里
[root@nginx ~]# ls
'\' nginx-1.20.2.tar.gz
8613512_www.cys486.top_nginx.zip nginx-1.22.0
anaconda-ks.cfg nginx-1.22.0.tar.gz
nginx-1.20.2 nginx_module_echo
[root@nginx ~]# unzip 8618537_www.cys486.top_nginx.zip
Archive: 8618537_www.cys486.top_nginx.zip
Aliyun Certificate Download
inflating: 8618537_www.cys486.top.pem
inflating: 8618537_www.cys486.top.key
[root@nginx ~]#
[root@nginx ~]# mv 8618537_www.cys486.top.key nginx.key
[root@nginx ~]# mv 8618537_www.cys486.top.pem nginx.crt
配置域名
[root@nginx ~]# cd /usr/local/nginx/conf/ssl/
[root@nginx ssl]# ls
nginx.crt nginx.key
[root@nginx ssl]# rm -rf *
[root@nginx ssl]# mv ~/nginx.key ~/nginx.crt .
[root@nginx ssl]# ls
nginx.crt nginx.key
[root@nginx ssl]# cd ..
# HTTPS server
#
server {
listen 443 ssl;
server_name www.cys486.top; //改成自己有的域名
ssl_certificate ssl/nginx.crt;
ssl_certificate_key ssl/nginx.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
[root@nginx conf]# systemctl restart nginx.service
状态页面开启和监控
location = /status { //添加
stub_status;
}
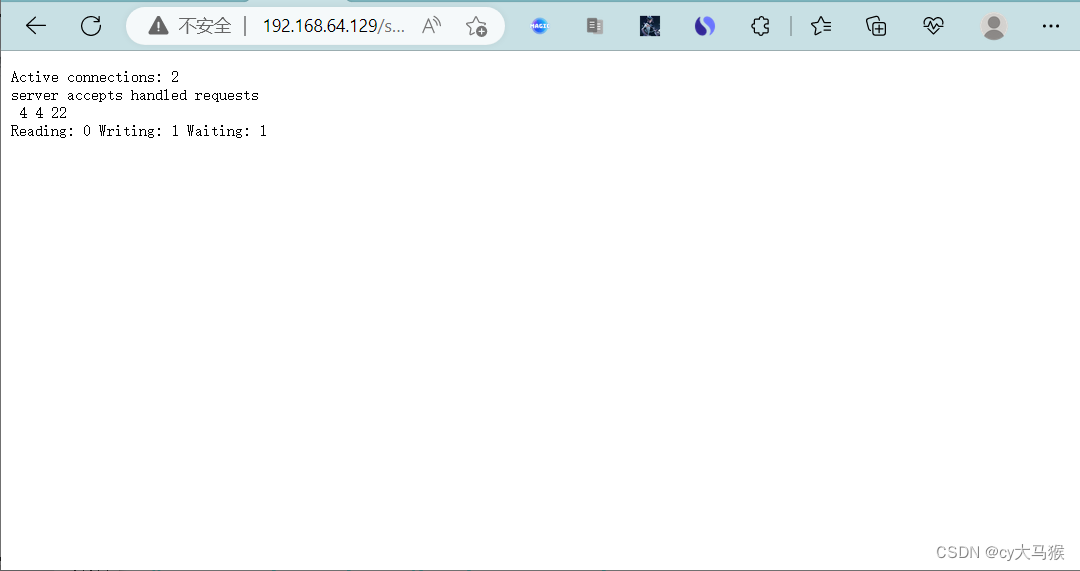
[root@nginx ~]# while :;do curl http://127.0.0.1;done

状态监控
[root@nginx ~]# curl -s http://192.168.64.129/status|awk 'NR==4{print $2}'
0
[root@nginx ~]# curl -s http://192.168.64.129/status|awk 'NR==4{print $4}'
1
[root@nginx ~]# curl -s http://192.168.64.129/status|awk 'NR==4{print $6}'
0